
What Are the Best Phishing Resistant Authentication Methods?
FIDO2 and Smartcard Authentication are the Best Phishing Resistant Authentication Methods
Choosing to adopt a phishing-resistant authentication method is one thing – figuring out the best way to implement said method is an entirely different challenge. In this blog, we will be outlining the key advantages of the two leading phishing-resistant authentication methods: FIDO2 and Smartcard authentication.
FIDO2 Authentication
What is FIDO2?
You can check out our blog on “what is FIDO2” for a true deep dive into the subject, but for the purposes of this article, let’s look at a general overview:
FIDO2 stands for “Fast Identity Online 2” and it is an evolution of the FIDO standards, aimed at enhancing online authentication methods. Developed by the FIDO Alliance, FIDO2 seeks to replace traditional password-based authentication with more secure and user-friendly alternatives. This standard leverages devices like smartphones and laptops, equipped with biometric features or security keys, for authentication in both mobile and desktop environments. The key motivation behind FIDO2 is to counter the inherent weaknesses of passwords and introduce a more robust form of user verification, reducing the risk of online fraud.
Smartcard Authentication
What is Smartcard Authentication?
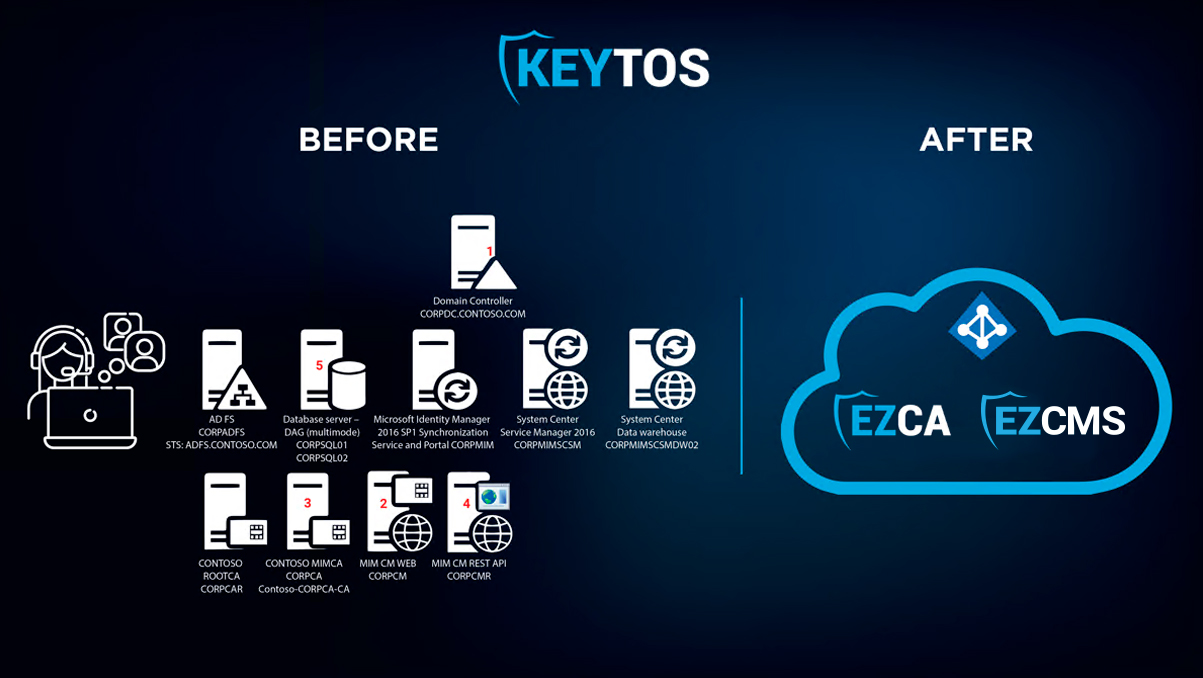
Smartcard authentication, recognized as the first-ever phishing-resistant authentication method, is a highly secure system that has been utilized globally by governments for over two decades. It is based on X.509 certificates, a standard format for public key certificates, which are crucial for establishing secure communications in networked environments. Despite being considered the most secure authentication method available today, smartcard authentication is also known for its complexity in both implementation and management. Historically, the deployment of a simple smartcard authentication solution necessitated extensive infrastructure, often involving more than ten servers! This complexity reflects the robust security measures that underpin this advanced authentication technology, ensuring a high level of security in sensitive and critical applications.
How Does Entra CBA Make Smartcard Authentication Easier?
Due to the Executive order 14028 where it required centralized identity management in the cloud, Microsoft introduced Entra CBA. Entra CBA removes the need for all the servers and complexities and makes smartcard authentication as simple as clicking some check boxes on Entra ID, Don’t believe me? Check out our guide on enabling Entra CBA, this plus the work of Microsoft partners such as Keytos creating Azure based PKI solutions and Smartcard onboarding technology allows any organization to enable government grade phishing-resistant authentication in minutes.
What Makes Smartcard Authentication Phishing Resistant?
Smartcard authentication’s resistance to phishing attacks stems from its reliance on cryptographic certificates, which are securely embedded in the smartcard or hardware tokens like YubiKeys. These certificates, conforming to standards like PIV, condense crucial user information, including the username and – following the KB5014754 update – the user ID. The foundation of Smartcard authentication lies in the trust established by the issuing CA; this trust mechanism allows organizations to authenticate users without needing to individually register each credential with every involved party. During the authentication process, instead of relying on potentially vulnerable user-inputted information like passwords, the service simply verifies that the certificate has been issued by a trusted CA and validates the user’s information contained within it. This process is similar to how we trust a driver’s license: when someone shows us a government-issued ID, we accept that person’s identity based on the trust in the issuing authority (the government). This is how Smartcard authentication effectively counters phishing, as the authentication doesn’t depend on credentials that can be easily stolen or manipulated.
Which Phishing-Resistant Authentication Method Should You Use?
If you’re struggling to choose between FIDO2 and Smartcard authentication for your organization, you’re in luck – you don’t have to choose! We strongly recommend using a combination of both FIDO2 and Smartcard authentication for the ultimate phishing-resistant authentication experience. FIDO2, though incredibly easy, is not supported everywhere; smartcards, however, are supported everywhere. As such, we recommend using both simply for the sake of convenience. By using hardware keys like YubiKeys (specifically something like the YubiKey 5 Series), you can use something that supports both FIDO2 and Smartcard, allowing you to utilize FIDO2 authentication most of the time and Smartcard authentication in the times where FIDO2 isn’t supported.
Luckily for you, tools such as EZCMS, the best credential management system for FIDO2 and Smartcard exist that allow you to use both FIDO2 and Smartcard authentication with ease! Check out the video below to see how EZCMS can help your organization, and if you want to learn more about how EZCMS can apply to your specific use case, feel free to schedule a FREE consultation with one of our ex-Microsoft identity experts!


