How to Send your RADIUS Logs to your SIEM
Prerequisites
Introduction - How to Send your RADIUS Logs to your SIEM
EZRADIUS enables your security team to monitor critical user actions by pushing the information to your SIEM. If your SIEM provider is not currently supported email your Keytos contact and request a connector for that specific provider.
How To Connect Your RADIUS To Azure Sentinel
- Go to your EZRADIUS portal.
- Click on Settings.
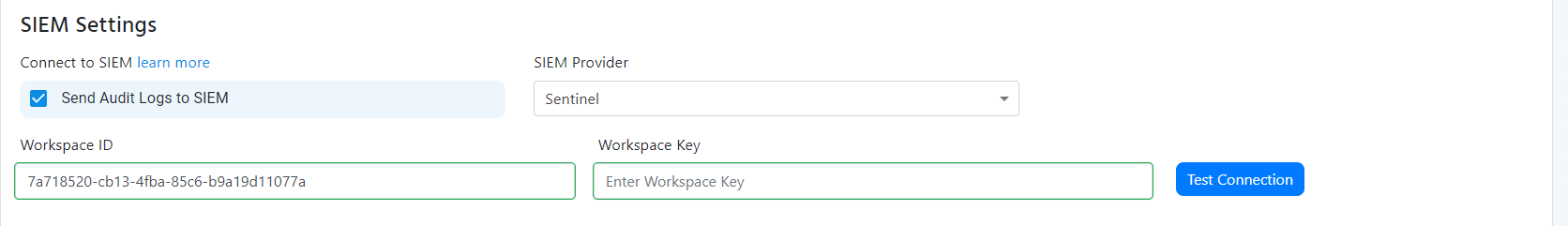
- Scroll to the bottom and enable the “Send Audit Logs” to SIEM option.
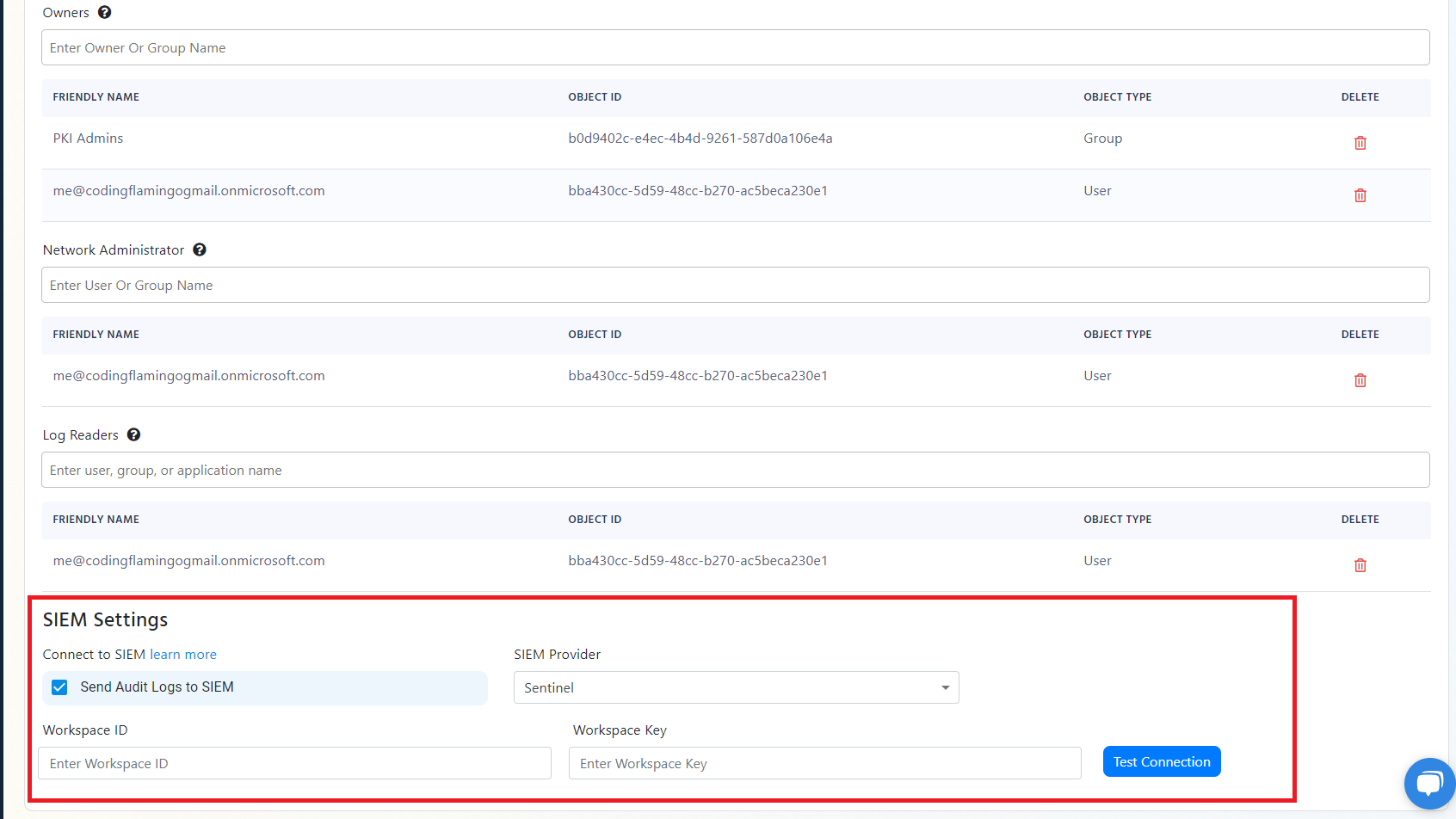
- Select Sentinel as the SIEM Provider.
