
How to Go Passwordless In Azure with Entra CBA (Certificate Based Authentication)
How to Implement Azure Certificate Based Authentication
Azure certificate-based authentication is the best way to meet executive order 14028 and protect your organization by using passwordless unphishable credentials. Azure certificate-based authentication does not only improve your security but also improves user experience and productivity, with studies showing a 4x authentication speed improvement, and 20%-50% support ticket reduction when using passwordless authentication. In this blog we will walk you through how to set passwordless authentication in Azure with Azure CBA up and start using it in less than an hour (sorry we tried to make it in 10 steps but it was so easy that the most we could do was 9).
What do you need to set up Azure Certificate Based Authentication?
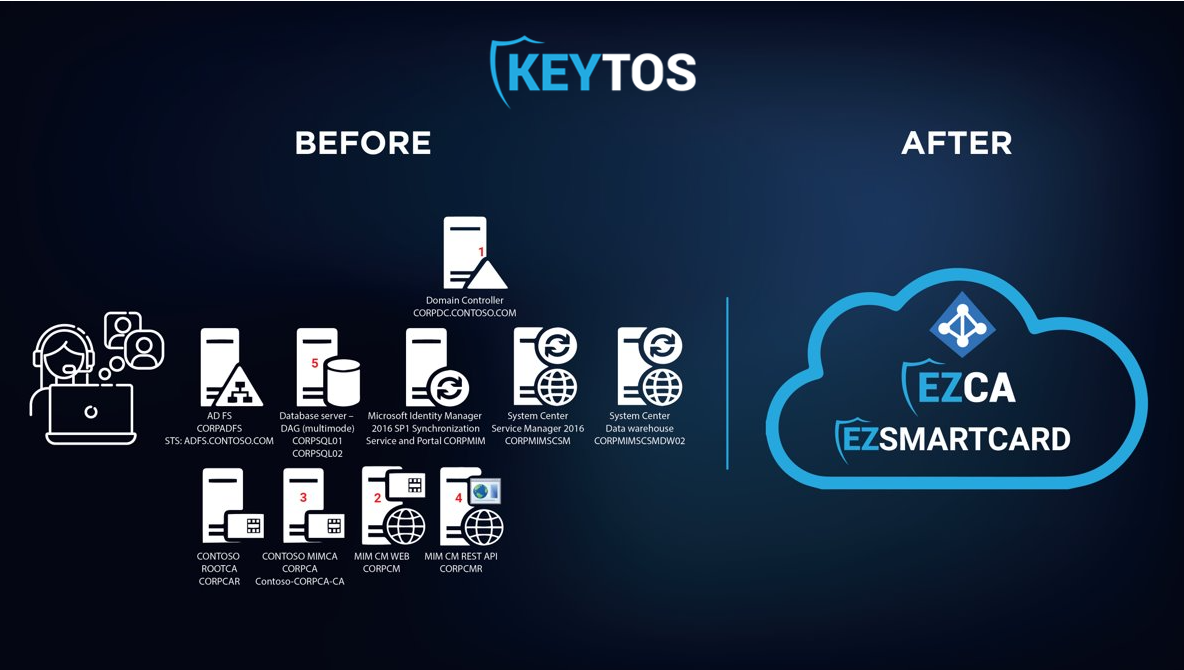
Azure Certificate Based authentication works by using X.509 certificates to authenticate users. X.509 certificates that are issued by a certificate authority that is trusted by Azure AD. This means that you need to have a certificate authority that can issue X.509 certificates to your users, unfortunately Azure does not have a built in certificate authority that can issue certificates to users, and they declare the issuance and distribution of certificates out of scope for Azure CBA. To achieve the certificate enrollment there are two options: using intune scep Note since Intune Certificates are not protected with a pin they are only considered single factor (see more in the Azure CBA section bellow to set Azure CBA for intune as a single factor), or using a smartcard / YubiKey to protect your user certificates. In this blog we will show you how to set up Azure CBA with smart cards and YubiKeys. To enable the smartcard certificate self-enrollment we will use EZCMS our smart card management tool that enables you to manage your smart card inventory, and enable self service smart card onboarding for your users. Thankfully, Azure CBA, EZCA and EZCMS are all Azure based SaaS solutions meaning your team does not have to worry about any infrastructure upkeep.
