
Cloud RADIUS for Microsoft Cloud PKI for Intune
How to Set Up Wi-Fi Authentication with X509 Certificates from Microsoft Cloud PKI for Intune and Cloud RADIUS
Congratulations! You have moved your PKI to the Cloud and you have set up your Microsoft Cloud PKI for Microsoft Intune, now you want to use these certificates to authenticate your users to your Wi-Fi network. One way to move our RADIUS to the cloud is to move your NPS Server to the cloud, but then you are still managing “On-Prem” Infrastructure and you are not taking advantage of the cloud. Instead, we recommend using a Cloud RADIUS Service that can speak to your Intune Cloud PKI and authenticate your users to your network. In this blog, we will cover how you can set up Wi-Fi authentication with X509 certificates from Intune Cloud PKI and Cloud RADIUS.
How To Setup Network Authentication With Intune Cloud PKI
This blog Assumes that you have already setup your Intune Cloud PKI and you have created your Intune SCEP Profiles. If you haven’t done this yet, here is a video setup of EZRADIUS start to finish that guides you through the process using EZCA but it is fairly similar when using Intune PKI, just switch the EZCA parts for Intune PKI. If you have already setup your Intune PKI, you can follow the steps (or video) below to set up Wi-Fi authentication with X509 certificates from Intune Cloud PKI and Cloud RADIUS.
How To Create a Cloud RADIUS Service for Microsoft Cloud PKI for Intune
The first step is to create the Cloud RADIUS Service, for this you must register the two Keytos Apps In your Tenant using a global administrator account, then you can Create your cloud RADIUS in Azure. Once your Cloud RADIUS is created, you will need to Create a RADIUS Certificate Policy that will allow your users to authenticate to the network using their Intune PKI Certificates.
Common Issues When Setting Up Wi-Fi Authentication with Intune Cloud PKI
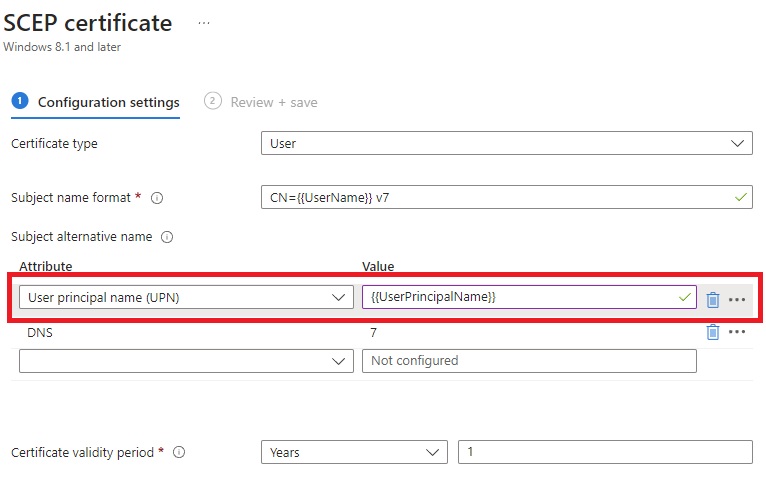
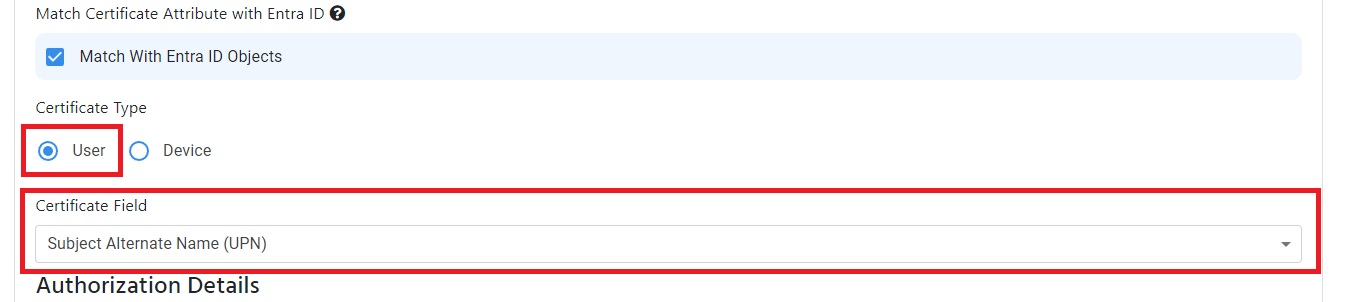
One of the most common issue we see when this is being setup, is the mismatch between the certificate and the RADIUS Policy. This can be caused by the certificate not having the correct fields or the RADIUS Policy not being set up correctly. To avoid this, please validate the field where you have your user or Device ID in your SCEP policy and make sure it matches the field in your RADIUS Policy. Below is an example where the User UPN is put on the certificate subject Alternate name for UPN and the RADIUS Policy is set to match the UPN with the certificate.
Intune SCEP policy for User
EZRADIUS Cloud RADIUS Policy for Intune Cloud PKI
How To Connect RADIUS Service to Network Infrastructure
Now that we have the RADIUS service squared away, we have to connect it to the network infrastructure in our RADIUS documentation we have many guides for how to connect different network devices to RADIUS. Once it is all connected, you are good to go and can authenticate with certificates. If you have any questions, feel free to schedule a meeting with one of our identity experts where one of our engineers can help you understand how EZRADIUS will work with Intune PKI and for your specific use case, and answer any other questions you might have about securing wi-fi access for your organization using certificates!


