How To Create Intune SCEP Profiles for Windows Devices
In this page we will guide you on how to create an Intune profile to issue X509 certificates either for devices or users using SCEP for Windows.
Prerequisites
Create Trusted Certificate Profile in Intune
The first step on getting your certificates distributed to your devices, is trusting the issuing CA certificate chain. The following steps will guide you on how to do that for your Windows devices.
- Go to https://aka.ms/intuneportal
- Select: Devices -> Windows -> Configuration profiles.
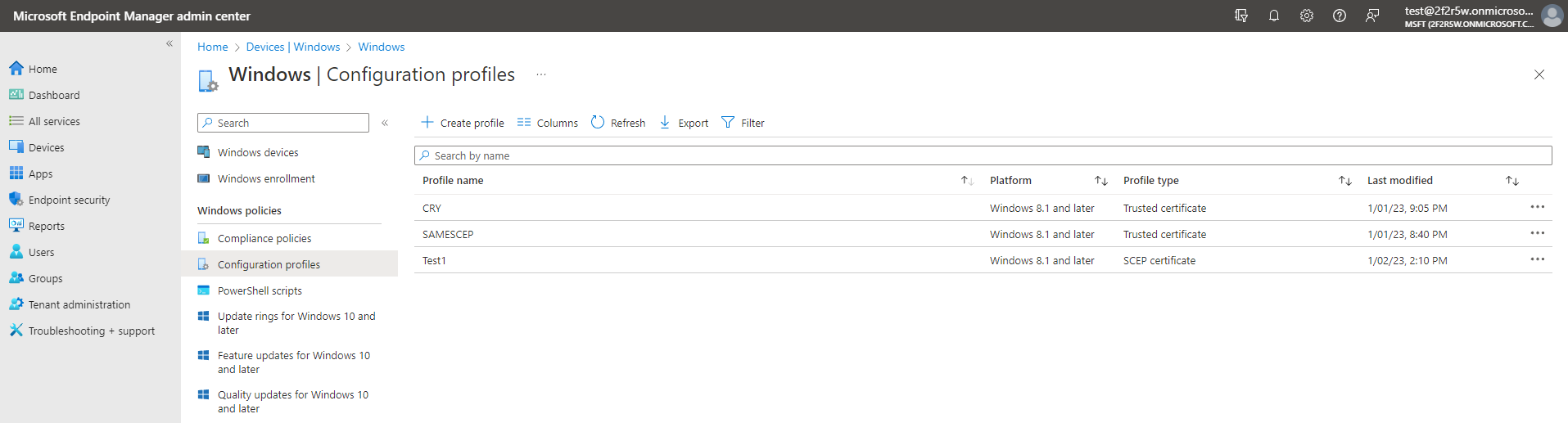
- Click the “Create profile” button.
- Select your Windows Platform.
- Select “Templates” as the profile type.
- Select the “Trusted Certificate” template.
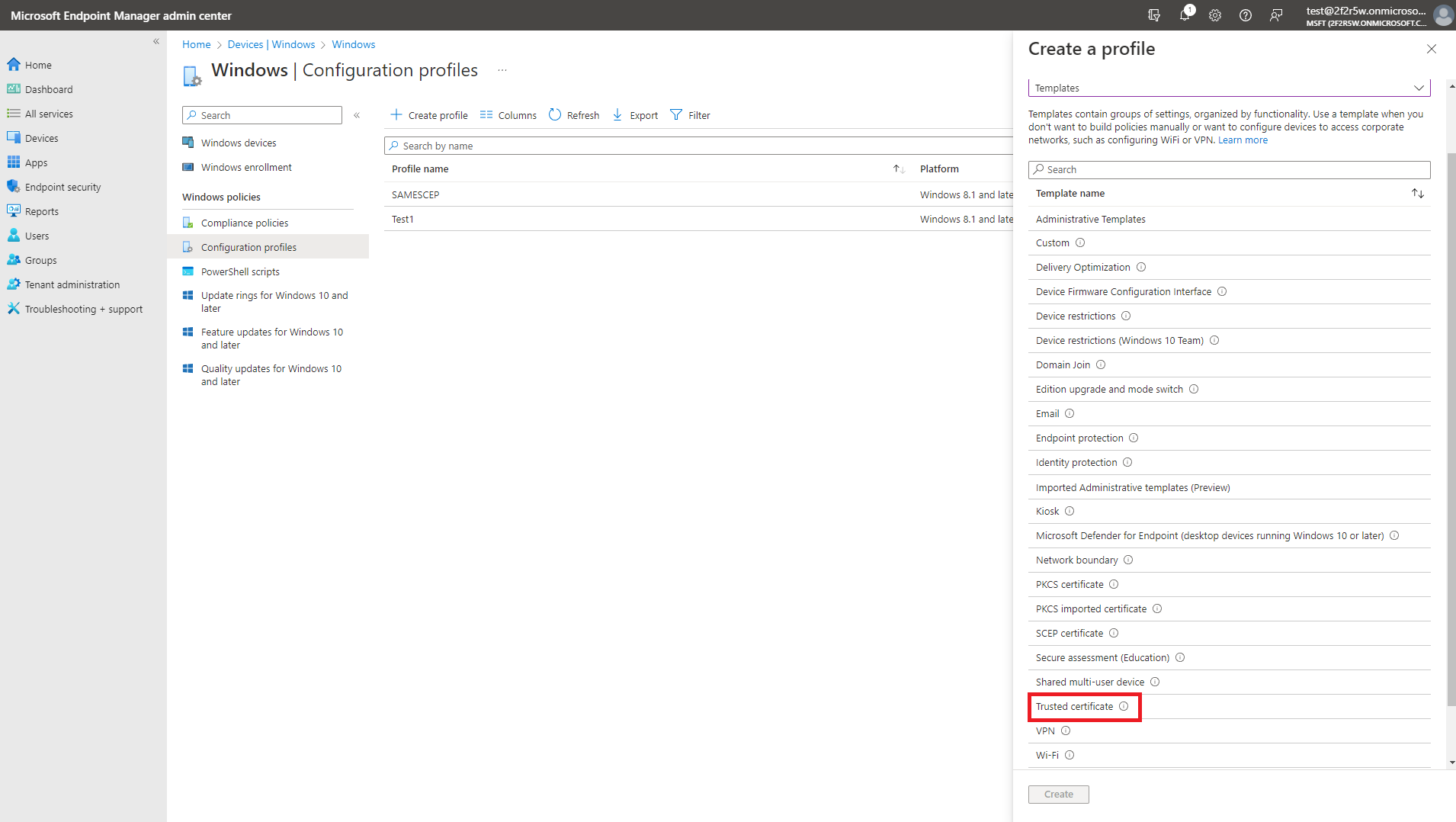
- Click create.
- Enter the name for this Intune certificate profile.
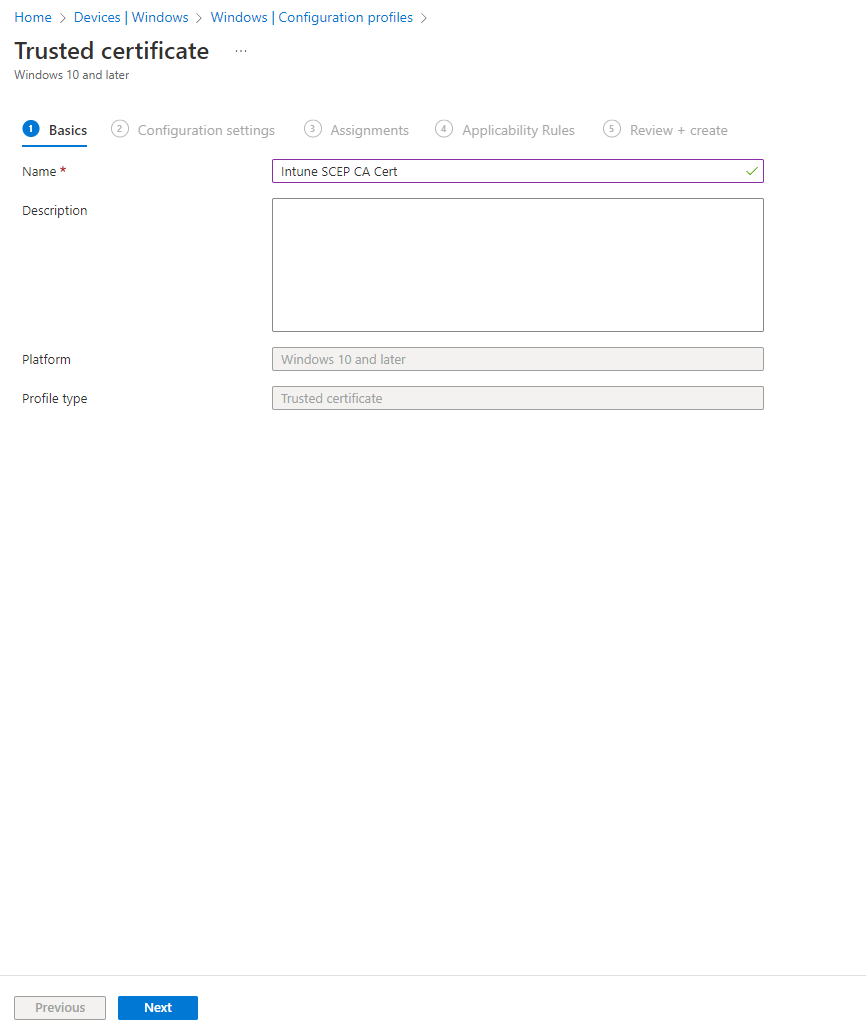
- Upload the CA Certificate you downloaded from EZCA.