Step 1 Select your smart card provider
Selecting your smartcard provider is a crucial step in setting up Azure CBA, since the decision will affect the user experience, security, and cost of your Azure CBA deployment. There are several smart card providers in the market, but we recommend using YubiKeys for Azure CBA, for the ease of use, FIDO2 support, and extra attestation and security measure Yubico and Keytos worked together on to achieve the highest level of onboarding security. However, we understand that YubiKeys are not for everyone, so we have also enabled support for PIVKey smartcards allowing you to have a lower cost option for your Azure CBA deployment that can also double as an employee ID (we even help with smartcard printing and distribution). Once you have selected your smart card provider, and have ordered a few for testing, we can setup the rest of the infrastructure.
Step 2 Create an EZCMS instance
To setup EZCMS, first you have to register the EZCMS application in your tenant, this will allow EZCMS to authenticate your users. Once the application is registered, you can go to the Azure Portal and create your EZCMS instance Once the EZCMS instance is created, and your organization settings are set, we are ready to create the Certificate Authority that will issue the smart card certificates.
Step 3 Create Your Azure CBA Certificate Authority
If you already have a Windows ADCS Certificate Authority set up for issuing smart card certificates, you can connect EZCMS to ADCS and start issuing certificates from your ADCS CA. However, if you do not have an existing CA or want to move your infrastructure to the cloud, we recommend using EZCA our cloud based certificate authority that enables you to create secure and compliant HSM backed Certificate Authorities in Azure (Note: The EZCA SmartCard CA must chain up to a Root CA, you can create one in EZCA or chain up to your existing root CA.). Once you have created your Certificate Authorities, we have to upload the certificates to Azure.
Step 4 Upload Certificate Authorities Certificates to Azure
Now that you have created your certificate authorities, it is time to upload your CA certificates as trusted CAs to Azure. To do this we must follow the following steps:
-
Go to the Azure portal as a Global Administrator.
-
Select Azure Active Directory, then in the left-hand side panel select Security.
-
Select Certificate Authorities.
-
Upload the certificate for each CA in your infrastructure (Root and Issuing CAs). Note: make sure to add a publicly accessible CRL url for Azure to validate that the certificates have not been revoked
Step 5 Configure Azure Certificate Based Authentication
After setting up the Certificate Authorities that Azure should trust for user authentication, we need to set up Azure to accept certificate based authentication as an authentication method. To do this we will:
-
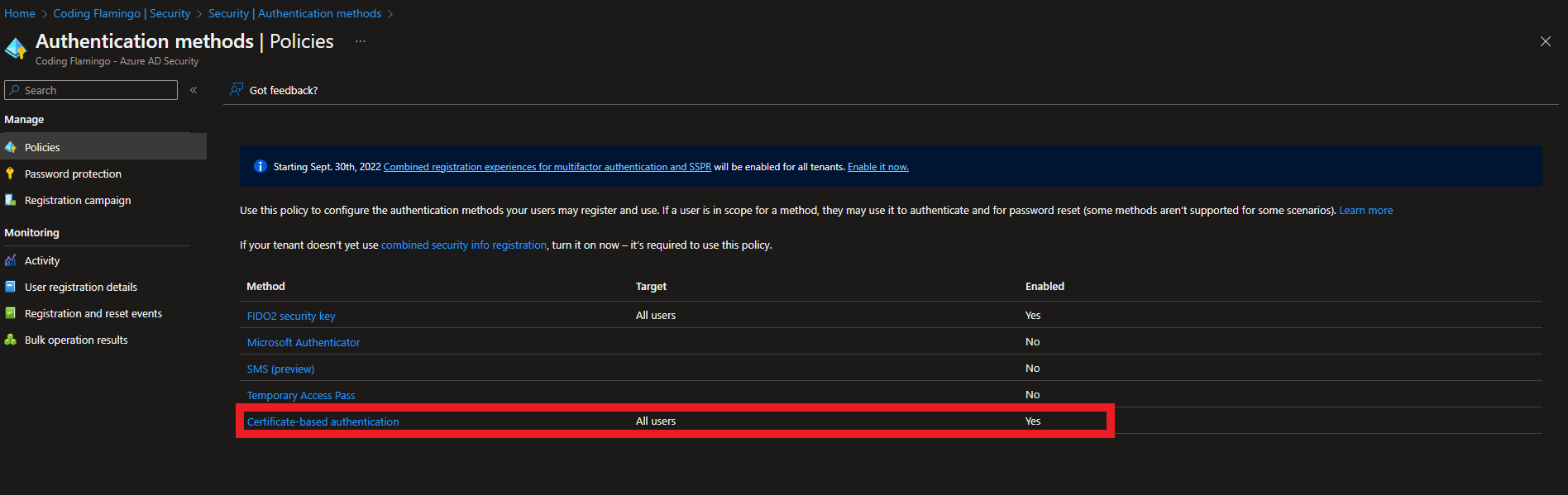
Navigate to Authentication Methods inside the security section.
