What is Certificate Authority Hierarchy and Which CA Hierarchy Should I Use?
The World of Certificate Authority Hierarchy
The world of CA hierarchy and design is a complex one – but it doesn’t have to be. The implementation of proper certificate authority hierarchy and design is key to secure communication across your organization; before we take a look at the recommended certificate authority hierarchy, though, it is first important to clarify and define what is a certificate authority.
What is a Certificate Authority?
In cryptography, a certificate authority/certification authority (CA) is, simply put, an entity that issues digital certificates. That digital certificate serves to verify that the specifically named subject of the certificate actually owns the related private key, allowing other parties to confidently be able to rely on signatures or assertions made about the corresponding key. A CA, then, serves as a trusted third party – it is trusted by both the subject (owner) of the certificate and by the party relying on the certificate.
What is CA Hierarchy?
CA hierarchy simply refers to the number of levels – or tiers – per each certificate authority. Determining the number of tiers in a CA hierarchy is paramount to effective PKI planning. The three options to choose from are Single/One-Tier Hierarchy, Two-Tier Hierarchy, and Three-Tier Hierarchy.
Single/One-Tier PKI Hierarchy
A Single/One-Tier Hierarchy consists of one singular CA which serves as both the root CA and the issuing CA. For a more detailed review of these types of CAs, check out our blog outlining the difference between a root CA and an issuing CA, but for now just know that a root CA is the trust anchor of the entire PKI. A root CA public key acts as the root of trust for a certificate – any applications, users, or computers that trust the root CA also trust any certificates issued by the CA as a result.
The Single/One-Tier Hierarchy is not recommended for any production scenario due to the fact that, with this hierarchy, a compromise of the single CA means a compromise of the entire PKI. For security reasons, root CAs and issuing CAs are usually separated, since it is typically challenging to quickly distribute a new root CA to replace a compromised CA.
Two-Tier PKI Hierarchy (The Recommended Way)
A Two-Tier Hierarchy is the design that meets most organizations’ needs. In a Two-Tier Hierarchy, there is an offline root CA and an online subordinate issuing CA; there is an increased level of security since the root CA and issuing CA roles are separated, but – more importantly – the root CA is offline protecting the private key of the root CA from a compromise. The Two-Tier Hierarchy also increases scalability and flexibility because there can be multiple issuing CAs subordinate to the root CA, which is one of our highlighted certificate management best practices. This allows administrators to deploy CAs in different geographical locations with differing levels of security as well as in different CA scopes (smartcard, SCEP, etc.); however, this extra security does come with higher costs. Manageability is increased since the root CA must be manually brought online to sign CRLs. Capital cost is also increased since an additional server or virtual machine and hardware security modules (HSMs) are needed. Despite the higher cost, the Two-Tier Hierarchy is the recommended design for most PKI solutions.
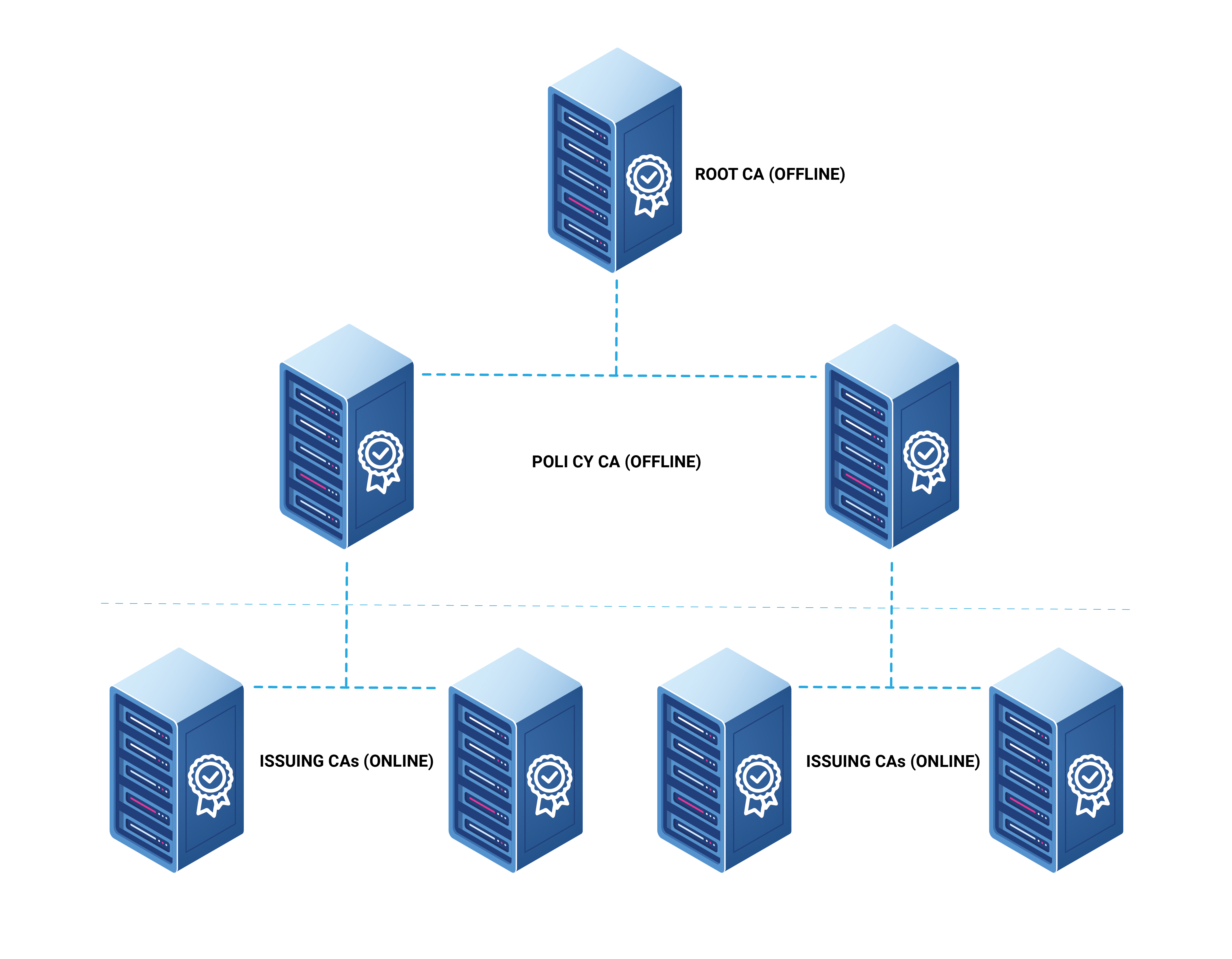
Three-Tier PKI Hierarchy
A Three-Tier Hierarchy adds an extra policy CA between the root CA and the issuing CAs. This policy CA is usually used to enforce issuing policies to impose issuing boundaries for the issuing CAs. Unless the organization is running a very large PKI infrastructure that requires multiple teams managing different issuing CAs, this hierarchy is not recommended since it adds extra, unnecessary complexities. An example of when a Three-Tier Hierarchy is used would be in the U.S. government, where you have a root CA, but you also have different branches of the government – in that example, you would want to have a policy CA in between so that, let’s say, the DOD cannot issue CIA certificates.
Get Started with Your PKI Architecture with Expert Help
By following these tips and recommendations, you and your organization can get a head start on the road to effective cybersecurity!
CA design and management can be tricky – that’s why we are here to help! Check out our certificate management tool, EZCA or schedule a free PKI assessment with one of our experts today! Additionally, to learn more about the foundations of PKI, feel free to check out our PKI Basics Series playlist on YouTube!


