
Certificate Authority in Azure Key Vault – How to Protect Your Keys
How to Move a Certificate Authority to Azure PKI
As more and more systems are being moved from on-premises to the cloud, more people are considering how to move certificate authorities to Azure. Browsing through Microsoft forums from even years ago, we can see that people want such things as a new PKI that connects to Intune and Azure Key Vault and having Key Vault act as a KSP to run certificate authorities in the cloud. In this blog, we will run through some alternatives to run CAs in the cloud in order to best help your organization modernize its PKI.
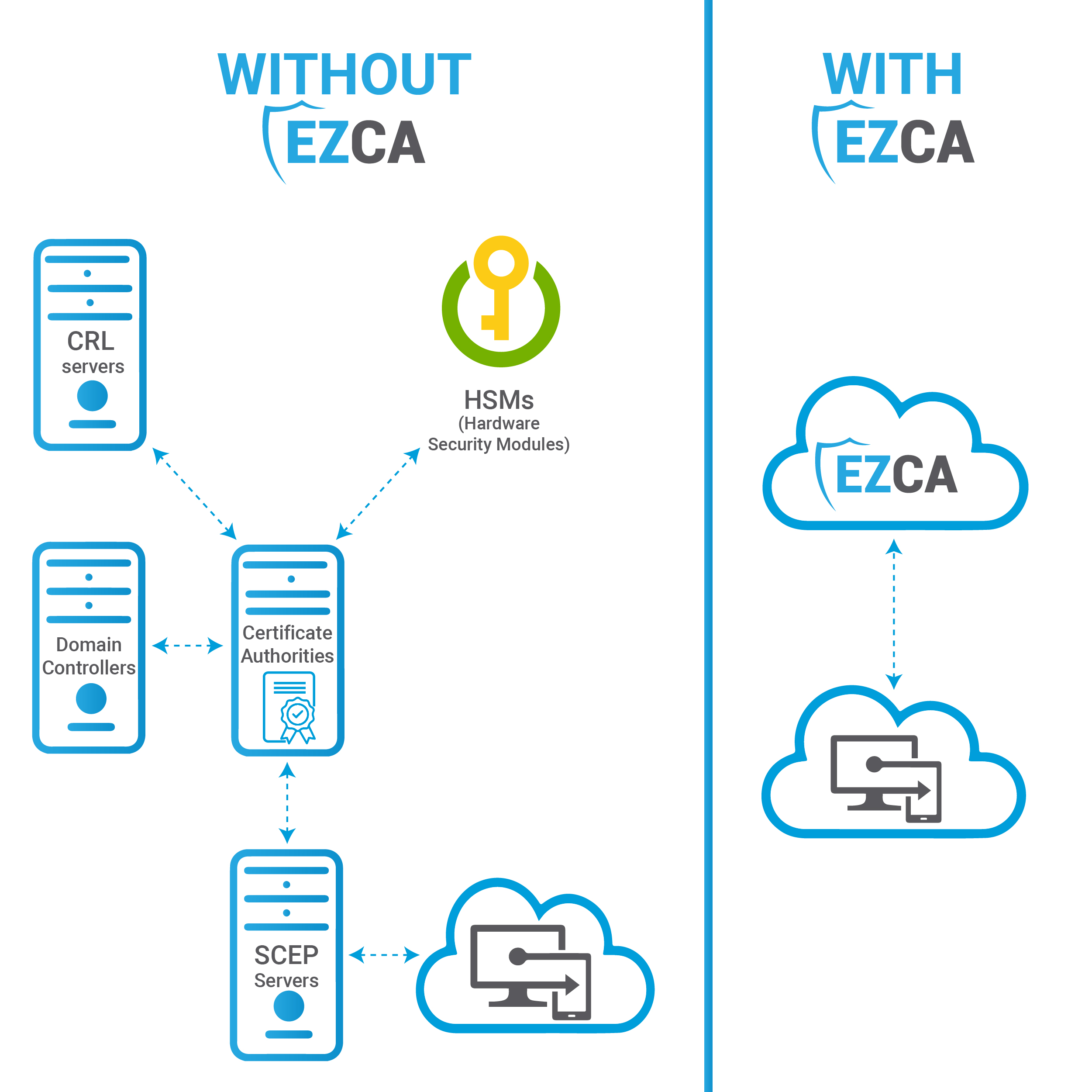
Running a Certificate Authority in an Azure VM
The first thing that you probably think of when management asks you to move your CAs to the cloud from on-premises is to simply run your on-prem infrastructure in the cloud. Easy, right? Unfortunately, while this method is comfortable and familiar, there are certain things to look out for. For example, you ought to watch out for any CA misconfigurations that can cause a breach and the need to have an express route connection to an existing on-premises HSM in order to secure your keys. In short, running certification authorities in an Azure VM is neither the most economical nor scalable method of migrating your PKI to the cloud.