-
Select Policies on the left hand side.
-
Click on certificate-based authentication.
-
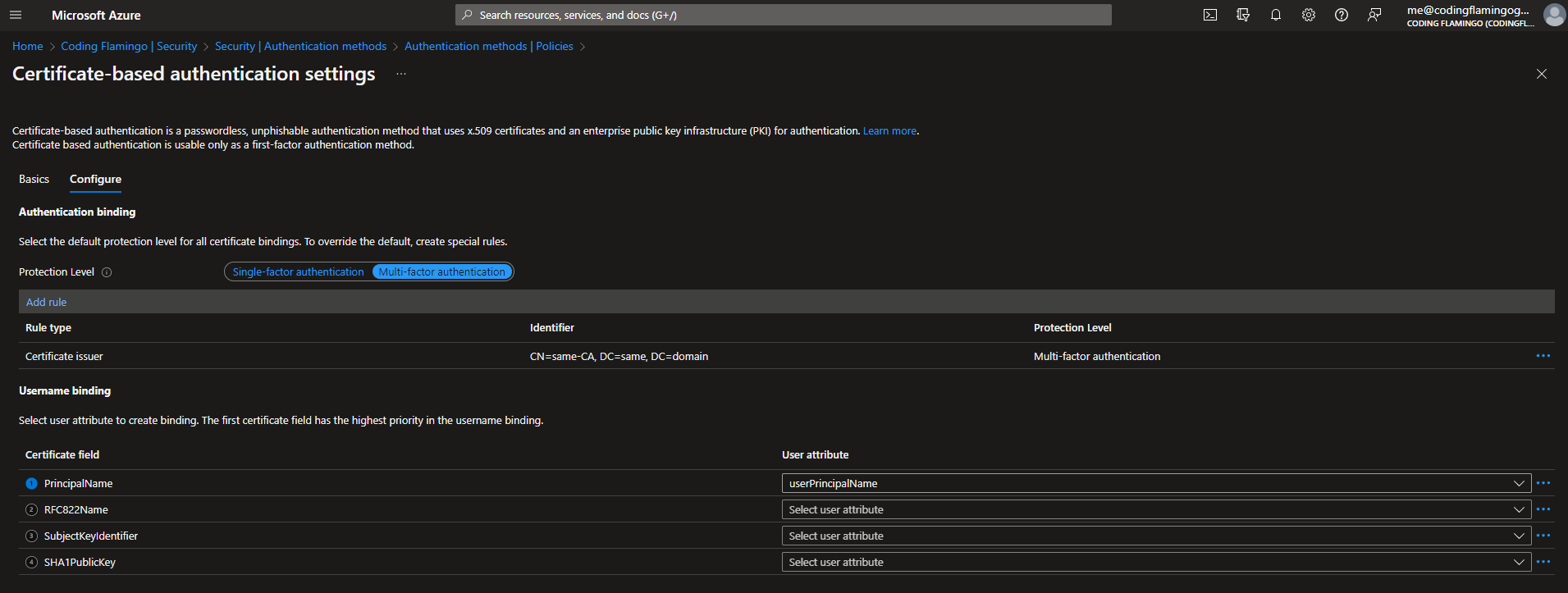
Click on the Configure tab.
-
Select protection level (Azure defaults to Single factor since it doesn’t know if you are just going to use a certificate without a smart card or if you are going to protect that certificate, so if you are going to use smart cards, change to multi-factor authentication).
-
In the rules section set the CAs that can issue user certificates. Note: You can also set a policy ID if you are using that CA for other certificate types but PKI best practices recommend using a dedicated CA for smart card authentication
-
Select the username binding order (this is how the user name is added in the certificate) in this example we are going to use PrincipalName mapping to the user principal name which is what EZCMS defaults to.
-
Click Save
Step 6 Register Your Tenant in EZCMS
EZCMS is designed to be able to onboard users from multiple tenants, so you can use it to onboard users to all your different tenants, for example at Keytos, we follow Azure security best practices and do full tenant isolation for corporate (keytos.io), test identities, and production identities and use EZCMS to onboard all of them. Follow the EZCMS documentation or the video below to register your domain.
