Giving EZCA Access To Azure Key Vault
Prerequisites
Introduction First Step to Automate Certificate Rotation in Azure Key Vault
Enabling Azure Key Vault Certificate Rotation Automation requires EZCA to have access to your Key Vaults. EZCA needs RBAC Reader Role to verify the user requesting the certificate has access to the Key Vault. EZCA CA also requires an access policy with the following certificate permissions: Get, Update, and Create.
This is only required if you are looking to automate certificate rotation in Azure Key Vault. If you using EZCA for SCEP, ACME, or other certificate management tasks, you can skip this step.
Adding Application to Key Vault RBAC in Azure Portal
- Login to https://portal.azure.com
- Navigate to the Key Vault you want EZCA to manage.
- Click on the Access control (IAM) menu option
- Click on Add
- Select the “Add Role Assignment” Option
- Select Reader role
- Click on Members
- Click on “Select Members”
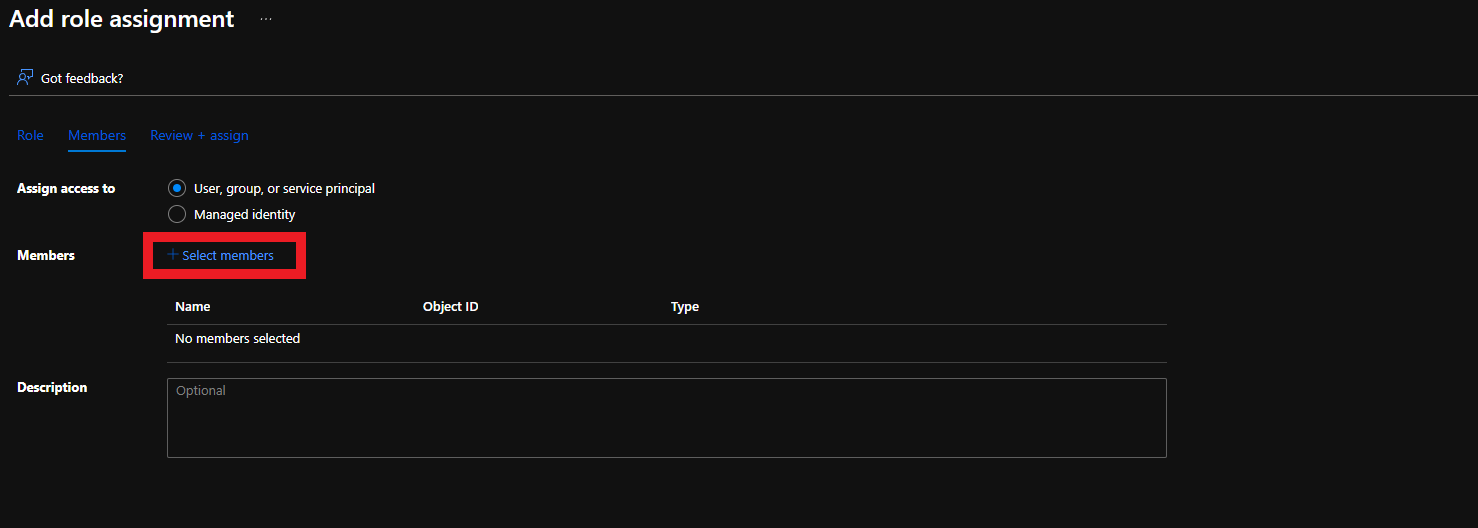
- Select the Keytos Application
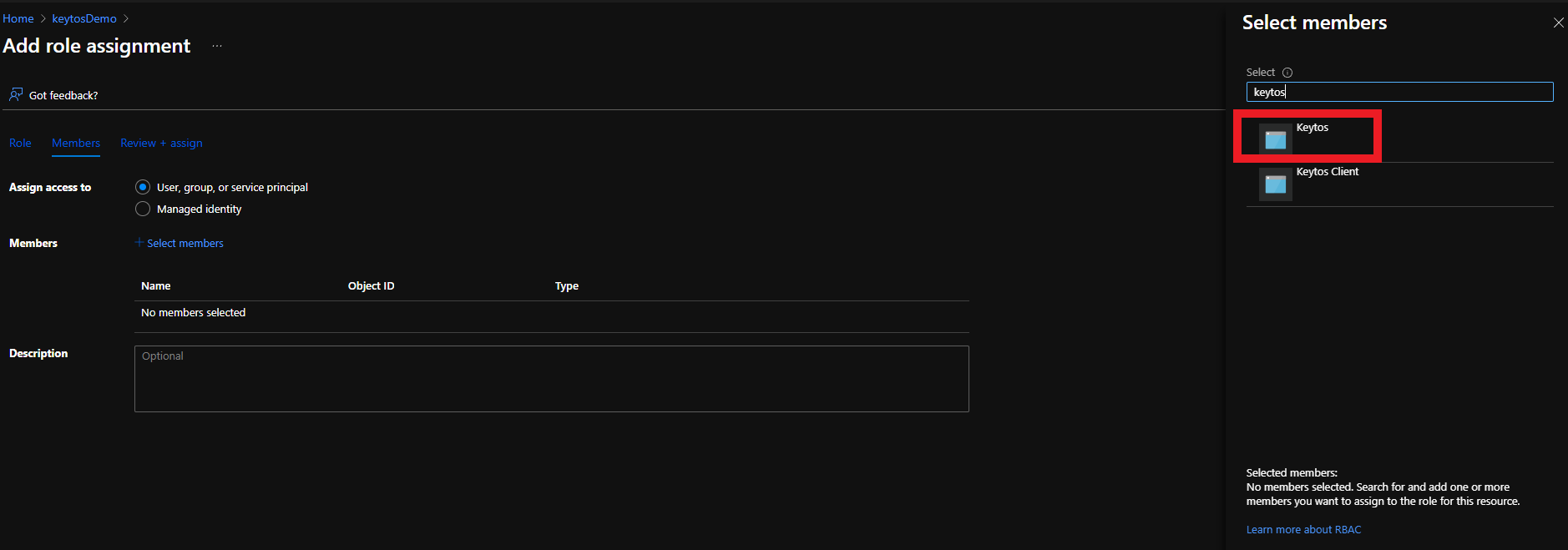
- Click the Select button
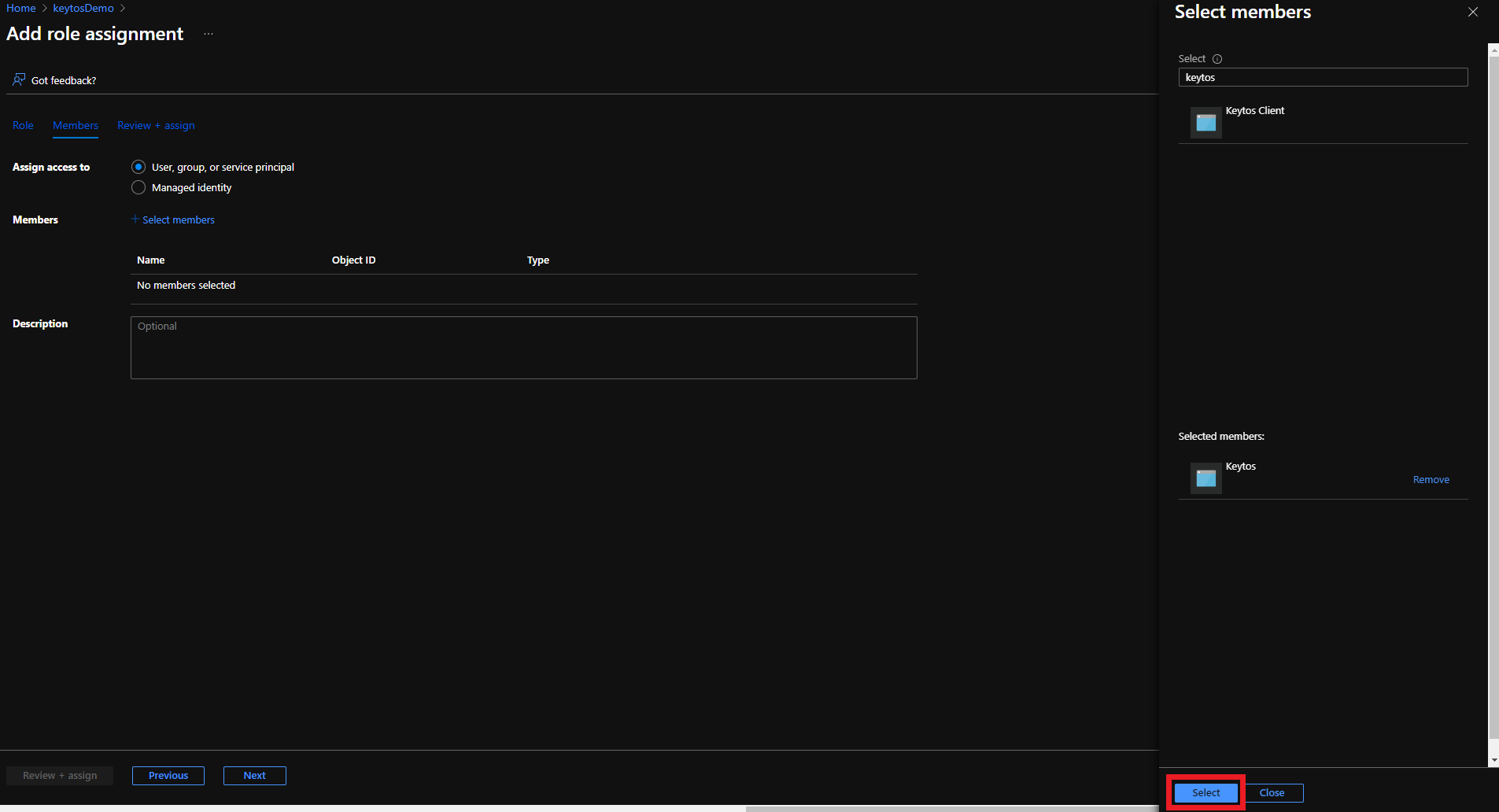
- Click the Review + assign button
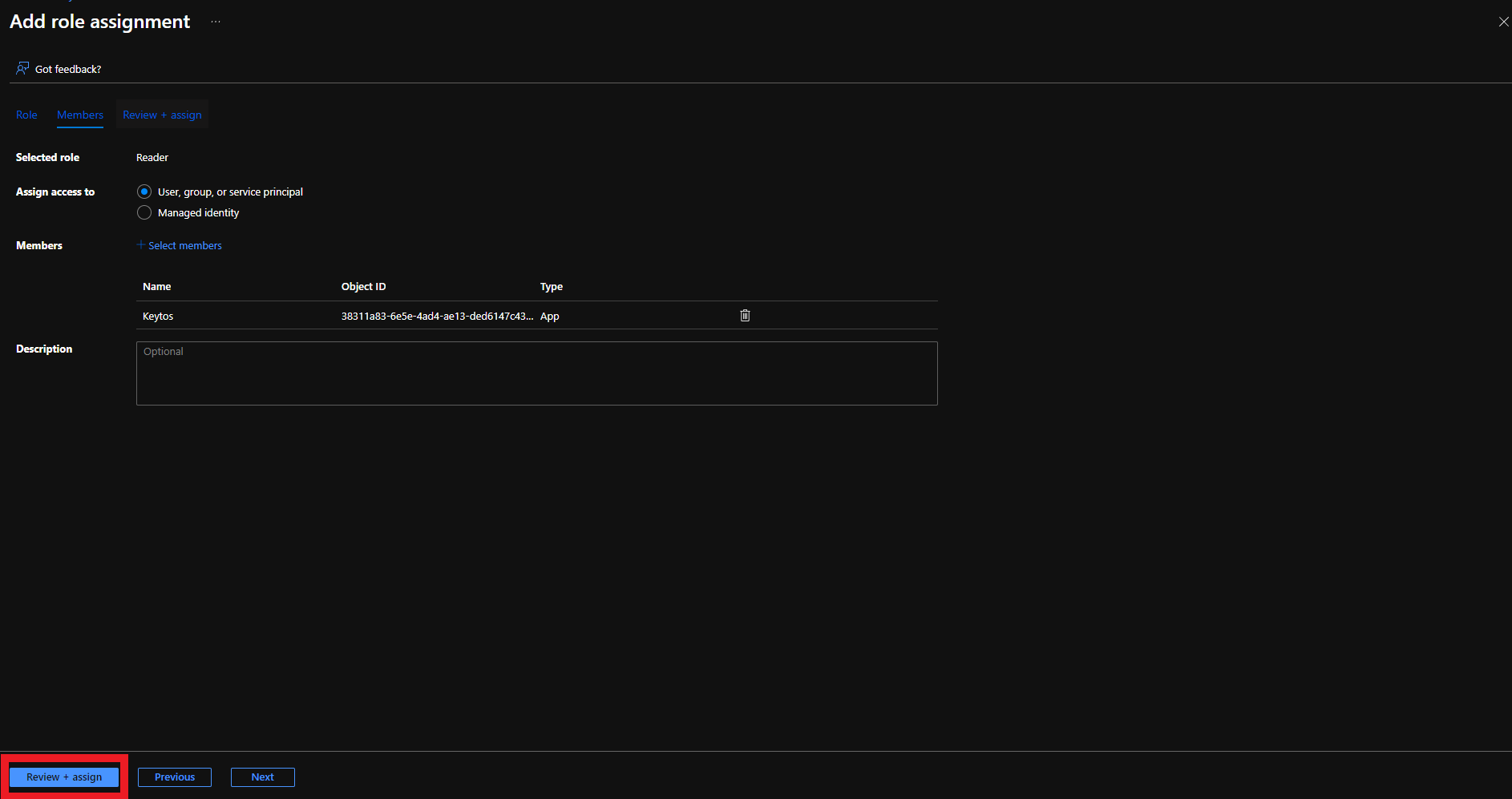
- Click the Review + assign button