- In another tab, go to the Azure Portal
- Select the log analytics connected to your Sentinel instance.
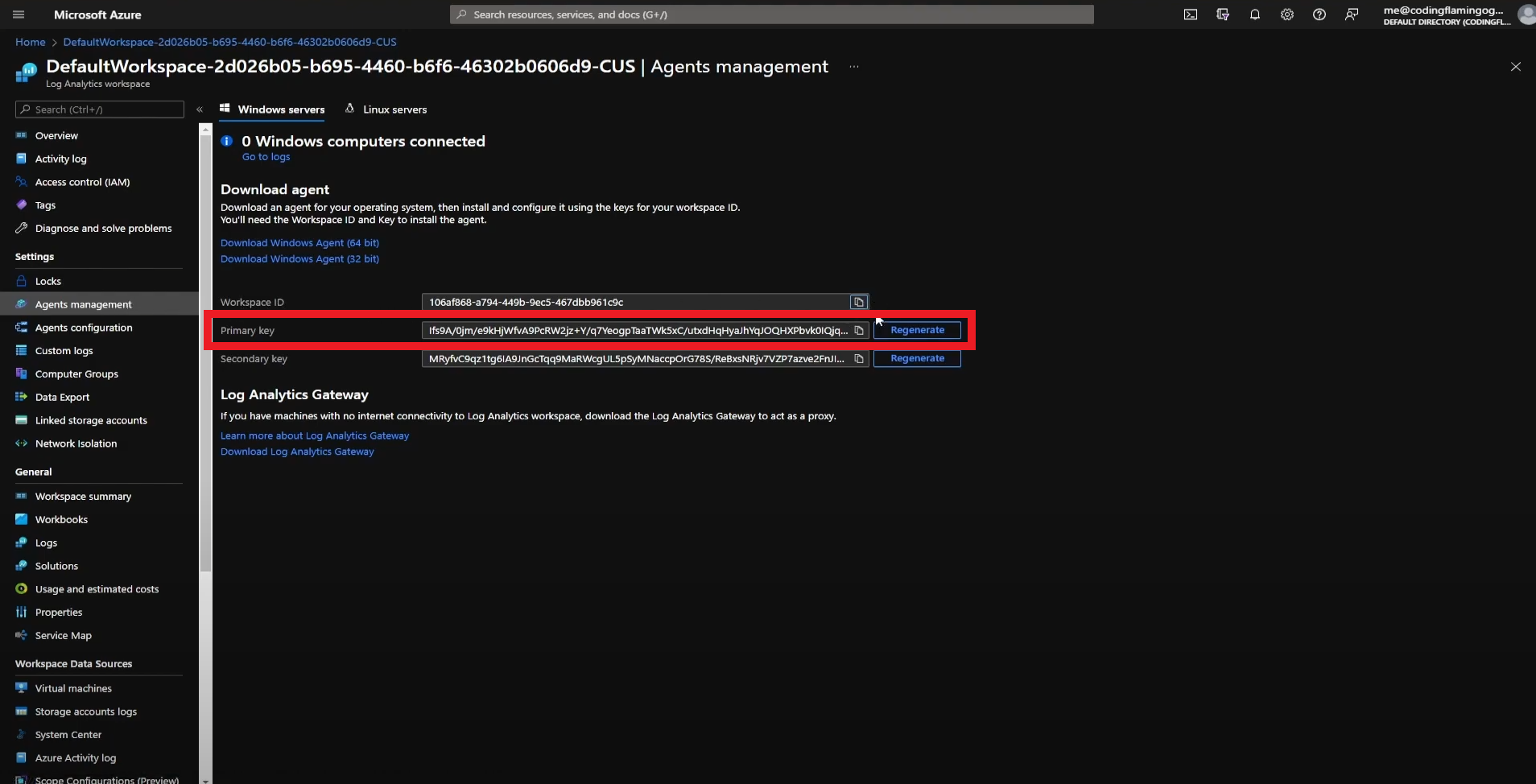
- Click on “Agents Management”.
