
How to Implement Unphishable Authentication in Azure AD
In order to effectively implement passwordless authentication in Azure throughout your organization, you need to first reflect on the entire user lifecycle. This involves processes like creating a user account without a password, distributing hardware keys (e.g., YubiKeys), onboarding users and personal computers, authenticating on the network, implementing conditional access, and enabling passwordless entry to non-Active Directory resources like Linux systems. We know that that can be a massive headache; while we can’t provide you with Ibuprofen, we can help alleviate that headache by diving into each of these aspects! Let’s take a closer look!
How to Create an Azure AD User Without a Password
Although Microsoft has been discussing the concept of a passwordless system for a while, they currently lack the feature to set up user accounts without passwords. The most feasible approach is to create accounts with extremely lengthy passwords (which are not recorded anywhere) and to establish conditional access policies mandating passwordless authentication methods. We offer an excellent tutorial on creating users with random passwords, complete with the PowerShell code to facilitate user creation – not that we’re biased or anything.
Shipping Your Hardware Keys Worldwide
For organizations of any size, one of the most challenging aspects of implementing passwordless authentication with hardware keys (think YubiKeys) is distributing them.
In large enterprises, global distribution poses significant challenges, from navigating customs to needing a dedicated team for managing and dispatching keys, leading to considerable complexity – who wants to deal with all of that? Fortunately, our experience in distributing tens of thousands of keys worldwide has been invaluable. EZCMS simplifies this process with its integrated ticketing software, aiding your IT desk in efficiently handling and tracking inventory. Additionally, our managed smartcard and YubiKey logistics service utilizes global partners to distribute keys to your users internationally.
Small businesses face different yet equally daunting challenges. These include limitations imposed by industry leaders who may not sell keys to smaller organizations and the lack of infrastructure to distribute or print smartcards, making the transition to a passwordless system tricky. At Keytos, we cater to organizations of all sizes, assisting with everything from smartcard printing to hardware key procurement and delivery. Our team of experts is dedicated to making your shift to a passwordless environment as smooth as possible!
How to Make an Unphishable Credential Without a TAP or a Password
The initial challenge here involves introducing users to your selected passwordless method without using a password, while simultaneously guarding against social engineering attacks on your IT staff (similar to the MGM password reset data breach where attackers posed as a user to obtain a temporary password).
When consulting Microsoft’s guidelines, they suggest using a Temporary Access Pass (TAP); however, when closely examined, a TAP essentially functions as a one-time password (OTP), susceptible to the kinds of attacks previously mentioned, potentially becoming the most vulnerable point in your entire system! We’ve prepared a comprehensive guide on how to onboard users without relying on TAP which we highly recommend you check out. Essentially, you should implement a self-service onboarding process, like the government ID validation feature offered by EZCMS, as illustrated in the video below:
Using Autopilot to Onboard to a Personal Computer
After creating the user identity, we advise either setting up a kiosk for users to access the EZCMS application independently of their personal computer or enabling remote users to enroll using their own computers. There’s no need for concern about security breaches from unmanaged devices, as EZCMS incorporates additional validations.
Subsequently, the user must configure their work PC. Notably, Windows 11 facilitates signing in with a security key right from the initial setup, allowing users to log into their computers for the first time using their FIDO2 key, thus eliminating the need for a password or a TAP!
How to Set Up Intune SCEP for VPN and Wi-Fi Certificate Authentication
If you’re using Autopilot, that means you’re also using Intune – for authenticating to your VPN and Wi-Fi, the most effective approach is to utilize X.509 certificates managed by Intune SCEP. You have the option to configure your ADCS CA and SCEP server and manage these servers manually; however, there are also third-party Intune PKI services like EZCA that greatly simplify this process! These services enable you to quickly establish an HSM-backed CA and set up a passwordless Wi-Fi profile in mere minutes.
How to Set Up Conditional Access
After implementing passwordless authentication in your organization, the next step is to ensure that only these methods are used for authentication. Microsoft facilitates this with its conditional access feature, available with an Entra ID Premium P1 license or higher, and it’s a worthwhile investment.