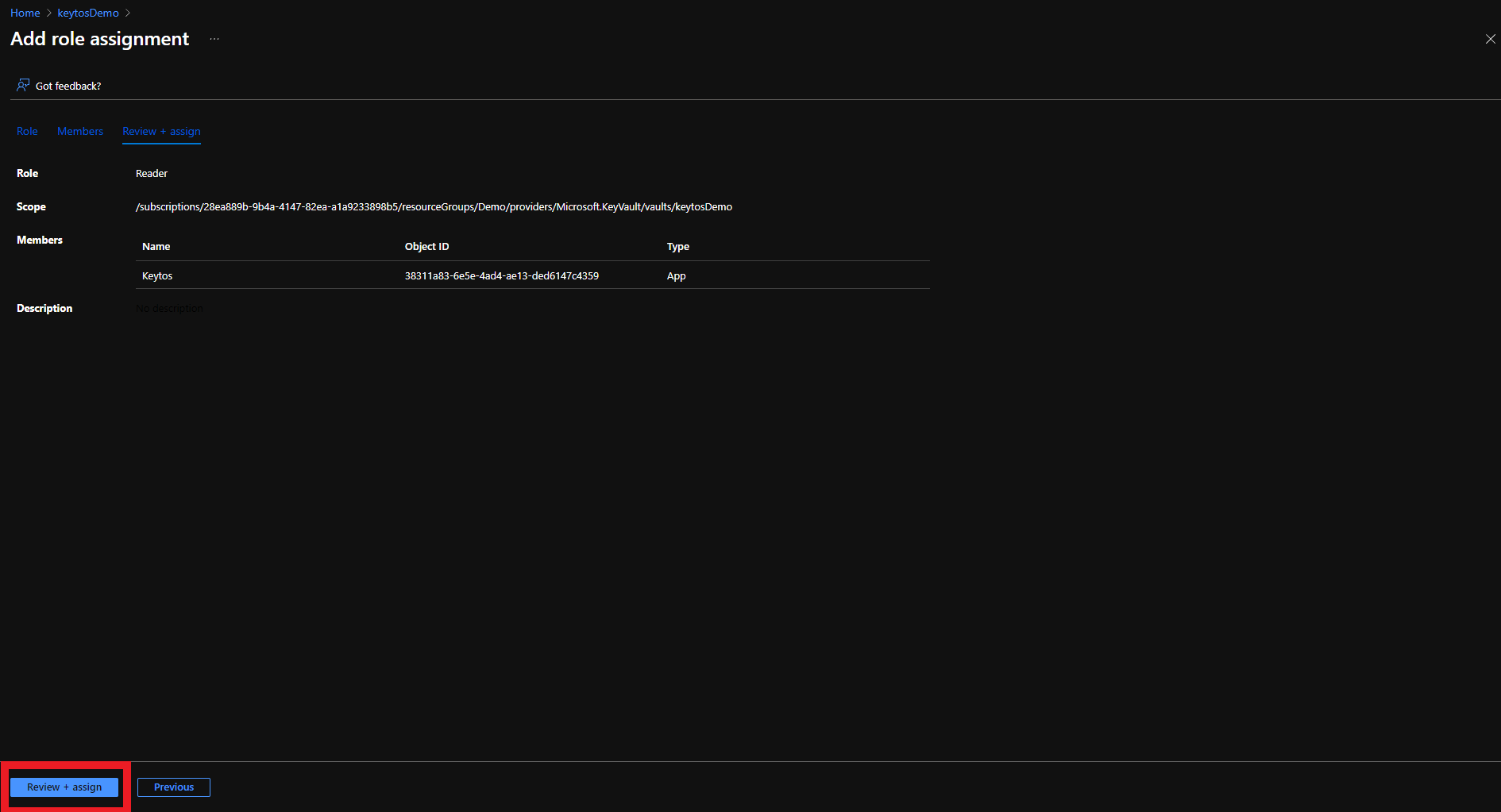
Adding Application to Access Policies in Azure Portal for Automated Certificate Rotation
To get the most granular control over the permissions that EZCA has to your Key Vault, you can add an access policy to the Key Vault. This will allow you to specify the exact permissions that EZCA has to the Key Vault.
- Login to https://portal.azure.com
- Navigate to the Key Vault you want EZCA to manage.