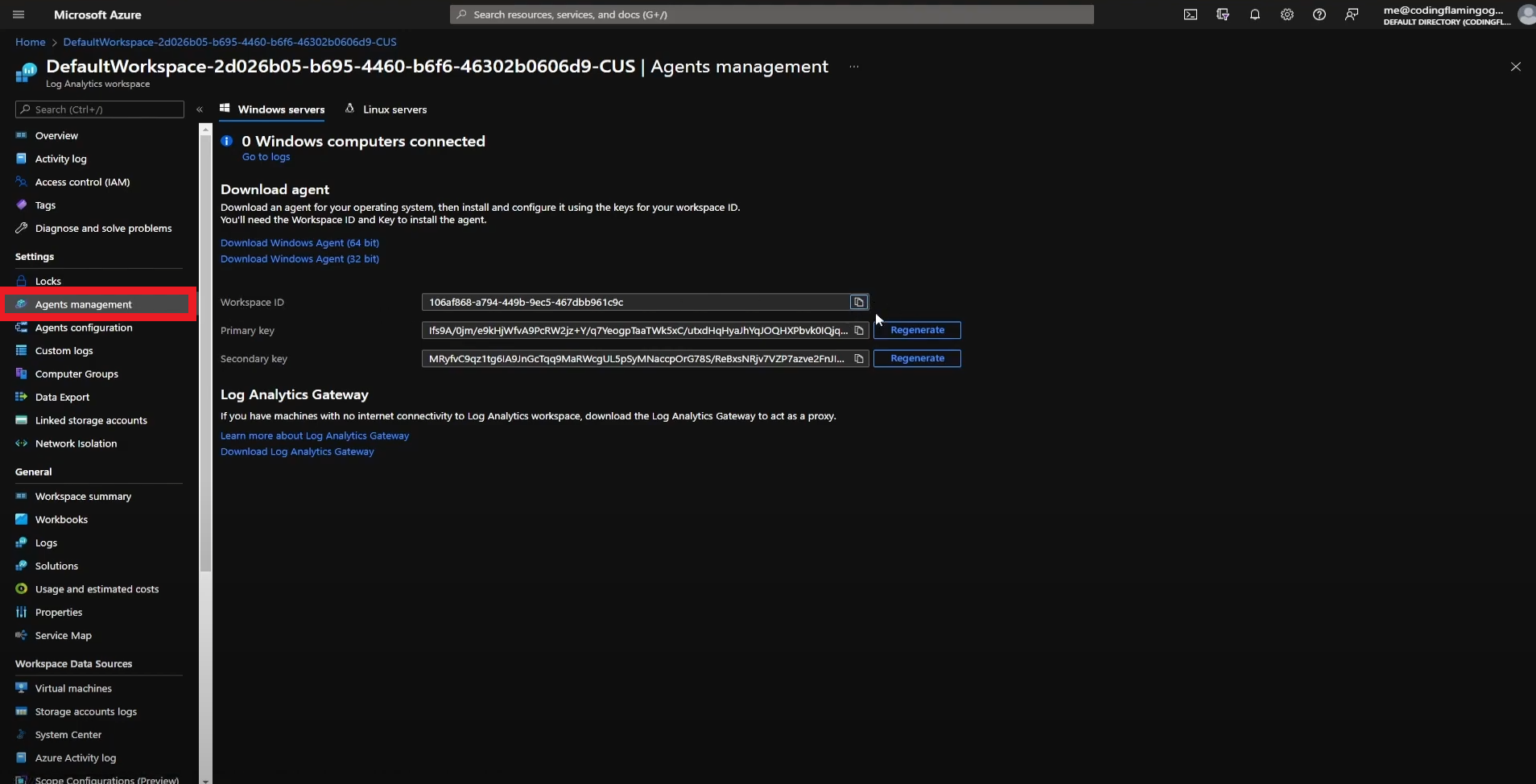
- Copy Your Workspace ID.
