
Detect Phishing and Man in the Middle Attacks Before They Happen
How Certificate Transparency Logs Help Protect Your Organization
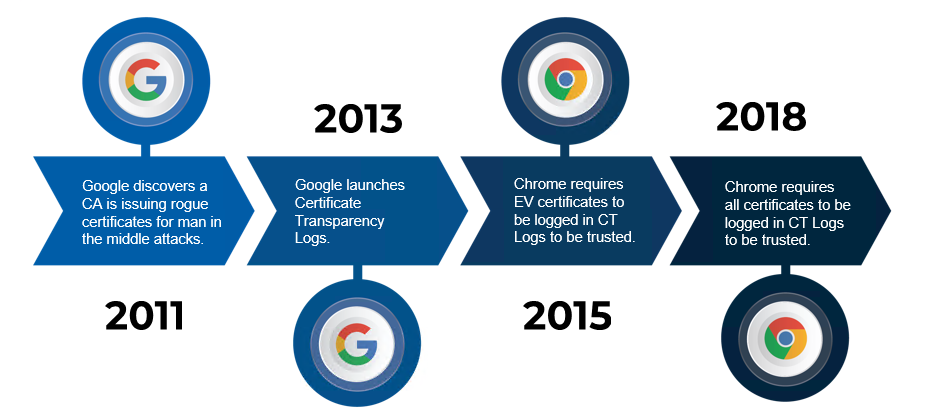
I want to start this blog post with a bit of history on why Certificate Transparency Logs were created. In 2011 Google discovered that a non-authorized entity had created an SSL certificate to man-in-the-middle Google services. Later it was discovered that a company that owned multiple publicly trusted CAs (Certification Authority) was hacked and their CAs issued rouge certificates. To prevent similar attacks, Google designed and implemented Certificate Transparency Logs, and in 2013 they released it to the world.
The Solution
The problem with the DigiNotar hack was that Google did not have visibility or knowledge that that certificate was issued or used (Google found out because a user posted in a forum that he could not login to Gmail unless he used a VPN and asked if someone else was having that problem). To solve the certificate visibility issue, Google created Certificate Transparency Logs.
Certificate Transparency Logs are a publicly available list of each certificate that has been issued. You are thinking: if a hacker issues a certificate, they will just not register it and it will go unnoticed. To enforce the usage of Certificate Transparency Logs, Google introduced an industry standard requiring a certificate to be registered in multiple Certificate Transparency Logs to be accepted by a browser.
The Solution’s Problem
While having a cryptographic tamper proof list of each certificate that has been issued is a great solution to the problem of not having visibility into certificates being issued, it also put the responsibility of monitoring the Certificate Transparency Logs for rogue certificates on each company in the world. While that might be a small project for large companies such as Google, it is a large project for most companies. With hundreds of new certificates issued every second, each company would have to deploy a very large infrastructure to search terabytes of data and catch any nonauthorized certificate for their domains.
The Solution to The Solution’s Problem
At Keytos, we aim to help companies secure their infrastructure by making PKI (Public Key Infrastructure) solutions easy to use. Therefore, we are happy to announce EZMonitor. For $1 a month, EZMonitor enables you to monitor Certificate Transparency Logs and will alert you if a new certificate for your domain is issued. Having the infrastructure to analyze this huge amount of data also enabled us to create more alerts such as:
- Alert if a certificate is about to expire and you have not renewed it.
- Alert if a renewed certificate has not been installed on your web servers.
- Monitor for new subdomains created.
- Alert on domains containing your domain. (This one is common on phishing campaigns where the attacker might use your domain as a subdomain. For example, yourdomain.com.attacker.com)
- Alert on certificate issued by a different Certificate Authority.
- Monitor internal certificates in your private network.
- We also alert on new vulnerabilities found that might still not be public.