Step 7 Add a Test User to EZCMS
The last step before issuing your first smart card is to add a test user to EZCMS and then you can assign a smart card to that user. and then you can issue your first smart card!
Step 8 Test Authentication
Once EZCMS is setup, and you have created your test smart card, you can test the authentication flow by:
-
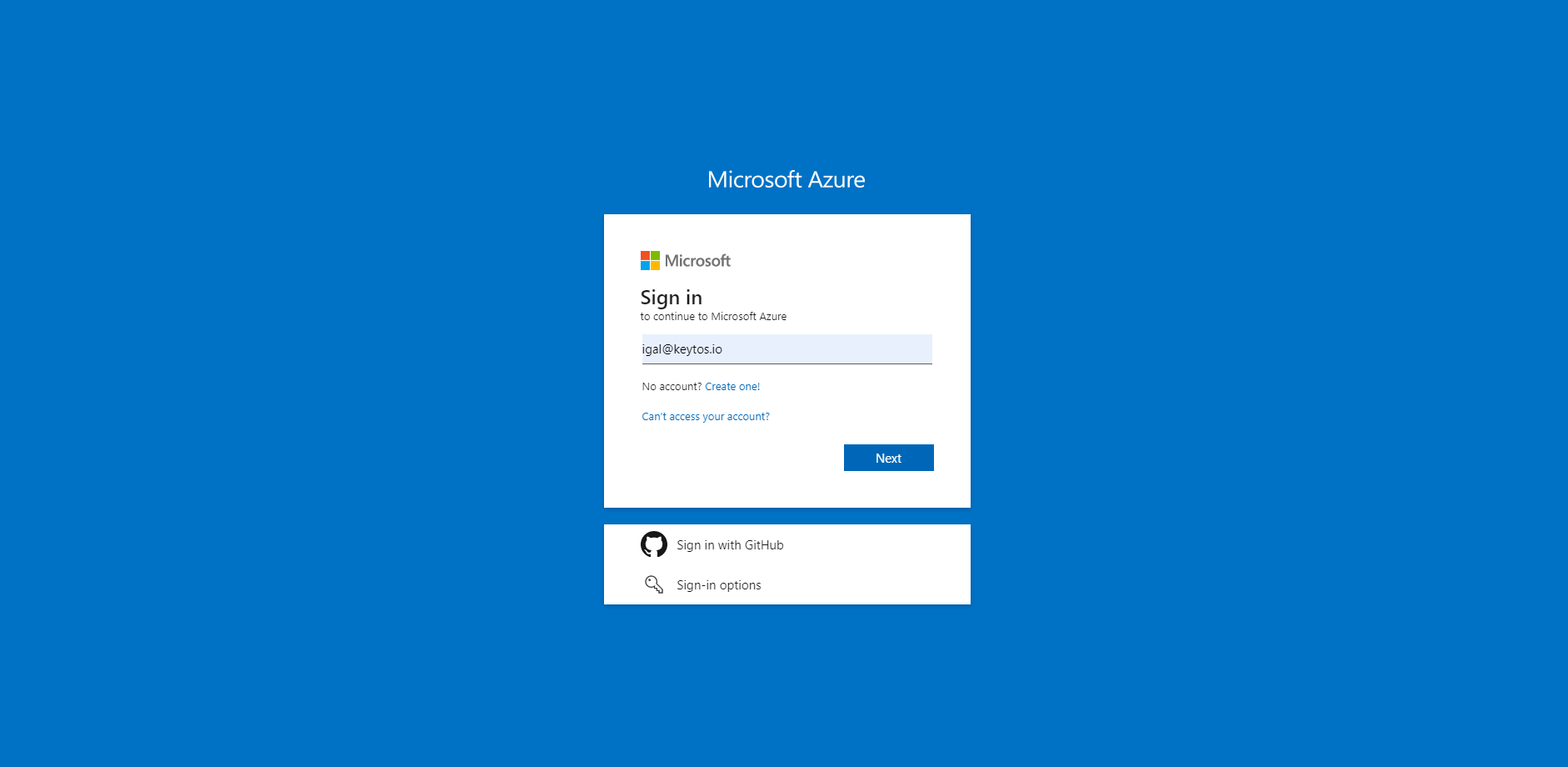
Going to the azure portal in an incognito tab.
-
Entering your username.