- Select your Assignment rules.
- Create the configuration profile. Now all the devices in scope will trust certificates issued by this CA.
- Repeat these steps for all the CA certificates on the chain (Your Root CA, and Issuing CA), if you only created a Root issuing CA, continue to create the scep profiles for your devices.
How to Create Intune SCEP Profile For Device Certificates
If you are looking for user certificates skip to the next section
- Once you have created your trusted certificate profile, go back to the Windows configuration profiles page and click the “Create profile” button.
- Select your Windows Platform.
- Select “Templates” as the profile type.
- Select the “SCEP Certificate” template.
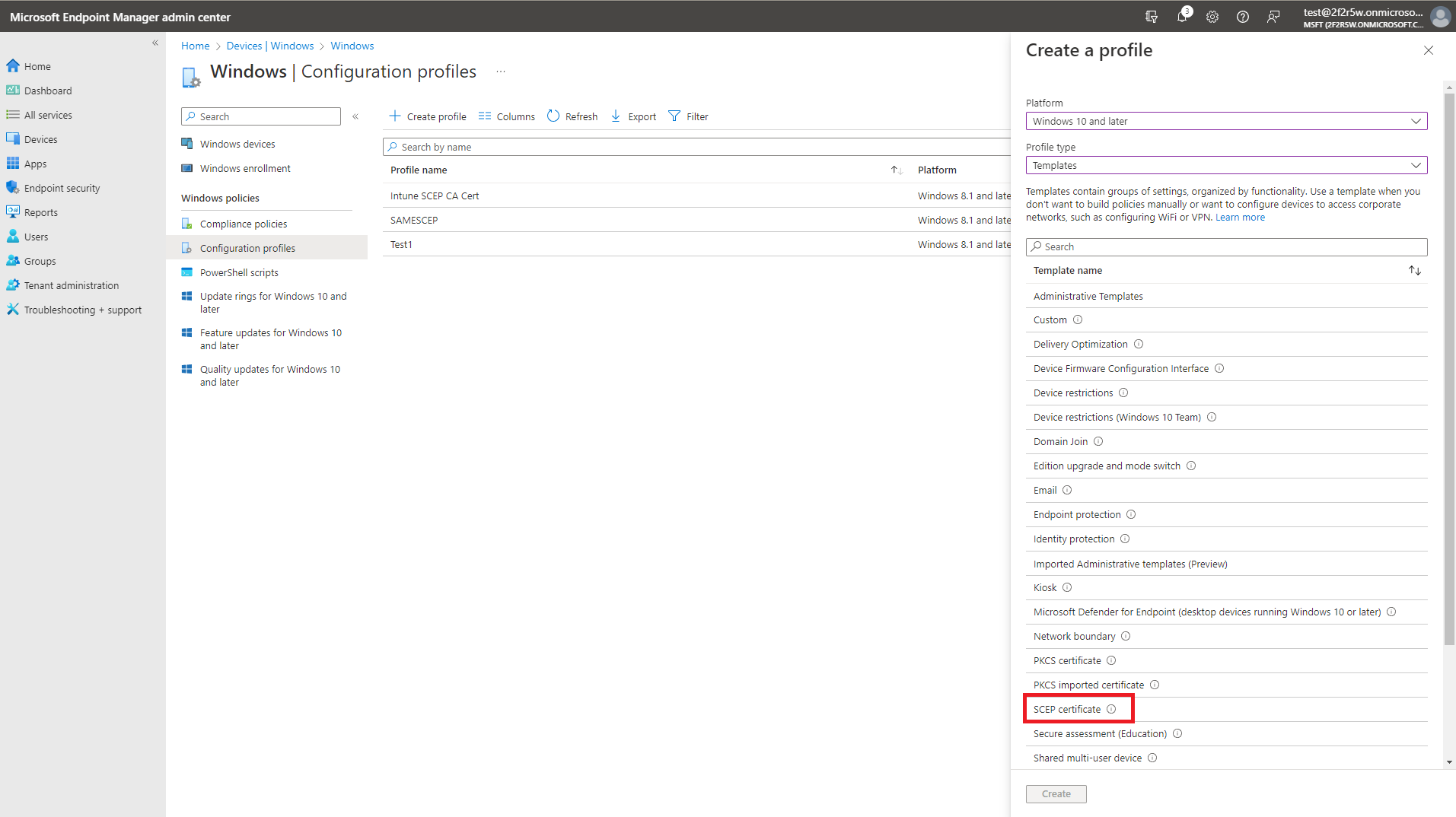
- Click create.
- Enter the name for this Intune SCEP profile.
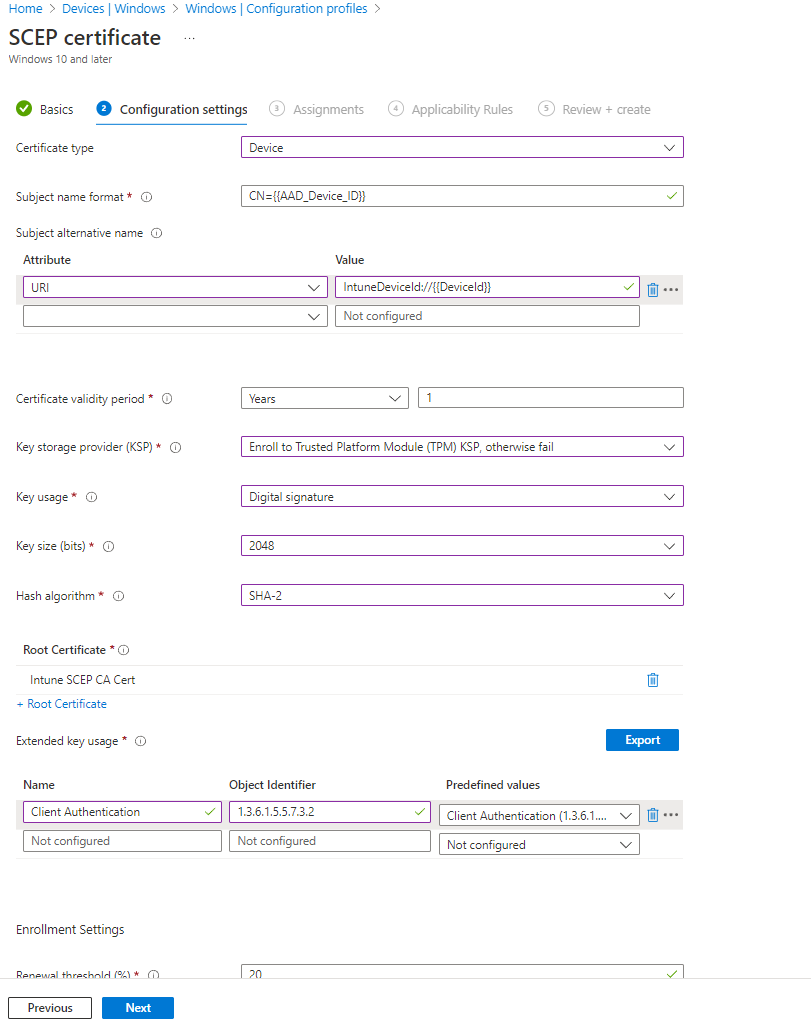
- In configuration settings, we are going to select Device as the certificate type.
