
Microsoft Cloud PKI for Intune Suite Falls Well Short of Security Community’s Expectations
Microsoft Cloud PKI Falls Short of Expectations
After years of promising to deliver a native cloud PKI, the good folks over at Microsoft have finally announced their Cloud PKI for Intune! Very exciting news for the Security community, right? Well, as it turns out, not so much.
“In February 2024, Microsoft Cloud PKI will be available as part of the Microsoft Intune Suite. For added flexibility, this new solution will also be available as an individual add-on to Microsoft subscriptions that include Intune …Cloud PKI as a standalone add-on will be $2 per user per month… Although available as a separate add-on to try or buy, we expect most organizations will realize the greatest value with the adoption of the entire Intune Suite. The list price for the Intune Suite will remain at $10 per user per month.”
In the announcement, Microsoft boasts about how this new tool will help simplify the process of creating a PKI. Excellent in theory, but unfortunately, users seem to believe that it’s a bit too remedial and doesn’t justify the cost. This is clearly evident when you scroll down to take a look at the comments section of the page. For example, one of the more cruel takes…
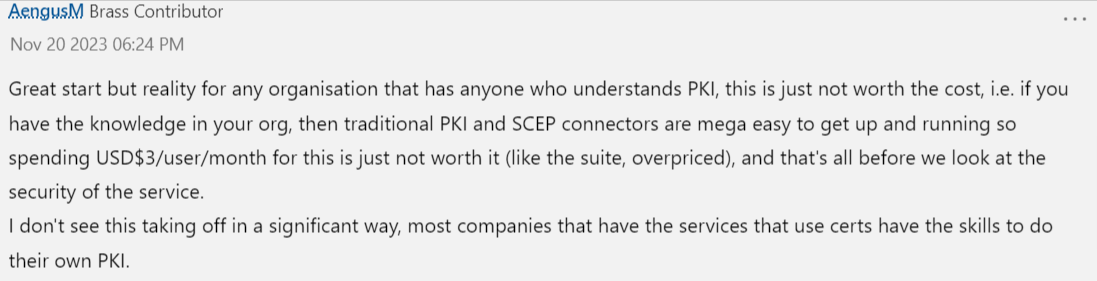
This comment is a fairly clear indication of the entire community’s sentiment. Seems as though it’s “Too little. Too late.” Or, as my Mother would say, “A day late, and a dollar short.” There’s obviously a significant gap between what this new offering provides, and what Security practitioners were expecting/actually need to be successful implementing PKI. They’ve been waiting patiently for this announcement, eager to see what’ll be available. Unfortunately, in true Microsoft fashion, they’ve fallen far short of the community’s expectations. Consequently, this has the Security community thinking that this new offering isn’t capable of accommodating their needs.
How Much Does Microsoft Cloud PKI Cost?
The pricing for the new Cloud PKI is $2 per user per month. This is a bit of a head-scratcher, as it seems to be aimed at per user licenses, which doesn’t scale to server certificates, or IoT Certificates. Showing that Microsoft is not really thinking about the needs of the Security community, and is instead focused on the needs of the Intune team.

What’s Not Supported in the New Microsoft Cloud PKI?
It seems that while the name indicates this is Microsoft’s cloud version of ADCS, it is only aimed at Intune. Starting with the pricing, the pricing is aimed at per user licenses, this pricing will not scale to server certificates, or IoT Certificates. As evidenced by the comments on the page, this PKI solution seems to be missing some of the key features that users were expecting. Let’s take a closer look at some of the features we think they missed.
Non-Intune SCEP
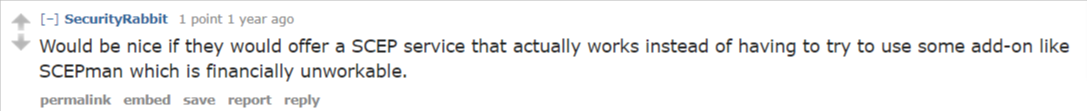
Most notably, the announcement only talks about issuing certificates through Intune SCEP. The key omission here is that there is no indication that SCEP certificates that are not managed through Intune, such as network devices, will be supported. Not ideal. Since last year’s update, users have been cautiously optimistic that this would be included in the offering. A quick look at one of the more prominent Azure discussion forums shows that SCEP capabilities have been a key concern/touchy subject for quite some time now.
OCSP
As certificate-based authentication continues to grow in popularity, ensuring that these certificates are valid and trustworthy is of extreme importance. One of the most popular ways to monitor and manage certificates is the Online Certificate Status Protocol (OCSP). Unlike more traditional methods like CRLs, OCSP was designed specifically for retrieving the revocation status of individual certificates, making it much more efficient than its traditional counterpart. Unfortunately, it is not included in Microsoft’s new Cloud PKI. Major bummer.
