Microsoft Azure Vulnerability Still Affecting Thousands of New Subdomains Each Month
Microsoft Azure Vulnerability Still Affecting Thousands of New Subdomains Each Month
Subdomain takeover is a vulnerability that has plagued cloud users since the beginning of the cloud. This is a common vulnerability that is exploited by attackers to hijack existing trusted subdomains - allowing them to impersonate organizations and attack their site users and employees, or to show spam content via legitimate sites. But it has often been ignored by large cloud providers such as Microsoft due to the assumed low probability of a vulnerable domain being found.
In Microsoft Azure alone, researchers at Keytos now uncover around 15,000 vulnerable subdomains every month using cryptographic certificates. Unless action is taken, these present a growing number of opportunities for cyber criminals to pose as household name businesses in convincing – but unsophisticated – cyber attacks.
While Keytos has now notified more than 1,000 organizations about their domain issues in the last year, only 2% of these have taken action – with most simply ignoring the warning or even stating that resolving the issue wasn’t worth the time it would take to fix.
Uncovering The Issue
First, let us break down what a subdomain takeover is and how it works. Imagine you are hosting a pop-up sale and create a special site in Azure for this sale “wintersale.myshop.com”. When the sale ends, you delete your Azure website, but forget to remove your DNS (Domain Name System) entry that points your domain “wintersale.myshop.com” to the Azure website. This mistake leaves a digital backdoor wide open for a cybercriminal to create a site in Azure that looks like your website and use your forgotten domain for this new fraudulent site. To any unsuspecting user, their fraudulent