
How to Build Mobile Driver's License ISO/IEC 18013-5 in the Cloud
What is ISO/IEC 18013-5?
ISO/IEC 18013-5 is a standard that defines the technical specifications for mobile driver’s licenses (mDLs). It provides a framework for secure and privacy-preserving digital identity verification, enabling individuals to present their driver’s license information in a digital format. This standard is crucial for ensuring that mDLs are interoperable, secure, and can be used across different jurisdictions. It is a very modern standard, since it allows you to use your phone as a driver’s license, which is very convenient while keeping your data secure. The standard also includes provisions for secure storage, transmission, and presentation of mDL information, ensuring that personal data is protected throughout the process. But if you are looking at setting up a mDL solution, you are probably already familiar with the standard, so let’s get into the details of how to build a compliant solution using Azure’s Managed HSM service.
How to Build an Issuing Authority Certificate Authority (IACA) CA for mDL in Azure
To build a compliant mDL solution, you need to set up an Issuing Authority Certificate Authority (IACA) CA. This CA is responsible for issuing and managing the document signing certificate used in the mDL process. The IACA CA must comply with the ISO/IEC 18013-5 standard and ensure that all certificates issued are secure and privacy-preserving.
Keytos EZCA is a cloud-based PKI solution that simplifies the process of setting up an IACA CA. With EZCA, you can easily create and manage your IACA CA in Azure, ensuring compliance with the ISO/IEC 18013-5 standard. The solution provides a user-friendly interface and API for managing certificates, making it easy to issue and revoke certificates as needed.
In addition to your IACA CA, you will also need to set up your document signing certificate. This certificate is used to sign the mDL data and ensure its integrity, due to it’s highly sensitive nature. The document signing certificate must be stored in a FIPS 140-2 Level 3 compliant hardware security module (HSM) to ensure its security. Thankfully Azure’s Managed HSM service provides a secure and compliant environment for storing your document signing certificate, ensuring that it is protected from unauthorized access. This will save you a lot of time and effort, since you won’t have to worry about setting up, securing, and managing your own HSM infrastructure.
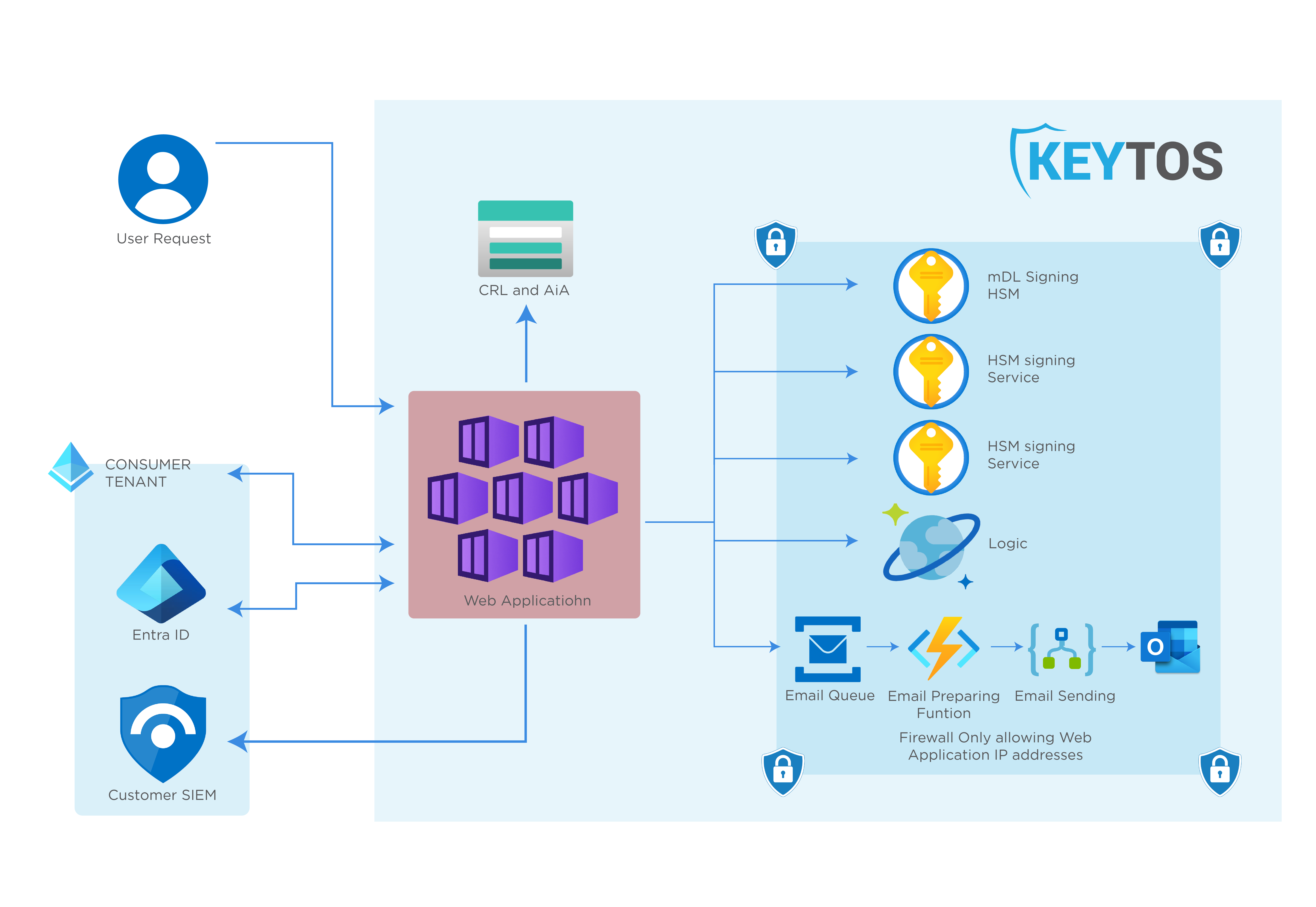
Secure Access to the Document Signing Infrastructure for mDL
Since all infrastructure is hosted in Azure, and compatible with Microsoft’s security tools you can use your Entra ID credentials, with Conditional Access and Azure PIM, to ensure that only authorized personnel have access to the document signing infrastructure. This is crucial for maintaining the security and integrity of the mDL process, as wells as for meeting the government’s security requirements.