Considering Using a Cloud-Based PKI?
Since Microsoft has declared that they will not build an Azure PKI, a handful of Microsoft partners have, thus, created their own PKI solutions in Azure. Of all of these offerings, did you know that only one is fully integrated with Azure? That’s right, and that PKI is EZCA by Keytos. With EZCA’s native Azure integrations, you can connect to any Azure resource the same way you would natively from any other Azure resource.
Do You Want to Issue Intune SCEP Certificates?
With the recent hype around zero-trust, many companies are now making their device authentication CBA (certificate-based authentication). With Intune SCEP, organizations can disperse certificates to user devices. EZCA connects to Intune as a Microsoft-approved PKI, allowing you to have an entirely cloud-based infrastructure and to set up your Intune cloud-based PKI in mere hours.
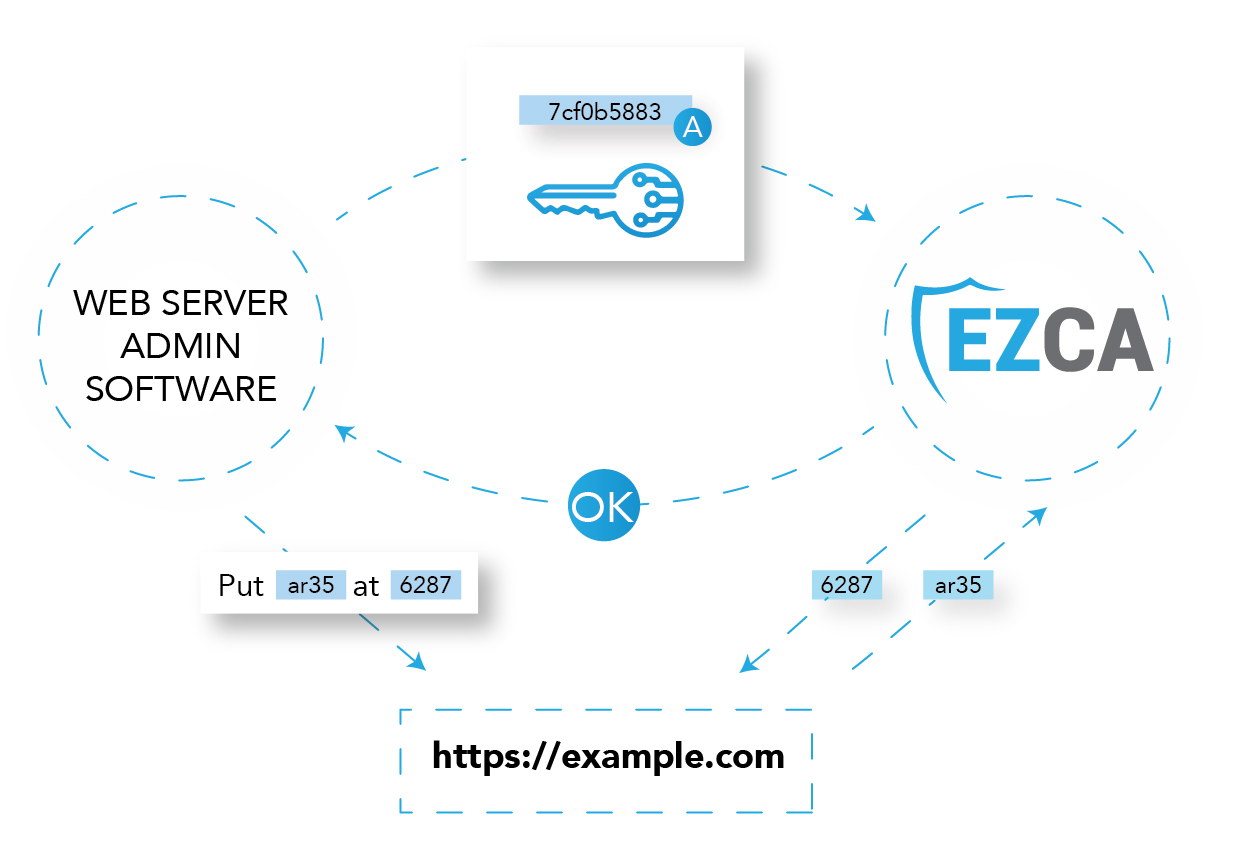
Private Certificate Support from ACME
Due to the rapid increase in SSL certificates, it has simply become unfeasible for PKI teams to check every single certificate request and to then issue them manually to users. As a result, ACME was developed to automate the process, enabling the CA to confirm domain ownership by having the applicant insert a particular challenge into the domain. EZCA provides the option to activate ACME within your private network, either through its cloud-based CAs that support ACME or by modernizing your current certificate authorities to become ACME-compatible.