site appears to be entirely legitimate since it is hosted in your domain. As evidenced in this video even password managers can be fooled into automatically inputting user passwords into these sites, not only exposing customer credentials, but also giving users a false sense of security.
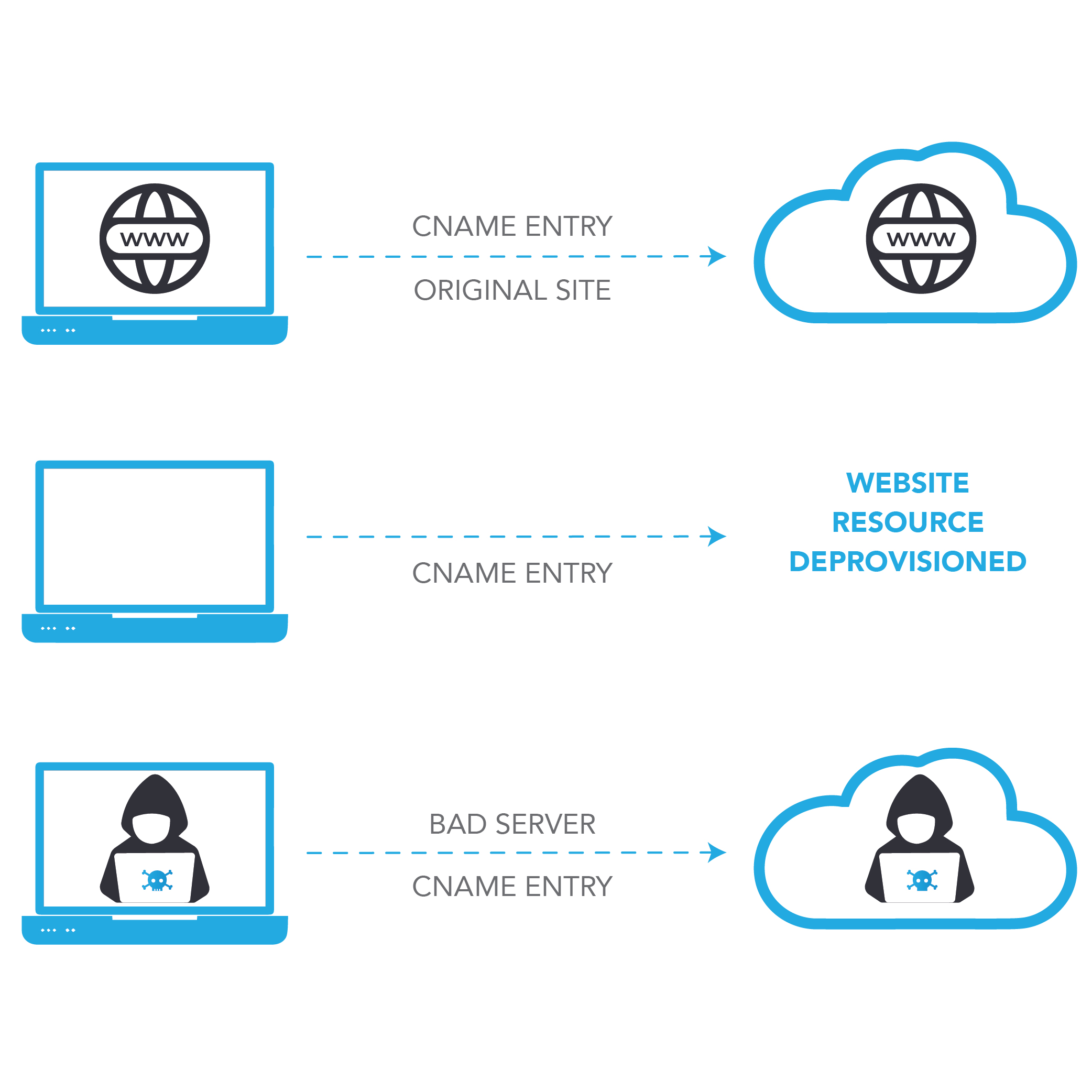
This is a real and present danger for millions of web users and Keytos is taking the initiative to drive awareness and urge sites to rectify this critical issue. Unfortunately, since this attack requires more work to exfiltrate data from users (such as creating a phishing campaign) and is not considered as bad as a full data breach in the eyes of businesses, most organizations (including federal and local governments) ignored the warning from Keytos researchers raising the alarm. One government IT administrator even told our researchers, “It is too much work to even remove the DNS entry and it is not my problem so I would not do all the paperwork for getting one domain fixed.”
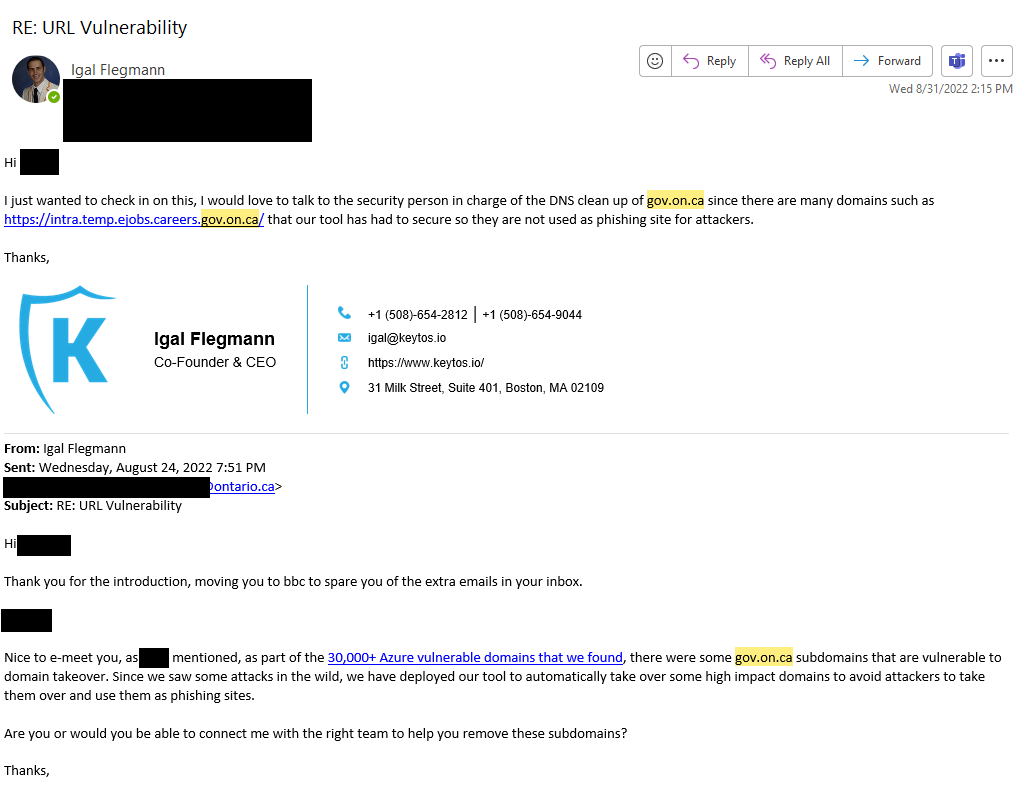
You can currently see a subdomain takeover in action here, where the Keytos team have created a dummy site to protect the Canadian government since no action has been taken to protect this subdomain: https://intra.temp.ejobs.careers.gov.on.ca/.
While this is a known problem in the cyber security industry with many researchers publishing smaller-scale findings on subdomain takeovers, this has not been taken seriously by cloud providers due to the false assumption that vulnerable subdomains are always hard to find, and therefore unlikely to be at real risk. Keytos now has an easy and automated way of checking the DNS entries to find vulnerable sites, and we can see that hackers have had access to tens of thousands of legitimate subdomains as a result of provider complacency.
