
Does Microsoft Have a Cloud PKI?
Microsoft Cloud PKI in 2024
Did you know that Microsoft finally announced their plan to launch a Cloud PKI? Well, they sure did! Coming in February of 2024 (fingers crossed…) the Intune Suite will offer “Microsoft Cloud PKI,” a cloud-based public key infrastructure (PKI) service that will handle all aspects of the certificate lifecycle for Intune managed devices. Microsoft has also stated that the tool will adhere to PKI industry standards while being simple to set up and manage. Awesome! What are some of the other things they’re bragging about? No on-premises servers to deploy or manage, no certificate connectors, no firewalls or proxies. That all sounds pretty cool, doesn’t it? So far, so good! Microsoft Cloud PKI will also take care of “all the other complexities” around standing up a PKI in a matter of minutes. Take a quick look at their announcement video below!
What Does Microsoft Cloud PKI Mean for the Security Community?
Anyone with their “ear-to-the-ground” within the Azure Security community will tell you, they’ve been looking forward to this announcement for longer than they’d like to admit. It’s not like PKI is a new concept, so security engineers have been relying on 3rd party PKI tools to satisfy their PKI requirements in recent years. Frankly, it’s very surprising that this is the first time that Microsoft has decided to wade into the waters of cloud public key infrastructure. So, you’d think that the community would be incredibly enthusiastic about the announcement, right? Turns out, not so much…
The well-intentioned folks over at Microsoft forgot one thing about the security community…they’re some of the most forward-thinking, resourceful, and practical people on the face of the Earth. They’re not the kind of crowd that’s going to get doe-eyed about press release that “promises” to deliver a solution next year. They’ve spent the past however-many years becoming experts in PKI, working with 3rd party PKI vendors on integrations, and collaborating internally to ensure the security of their data. The security community wasted absolutely no time letting Microsoft know about the shortcomings of Microsoft Cloud PKI for Intune in the comments sections almost everywhere across the internet.
What’s the Catch with Microsoft Cloud PKI?
As mentioned above, the comments section(s) of every prominent discussion forum are littered with questions about the granular details about the new tool. In fact, one user has “several questions” about the tool. If you ask me, this is just an exceptionally awesome, passive aggressive way in which to casually point out the PKI’s shortcomings.
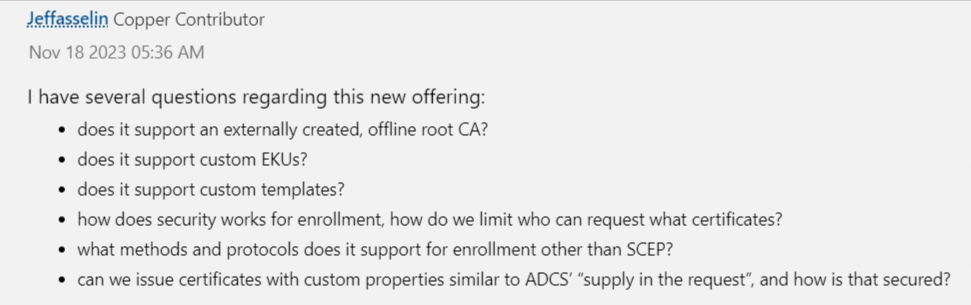
Pretty funny, right? So, what else are people concerned about?
Azure IoT Hub Integration: After Intune, the biggest use for certificates in Azure is Azure IoT Hub. Millions of certificates are issued and used for authentication with our Azure IoT Hub CA. Having a private CA that supports IoT devices could help Microsoft unblock billions of dollars of revenue in other cloud services such as datalake, IoT Central, etc.
Non-Intune SCEP: If you read closely, you’ll notice that the announcement only talks about issuing certificates through Intune SCEP. There’s been no indication that SCEP certificates that are not managed through Intune, such as network devices, will be supported. This could be a major issue for organizations that have already figured out how to integrate with ManageEngine or other MDM tools. A quick look at one of the more prominent Azure discussion forums shows that SCEP capabilities have been a key concern/touchy subject for quite some time now.
OCSP: One of the most popular ways to monitor and manage certificate revocation is the Online Certificate Status Protocol (OCSP). Unlike more traditional methods like CRLs, OCSP was designed specifically for retrieving the revocation status of individual certificates, making it much more efficient than its traditional counterpart. Unfortunately, this too is not included in Microsoft’s Cloud PKI for Intune.
Smartcard Certificates: This omission is really astonishing! Smartcards have been one of the most widely used phishing resistant authentication methods for YEARS. Microsoft themselves added Azure CBA Support last year, and even mention it in this blog; however, this is for single factor certificates.
ACME: Automated Certificate Management Environment (ACME) is an exceptionally useful protocol designed to automate the interaction the certificate issuance for web servers. The primary motivation behind leveraging ACME is to simplify the process of obtaining, renewing, and managing SSL/TLS certificates. Long story short, having ACME support in a private CA is a must in this day and age, and it’s strange that this isn’t included in Microsoft Cloud PKI for Intune.
Azure Key Vault Certificate Rotation: AKV has supported Automated certificate rotation for DigiCert for over 5 years, so adding a similar functionality for private certificates would make this new cloud offering a great option. Unfortunately, it doesn’t look like that’s going to happen.
Complete PKI Solution for Azure – EZCA by Keytos
As you can plainly see, the initial reaction from the security community hasn’t exactly been warm. The individuals responsible for PKI within their organizations have, for better or worse, been looking up to the good people at Microsoft as something of the de facto thought leaders and experts in the space. They’ve been left exceptionally disappointed by the announcement, primarily because they’ve been using more complete solutions like EZCA for years now. Built by former Microsoft PKI Engineers, Keytos has beaten Microsoft to the punch when it comes to developing the first Azure Native CA. Take a look at how easy it is to get started!


