Root CA vs. Subordinate CA
Root CA vs Issuing CA
Now that we’ve defined and differentiated between a public CA and a private CA, the next step is to do the same with a root CA and an issuing CA. As mentioned in our blog outlining certificate authority hierarchy and CA design, root certificate authorities and issuing/subordinate certificate authorities are vital to CA design, particularly in a Two-Tier Hierarchy. So, what are they?
What Is a Root Certificate Authority?
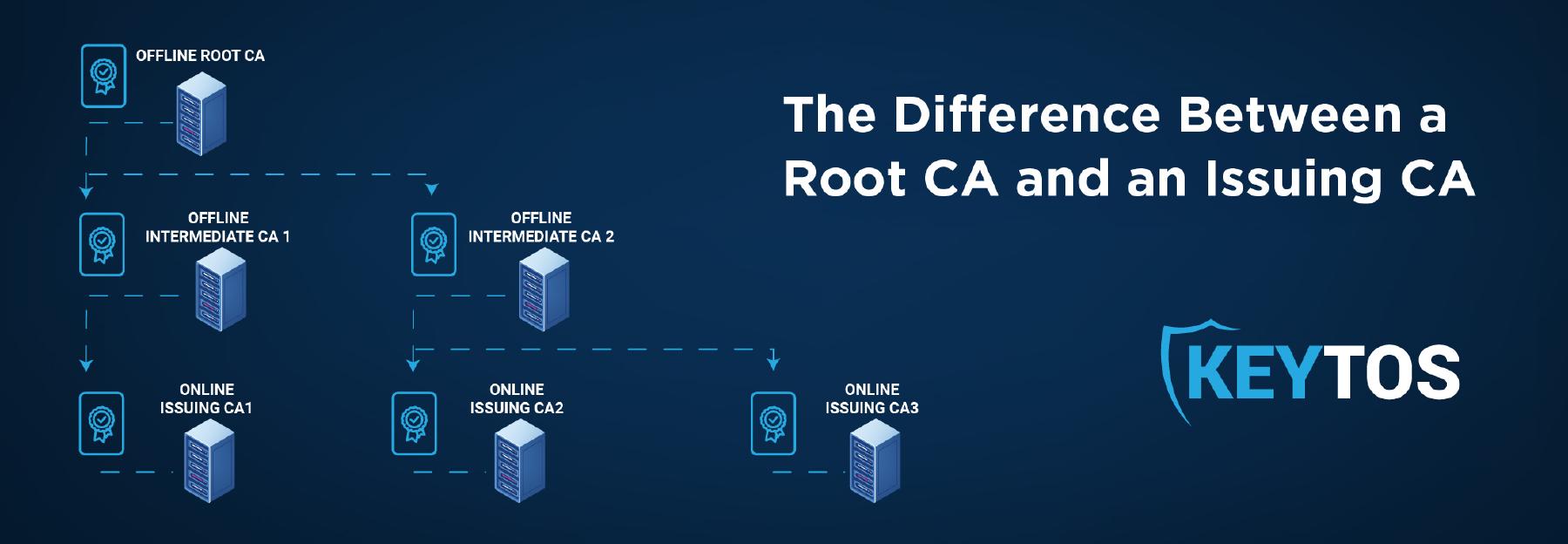
A root certificate authority, as the name implies, is the root of trust for your PKI. In order to trust a certificate chain, the root certificate needs to be added to the trusted root store of the operating system.
Since the root CA is the root of trust for your entire certificate chain, it is vital that it is your organization’s most protected asset; after all, if a bad actor gets control of your root CA, they have the keys to the kingdom. Protecting the root certificate authority locks the door for would-be attackers. This is why root CAs are typically kept offline in a secure, undisclosed location and are only ever turned on by the PKI team when a new issuing CA is being issued or a CRL is being signed.
What Is an Issuing Certificate Authority/Subordinate Certificate Authority?
In a Two-Tier PKI Hierarchy, the subordinate CA is responsible for issuing certificates to end users – hence its name. To inherit the trust of the root certificate authority, the subordinate certificate authority is signed by the root CA. One root CA can have multiple issuing CAs, but it is recommended to separate the subordinate certificate authorities by the types of certificates that they issue – for example, Smartcard and SSL. Other common scenarios that call for having multiple issuing CAs, are scalability and for geo-redundancy.
How Cloud-Based PKI Certificate Management Tools Can Help
EZCA, our certificate management tool, was designed specifically by our team of ex-Microsoft engineers to support both your existing root certificate authorities and issuing/subordinate certificate authorities. Here’s how:
Root CA Support in EZCA
When we designed EZCA, we understood that we would have customers with existing offline root CAs already managed by their PKI team, as well as customers without a root CA who do not want the costs and responsibilities associated with managing one, such as CRL management, HSM management, and making sure the root CA is in a secure facility. This is why we support both bring your own root CA and managed root CA.
Issuing/Subordinate CA Support in EZCA
EZCA allows you to generate geo-redundant issuing/subordinate CAs in mere minutes. To meet our customer’s needs, we allow you to chain your CA up to an offline root managed by your organization or to an EZCA root CA. EZCA also helps you manage your issued certificates and automatically rotate them, as well as connect into Azure key vault. EZCA also ensures that your organization is following certificate management best practices, as it was designed to do so and remove the worry about following them from your shoulders. Manual certificate management is long and difficult – using EZCA is the opposite.
To learn more about EZCA, check out our certificate management tool product page or schedule a free PKI assessment with one of our experts today! Additionally, to learn more about the foundations of PKI, feel free to check out our PKI Basics Series playlist on YouTube!