Since there are billions of sites, it would be impossible for an organization to efficiently scan all sites to find vulnerable domains, Keytos researchers were able to automate the finding on domains by expanding our EZMonitor tool with an automated scanner that:
-
Uses certificate transparency logs to find the CAs (Certificate Authorities) Azure uses to issue certificates for Azure hosted websites. In order to be trusted by browsers, all certificates issued in the world must be added to certificate transparency logs we use this list to find which certificate authorities have issued known Azure hosted sites, helping us narrow down how many domains we have to check further.
-
Scans all certificate transparency logs for those specific Certificate Authorities, and checks if the site is still working. When a certificate is found to be issued by one of the CAs used by Azure, we further examine that domain by checking if the site is still working. This helps us narrow the search to avoid being rate limited by DNS servers.
-
If the subdomain is still pointed at a resource but the site is not operational, our system checks if the site is being pointed to Azure. Now that we have verified that the site is not operational, we check if the DNS entry is pointing to an Azure resource.
-
If the site DNS is pointed to Azure, EZMonitor checks if that Azure resource is available, if it is, this site is a vulnerable site and is added to our database of vulnerable Azure domains. This smart checking allowed EZMonitor to find over 30,000 vulnerable domains in its first month (and thousands a month ever since).
Vulnerability by the Numbers

As the image above shows, the large number of vulnerable domains is just scratching the surface of the problem. Microsoft has over 480,000 organizations, including 85% of the fortune 500 companies. To help solve this problem at the root, we contacted Microsoft to try to solve the problem and prevent organizations to be vulnerable to this attack.
How Major Organizations Have - and Have Not - Responded
When Keytos first approached Microsoft last year, Microsoft told the Keytos research team that they were working on the issue and would have some fixes soon. In the meantime, Keytos helped Microsoft remove over 700 of their own vulnerable domains. Unfortunately, when Microsoft released their fixes, they did not address the core of the problem, leaving thousands of organizations vulnerable.
- - Microsoft released Defender for App Service Dangling DNS detection. However, this only cover one of the many services vulnerable to this attack.
- - Microsoft also added an extra domain validation needed to add a custom domain to a web application, while this prevents attacks on web applications, it leaves vulnerable the most popular services such as traffic manager, Azure Kubernetes Service, and Azure Public IPs.
How Organizations That Were Notified Responded
As the figures above show, most organizations did not take the threat seriously. Most of them, ignoring our approaching them all together, others quickly removed the one DNS entry without looking at the root cause which enables multiple recurrences of this issue. You can read in more detail in one of our researchers’ blogs on how hard it was trying to get organizations to listen to security researchers.
Implications and Attack Scenarios
If an attacker takes over a real subdomain, they can steal user credentials, use your reputation to give legitimacy to false information, and trick your customers into downloading malware. In Q4 2022 alone, the Anti-Phishing Working Group detected 1,350,037 phishing attacks - a new record worst for phishing worldwide. Vulnerable subdomains make life very easy for the cyber criminals behind these types of attacks.
Let us look more closely at the attack scenarios that most of these organizations were missing.
Theft of Login Credentials
As shown in the video at the beginning of this blog, an attacker can create a phishing campaign that will fool your best trained users since it is a real subdomain so it would pass all the tests that we teach end users to do before trusting a site. As well as some password managers will automatically fill in the user password so even before the user realizes that it is a phishing site, the attacker might have already stolen the password.
Giving Legitimacy to False Information
Since this is coming from your domain, attackers can use it to give legitimacy to information on this page, as well as to give SEO (Search Engine Optimization) legitimacy to fraudulent sites by linking from highly reputable sites.