- For Subject name we will enter
CN={{AAD_Device_ID}}orCN={{DeviceId}} - In the Subject Alternate Name we will select the URI Attribute and enter
IntuneDeviceId://{{DeviceId}}as the value. - If the Subject name is not
CN={{AAD_Device_ID}}we recommend adding a second subject alternate name with URIAzureDeviceId://{{AAD_Device_ID}}as the value, this will ensure that if it is a hybrid joined machine it will get the required extension for KB5014754. - For Certificate Validity period enter the period you entered in EZCA.
EZCA will always use the certificate validity period you set in the CA, if you set a different value in Intune, it will be ignored (This is due to this value not being supported in Apple devices). If you want to change the validity period for a specific Intune profile, you can add a DNS SubjAltName with the value
keytosEZCAValidity=365where the number is the number of days for that specific certificate (This number has to be lower than the number set in EZCA, if it is larger it will be ignored).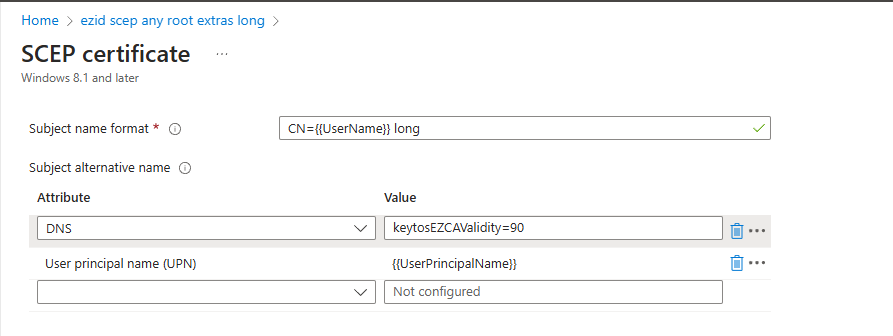
