
Let’s start at square one. Certificate Transparency (CT) is an open framework to facilitate the monitoring and issuance of SSL/TLS certificates. When the concept was conceived, its primary purpose was to prevent the misappropriation and misuse of certificates. It also provides a way for domain owners to monitor and audit certificates issued for their domains. Certificate Transparency achieves this through the use of publicly accessible logs called Certificate Transparency (CT) Logs. The log servers are maintained to be highly available and resilient, often built with georedundancies to ensure uptime and reliability.
In the past, there were occurrences where certificates were miscreated for man in the middle attacks. These certificates were created either by impersonating the requesting party and fooling a certificate authority; for example, with subdomain takeover or with more elaborated attacks such as hacking a certificate authority. These threads can be mitigated with a CAA as well as monitoring the issuance of certificates with certificate transparency logs.
Public Chronicle: When a certificate is created, it’s like making an entry in this massive, cryptographically protected, communal diary – available for all to see, yet immutable.
Authentication Seal: Post entry, the log grants a verification, known as a Signed Certificate Timestamp (SCT). This SCT acts as a seal, confirming the certificate’s inclusion and consistent tracking.
For All Eyes: CT logs are a public domain. From tech giants to individual netizens, everyone can access and scrutinize these records, ensuring accountability.
Log Servers: The custodians of our communal notebook. They uphold the CT logs and ensure each certificate gets its proper acknowledgment.
Monitors: The vigilant observers. Their role is to continuously oversee the logs, ensuring no dubious certificates slip in.
Auditors: Think of them as the quality-check experts. Their task is to periodically assess the logs, ensuring their integrity and authenticity.
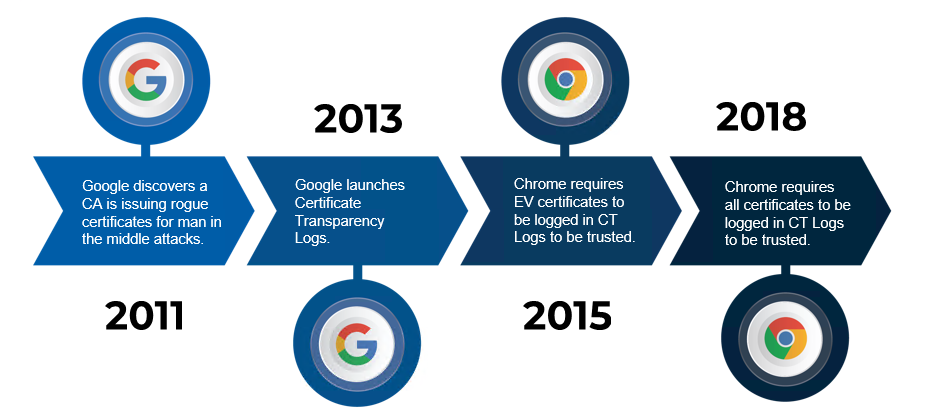
As with many security tools, the origin of certificate transparency logs can be traced back to a cyberattack. The attack that can be credited with the creation of CT logs is the 2011 attack on DigiNotar where attackers hacked a publicly trusted Certificate Authority and created SSL certificates impersonating Google, these certificates were then used for man-in-the-middle attacks against google users.
After Google responded to this attack, they realized a gap in the cyber security offered by SSL certificates. The blind trust given to the Certificate Authorities in the trusted root store program did not consider what happened if one of those Certificate Authorities was hacked. To fix this gap, Google came up with certificate transparency logs, cryptographic safe public logs where each certificate that is issued must be logged to be trusted by the browser. Now that all certificates are logged in these logs, organizations like Google can now monitor all certificates issued for their domains and make sure that they were created by their organization.
CT log monitoring is vital because it ensures transparency in the issuance of SSL/TLS certificates, preventing unauthorized or malicious certificates from going unnoticed. By continuously overseeing these logs, organizations can promptly detect and address potential security breaches stemming from mis-issued certificates. This active surveillance boosts users’ trust, knowing that their connections are authenticated and secure. Additionally, certificate authorities are held accountable, which assists in maintaining the integrity of the entire web security ecosystem.
Since their creation in 2013, and their enforcement in 2018, many organizations such as the United States Department of Homeland Security recommend using certificate transparency log monitors such as EZMonitor to monitor certificate transparency logs and detect attacks before your users are affected. While such a sophisticated attack might not be your number 1 priority, these monitors usually offer other SSL monitoring features such as (view the full list here):
1) SSL Certificate expiry notification.
2) Similar domain being used for phishing.
3) Monitor for new subdomains created.
4) Alert on domains containing your domain. (This one is common on phishing campaigns where the attacker might use your domain as a subdomain. For example, yourdomain.com.attacker.com)
5) Invalid certificate installed.
6) CT Logs also helped us find over 30,000 vulnerable domains to domain takeover.
7) CAA (Certification Authority Authorization) Mismatch.
And more!
If you want to learn more about how certificate transparency logs can help you secure your organization and prevent your next outage, check out EZMonitor! Hosted architecture gives you full visibility into all your certificates in one convenient dashboard, enabling your team to start monitoring your SSL health in minutes. Receive auto-generated alerts by: Email, SIEM integration, or by calling our APIs. Want to speak with one of our Security experts? Book a FREE call TODAY to learn more about how monitoring certificates can help safeguard your organization!