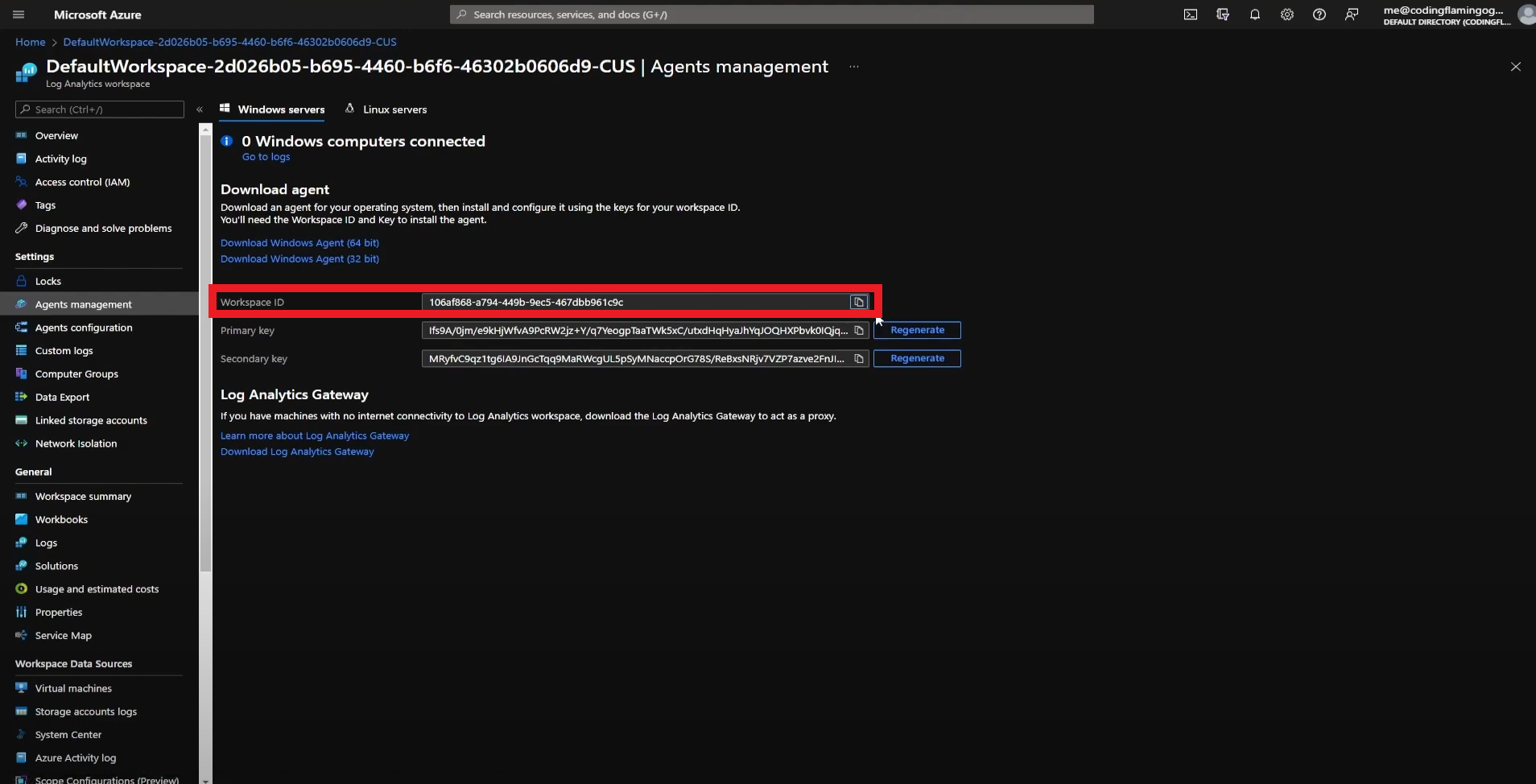
- Go back to the EZRADIUS tab and paste it in the “Workspace ID” field.
- Go back to the Azure tab and copy the primary key.
- Go back to the EZRADIUS tab and paste the key in the “Workspace Key” field.
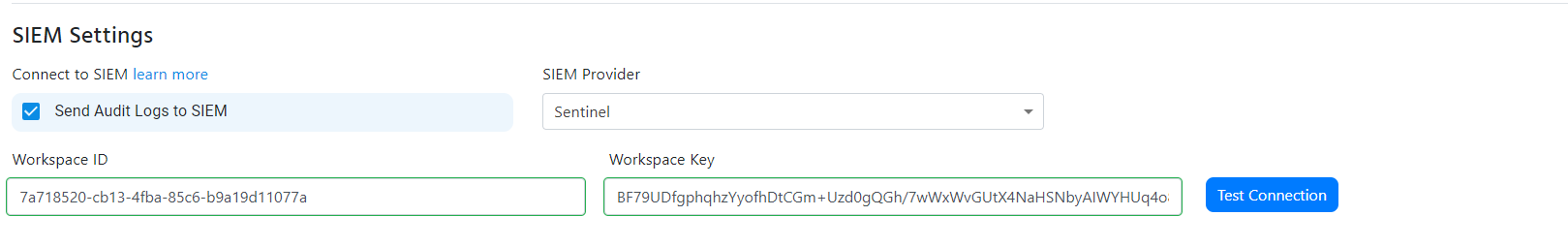
- Click the “Test Connection” button, this will create a test log in your SIEM to make sure EZRADIUS can write to the SIEM.
