
Setting up a cloud PKI for Azure IoT has never been easier than it is now, thanks in part to innovative 3rd party PKI tools like EZCA from Keytos! As IoT devices proliferated and gained traction in the market, the complexity of managing them at scale increased proportionally. Due to the sheer volume of devices in existence, traditional methods of authentication simply didn’t cut it anymore. …If you didn’t already know, passwords are a problem, even for devices: Mirai botnet is a great example of why we shouldn’t use passwords. Additionally, traditional authentication methods lack the dynamic security measures (think automation and monitoring) needed to protect against increasingly sophisticated cyber threats, rendering them virtually useless in the modern IoT ecosystem and making them unsuitable for the continuously-evolving and interconnected nature of IoT ecosystems. A quick glance at some of the benefits associated with implementing the cloud makes it very clear as to why so many organizations are migrating to the gold-standard in device security. From enhanced security via encryption, to scalability, to automation, all the way through to adherence to industry-specific compliance standards, anyone that’s serious about IoT device security is taking proactive measures to get their cloud PKI set up with haste. In this post, we’re going to take a look at how to authenticate with certificates into Azure IoT Hub. Let’s dig in.
The obvious first step in virtually any process is planning (duh). When it comes to Azure IoT Cloud PKI, several considerations are important for a successful implementation. Scalability is first and foremost. Your PKI must be able to grow with your IoT environment, accommodating an increasing number of devices without compromising performance. Efficient certificate management is crucial for maintaining the security lifecycle of each device, from issuance to revocation. This includes automating certificate renewals and ensuring that expired certificates are promptly replaced. Finally, consider device compatibility. Your chosen PKI solution should support various device types and platforms in your IoT ecosystem, ensuring seamless integration and security across all connected components. This comprehensive approach will lay a solid foundation for your Azure IoT Cloud PKI strategy. Once you have a solid understanding of what exactly it is you’re trying to do, it makes it far easier to begin souring and implementing the appropriate solution.
This is the fun part! …well, not really… unless you enjoy endless “qualification” calls with entry-level Liberal Arts majors from sub-par schools or listening to vague “ballpark” pricing with hidden fees and a-la-cart add-ons that completely eliminate certain vendors from the consideration set. Rant over.
Frankly, most of the available tools do more-or-less the exact same things. Make sure to do the appropriate amount of research to gain a thorough understanding of what’s available, and what might be right for you. At a high level, you should be looking for solutions that are native to Azure, easy to install and manage, meet and exceed your compliance standards, integrate with services like Azure Key Vault, are reasonably priced, and provide automation. Most importantly, look for a vendor that provides top-tier customer service. I’m not just talking about SLA’s.
Pro-tip: send an inbound request on Friday afternoon and see how long it takes to get a response.
Getting down to brass tacks, let’s explore the implementation process. This part ought to be VERY smooth, especially if you’ve spent time speaking with vendors about their processes and congruence with your infrastructure. That being said, we’ve heard on numerous occasions that this can be the most time consuming, frustrating part of the entire process. As mentioned above, try to find the solution that is going to suit your specific needs and be “easy” to implement. What do we mean by easy? Well, how about a solution that you can implement yourself as opposed to one that requires a team of on-site “experts” to get the job done? Here’s a quick look at the simplicity provided by EZCA.
We encourage you to explore our EZCA YouTube playlist that will walk you through each step involved in getting your Cloud PKI for Azure IoT squared away. More of a reader? Take a peek at our documentation about getting started with EZCA!
As mentioned previously in our Azure IoT security best practices blog, the most difficult part of the process is adding your first certificate to the IoT device. With EZCA, creating your first Azure IoT certificate is an absolute breeze! In addition to the exceptionally intuitive UI, detailed step-by-step written and video tutorials available in our documentation section, the lovely Engineering team here at Keytos has created a code sample available on GitHub for you to use. Simple as that! Watch the video below to see how to get this done-and-dusted in under 5 minutes!
When leveraging a cloud CA, you can have your devices talk directly to the certificate authority through modern protocols such as a simple REST call. To make it easier for users, we have created a C# NuGet package that makes certificate renewal one simple line of code. If you are not using C#, you can use the sample code or the swagger page to write your own code to automatically renew your IoT certificates. Remember, since we are using a trusted certificate authority, we don’t need to register the new certificate in Azure, it’ll happen automatically!
Remember earlier in the post when I said, “Frankly, most of the available tools do more-or-less the exact same things.”? Well, there’s one crucial feature specific to EZCA that makes it the clear choice. An Engineer from Keytos discovered a bug in Azure IoT regarding revoked certificates, and how they’re still able to authenticate even if they’ve been revoked. In typical Microsoft fashion, after we told them about the issue (and were paid a bug bounty!), it only took 1 year and 10 months to add the following paragraph to their Azure PKI Documentation:
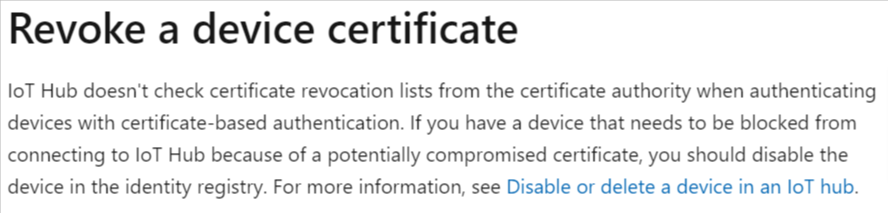
To be clear, the bug was never fixed. Meaning that o you want to stop a certificate from working, you’re going to have to manually deactivate the device. Sounds like a nightmare, right? Sure does. We are happy to announce that EZCA is the only Azure Cloud CA that automatically disables devices when a certificate is revoked, meaning you’ll never have to worry about the tedious and time-consuming task of manual deactivation. Just imagine how much time this’ll save compared to manually managing the process. EZCA is truly the IoT Engineer’s best friend when it comes to certificate automation in Azure IoT cloud!
It’s clear to see that we’ve built EZCA specifically with IoT in mind. As a cloud-native organization, we’re dedicated to providing the most comprehensive and easy to use tool(s). EZCA is the clear choice for the modern IoT Engineer that needs a solution they can rely on without breaking the bank. Schedule some time to chat with our Engineering team about your needs and to see how we can help! In the meantime, check out this video of how “EZ” (see what I did there?) to get started!