What’s the Difference Between EAP-TTLS/PAP vs. EAP-TLS?
How to Prevent Credential Compromise with EAP
For the sake of argument, we’re going to assume you’ve landed on this post because the sanctity of your organization’s network security is of supreme importance to you, prompting a quest for fortified defenses. Alternatively, should this subject matter not have previously piqued your interest, allow us to assert the urgency of attending to this matter forthwith.
A recent exposition by Positive Technologies has illuminated a rather alarming vulnerability within the digital “security infrastructure” of modern enterprises: a staggering 93 percent of a company’s digital assets can fall prey to cyber incursions within 48 hours (about 2 days) of an initial attack. This revelation underscores the criticality of “credentials compromise” as a predominant vector for successful intrusions within network defenses. If you’re familiar with the blog, you’re aware that passwords are a problem!
In the quest to safeguard your organization’s WPA2-Enterprise network, the arsenal of protocols at your disposal is vast. Yet, among these, the Extensible Authentication Protocols (EAP) emerge as the preeminent choice for a substantial number of enterprises. Let’s delve into an examination of the two most prevalently employed EAP protocols, aiming to highlight the merits of each and thereby assist you in making an informed selection most befitting your organizational needs.
What is Extensible Authentication Protocol (EAP)?
At its core, the Extensible Authentication Protocol (EAP) represents a framework designed to fortify the communication corridors between a client and server with a veil of encryption. Through this encrypted conduit, a series of trust verifications are enacted—spanning server certificates, intermediate certificates, to client validations—thereby establishing a robust chain of trust anchored by the Root CA and the CN (Common Name) of the server certificate. This protocol serves as the cornerstone of modern wireless networking, offering a barrier against the multifaceted threats that besiege our organizations in today’s day and age.
Imagine EAP as a secret tunnel where messages between your device and the network’s server play tag securely, thanks to some digital trust magic involving certificates. There are a few ways to set up this secure tag game, but EAP-TLS and EAP-TTLS/PAP are the main characters, so to speak, in the EAP world.
What’s the Difference Between EAP-TTLS/PAP vs. EAP-TLS?
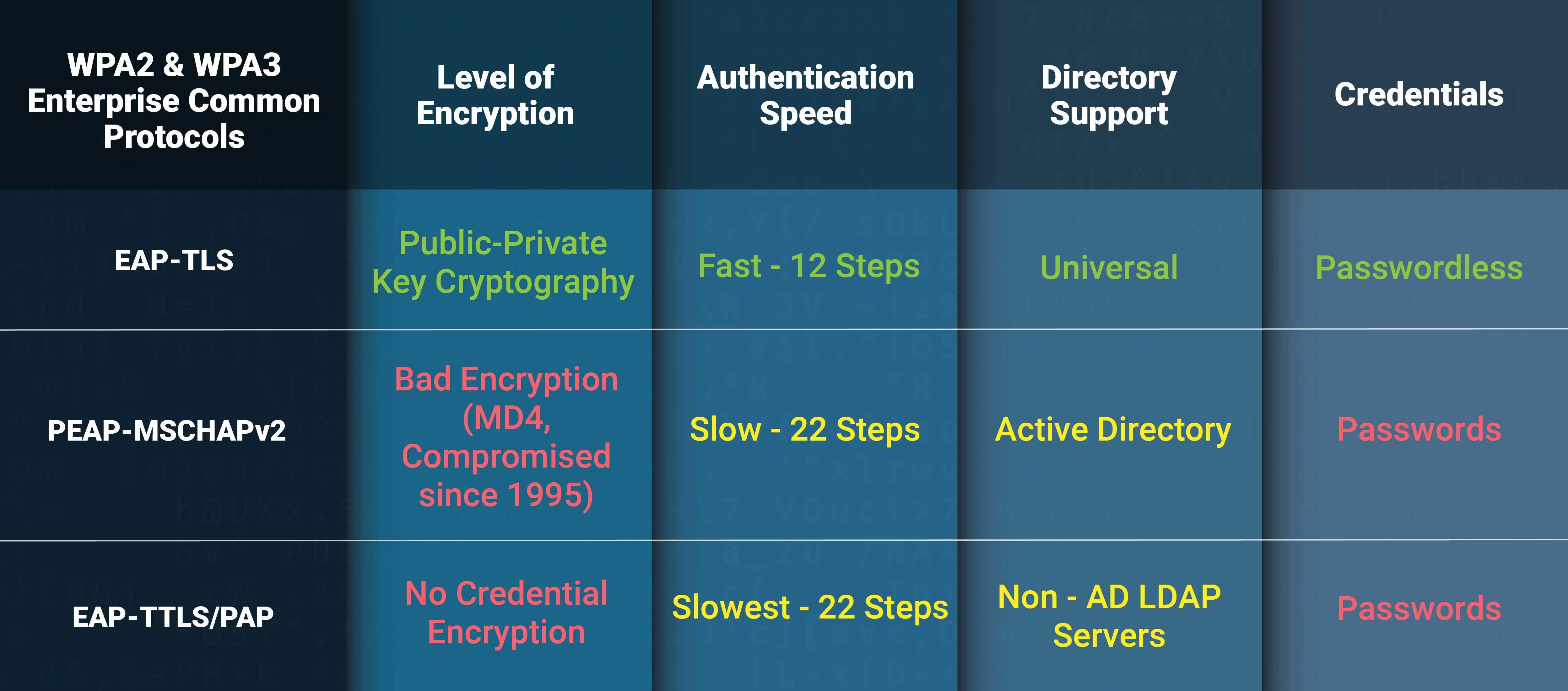
EAP-TLS is like a high-security handshake where both sides need to show ID (certificates, in this case) to trust each other. It’s like a secret club’s handshake but with digital certificates.
EAP-TTLS/PAP, on the other hand, is a bit more “relaxed”. The server still has a certificate but the client is not required to have one. Once a TLS tunnel is created, the client shares the password with the server through the tunnel. While it is more secure than regular PAP that is not encrypted, you are still relying on a password.
What are the Advantages of EAP-TLS?
EAP-TLS is like the Fort Knox of authentication. It uses sophisticated digital certificates instead of simple passwords, making it a tough nut to crack for any would-be intruders. It’s faster, more secure, and can be automated with an MDM (you automatically create the certificate, and set the wifi profile to use the certificate. No interaction from the user). In the battle against cyber baddies, moving away from passwords to something like EAP-TLS can be a game-changer. It’s not just about locking doors; it’s about making sure those doors are as strong as they can possibly be.
What are the Shortcomings of EAP-TTLS/PAP?
Though EAP-TTLS/PAP sounds easy-peasy, it’s got a few chinks in its armor. For starters, it still depends on passwords managed by a human, which is a no-go in a world where hackers are lurking. Here, if the user is not educated on best practices, can fall for a man in the middle attack, giving the credentials to an attacker.
How to Get Started with EAP-TLS
Keytos is your ally in this quest, offering everything you need to transition to a certificate-based authentication with EAP-TLS. We’ve got tools, support, and the know-how to make your network as secure as it can be, without making it a hassle for you or your team. So, what’s it gonna be? Stick with the old and vulnerable, or step up to the secure, sleek future with EAP-TLS? Your call, but I know where I’d put my money. Feel free to reach out to our Team of PKI Experts for a FREE assessment as to how to best move forward with EAP. DIY more your style? Head on over to the docs or view some more of our suggested reading below.


