
Since its initial announcement in 2022, Microsoft has significantly enhanced Entra CBA across various platforms. In their most recent update on December 13th, Microsoft announced that these enhancements encompass support for certificates on different devices and compatibility with external security keys, such as YubiKeys. The updated system provides users with more flexibility and control over authentication processes with customizable authentication policies based on certificate type, user group, resource type, and certificate strength. It was really great to see our partners at Yubico mentioned by name in that update from Microsoft! In case you’re new to our blog, we’re probably the world’s biggest YubiKey fans…even the old guy in Marketing and that whacko from Coding Flamingo love them!
YubiKeys provide a robust and user-friendly way to enhance security without relying on traditional password systems, which we know are a problem. This alignment with modern security practices and regulatory demands makes them an excellent choice for organizations looking to adopt a passwordless approach.
Certificate-based authentication works by using X.509 certificates to authenticate users. How do we get these certificates? Well, you’re going to need a Certificate Authority to issue them. Unsurprisingly, there is no built-in azure native certificate authority, as Microsoft has declared the issuance and distribution of certificates out of scope.
We’ve made it our mission at Keytos to help organizations of all shapes and sizes clear this hurdle with ease! We’ve built an Entra-Native Certificate Authority and CMS to easily manage the process from start to finish. The following will walk you through the steps associated with selecting and onboarding a YubiKey, the most reliable unphishable credential for the modern security practitioner.
Choosing the right YubiKey for you and your organization may seem like a daunting task, but in reality, it’s quite easy. If you’re looking to do a deep dive into how much YubiKeys cost and which ones may be best for you, check out our blog on the subject. We recommend using YubiKeys for Entra CBA because they’re easy to use, support FIDO2, and have extra attestation. No matter which one you select, you’re making an excellent choice. Pro tip: opting for the biometric keys might be overkill…
Start by registering the EZCMS application in your tenant to allow EZCMS to authenticate your users. Once the application is registered, you can go to the Azure Portal and create your EZCMS instance. After the EZCMS instance is created, and your organization settings are set, we are ready to create the Certificate Authority that will issue the smart card certificates.