- Click on the Access policies menu option
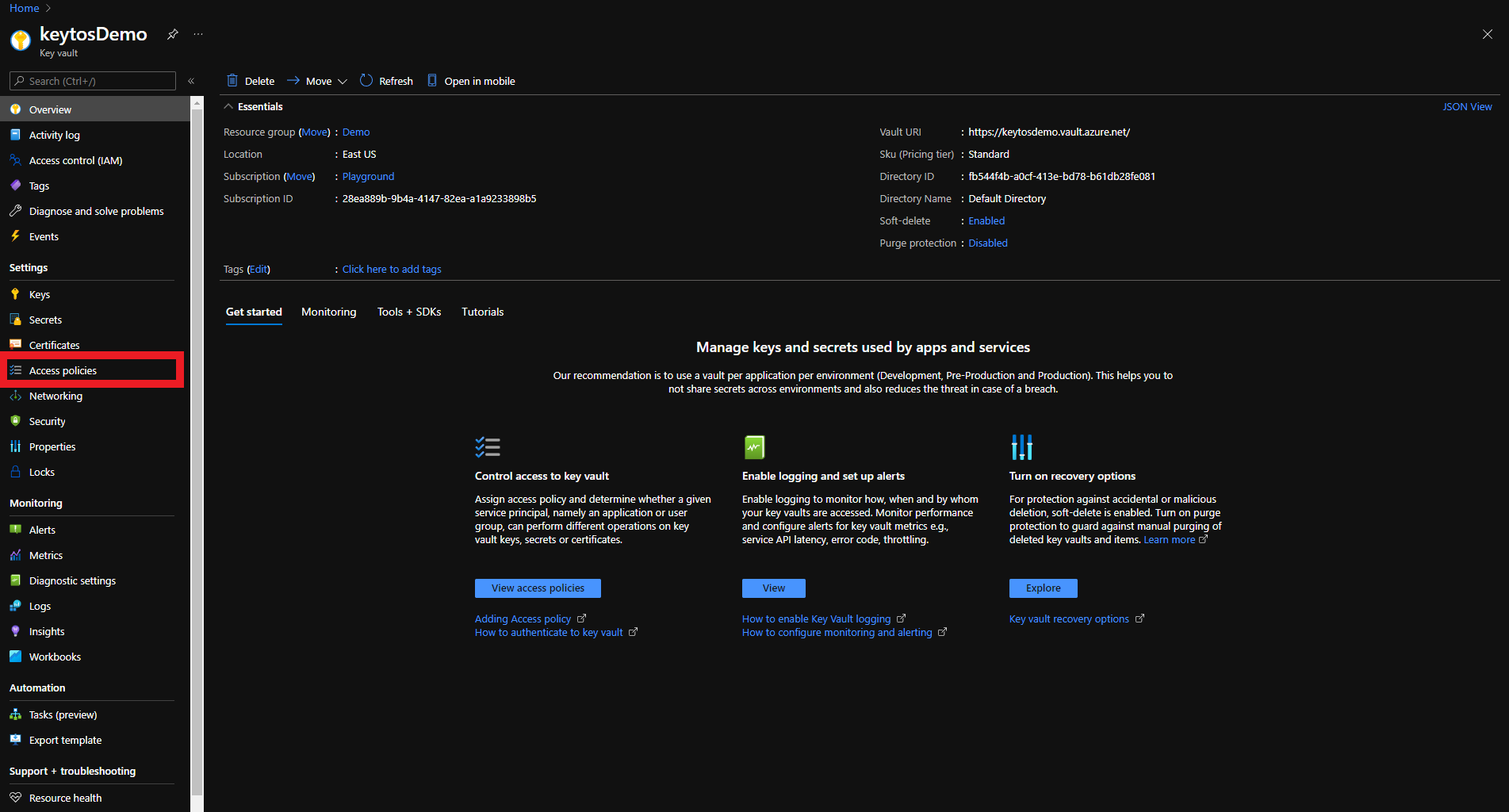
- Click on Add Access Policy
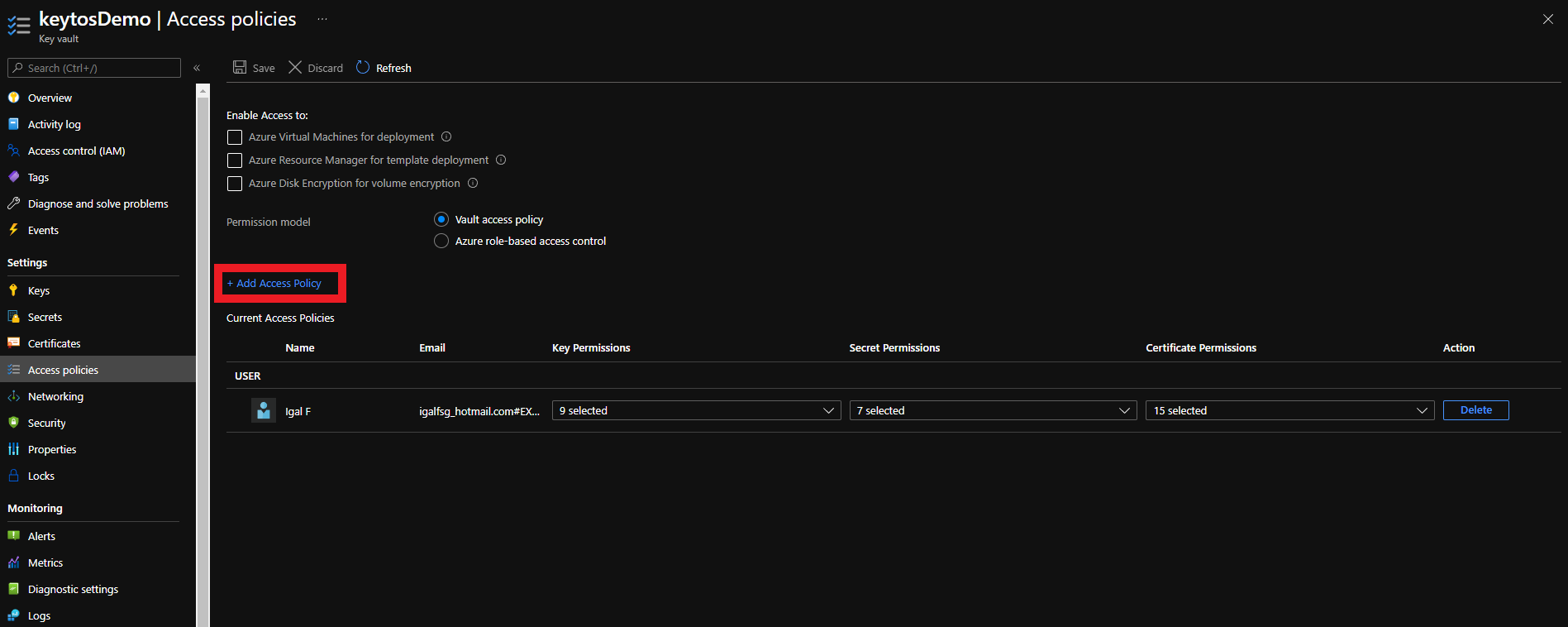
- Under Certificate permissions select: Get, Update, Create.
