How to Prevent Subdomain Takeover in Your Azure Cloud with SSL Certificate Monitoring
What is Subdomain Takeover?
Let’s start by defining what subdomain takeover is. Subdomain takeover is when an attacker takes over an unused subdomain to impersonate you. While this might seem like an innocent vulnerability since no customer data is being accessed, this TechCrunch article explains, domains are being sold in the dark market and are a gold mine for phishing scammers. With over 80% of cyber-attacks starting with phishing, phishing has become the most common attack. To protect themselves, companies have trained employees to check the domain to match the company’s domain before entering any information. Subdomain takeover lets attackers impersonate your domain with a real domain, passing all the tests that your employees have been trained to look for.
How Is Azure Affected?
To use your own domains in Azure, you must point the DNS entry to a specific Azure resource, such as yoursite.trafficmanager.net, this will send all traffic to that Azure resource and the Azure resource will serve your content. As the cloud promises, this is a very straightforward process, and all the networking is taken care of for you.
The problem comes when deprovisioning the resource. After the Azure resource is deleted, if the DNS record is not removed, anyone that creates that same resource can impersonate your site and create a phishing site for your customers or employees.
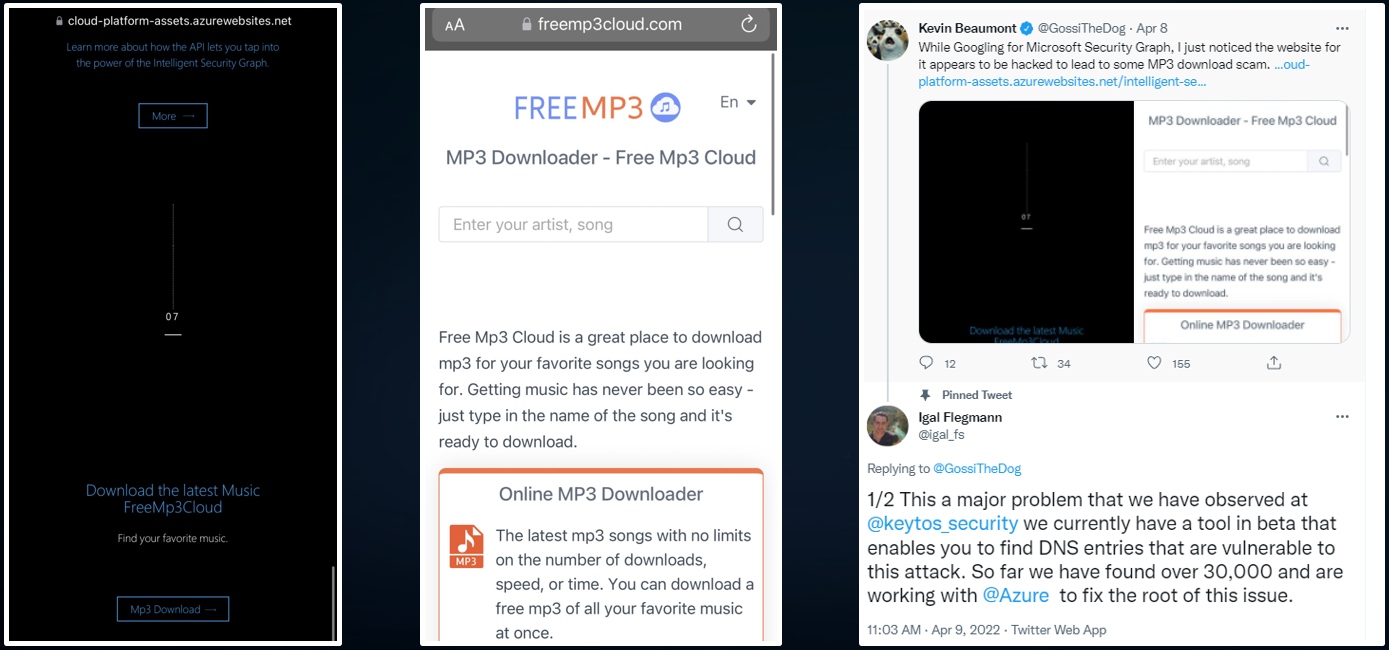
Unfortunately, it is very hard for security teams to keep track of all sites that are created in Azure and detect any site that has been deleted and the DNS entry for it is still pointing to an Azure resource. As seen in the screenshots below, even Microsoft has fallen victim to this attack.
What is the Scale of the Problem?
This vulnerability was detected by our team while creating EZMonitor and it was immediately reported to Microsoft. Since then, we have worked closely with Microsoft to remove over 700 vulnerable Microsoft owned domains that were pointing to non-existing Azure resources.
In the first month of EZMonitor being released, EZMonitor has detected over 30,000 vulnerable subdomains. A very common problem that we have seen with these domains is that many of these URLs were either temporary site such as: wintersale.yoursite.com, employeebonus.yoursite.com, etc. or a deprecated administrator site such as admin.yoursite.com making them prime domains for attackers.
Free Domain Checks
As a responsible member of the cyber security community, we have made the check for vulnerable URLs completely FREE for anyone. Just go to the EZMonitor portal and enter your domain and we will disclose if we have found any vulnerable subdomains (we will not disclose the actual subdomains without first validating domain ownership).
Free Domain Checks
As a responsible member of the cyber security community, we have made the check for vulnerable URLs completely FREE for anyone. Just go to the EZMonitor portal and enter your domain and we will disclose if we have found any vulnerable subdomains (we will not disclose the actual subdomains without first validating domain ownership).
Check My Domain