How To Design and Build a Mobile Driver’s License Solution In Azure
As previously mentioned, the whole infrastructure is hosted in Azure, making it easy to deploy and manage. This can be hosted in your own Azure tenant, or in a Keytos managed tenant. The solution is designed to be highly scalable and flexible, allowing you to easily adapt to changing requirements and workloads. All the underlying infrastructure is built on Azure PaaS services, which means you don’t have to worry about managing servers or other infrastructure components.
Don’t worry we have a script that will do all the heavy lifting for you. The script will create all the necessary resources in Azure, and have a dedicated Azure PKI ready for you to create your IACA CA.
Step 1: Create your IACA CA For mDL
The first step is to create your IACA CA. EZCA will guide you through the process and it will automatically manage the HSM and CRL for you, making this whole process a 5 minute task.
Step 2: Create your Document Signing Certificate
The next step is to create your document signing certificate. For this you have two options, you can either create a key in the managed hsm and then have your solution send the csr to Keytos and have Keytos sign the document signing certificate and then return it to you, or you can use the Keytos API to have EZCA create the document signing Key and certificate for you, removing the need for you to manage the HSM process, after that you can use the Keytos Sign API to sign the mDL data.
Step 3: Create your mDL Data
Now that you have your document signing certificate, you can create your mDL data hash and sign it with your document signing Key. you will then have to return the cbor object with the signed data to the client (If using the Keytos API this will be done for you automatically). One of the best parts of ISO/IEC 18013-5 is that it will sign each part of the CBOR object separately, so when an entity wants to verify the mDL data, you can select which parts of the data you want to share with them. This is a great way to ensure that you are only sharing the data that is necessary for the verification process, and it also helps to protect your privacy.
How mDL Verification Works
-
- When a user presents their mDL to a verifier (such as an airport TSA agent), the verifier will request certain fields (such as name, date of birth, and address) from the User.
-
- The user will then receive a prompt on their phone asking them to approve the request and share the requested fields.
-
- Once the user approves the request, the mDL data is sent to the verifier, along with a digital signature for each of the fields that proves the data has not been tampered with.
For example:
{
"fields": {
"name": {
"digestID": 0,
"random": h'BBA394B98088CAE238D35979F7210E18DFAF70354524D86149CA20046E4321B1',
"elementIdentifer": "given_name",
"elementValue": "John",
},
"date_of_birth": {
"digestID": 1,
"random": h'AAA394B98088CAE238D35979F7210E18DFAF70354524D86149CA20046E4321B1',
"elementIdentifer": "Birth_date",
"elementValue": "01/01/1990",
},
}
}
and this will be able to be verified with the Mobil Security Object containing the Signed Hashed of each of the fields:
{
"version": "1.0",
"digestAlgorithm": "SHA-256",
"valueDigests":
{
"org.iso.18013.5.1":
{
0: h’D6AA81E454036313A9A681809151DDDBDF702289094F18286DDC591C41C6434E',
1: h'4C3D83940CA8C5DE8060A23EB649C175E79B745B6A7D9939B4D16B3E46BB14D5'
}
}
}
Need help planning your mDL solution?
Keytos isn’t just another PKI provider or consultant. Founded by former Microsoft PKI experts, we are dedicated to helping organizations deploy user-friendly PKI solutions—without requiring PKI expertise. We serve as your strategic partner in building and maintaining a secure digital infrastructure. Our team has over a decade of experience managing PKI and cryptographic services for some of the world’s largest organizations. Talk to a PKI Expert today to explore how we can help you develop a secure and compliant mDL solution in Azure.