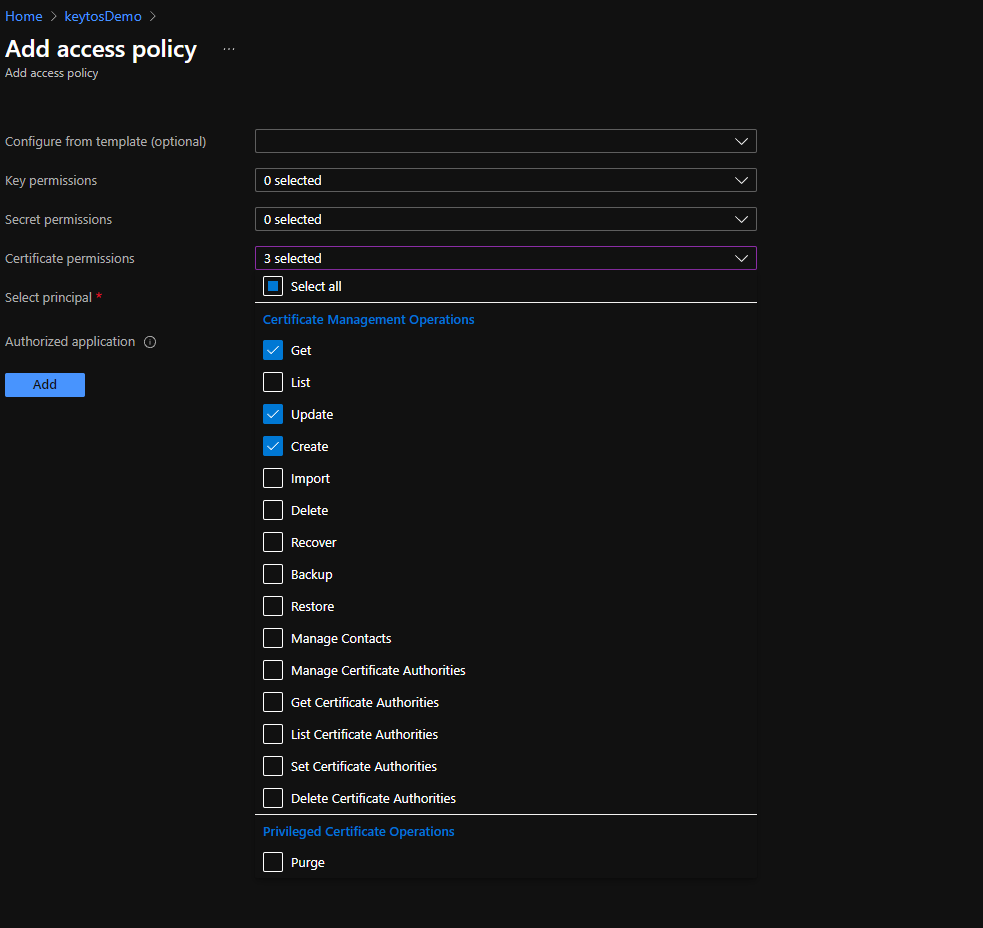
- Click on the “None selected” link to the right of Select Principal
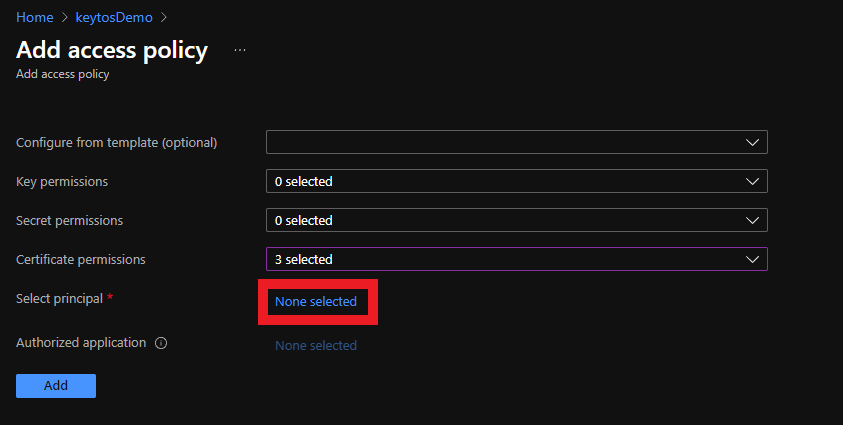