- If the connection test is successful, click “Save changes” at the top of the subscription.
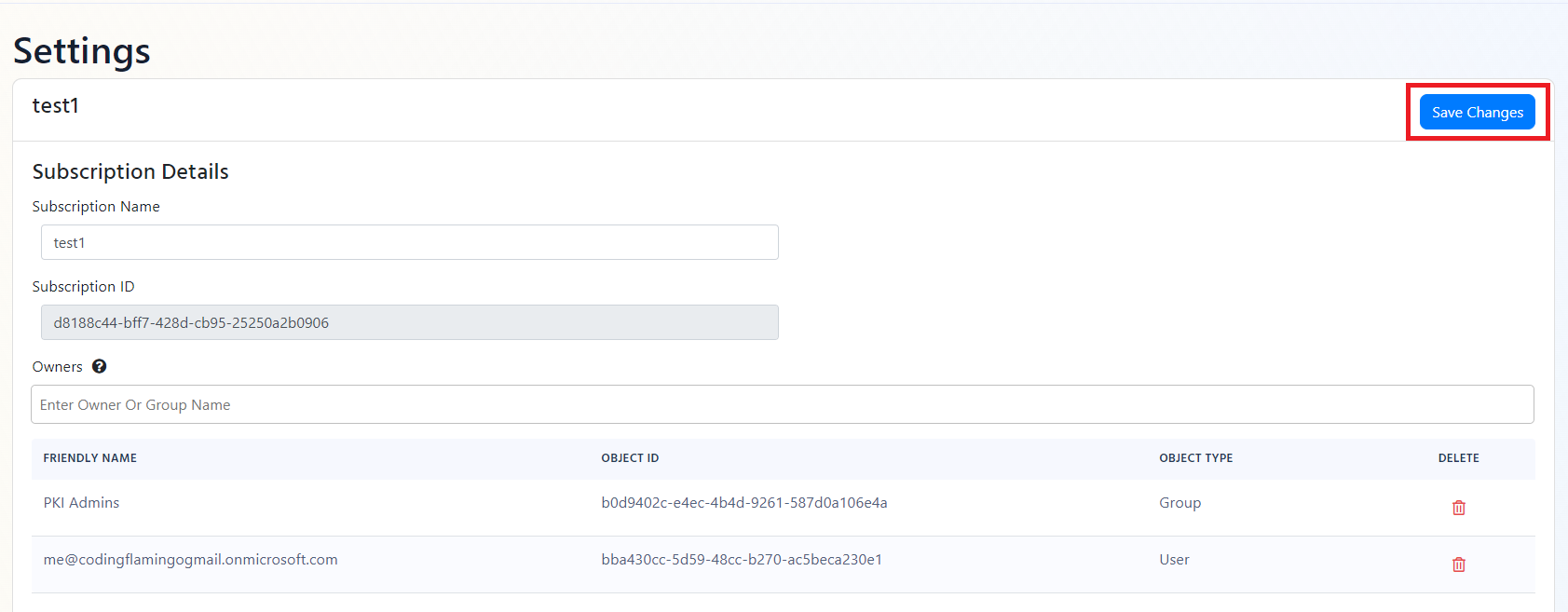
- EZRADIUS will now send your security logs to your SIEM. If an error occurs it will email your subscription PKI administrators. EZRADIUS will now send your security logs to your SIEM. If an error occurs it will email your subscription PKI administrators. Now you should check out how to create a dashboard for your RADIUS service
How To Connect Your RADIUS Service To CrowdStrike Falcon LogScale
- Go to your EZRADIUS portal.
- Click on Settings.

- Scroll to the bottom and enable the “Send Audit Logs” to SIEM option.

- Select CrowdStrike Falcon LogScale as the SIEM Provider.

- In another tab, go to your CrowdStrike Falcon LogScale instance.
- Click on the Settings tab.
- Select the “Ingest Tokens” menu.
- Click on the “Add Token” button.