- For Key Storage Provider (KSP) We recommend “Enroll to Trusted Platform Module (TPM) KSP, otherwise fail” however, if you want to support PCs without TPM and are ok with the risk of software based keys, feel free to use one of the other options.
Some customers have reported issues with the TPM stored certificates not being accessible by some applications such as VPN clients (Including Azure VPN), if you are experiencing this issue, you can use the “Enroll to Software KSP” option.
- For Key Usage select bot “Digital Signature” and “Key Encipherment”
- Key Size select “2048”.
- Hash Algorithm “SHA-2”
- In the root certificate field click the “+ Root Certificate” link and select the CA we created in the “Create Trusted Certificate Profile” section.
While it says Root Certificate, If you created a Subordinate/Issuing CA, you must select the Issuing CA profile not the root CA.
- For Extended key Usage select “Client Authentication (1.3.6.1.5.5.7.3.2)”
- Feel free to leave the renewal percentage at 20% or increase it to a value you feel comfortable with.
- Now your Setup should look something like this:
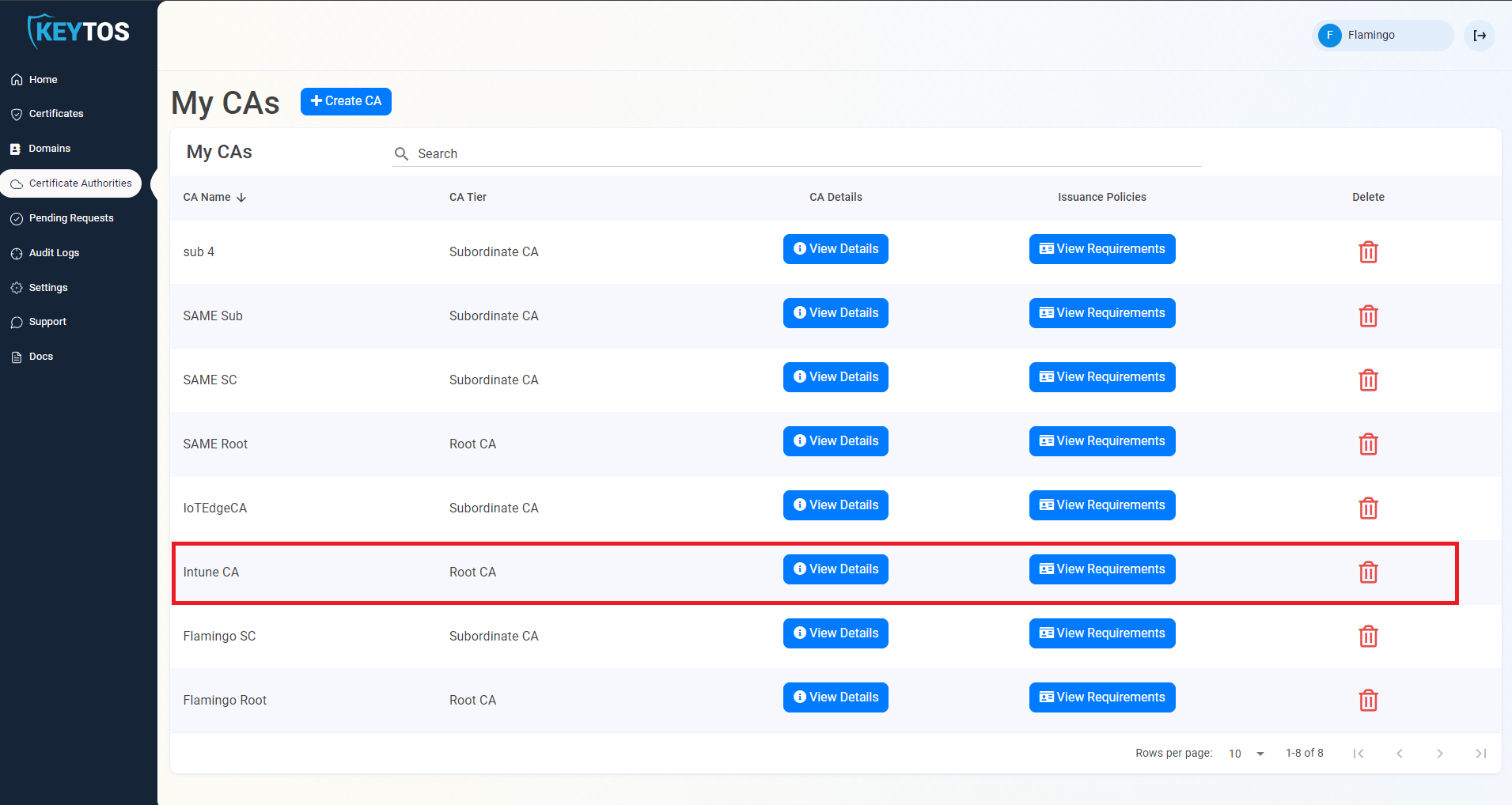
- The Last step is to get the SCEP Server URLs from EZCA. For this we will go back to your EZCA Portal, Click on Certificate Authorities and Select the “View Requirements” button on your Intune CA.
- Copy the SCEP URL.
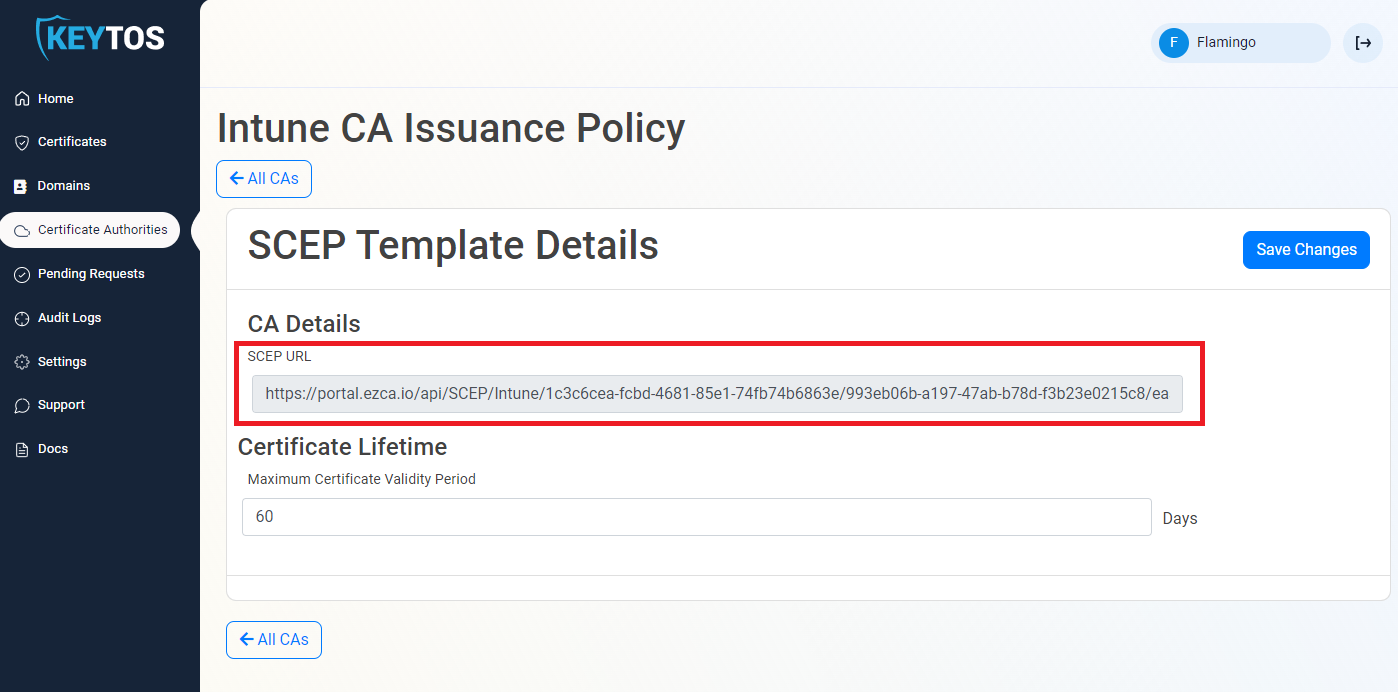
- Go back to your Intune Portal tab, and paste the URL in the “SCEP Server URLs” section.
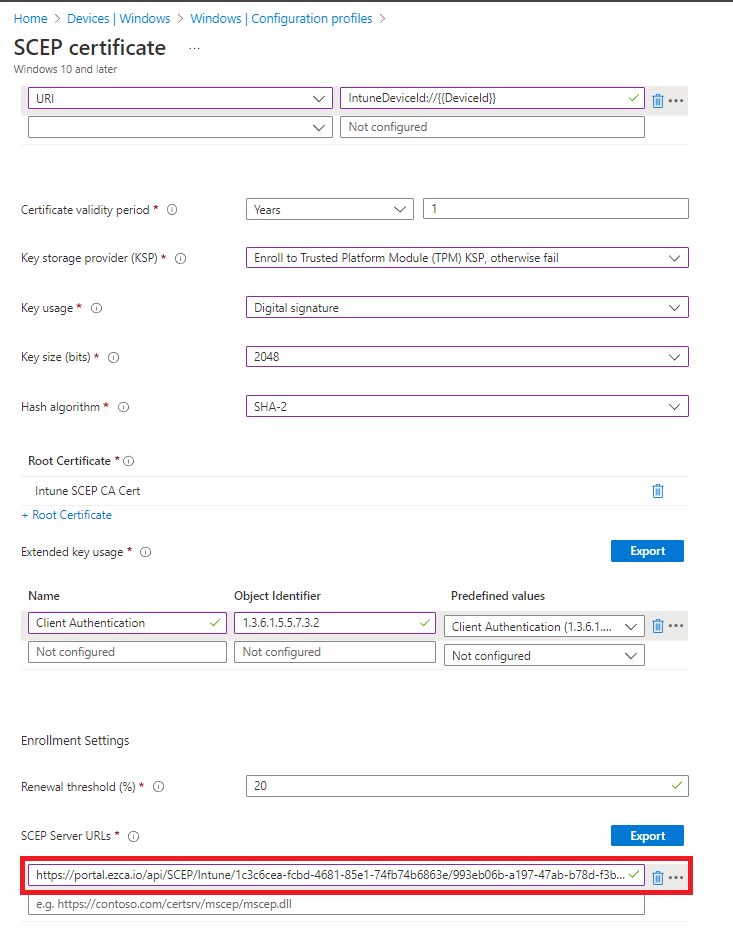
- Click Next.
- Select the devices or groups you want to apply this profile to, Once the assignments are added, review and create the policy.
How to Create Intune SCEP Profile For User Certificates
- Once you have created your trusted certificate profile, go back to the Windows configuration profiles page and click the “Create profile” button.
- Select your Windows Platform.
- Select “Templates” as the profile type.
- Select the “SCEP Certificate” template.

- Click create.
- Enter the name for this Intune SCEP profile.
- In configuration settings, we are going to select User as the certificate type.