Smartcard Certificate Distribution
Really not sure how they failed to include support for smartcards in the offering. In my humble opinion, this seems to be an egregious omission. Smartcards have been one of the most widely used authentication methods associated with CBA for YEARS. Microsoft themselves added Azure CBA Support last year, and even mention it in this blog; however, this is for single factor certificates – they do not support the more secure version of smartcards, or YubiKeys for that matter.
ACME
Automated Certificate Management Environment, or as the cool kids call it, (ACME), is an exceptionally useful protocol designed to automate the interaction the certificate issuance for web servers. Essentially, it allows for the automated certificate deployment and automation across web servers. The primary motivation behind leveraging ACME is to simplify the process of obtaining, renewing, and managing SSL/TLS certificates. Prior to ACME, obtaining and managing these certificates required manual steps which could be a royal pain in the rear-end, especially for large-scale deployments or in instances where there are frequently expiring certificates. Long story short, ACME has saved the Security Development and Engineering communities countless time and headaches, having ACME support in a private CA is a must in this day and age.
Azure Key Vault Certificate Rotation
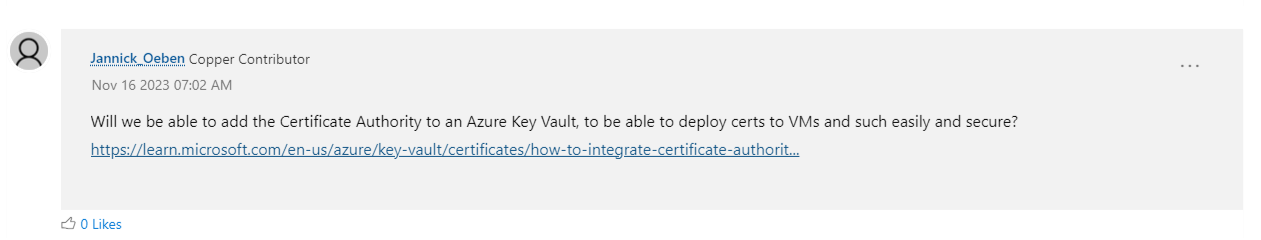
One of the best Azure features is Azure Key Vault it allows you to securely manage your certificates and services and even push them to your Azure VMs. AKV has supported Automated certificate rotation for DigiCert for over 5 years, adding a similar functionality for private certificates would make this new cloud offering a great option. (see the video below on how great Azure Key an Azure Key Vault certificate experience could have been)
Azure IoT Hub Integration
After Intune, the biggest use for certificates in Azure is Azure IoT Hub, millions of certificates are issued and used for authentication with our Azure IoT Hub CA looking it at the business side, having a private CA that supports IoT devices, could help unblock billions of dollars of revenue in other cloud services such as datalake, IoT Central, etc.
What Does This Mean for the Security Community?
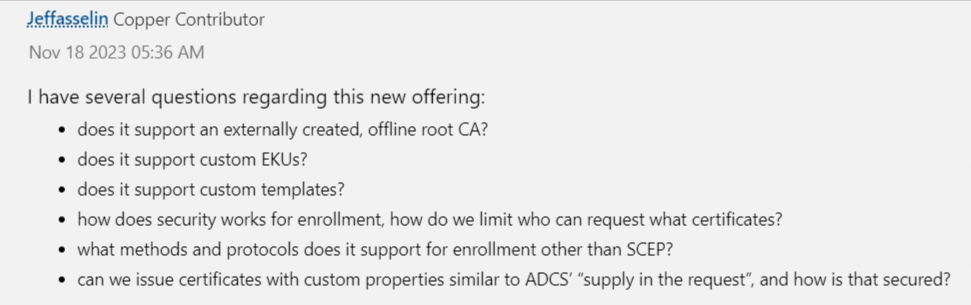
First things first, they want answers, directly from Microsoft, regarding the functionality and support for the new Cloud PKI. Another glance at the comments section of the announcement indicates that the community wants more granular detail on the offering. In fact, one user has “several questions”, which just appears to be a passive aggressive way of pointing out the PKI’s shortcomings.
The initial knee-jerk reaction has been excitement of the announcement with a mix of disappointment, people have been looking up to Microsoft as the PKI leader of the world, however, in the past years they have been left behind by other technologies such as EZCA that do meet the customer PKI requirements for Azure. The Security Community deserves a more robust solution, and we’re disappointed at the lack of functionality available with this new Cloud PKI. Engineers are going to begin utilizing more advanced and sophisticated PKI solutions like EZCA from Keytos, the first Azure-native Certificate Authority.