Get Users to Download Malware
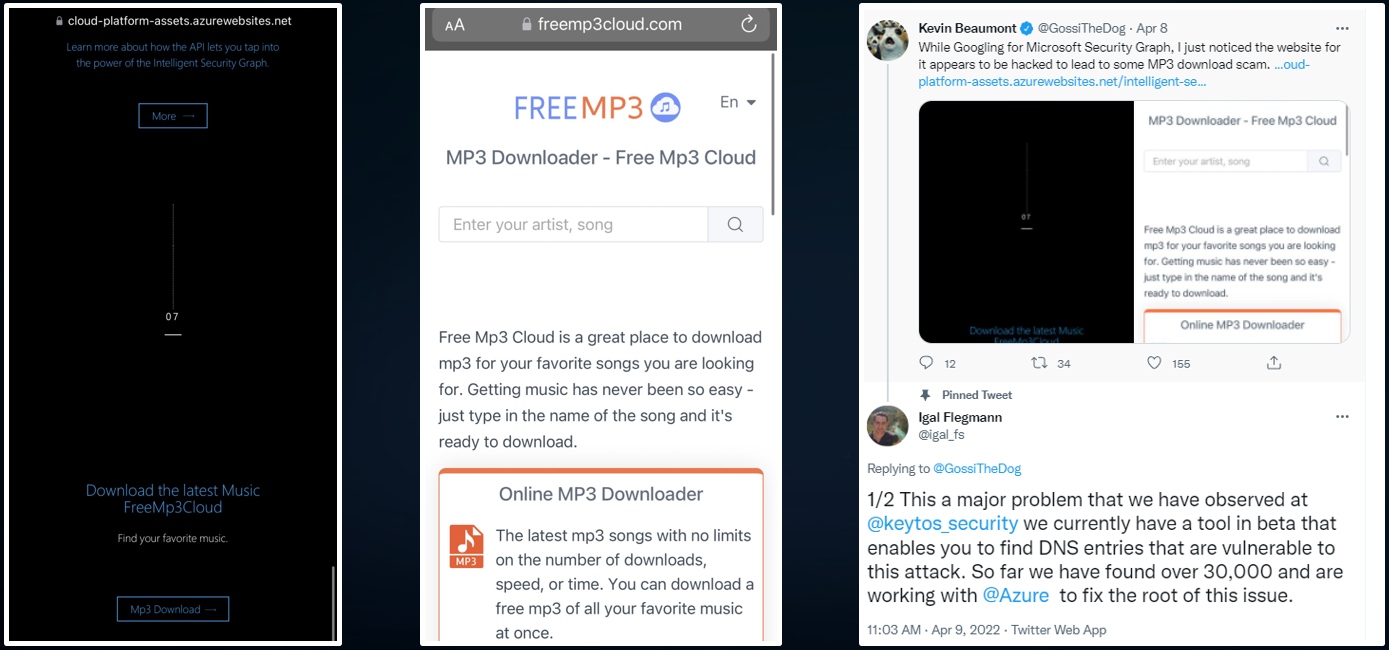
Fortunately, the most common attack we have seen in the wild, is hackers using these sites to put tacky websites with download buttons to obvious malware. Such as this image below from a Microsoft site that was discovered by Kevin Beaumont. Now imagine that instead of “Free MP3 player” they would have put an executable named “Microsoft Graph Explorer”.
How to Check if Your Site is Affected
As a responsible member of the cyber security community, we have made the check for vulnerable URLs completely FREE for anyone. Just go to the EZMonitor portal and enter your domain and we will disclose if we have found any vulnerable subdomains (we will not disclose the actual subdomains without first validating domain ownership).
Staying Protected
As a User
Unfortunately, as end users there is nothing, we can do to protect ourselves from these types of attacks, however, we can demand companies to take this more seriously.
For Site Owners
There are many actions that must be taken to prevent this type of attacks.
-
Keep track of all your subdomains using a Certificate Transparency monitoring solution, and ensure you are deleting any dangling DNS. This must be automated and cannot be reliant on process, since humans make mistakes.
-
Protect your domains from certificate unauthorized issuance outside the CAs you use with CAA records. Out of the thousands of domains we inspected, only two organizations (FedEx, and Lego land) had CAA records that prevented attackers from issuing certificates for their domains.
-
Take any security disclosures seriously. Researchers will go out of their way to let you know that you have a problem before an attacker finds it, and disclosures present you with an opportunity to ask questions and get help in taking the most effective action at speed.
Glossary
DNS Entry A DNS (Domain Name System) entry is a record in a DNS server that links a domain name to an IP address. This allows internet users to access websites by typing in the domain name instead of the numerical IP address.
TLS/SSL Certificates A TLS (Transport Layer Security) or SSL (Secure Sockets Layer) certificate is a digital document that provides authentication for a website and enables an encrypted connection. It verifies that a secure web page (using HTTPS) is properly encrypted and that all information passed between a user and the site is private.
CAA Record A CAA (Certificate Authority Authorization) record is a type of DNS record that allows a domain name holder to specify which Certificate Authorities (CAs) are allowed to issue certificates for their domain. This helps to prevent unauthorized issuance of TLS/SSL certificates for a domain.
Certificate Transparency Logs Certificate Transparency Logs are public records that contain information about all the digital certificates that have been issued by a Certificate Authority (CA). They are part of a system known as Certificate Transparency (CT), which aims to detect and prevent fraudulent and mistakenly issued SSL/TLS certificates, thereby enhancing the security of the internet.