- For Subject name we will leave
CN={{UserName}},E={{EmailAddress}} - In the Subject Alternate Name we will select the “User Principal Name (UPN)” Attribute and enter
{{UserPrincipalName}}as the value. - For Certificate Validity period enter the period you entered in EZCA.
EZCA will always use the certificate validity period you set in the CA, if you set a different value in Intune, it will be ignored (This is due to this value not being supported in Apple devices). If you want to change the validity period for a specific Intune profile, you can add a DNS SubjAltName with the value
keytosEZCAValidity=365where the number is the number of days for that specific certificate (This number has to be lower than the number set in EZCA, if it is larger it will be ignored).
- For Key Storage Provider (KSP) We recommend either “Enroll to Trusted Platform Module (TPM) KSP, otherwise fail” or “Enroll to Software based KSP” depending on how you want to use this certificate. However, if you want to support PCs without TPM and are ok with the risk of software based keys, feel free to use one of the other options.
Some customers have reported issues with the TPM stored certificates not being accessible by some applications such as VPN clients (Including Azure VPN), if you are experiencing this issue, you can use the “Enroll to Software KSP” option.
- For Key Usage select bot “Digital Signature” and “Key Encipherment”
- Key Size select “2048”.
- Hash Algorithm “SHA-2”
- In the root certificate field click the “+ Root Certificate” link and select the CA we created in the “Create Trusted Certificate Profile” section.
While it says Root Certificate, If you created a Subordinate/Issuing CA, you must select the Issuing CA profile not the root CA.
- For Extended key Usage select “Client Authentication (1.3.6.1.5.5.7.3.2)”
- Feel free to leave the renewal percentage at 20% or increase it to a value you feel comfortable with.
- Now your Setup should look something like this:
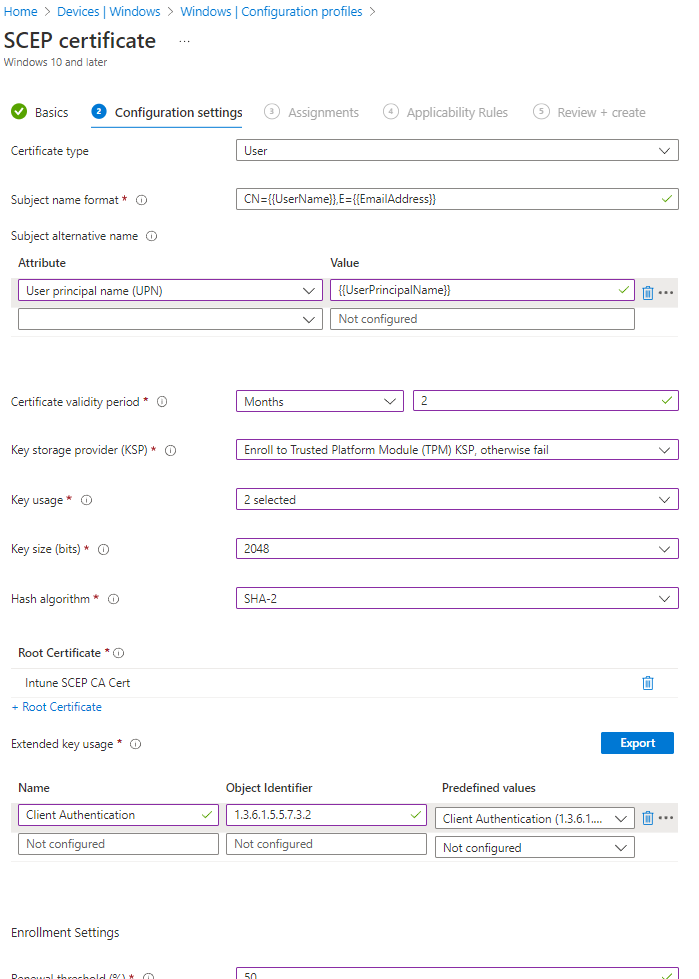
- The Last step is to get the SCEP Server URLs from EZCA. For this we will go back to your EZCA Portal, Click on Certificate Authorities and Select the “View Requirements” button on your Intune CA.

- Copy the SCEP URL.

- Go back to your Intune Portal tab, and paste the URL in the “SCEP Server URLs” section.

- Click Next.
- Select the devices or groups you want to apply this profile to, Once the assignments are added, review and create the policy.