
What is the Chicken and Egg Problem for Passwordless Authentication?
The Chicken and Egg Problem for Passwordless Authentication
So, you’re trying to go passwordless to avoid all the problems associated with passwords, but you can’t stop thinking to yourself, “How on Earth do you create a passwordless identity without first having a password?” You’re not alone! We consider this the cybersecurity iteration of “The Chicken and Egg” conundrum. Your next thoughts probably gravitate towards, “Shouldn’t someone like Microsoft have figured this out already?” Well, they haven’t…unless you consider TAP solving the problem (pro tip: a temporary password is just as vulnerable as a “regular” password). Remember, once you go passwordless, attackers will try to attack the weakest part on your identity story, which is usually the onboarding or password reset. Anyway, take a look at the screenshot below for my inspiration in writing this post…
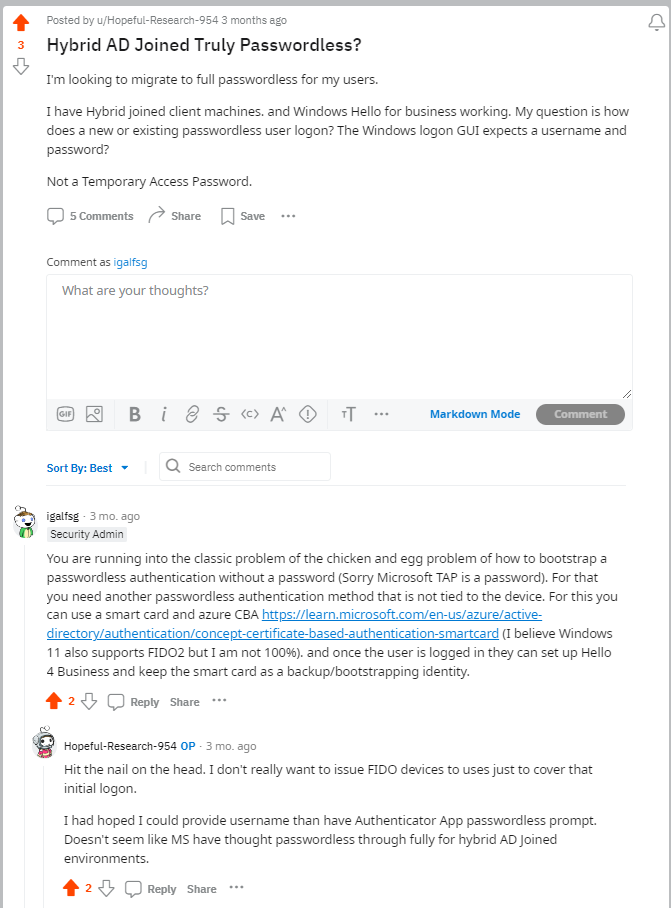
So, let’s talk about the problem and then I will offer some solutions on how you can onboard new users to Entra ID without using TAP.
How to Onboard Passwordless Users to Entra ID (Azure AD) the Microsoft Way
Microsoft has been pushing passwordless for a while (I mean, I was in their passwordless team in 2017, so it has been a while!). When they speak of passwordless, they talk about how it is more secure, improves user experience, and how you can use it everywhere; however, they rarely talk about the onboarding process. Why? Because they don’t have a good solution.
They did come up with TAP to help onboard to FIDO2 and said that that one-time password is multifactor. Fun fact: When I asked the PM in charge of that project of why TAP was considered MFA (since it is just a password) she responded, “It is MFA because we say it is MFA!” So, if you also don’t consider that to be an acceptable response, let’s talk about the options out there.
What Passwordless Authentication Methods are There?
Ok so if TAP is not an option, let’s talk about the other passwordless methods, see their onboarding options, and go from there.
Windows Hello For Business
The first one that comes to mind is Windows hello for business, this uses the TPM on your computer to store the private key making it almost as secure as having an external key such as a YubiKey, with the added benefit of not having to pay for an external key.
Onboarding Credentials for Windows Hello For Business
As the name implies, Windows Hello For Business is attached to Windows, meaning that when you get a new PC you cannot use your existing Windows Hello For Business on another machine to authenticate to the new machine, the options you have are:
- - TAP
- - FIDO2
- - Smartcard
- - Microsoft Authenticator App (if it is not during OOBE, but you still need one of the first three for OOBE)
FIDO2 Authentication
The next authentication method that comes to mind (due to its amazing marketing within the cybersecurity community) is FIDO2 (Passkeys are also a variant of FIDO2). FIDO2 keys are popular since they are one of the passwordless authentication methods that are considered phishing resistant since the key never leaves the device, making it almost impossible for attackers to phish your credentials. The great thing about FIDO2 is that it can be used to onboard to Windows Hello For Business. What we do internally at Keytos is we create a FIDO2 key, and then use that to create our Windows Hello For Business credentials, making WH4B our main authentication method, and then the hardware key a backup method and bootstrapping device for when we get a new machine.
Onboarding Options for FIDO2
- - Any existing MFA credential registered in Entra ID
You might see a trend here: you still need an MFA to get the FIDO2 credential, so you can do it the Microsoft way and issue them a TAP, or you can use a Credential Management System such as EZCMS to enable self-service FIDO2 creation using a government ID and face scan, breaking the chicken and egg problem while still protecting your onboarding process with Multi-factor authentication (Factor 1 something you have (your government ID), Factor 2 something you are (your face)).
Smart Card Authentication
Smartcard authentication is the oldest passwordless authentication method; however, it has gotten a bad reputation over the last few years because it used to be very hard to setup. With a Microsoft-only shop, you needed over 10 servers to enable smartcard onboarding and authentication; however, over the past years with the introduction of Entra ID CBA and azure based Certificate Authorities smartcard authentication can be setup in less than an hour without a single server, all by managed servers in the cloud.
Onboarding Credentials for Smartcard Authentication
If you are using the legacy smartcard authentication process with your on-premises infrastructure, you require an existing AD account.
If you are using a modern smartcard onboarding tool such as EZCMS, you only need Government ID and Face, or even an existing account from another tenant (this is very popular with our government customers where they use an existing identity to create their other identities for other tenants).
Final Thoughts on the Chicken and Egg Problem for Passwordless
Creating a fully passwordless onboarding experience requires many moving things, and as the MGM hack of 2023 showed us, protecting the user onboarding process is one of the most important parts of the identity lifecycle. My personal recommendation is using a hardware key as your main onboarding method and then using other methods such as Windows Hello For Business for your day-to-day authentication, allowing you to have full passwordless authentication while also having a backup method for onboarding new devices.


