How to Add ACME to ADCS
ACME Is Now Available for Windows ADCS (Active Directory Certificate Services) with EZCA
Over the past few months, we have been doing hundreds of SSL health assessments to companies around the world. Unfortunately, the results usually indicate that the companies still have a lot of work to do to meet our security requirements across all their domains. However, there was one company that after doing the scan got an “A” grade in most of their domains, I had to run the scan again because I could not believe what I was seeing. During our meeting where we were going over the results with their IT team I told them that I was impressed by their results and that they were the best company we have ever scanned. Their response was the biggest surprise I got, instead of them talking about how they have invested a lot of time into ensuring that their SSL Certificates are up to date and have a full team looking at their certificate health, they just looked at each other and said: “I guess the free certificate thing we moved to a few months ago was a good decision.” This shows us that the best way to secure our endpoints is not throwing a bunch of experts and manually managing the security, but to remove the human from the equation and automate the security.
The Technology Behind the ACME Magic
Well after reading that you are wondering what is this new technology this company used to automate their certificate issuance and the answer to that is they were issuing Let’s Encrypt certificates using the ACME protocol this protocol has been widely adopted by the community and there are plugins for most web hosting options (such as Kubernetes, IIS, Apache web servers, AWS, Azure, and more) to automatically issue and rotate certificates using ACME. Allowing DevOps engineers to set and forget their SSL certificates, fully removing the human out of the equation and preventing the costly SSL related outages that 80% of organizations have experienced in the last 2 years.
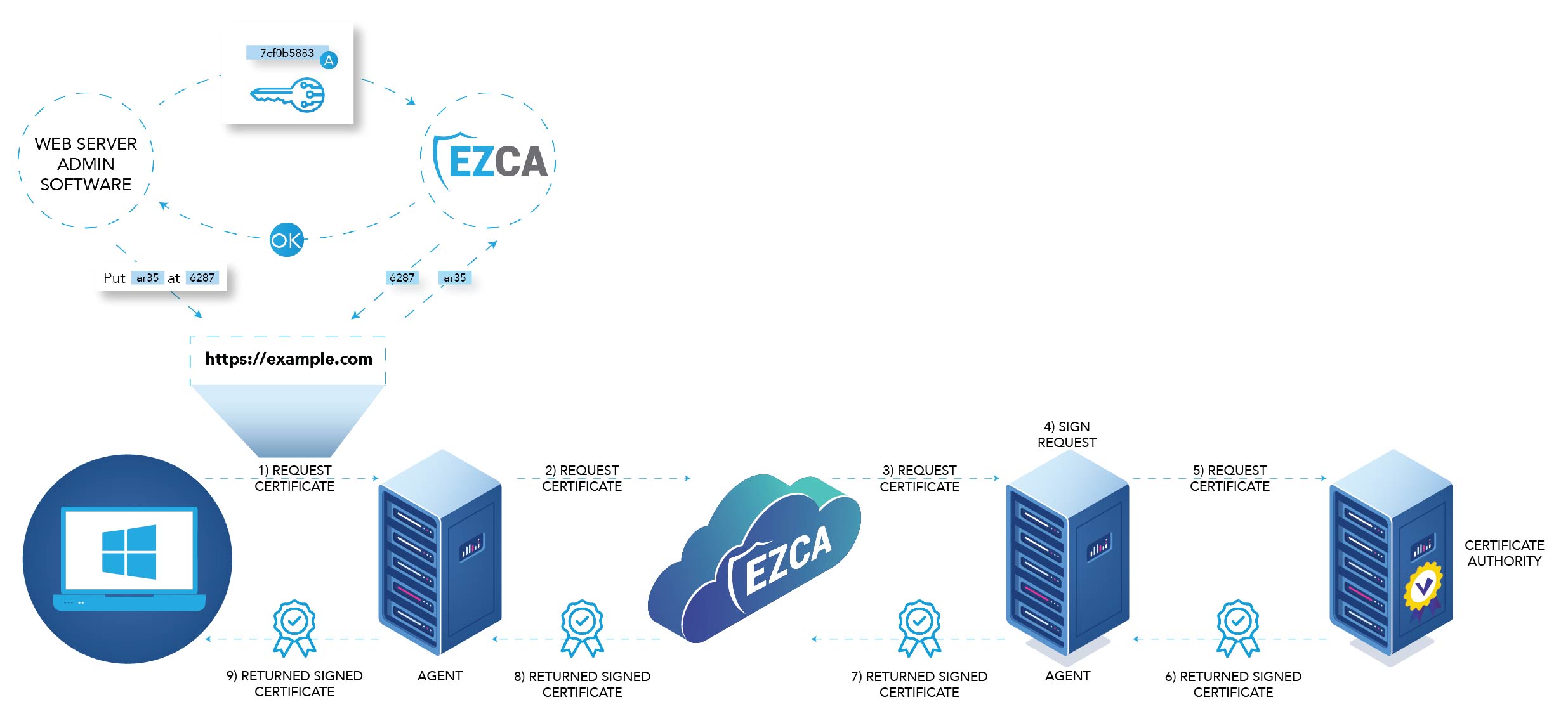
ACME Support for Private Certificates
ACME’s popularity has exponentially risen over the past 5 years and currently is used by over 260 million websites around the world to issue their SSL certificates. However, this amazing technology is not currently supported by Microsoft’s PKI offering ADCS, meaning that engineers still need to manually manage their internal SSL certificates. Costing companies millions of dollars on wasted engineering hours and outages.
Our EZCA tool enables you to extend your existing PKI to issue certificates with the ACME protocol while also giving you full visibility into all your organization’s certificates. Allowing your engineers to automate themselves out of the certificate management tasks that get on the way of their main job functions while giving your security team full visibility into all your organization’s certificates allowing them to find issues before they become a larger problem.
Using ACME with EZCA
EZCA offers an easy way to set up a secure ACME CA in minutes. You can modernize your ADCS CA by connecting to EZCA Once your CA is created, follow these steps to enable ACME certificate issuance in your private network.
Connecting Your Clients to Your New ACME CA
Once you have created your ACME CA, you are ready to start creating ACME Certificates. Since EZCA works with the native ACME protocol, any ACME client can request certificates from EZCA. See ACME Issuance Samples with EZCA here.
Common Challenges and Pitfalls When Setting Up a Private CA with ACME Support
Setting up a private CA with ACME support can be a complex process, and there are several challenges and pitfalls that you may encounter along the way. Here are some common issues to be aware of, and tips for overcoming them:
-
Ensuring secure and reliable communication between the ACME client and server: One of the key challenges when setting up a private ACME CA is ensuring that the server can validate domains in your private network. This requires careful configuration of network settings, firewalls, and other security measures.
-
Managing certificate revocation and renewal: With ACME, certificates are automatically renewed when they approach their expiration date. However, if a certificate is compromised or otherwise needs to be revoked, you will need to take steps to ensure that it is no longer trusted by clients. This requires careful management of certificate revocation lists (CRLs) and other aspects of the certificate lifecycle.
-
Ensuring compliance with regulatory and industry standards: Depending on your industry and location, you may be subject to various regulatory and industry standards that affect how you manage your CA and issue certificates. It is important to ensure that your ACME CA is set up in a way that meets these requirements, to avoid potential compliance issues.
To help overcome these challenges and ensure that your ACME CA is set up properly, it is recommended to work with a trusted provider like EZCA, who has experience in helping organizations set up and manage secure and compliant CAs.
To learn more about how you can automate your certificate lifecycle schedule a free PKI consultation with one of our experts today!