- Click on the “None selected” link to the right of Select Principal

- Select the Keytos Application
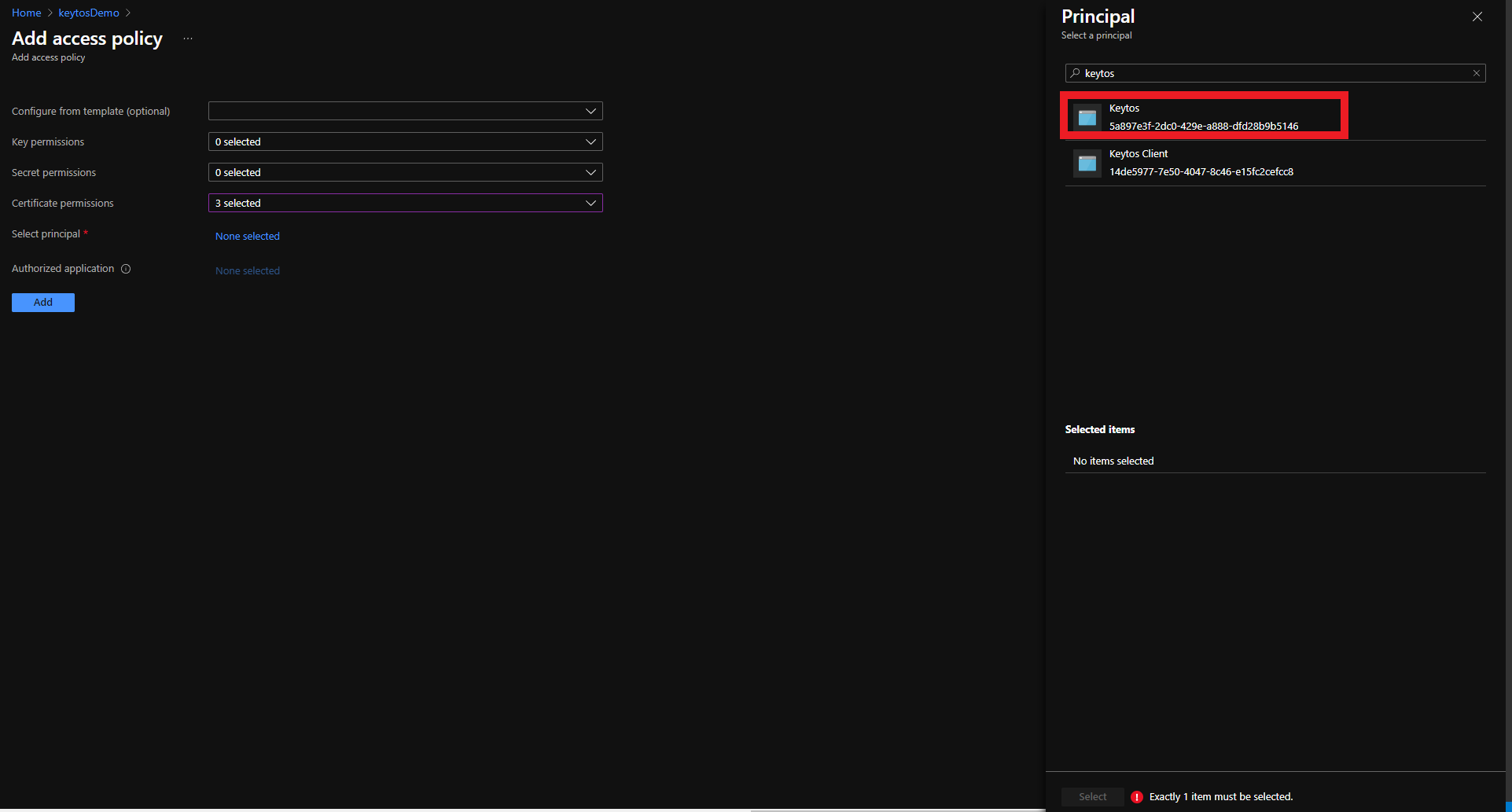
