
What’s Going on with the KB5014754 Update?
Remember that blog we wrote back in the beginning June about the KB5014754 update when we were trying to make everyone aware for the impending doom? NO? Seriously? Alright, well, have you happened to see Sir Tificate’s explainer video about the subject?
Still not ringing a bell? Frankly, we don’t blame you. These KB updates are so common and usually inconsequential; however, being that this one applies to your PKI, here’s the TL;DR to get you up to speed on why everyone is saying about the KB5014754 update.
KB5014754 Updated Timeline
June 2022: Microsoft released the security update KB5014754 to address an elevation of privilege vulnerability that can occur when the Kerberos Distribution Center (KDC) is servicing a certificate-based authentication request. Once this is applied, the new certificates that are the certificate information is populated from AD (Active Directory) will automatically have the new strong mapping.
April 11, 2023: After this patch, the following events will start showing for non-compliant certificates:
November 14, 2023 (This has been now pushed to 2024): Full Enforcement mode will start on this date or later. In this mode, if a certificate fails the strong (secure) mapping criteria, authentication will be denied.
We first heard rumblings of discontent in the PKI community on Reddit about 9 months ago when things started going sideways. Here’s a quick glimpse into what was said on the original post titled “Strong Certificate Mapping w/ SCEP”:
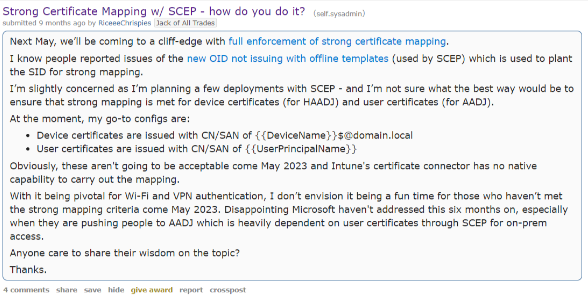
…I’m writing this on the morning of September 18th, 2023 (SHOUTS OUT to my Big Brother Will over at Verizon!). We are now roughly 2 months out from “Full Enforcement.” As I’m sure you’ll be absolutely shocked to know, there’s still a great deal of uncertainty in the industry as to when Microsoft will actually enforce anything, the reason for this is, while online templates have been patched, Microsoft has not issued a patch to map offline templates. What does that mean, if you have a template that the user provides the certificate information, for example Intune SCEP, then ADCS will not add the strong mapping into the certificate, and it will break your authentication in November.
To further explain the consequences and impact of this patch, here’s some more color from our fellow Devs and PKI pioneers over in the SysAdmin subreddit are saying:
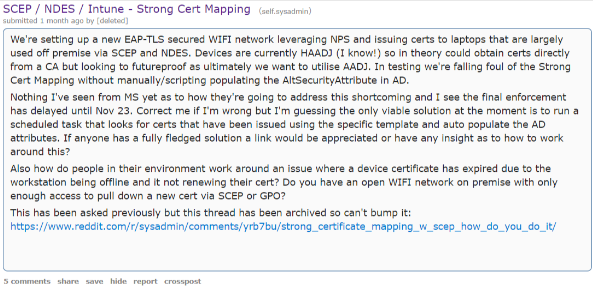
Most notably, this phrase stands out as particularly aggravating about Intune strong SCEP mapping:
“Nothing I’ve seen from MS yet as to how they’re going to address this shortcoming and I see the final enforcement has delayed until Nov 23. Correct me if I’m wrong but I’m guessing the only viable solution at the moment is to run a scheduled task that looks for certs that have been issued using the specific template and auto populate the AD attributes. If anyone has a fully fledged solution a link would be appreciated or have any insight as to how to work around this?”
So, how do we move forward from here with so much uncertainty ahead? Let’s not even try to be subtle about it. You’re going to want to check out EZMonitor, our all-in-one solution for your certificate monitoring needs. You can check it out and purchase directly from Azure or schedule a free consultation with one of our PKI experts today!