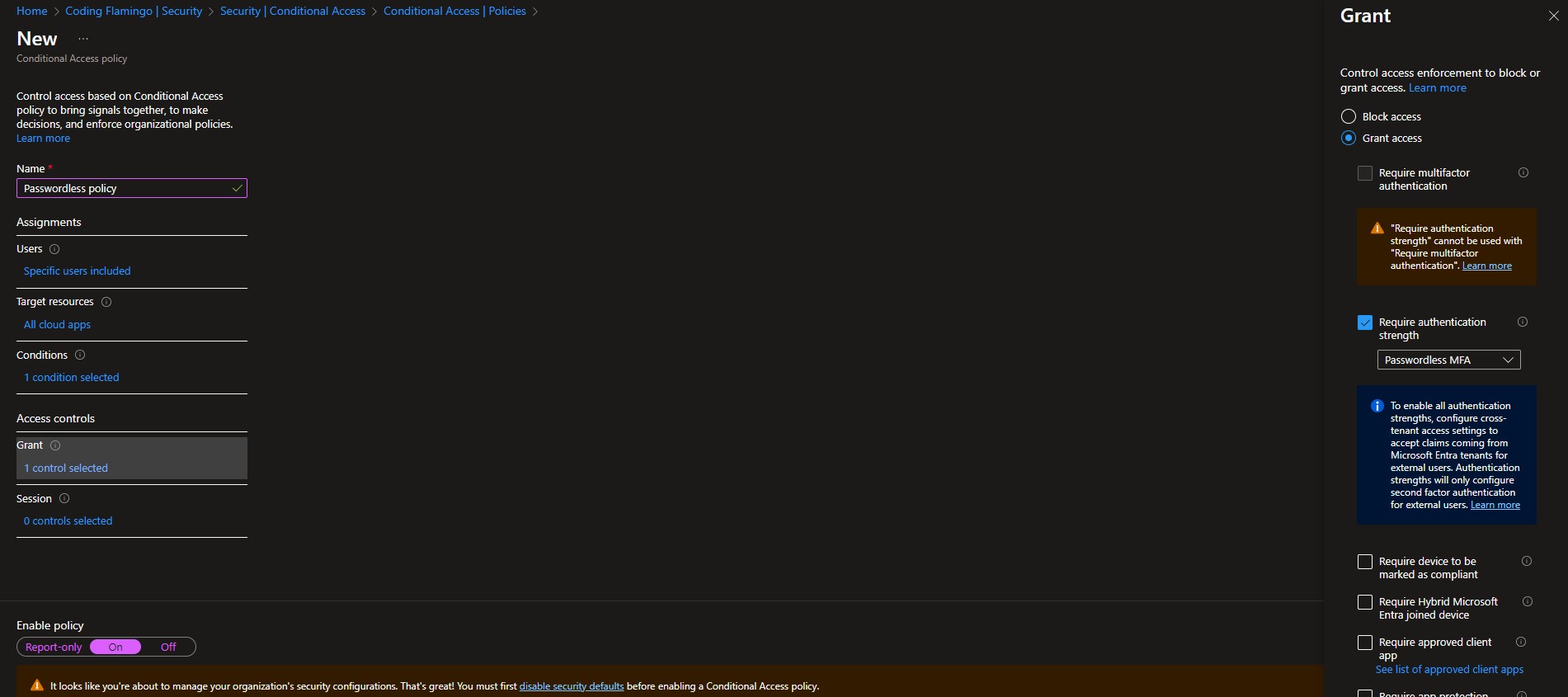
To configure this, log in to the Azure portal as a global administrator, navigate to Entra ID, then to Security -> Conditional Access Policies -> New Policy. Create a policy, initially applying it to a select group of test users to avoid accidentally locking everyone out. Choose the applications you wish to apply this policy to. In the conditions section, you might opt to exclude device platforms not compatible with your chosen authentication method, but it’s advisable to enforce it across all platforms, as hackers only need a single vulnerability to wreak havoc. In the access controls’ Grant section, set the “Require Authentication Strength” to Passwordless MFA. It’s also wise to implement device requirements; for more details on device security, refer to our webinar on device security, though this blog isn’t the place for an in-depth discussion on that topic.
How to Use Azure AD Authentication in Linux
Securing corporate accounts is just the first step towards passwordless authentication, but many organizations stop there and overlook a critical component of their infrastructure: Linux. Traditionally, Linux has local accounts that aren’t linked to Active Directory, a system adequate for the early days of SSH but inefficient for the scale and security needs of modern cloud environments – the overhead of credential lifecycle and user management simply does not scale. Some organizations attempt to integrate their Linux machines with Active Directory, but this approach – while functional – lacks optimal security and is vulnerable to DNS-related disruptions. Major organizations like Google, Facebook, Uber, and Netflix have shifted to using SSH certificates instead.
SSH certificates are cryptographic tools granting temporary access to Linux nodes. The challenge lies in their creation: manual creation is possible, but Linux lacks an automated system for verifying user access levels before granting permissions. These larger companies have developed internal tools for verifying user permissions and generating SSH certificates. Although these internal tools are proprietary, EZSSH offers a similar solution. EZSSH authenticates users via Entra ID, ensures compliance with your conditional access policies, and checks Azure RBAC or hybrid policy ACLs for non-Azure SSH endpoints. EZSSH then generates a short-term SSH certificate for user access. After the session, the certificate expires, preventing misuse. Talk about a gamechanger!
Final Thoughts on Implementing Unphishable Authentication Throughout Your Organization
This extensive guide demonstrates that, while transitioning to a fully passwordless system in Azure involves many components, it is entirely achievable so long as you are fully prepared. Once you make the switch to passwordless authentication, you’ll likely never want to return to the old ways – we’ve been operating in a passwordless model for over two years and the experience has been nothing short of fantastic!
If you’re prepared to advance in your passwordless journey, feel free to schedule a FREE consultation with one of our ex-Microsoft identity experts! We look forward to evaluating your strategy and helping ensure that every detail has been thought of and addressed!


