
What is FIDO2? What Does FIDO2 Do?
What is FIDO2?
FIDO stands for “Fast Identity Online” and it enables users to authenticate on online platforms using their devices such as smartphones or laptops with biometric features, or USB security keys, in both mobile and desktop settings.
Developed by the FIDO Alliance (a coalition of technology, finance, and government entities), FIDO is a set of technical guidelines. This group was formed to phase out password usage on websites and apps and to refine the authentication methods – after all, we know that passwords are the least safe form of authentication out there.
The FIDO2 standard, an evolution of FIDO, offers improved security and user convenience by removing the reliance on passwords. This results in a more secure, user-friendly, and modern method of verification, reducing the risk of fraud in online interactions. Furthermore, FIDO2 extends its capabilities to web-based authentication.
What are the FIDO2 Specification Protocols?
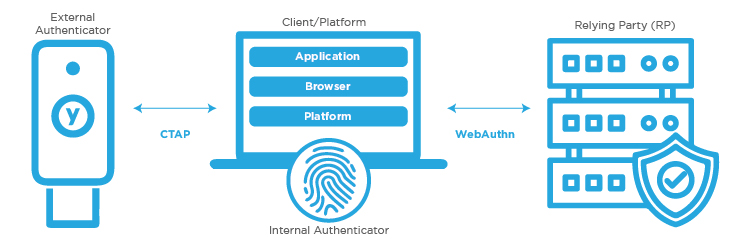
The FIDO2 standard consists of two distinct protocols: the W3C WebAuthn protocol and the FIDO Alliance CTAP (Client-to-Authenticator Protocol).
The W3C WebAuthn Protocol
The W3C WebAuthn protocol is responsible for outlining the interaction between the web browser (the user agent) and the FIDO2 server (the relying party).
The FIDO Alliance CTAP
The FIDO Alliance CTAP specifies how the browser (the user agent) communicates with the user’s authenticating device (the authenticator).
What Does FIDO2 Do?
FIDO2’s purpose is straightforward: it allows us to leverage biometric data stored on our computers or mobile devices (such as fingerprint scanners, touch ID, face ID, external tokens, etc.) for accessing websites and applications.
This system authenticates users locally on a device that has already been set up, utilizing biometrics as part of a 2FA process. Essentially, this simplifies the user experience by eliminating the need to remember those pesky usernames and passwords.
Consequently, this enhances the security of the authentication process and provides users with a more user-friendly method of accessing platforms.
How FIDO2 Works
FIDO2 consists of two main processes: the registration process and the authentication process. Let’s take a closer look at the two:
The Registration Process in FIDO2
The registration process for FIDO2 keys is fairly straightforward. It involves registering the public key of the FIDO2 device in the identity provider and then assigning it to the user. This allows the identity provider to authenticate the user without ever needing to access the private key.
The Authentication Process in FIDO2
For future logins, authentication requires the private key, which must be activated by the user. When the unauthenticated user accesses the company website from a browser, they are directed to the login page. Alongside the usual username/password method, there’s an option to log in using the FIDO2 authentication. If the user and device are already registered, a cryptographic key exchange occurs between the server and browser, enabling authentication through the user’s chosen local mechanism (such as hardware key, touch ID or face ID on an iPhone, touch ID on a Mac, or fingerprint, face, or iris sensors on an Android).
What Are the Advantages of FIDO2?
The FIDO2 standard offers several advantages, most notably security, ease of use, privacy protection, and scalability.
Security: FIDO2 employs a cryptographic key system (private and public keys) that is accessible only through the registered device. Each website receives unique cryptographic login credentials, which are confined to the user’s device and are never stored on any server. This approach effectively guards against phishing, password theft, and replay attacks.
Ease of Use: Users can access their cryptographic credentials using their device’s inherent security features, like fingerprint sensors or facial recognition, as well as external devices like USB keys or Bluetooth bracelets.
Privacy Protection: The cryptographic keys are distinct for each website, preventing the tracking of users across different websites. Furthermore, biometric data is processed only on the user’s device, eliminating risks associated with centralized storage of biometric information.
Scalability: FIDO2’s decentralized authentication model ensures high scalability. Web applications authenticate users through a standardized JavaScript API, which is compatible with most contemporary web browsers.
Are Passkeys FIDO2?
The short answer: yes, passkeys are FIDO2 keys. The FIDO Alliance proudly boasts on their website about how FIDO2 keys now support single-device passkeys, and deservedly so! In fact, to quote the FIDO Alliance themselves, “any passwordless FIDO credential is a passkey,” and FIDO2 keys absolutely fall into that description. Passkeys and FIDO2 keys employ the same basic principles of signing in using cryptographic keys as opposed to the passé username and password combination.
We Recommend Using FIDO2 and Smartcard Authentication to Become Unphishable!
At Keytos, we strongly recommend using both FIDO2 and smartcard authentication throughout your organization to make you as secure as humanly possible. If you want to learn more about how Keytos and EZCMS can help take your organization’s security posture to the next level, feel free to schedule a FREE consultation with one of our ex-Microsoft identity experts today!


