
What Is KB5014754 and Why it Will Cause Your Next Outage
What Is KB5014754?
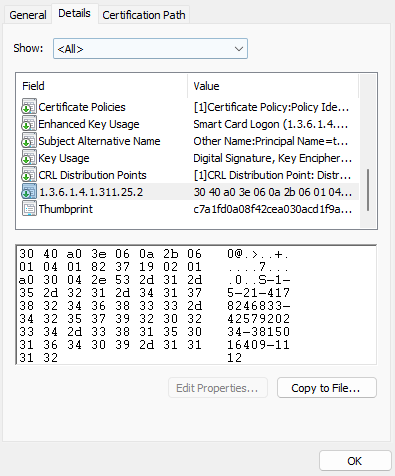
KB5014754 is a Microsoft security patch that was released in June 2022 to squash the CVE-2022-26923 and CVE-2022-26931 bugs. These bugs took advantage of the way certificates are matched in active directory by using the account’s friendly name. Since the $ of computer accounts was ignored, attackers could elevate privileges by creating user accounts and machine accounts that matched their friendly name to impersonate the privilege account. To mitigate this, Microsoft added an extra extension (1.3.6.1.4.1.311.25.2) to certificates that has the account unique SID, creating a better mapping to the account that is intended for.
Important Dates
-
June 2022: Microsoft released the security update KB5014754 to address an elevation of privilege vulnerability that can occur when the Kerberos Distribution Center (KDC) is servicing a certificate-based authentication request. Once this is applied, the new certificates that are the certificate information is populated from AD (Active Directory) will automatically have the new strong mapping.
-
April 11, 2023: After this patch, the following events will start showing for non-compliant certificates:
- - No strong mapping (event ID 39) The certificate has not been mapped explicitly to a domain account, and the certificate did not include the new SID extension.
- - Certificate predates account (event ID 40) A certificate was issued before the user existed in Active Directory, and no explicit mapping could be found.
- - User's SID does not match certificate (event ID 41) A certificate contains the new SID extension, but it does not match the SID of the corresponding user account.
- November 14, 2023 (This has been now pushed to 2024): Full Enforcement mode will start on this date or later. In this mode, if a certificate fails the strong (secure) mapping criteria, authentication will be denied.
How to Prepare for AD Certificate Strong Mapping
The first thing you must do to prepare for AD certificate strong mapping is ensure that all of your Windows servers are patched with the latest security patches. Then, you must get visibility into all the domain certificates to ensure that there are no certificates that will be affected by this patching.
The easiest way to find certificates that will stop working once the new mapping is enforced is to set up new alerts to find the events with IDs: 39, 40, 41. While this will find the certificates that are currently in use, if you do not see these event IDs it does not mean that your domain will not have issues once this is enforced. In complex AD environments, there are many certificates that are not used daily and would not be caught by these events when you scan the logs. We recommend you go through all the domain certificates and ensure that all certificates issued to an AD account - either computer or human - are rotated and have the new mapping. If your environment is small, this might be a painful task, but it is manageable and vital for a smooth mapping process; however, if your environment is at a scale where doing it manually is not feasible or cost efficient, we recommend using an SSL certificate scanning tool like EZMonitor to quickly scan all your networks and ensure that no certificates are being overlooked.
Not All Certificates Will Get Updated Automatically
While earlier we said that ADCS will automatically add this new extension to the new certificates being issued, we mentioned that it will only add it to certificates that it populates the certificate information from AD, so any certificate that the user information is passed in the request (i.e., Intune certificates and other certificates issued by third parties) will not have this extension and will start failing. It is important to check in with your third-party provider to ensure that they are adding this extension to new certificates and automatically rotating legacy certificates. For users using EZCA for Intune SCEP certificates or EZCA + EZSmartCard for passwordless authentication, all new certificates will be issued with this extension, and you will get alerts to rotate certificates that are not compliant with this new requirement.
Automate SSL Certificate Management to Prevent Future Emergencies
While events like this one where you must find all certificates and rotate the affected ones are rare, they do happen every few years and we must be prepared for them. With the use of certificates exponentially increasing, we must use tools to automate certificate discovery and management. Tools such as EZMonitor, the best SSL monitoring tool for Azure are available to you and your organization to help make the intimidating process of SSL certificate monitoring and avoid being impacted by patches such as KB5014754.


