
The growing demand for secure and passwordless authentication has brought FIDO2 (Fast Identity Online 2) to the forefront of the cybersecurity industry. As businesses continue to adopt hybrid work environments, there is an increasing need to find solutions that seamlessly integrate with both on-premises and cloud-based systems. In this blog post, we will discuss how FIDO2 can be implemented for on-premises Active Directory (AD) and how you can use PIV certificates to complement FIDO2 for legacy.
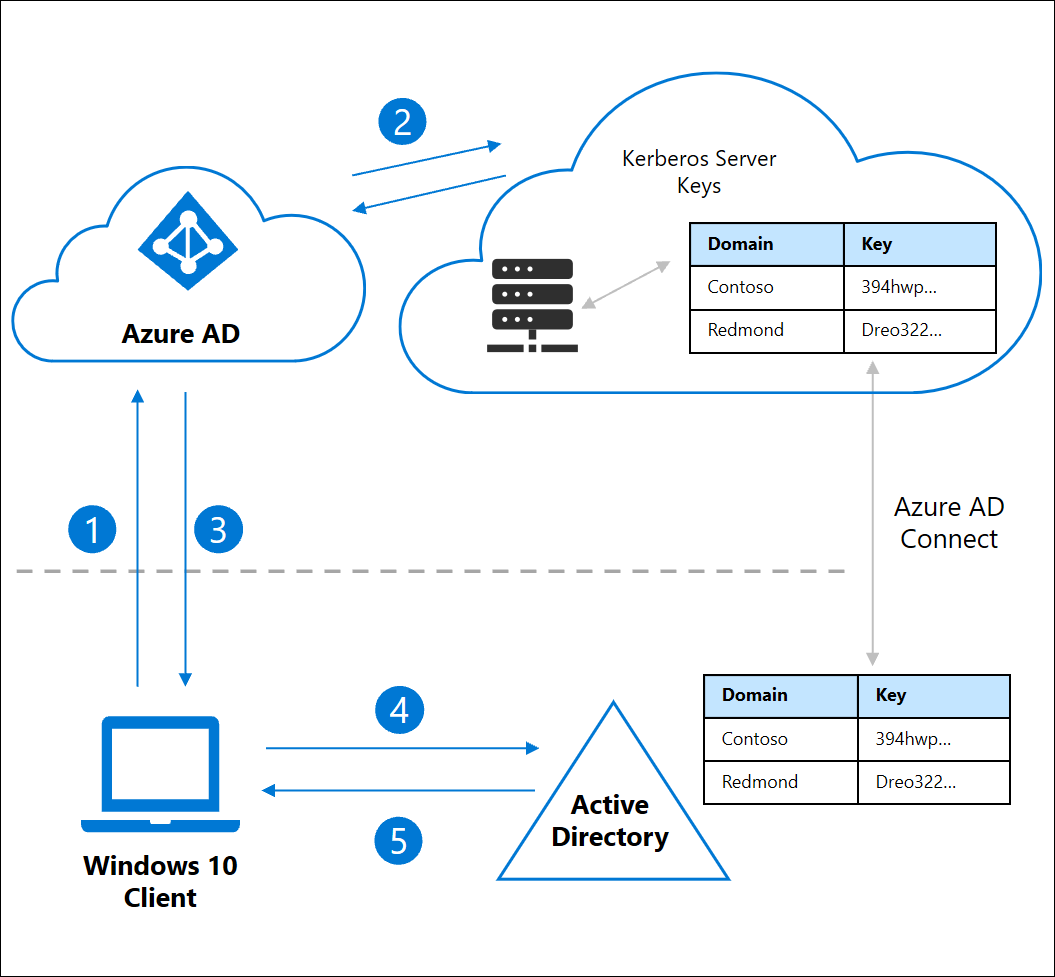
FIDO2’s popularity due to its security and ease of use have made it a popular choice for many organizations (with estimates of 60% of organizations starting their passwordless journey in 2023). This has made Microsoft create connectors for FIDO2 to work on premise. How it works? User SSOs into Azure AD and Azure AD issues a Kerberos token for legacy applications to accept. To set up Azure AD as a Kerberos server follow this guide.
Note: You must use Azure AD Connect since Azure AD Connect Cloud Sync does not synchronize device objects.
As previously mentioned, FIDO2 was created for the cloud and while you can use Azure AD as a Kerberos server and breach the gap to FIDO2 on premises, it is not native behavior for AD authentication, while also adding an external dependency (Azure AD) for on premises operations. PIV/Smartcard authentication have been a part of AD authentication since the beginning of this century and best of all, they work very similar to FIDO2, the only difference between the two is the infrastructure behind the issuance of the cards, but thanks to modern tools, this infrastructure is offered as SaaS offerings watch our webinar below on the difference between FIDO2 and Certificate Based Authentication.
Government Compliance requirements still require smartcards for government agencies and their contractors, to solve this issue Microsoft also created a connector that allows you to use smart cards in Azure without the need to deploy all the on-premises AD services such as: Domain Controllers, ADFS servers, Certificate Authorities, CRL (Certificate Revocation List) Servers, etc. This solution is Azure CBA, learn how to deploy Azure CBA.
As you can see, Microsoft has created bridges for smart card authentication to be used in the cloud and for FIDO2 to be used on premises, but they are just that, bridges that will not give you the best experience in the other environment. To have the best user experience and compatibility for legacy and modern authentication the answer is to have both FIDO2 and Smartcard authentication enabled in your organization, while this might sound like a lot of work, thanks to the work that Microsoft, Yubico, and Keytos have done together achieving this is seamless for the user and the IT administrator, since when a YubiKey is registered using EZCMS, the same key will hold both a FIDO2 key and a Smartcard certificate, giving the user the best user experience for both scenarios without the user knowing if they are using a smartcard certificate or a FIDO2 key, all the user needs to know is that their Yubikey is the tool they use for passwordless authentication.
While this post was mostly theoretical, getting started with FIDO2 and Smartcard authentication is easy, all you need is a Yubikey and a an Azure subscription. Follow this guide to issue your first FIDO2 and SmartCard Yubikey in less than an hour!