
Unphishable Credentials For Azure and On-Premises - Cheaper and More Secure than Password-Based Authentication
Phishing Resistant Credentials For Azure and On-Premises: Cheaper and More Secure than Password-Based Authentication
Phishing has increased 47% in the past year; with over 90% of companies reporting being targeted with a phishing attack in the last year, organizations can no longer depend on education and spam filters alone to prevent attacks. With the growth of spear-phishing attacks and with the lack of response from organizations to remove dangling DNS entries, even the best-trained users and spam filters are bound to be fooled by one of these advanced attacks. The Solution? Unphishable credentials.
What Are Unphishable Credentials?
Unphishable credentials, or unphishable MFA, is a new mandate for using credentials that cannot be phished by attackers. These credentials are composed of asymmetric cryptographic keys, and this design allows authentication without ever sharing the private key thus preventing an attacker from stealing the secret. There are currently only two types of Unphishable credentials – FIDO2 and Smart Card authentication – which both work in a similar fashion; the difference is how the key is validated.
How Smart Card Authentication Works
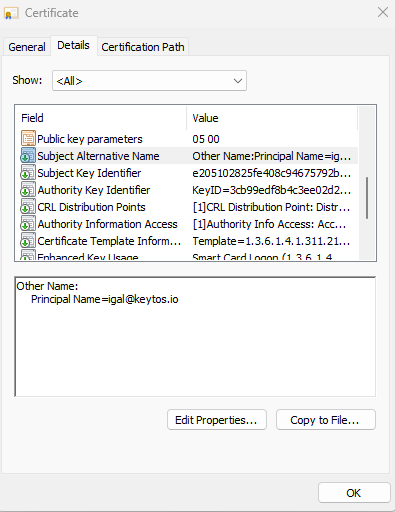
Smart card authentication is the oldest and most used unphishable authentication method and is based on X509 Certificate based authentication. When a smart card is created, a cryptographic certificate is created and added to a smart card or hardware token (YubiKeys and other hardware tokens support the PIV standard), and this certificate contains the information of the user such as username and, after KB5014754, it also contains the user ID. This certificate trust, based on the Certificate Authority (CA) that issue the certificate, enables organizations to accept authentication for users without the need to register each credential with each party. Instead, when authenticating a user, the service verifies that the certificate is issued by a trusted authority and validates the information of the user. This is like how in the real world we validate that a driver’s license is issued by the government and, hence, we trust that the person showing the ID is who they say they are.
How FIDO2 Authentication Works
FIDO2 Authentication is the simplification of smart card authentication. Before easy-to-use cloud-based certificate authorities such as EZCA, our Azure based Certificate Authority, running a secure PKI and all the infrastructure necessary to create smart cards was overly complex and only large organizations and governments could afford to have smart card authentication. To help organizations protect their infrastructure against the rise in phishing attacks, the FIDO alliance came together to implement a protocol that made it easier for everyone to use unphishable credentials: the solution was FIDO2. Under the hood, it still uses the same cryptographic authentication that makes smart card authentication so secure, but instead of needing each organization to run their own PKI, they opted for mapping the serial number of the public key to the user. While this simplified the infrastructure requirements, some centralized management such as central revocation was compromised to make this more accessible to everyone.
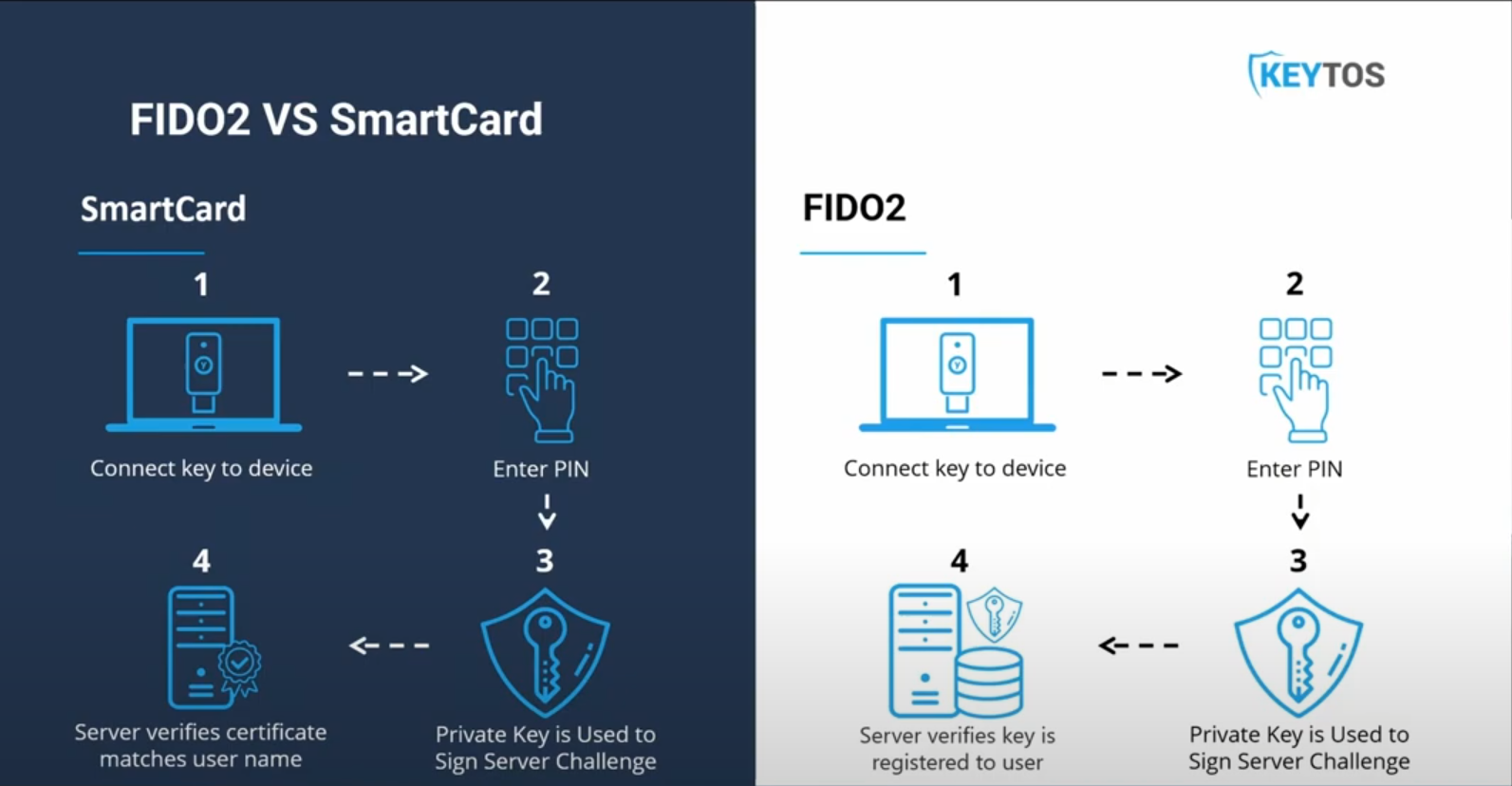
Difference between FIDO2 and Smart Card Authentication