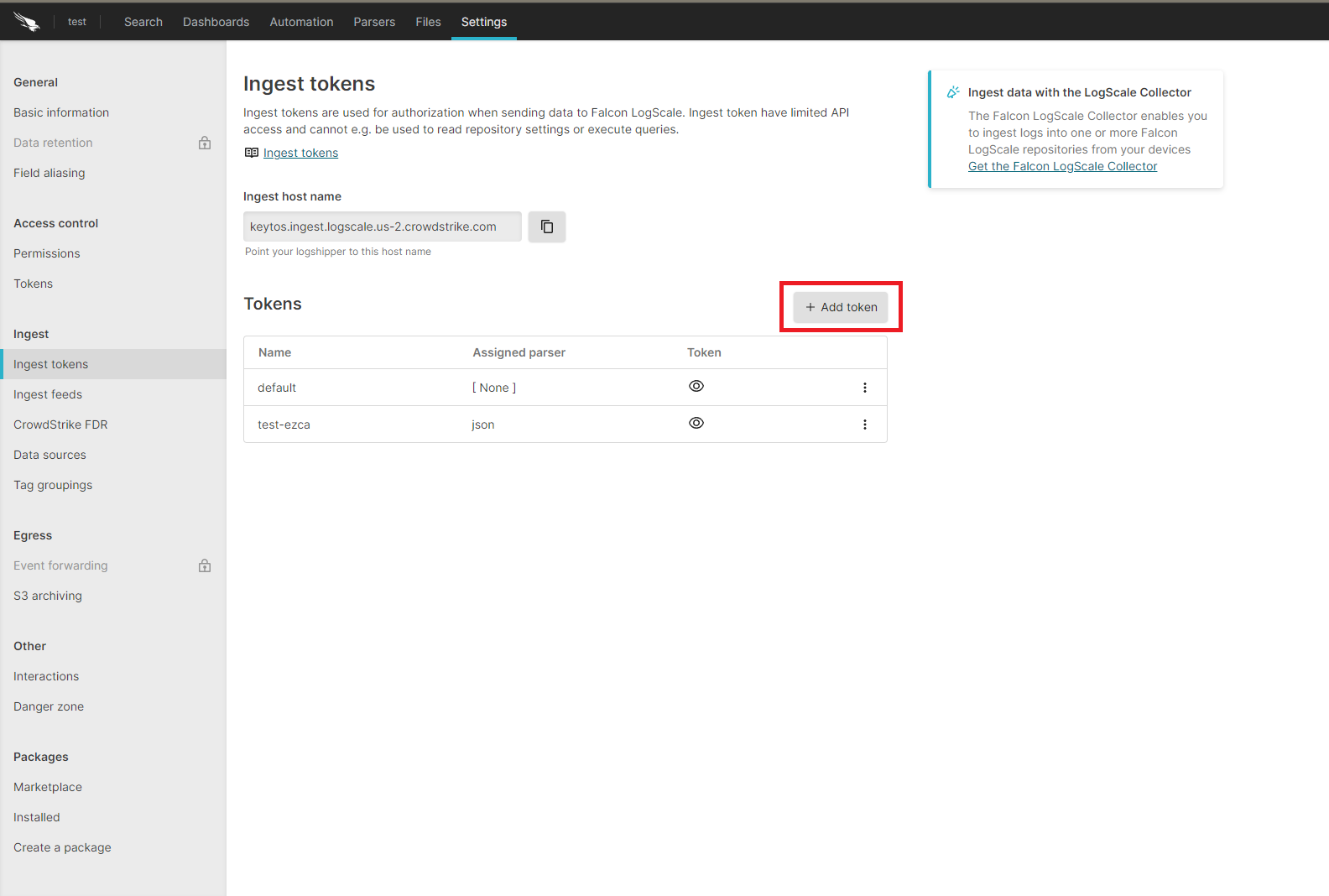
- Enter the token name
- Assign the json parser and click “Create”.
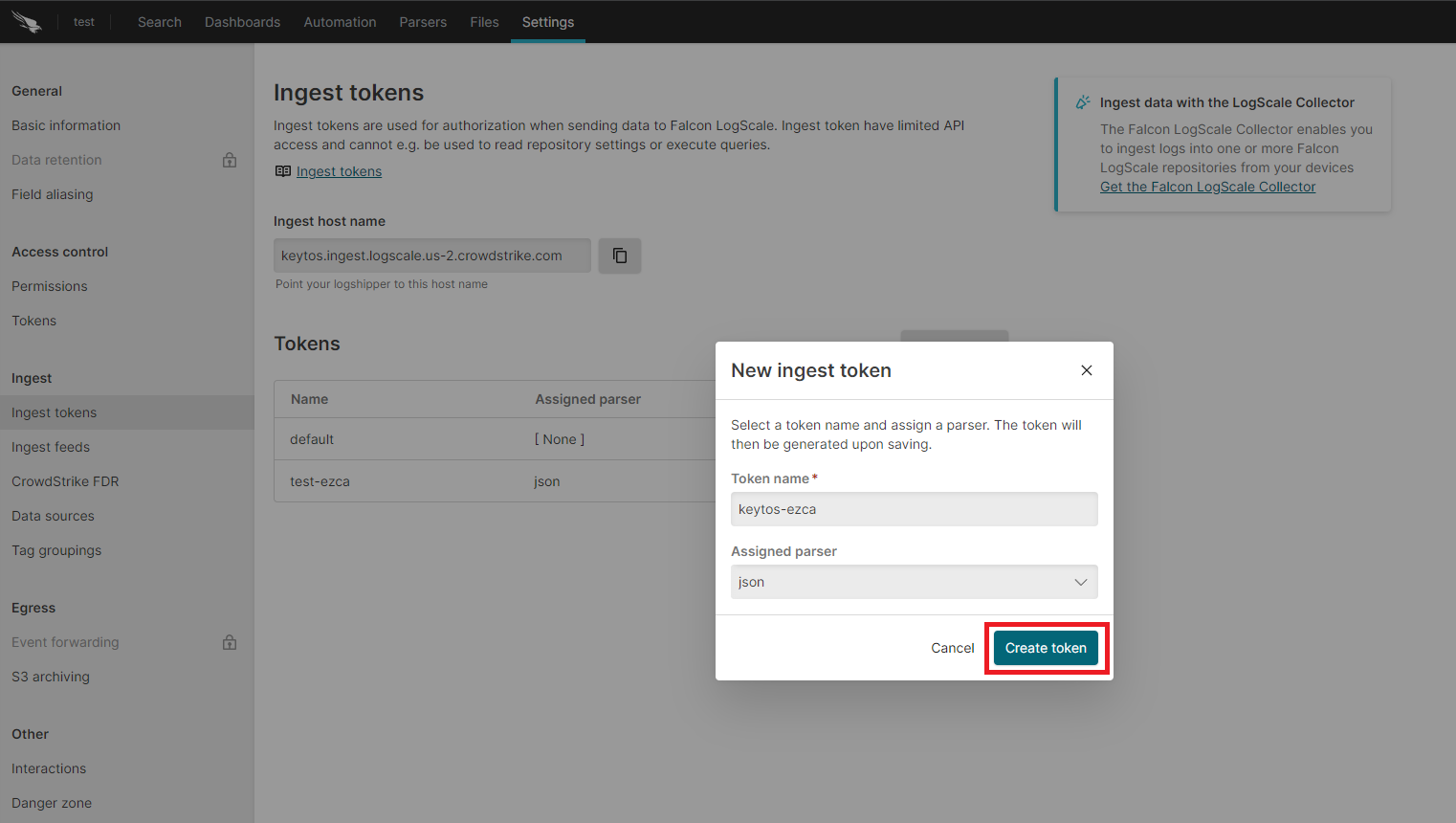
- Copy the token and the ingest host name.
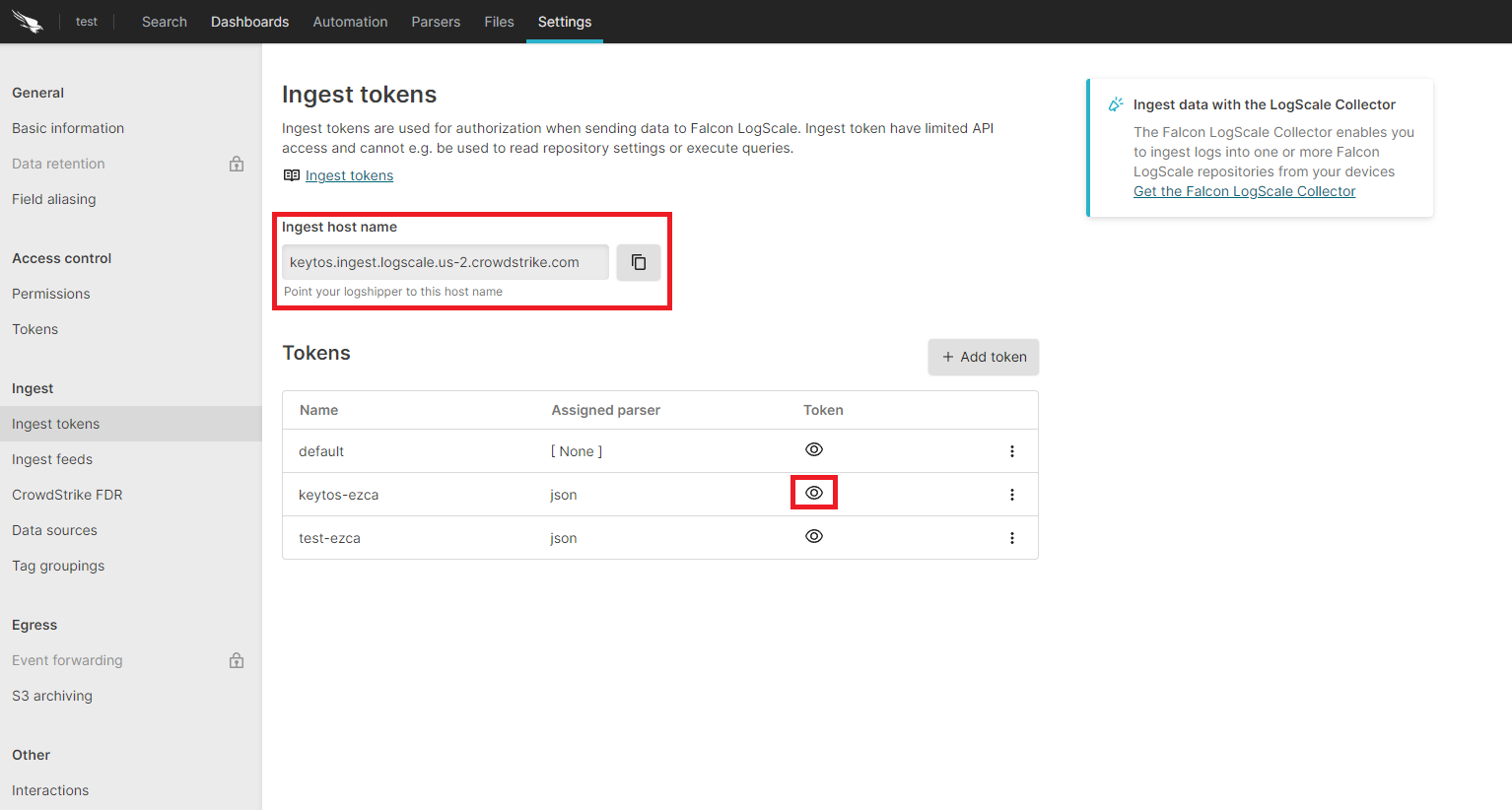
- Go back to the EZCA tab.
- Paste the ingest host name in the “Ingestion Endpoint” field.
- Paste the token in the “Ingestion Token” field.
- Click the “Test Connection” button, this will create a test log in your SIEM to make sure EZCA can write to the EZCA.
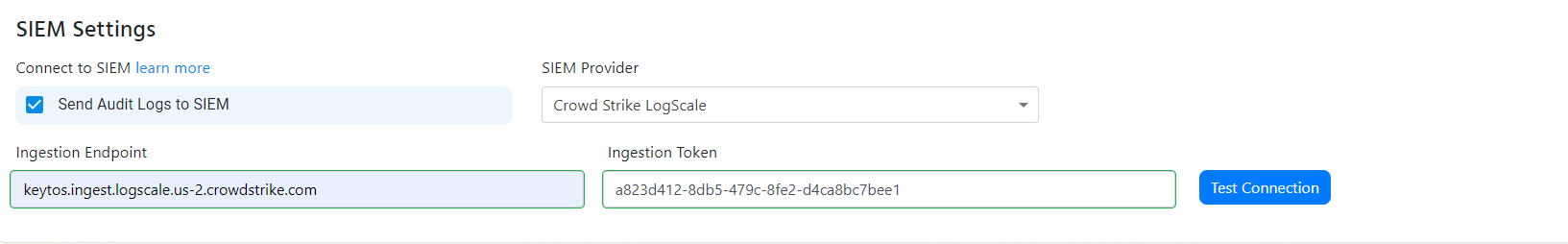
- If the connection test is successful, click “Save changes” at the top of the subscription.

SIEM Events
Administrator Events
Administrator events (found in the EZRadiusAdministrator table) are events triggered when the administrator performs an action on the subscription