If you already have a Windows ADCS Certificate Authority set up for issuing smart card certificates, you can connect EZCMS to ADCS However, if you do not have an existing CA, or want to move your infrastructure to the cloud, just set up EZCA, our cloud based certificate authority.
Now that you have created your certificate authorities, it is time to upload your CA certificates as trusted CAs to Azure. Follow these steps to get going:
1) Go to the Azure portal as a Global Administrator.
2) Select Azure Active Directory, then in the left-hand side panel select Security.
3) Select Certificate Authorities.
4) Upload the certificate for each CA in your infrastructure (Root and Issuing CAs). Note: make sure to add a publicly accessible CRL URL for Azure to validate that the certificates have not been revoked.
After setting up the Certificate Authorities that Entra should trust for user authentication, we need to set up Entra to accept certificate-based authentication as an authentication method. Here’s how it’s done.
1) Navigate to Authentication Methods inside the security section.
2) Select Policies on the left-hand side.
3) Click on certificate-based authentication.
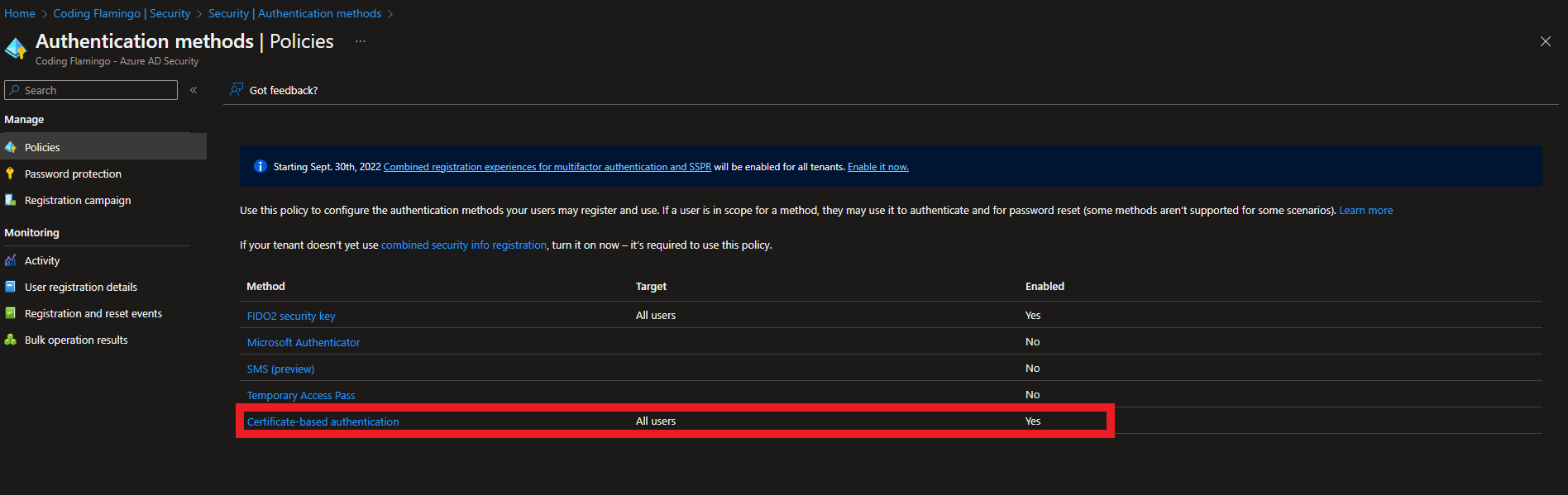
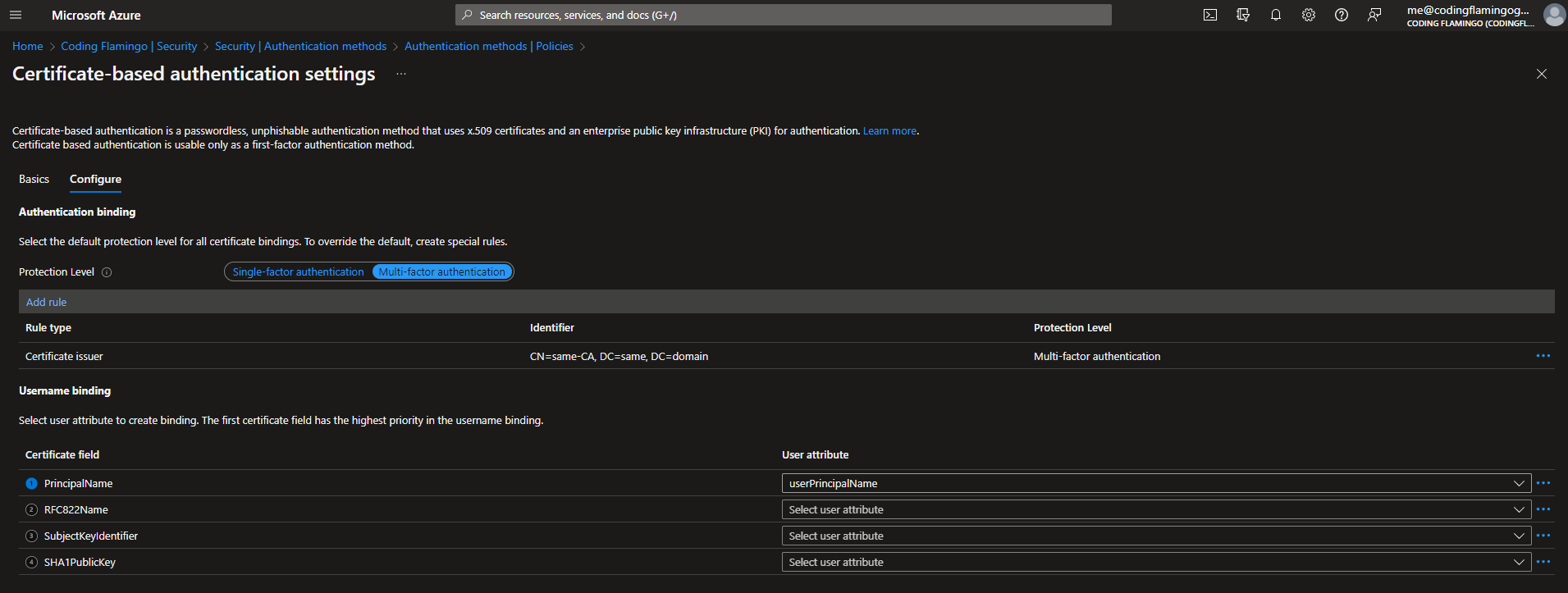
4) Click on the Configure tab.
5) Select protection level (Entra defaults to Single factor since it doesn’t know if you are just going to use a certificate without a smart card or if you are going to protect that certificate, so if you are going to use smart cards, change to multi-factor authentication).
6) In the rules section set the CAs that can issue user certificates. Note: You can also set a policy ID if you are using that CA for other certificate types but PKI best practices recommend using a dedicated CA for smart card authentication.
7) Select the username binding order (this is how the user name is added in the certificate) in this example we are going to use PrincipalName mapping to the user principal name which is what EZCMS defaults to.
EZCMS is designed to be able to onboard users from multiple tenants, so you can use it to onboard users to all your different tenants, for example at Keytos, we follow Azure security best practices and do full tenant isolation for corporate (keytos.io), test identities, and production identities and use EZCMS to onboard all of them. Follow the EZCMS documentation or the video below to register your domain.