As you can see, FIDO2 and smart card authentication both depend on the same cryptographic technology; the main difference is that smart card authentication uses X509 Certificates for validation and central management of key validity, while FIDO2 was created to remove the need to manage a PKI infrastructure and instead registers the key serial numbers and maps that to the user. While FIDO2 simplifies the onboarding process by removing the need for extra infrastructure, it makes the revocation process more complicated since the key must be removed from all services where it has been registered. While they might sound complicated, both technologies can easily be implemented with a modern CMS (Credential Management System) that automatically handles the provisioning and deprovisioning of keys as well as enables self-service onboarding for remote employees.
Misconceptions of Unphishable Credentials
Many organizations are afraid of implementing unphishable credentials due to some misconceptions caused by misinformation or outdated information. The three main reasons we hear why people are afraid of implementing this technology are: 1) “it is hard to use,” 2) “it is too expensive,” and 3) “we already have MFA and it is the same.” Let’s break it down below and talk about how these are not true.
1. Unphishable Credentials are Hard to Use
While it is a different sign-in experience than what users are accustomed to, once they understand how it works, studies show that unphishable credentials have 4x faster logins than other MFA methods. If we think about it, this just makes sense. Regular MFA requires you to enter your password, then send a notification to another device or get a code from a different device and enter that information, versus with unphishable credentials all you need to do is connect the token and enter your pin. This is not only faster, but it also removes the need to remember long and complex passwords.
2. Unphishable Credentials are Expensive
One of the main pushbacks to unphishable credentials is the upfront cost. Hardware keys cost around $40 per key, and then there is the cost of the CMS, which is usually around $2-4 per user per month; however, organizations are currently paying 3 times as much in lost productivity due to password resets. Foresters estimates the cost of each password reset as $75 with organizations having quarterly password rotations (this is without counting any forgotten passwords that take more time and money since helpdesks must be involved), so the cost of using passwords per user is $300 per year. Making unphishable credentials proves to be not only more secure but also a cheaper alternative to other MFA methods.
3. Unphishable Credentials are as Secure as Other MFA Methods
The biggest security myth is that all multi-factor authentication methods are equal. While Authenticator applications are way more secure than SMS-based authentication, they are still vulnerable to phishing attacks as well as vishing attacks. See the video below on how unphishable credentials can stop attacks that regular MFA cannot stop.
Implement Unphishable Credentials with Azure AD
As aforementioned, implementing passwordless authentication is easier than you think. Watch the video below where our CEO talks with a Microsoft identity expert on how it is time to go passwordless with Keytos and Microsoft. When you are ready to implement unphishable credentials, schedule a free call with our identity experts today!


