
Is Certificate Transparency Logs Monitoring Needed for PCI Compliance?
At Keytos, we’ve been huge proponents of Certificate Transparency (CT) log monitoring for quite some time. We’ve written extensively about what are CT Logs, and why they’re important, which CT Log monitoring tools are best, and how they help prevent things like man in the middle attacks. All of that considered, there was some very interesting news yesterday about how the newest updates the PCI DSS requirements all but necessitate the need to employ CT Monitoring if you plan to comply with the standards.
If you’re unfamiliar, PCI DSS stands for the Payment Card Industry Data Security Standard. It is a set of security standards designed to ensure that all companies that accept, process, store, or transmit credit card information maintain a secure environment. Essentially, it’s a global standard aimed at reducing credit card fraud and protecting cardholder data in the digital transaction process. The standard encompasses a range of requirements including but not limited to maintaining a secure network, protecting cardholder data, managing vulnerabilities, implementing strong access control measures, regularly monitoring and testing networks, and maintaining an information security policy. These requirements are intended to protect both the businesses that handle payment card information and the customers whose data is being processed. Here’s a look at the most recent update…
Requirement 4: Protect Cardholder Data with Strong Cryptography During Transmission Over Open, Public Networks
The current objectives outlined in Requirement 4 have existed for a long time, for good reason, and have undergone some changes and additions in the v4.0 release. The new requirement we’re going to focus on is 4.2.1.1 which states:
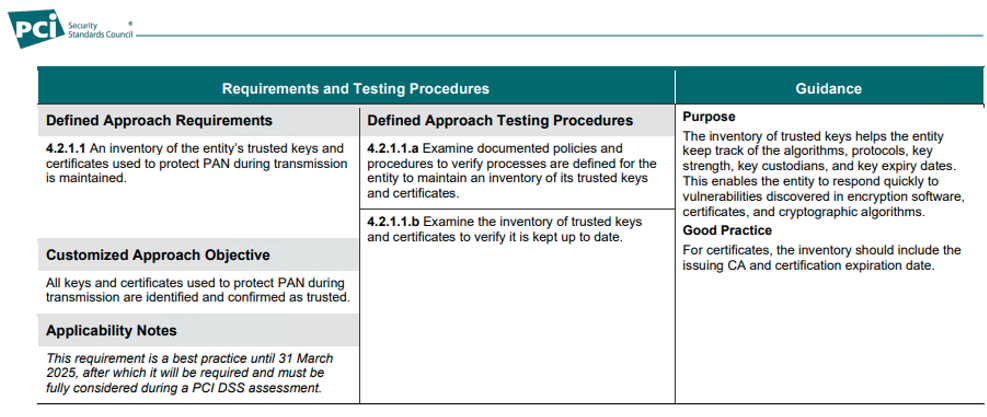
4.2.1.1 An inventory of the entity’s trusted keys and certificates used to protect PAN during transmission is maintained.
So, what does this actually mean? Let’s break it down.
Inventory: This refers to a comprehensive list or record.
Entity’s trusted keys and certificates: These are the digital tools and credentials used for encryption. “Keys” are used to encrypt (scramble) and decrypt (unscramble) data, while “certificates” help verify the identity of the parties exchanging the information.
Used to protect PAN during transmission: PAN stands for Primary Account Number, which is your credit card number. The keys and certificates are used to secure this number when it is sent over networks, like the internet, to prevent unauthorized access.
Is maintained: This implies that there is an ongoing effort to keep the inventory up-to-date and accurate, ensuring that all tools and credentials are in place and accounted for to safeguard the data continuously.
So, in simpler terms, this requirement ensures that any organization handling credit card information keeps a detailed and updated list of all the security measures (like encryption keys and digital certificates) they use to keep that information safe as it’s sent over the internet. This helps prevent data theft or fraud.
Does PCI DSS v4 Make CT Monitoring Mandatory?
Absolutely, and here’s why. Imagine I’m processing payments through Keytos.io, and naturally, I use certificates and keys to encrypt this data in transit using TLS. It’s straightforward to track the new certificates I buy and the existing ones I hold, but what if there are certificates out there that I’m unaware of? Suppose someone within my organization bypasses our standard procedure and gets a certificate. That would go undetected in our inventory. Or what if an outsider somehow convinces a Certificate Authority to issue a certificate for Keytos.io in error? Again, that would skip our inventory check. Even simple human error could lead to a missing certificate.
The reality is that certificates can slip through the cracks in numerous ways, which is where Certificate Transparency Monitoring comes into play. This system ensures that if any publicly trusted certificate is issued for my domain, Keytos.io, it gets detected and logged. Certificate Transparency stands as the cornerstone of ensuring complete transparency and security in certificate management. And the best part? Setting it up is just a few clicks away.
The Best CT Monitoring Tool - EZMonitor
Keytos’ EZMonitor is an easy-to-use tool that allows users to monitor all their domains and get full visibility into all the domains and subdomains for the organization. What sets it apart? It was built by ex-Microsoft Identity Engineers specifically to meet the needs of the modern workforce. Think of it as the Sherlock Holmes of SSL - always alert and on the lookout for potential threats, like Shadow CAs!