The last step before issuing your first YubiKey is to add a test user to EZCMS and then you can assign the YubiKey to that user. Now you’re ready to issue your first YubiKey!
Once EZCMS is setup, and you have created your test YubiKey, you can test the authentication flow by:
1) Going to the azure portal in an incognito tab.
2) Entering your username.
3) Select “Use a Certificate or smart card”.
4) Select your smart card certificate.
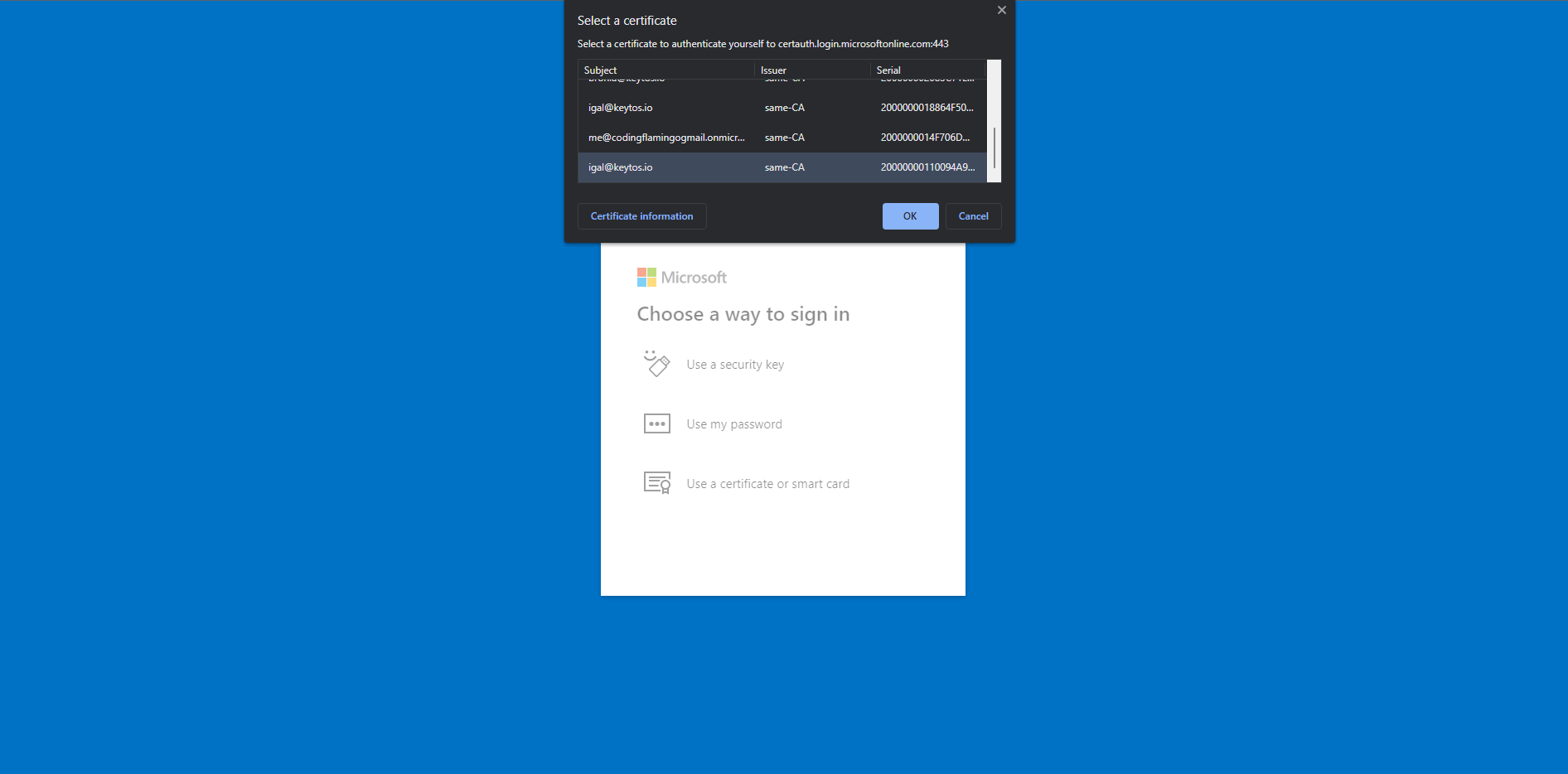
5) Enter your PIN.
6) Touch the YubiKey to complete the authentication.
7) CONGRATS! You have successfully logged in!
Now that you have successfully set up YubiKey authentication with Entra Certificate Based Authentication, you can start rolling it out to all your users. If you have any questions on how to setup Entra or Azure Certificate Based Authentication, book a free identity assessment with our identity experts.