Automatic Certificate Rotation in Azure Key Vault
As cloud usage continues to rise, handling certificates manually is no longer feasible. To address this challenge, we’ve partnered with Azure Key Vault! This integration allows Microsoft users to seamlessly and automatically rotate their private CA certificates in the cloud.
Automatic Certificate Renewal for Entra ID Application
Regrettably, Entra ID applications have yet to accommodate subject-based authentication for certificate validation. This implies that, with every certificate renewal, a new thumbprint must be logged in Entra ID. Aiming to streamline this process for organizations, we’ve upgraded our Azure Key Vault certificate rotation feature to include an auto-registration feature for the fresh certificate in Entra ID, becoming the first tool to facilitate automatic certificate rotation for Entra ID applications.
One-Click CBA with Azure IoT
Using CBA for Azure IoT is the safest method to connect your IoT devices to Azure. For those considering using their CA to distribute IoT certificates, we’ve compiled an IoT security best practices guide. Additionally, we offer a one-click integration with Azure IoT. This ensures organizations can commence their IoT projects by adhering to security standards and employing a certificate authority tailored to accommodate their growth.
Open-Source Tools and NuGet Package
While modern protocols like ACME and Azure integrations may suffice for a majority of Azure users, our goal is to ensure every user establishes a secure PKI within Azure. That’s the driving force behind our development of open-source certificate rotation tools and a popular NuGet package that offers one-line certificate requests. From engineers overseeing older systems to those shaping the future’s infrastructure, EZCA and Azure stand ready to help.
Integration with Entra CBA
EZCA smoothly integrates with EZCMS, our passwordless onboarding tool, to allow businesses to adopt a completely passwordless approach in Azure. This combination manages user onboarding, the distribution of hardware keys, and it also provides support for the Microsoft Authenticator app! For organizations aiming to transition to a passwordless system, these tools are indispensable.
Manage Your Public CA Certificates
For those who have read this far and wish EZCA could also handle your public certificates, good news awaits! We recently introduced a feature in EZCA for public SSL certificate management! Now, all the impressive integrations you’ve learned about can be applied to your public certificate management as well.
Final Thoughts on Cloud Migration
The shift to the cloud from on-premises is inevitable, but it brings along fresh complexities and uncertainties, particularly regarding secure PKI migrations. While the conventional method of operating certificate authorities in Azure VM might be a familiar route, it isn’t always the most optimal or secure choice by any means. Contemporary solutions, like cloud-based PKIs, promise increased adaptability, integration, and protection, especially when designed for Azure settings. EZCA emerges as an all-encompassing tool, boasting innate Azure integrations and automated answers to current-day hurdles. Keytos’ dedication to flexibility and multifaceted approaches shines through with our open-source utilities and NuGet package, ensuring we address the needs of a broad spectrum of Azure users. For organizations aiming to refine and bolster their PKI within Azure, leveraging tools with EZCA, which are deeply rooted in and aware of cloud nuances, can ensure a more fluid shift and a fortified digital future.