-
Select “Use a Certificate or smart card”
-
Select your smart card certificate
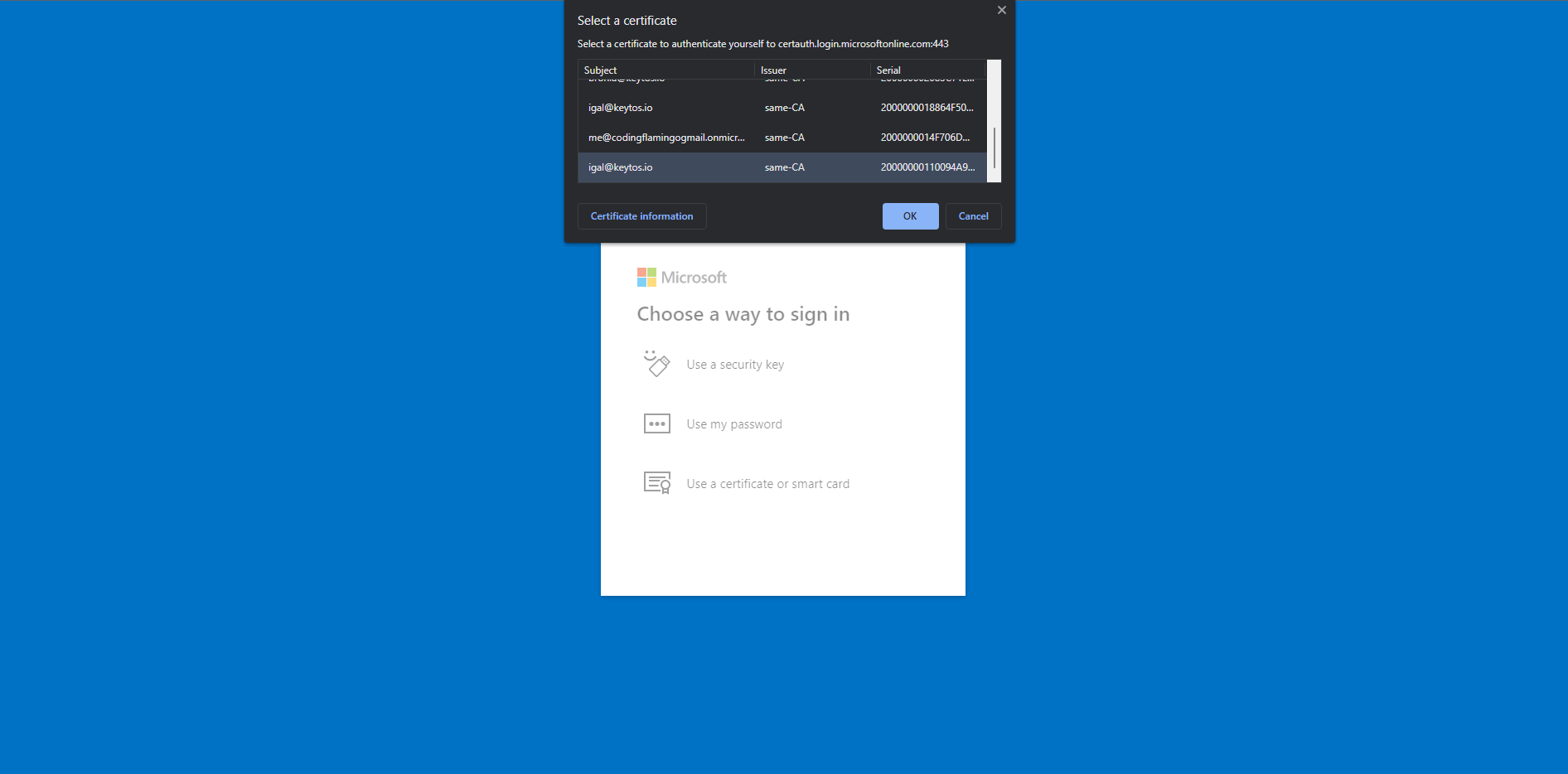
-
Enter your PIN.
-
If using a YubiKey, touch the YubiKey to complete the authentication.
-
You have successfully logged in with you smart card.
Step 9 Start Rollout
Now that you have successfully set up smart card authentication with Azure Certificate Based Authentication, you can start rolling it out to all your users. If you have any questions on how to setup Azure Certificate Based Authentication, book a free identity assessment with our identity experts.