such as adding users, removing users, or changing the subscription settings. These events are important to monitor since they can indicate a compromise to the subscription. Below are the events that are considered critical to monitor:
| Action | Event Summary | Potential Criticality |
|---|---|---|
| NotAuthorized | Someone attempted to perform an administrative a that they are not authorized to do. | High |
| SubscriptionUpdated | An administrator made changes to the subscription. | Medium |
Policy Events
When an administrator creates or modifies a policy, an event is triggered in the EZRadiusPolicy table. These events are important to monitor since they can indicate a compromise to the subscription.
Authentication Events
Every time a user authenticates to the RADIUS service, an event is triggered in the EZRadiusAuthentication table. You can monitor these events to detect abnormal behavior or unauthorized access to your network.
Accounting Events
In accordance with RFC2866 EZRADIUS records accounting information for each user session. You can monitor these events to detect abnormal behavior or unauthorized access to your network.
How To Create Alerts in SIEM to Monitor Your PKI
Using a SIEM enables you to create alerts for critical operations or abnormal behavior. We recommend setting up alerts for any high criticality event, and closely monitor medium and low events. Below are sample queries for the Administrator events.
Azure Sentinel
EZRadiusAdministrator_CL | where Action_s == "NotAuthorized"
CrowdStrike Falcon LogScale
LogType = "EZRadiusAdministrator" and Action = "NotAuthorized"