- Click the Select button
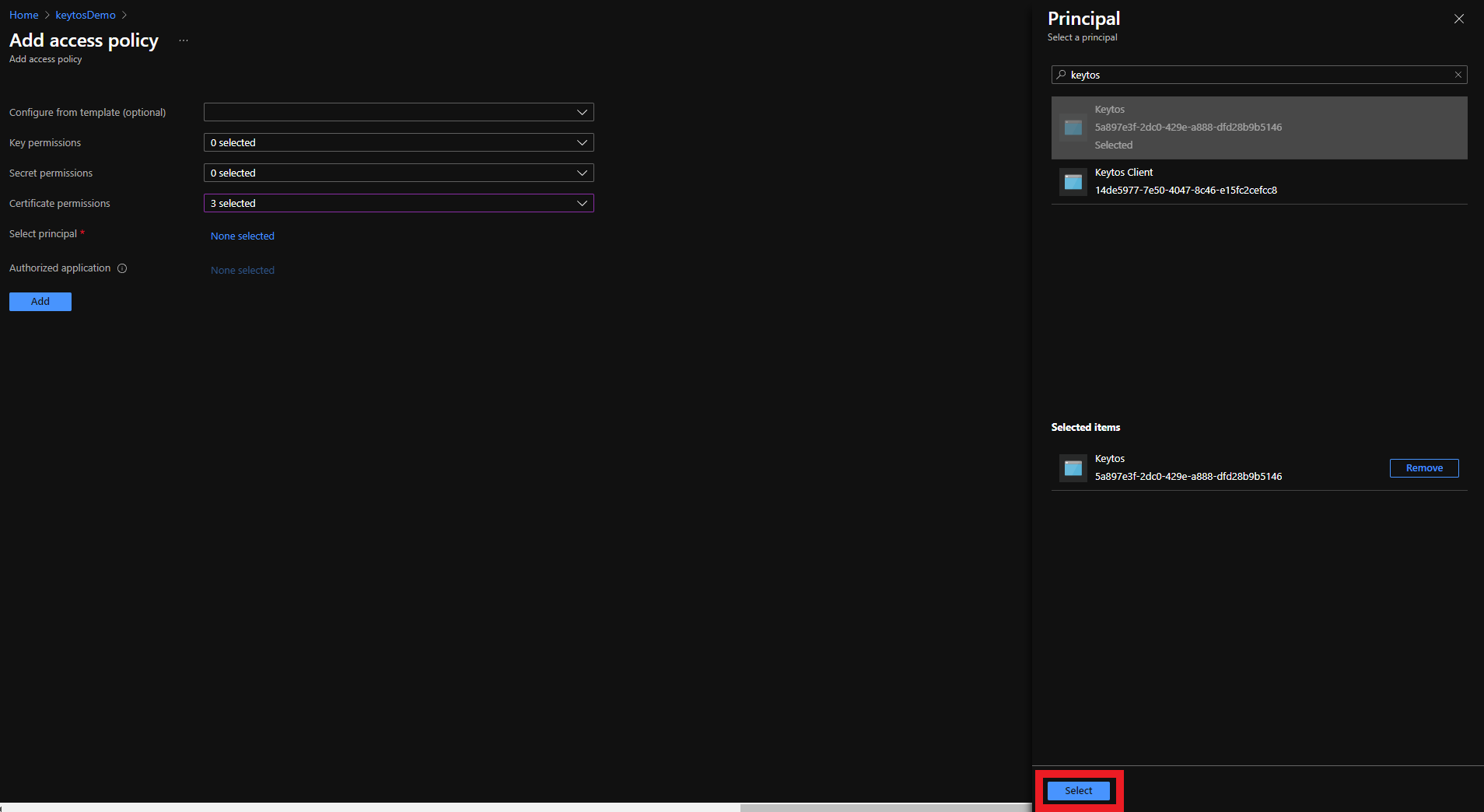
- Click the Add button
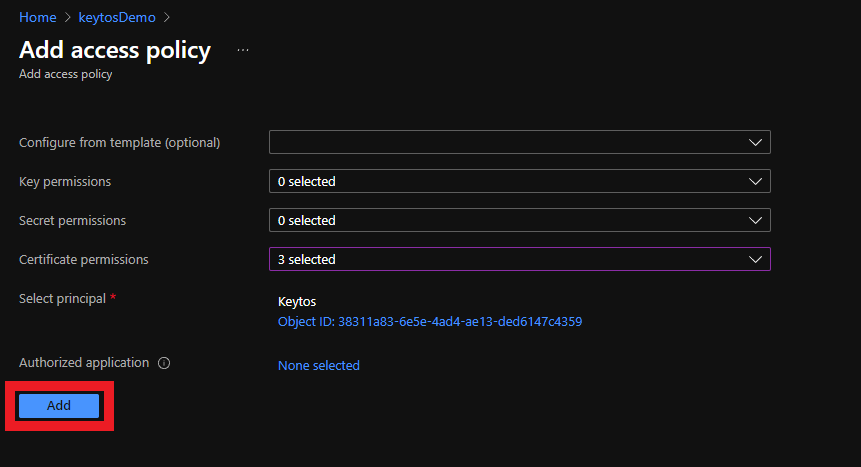
- Click the Save button
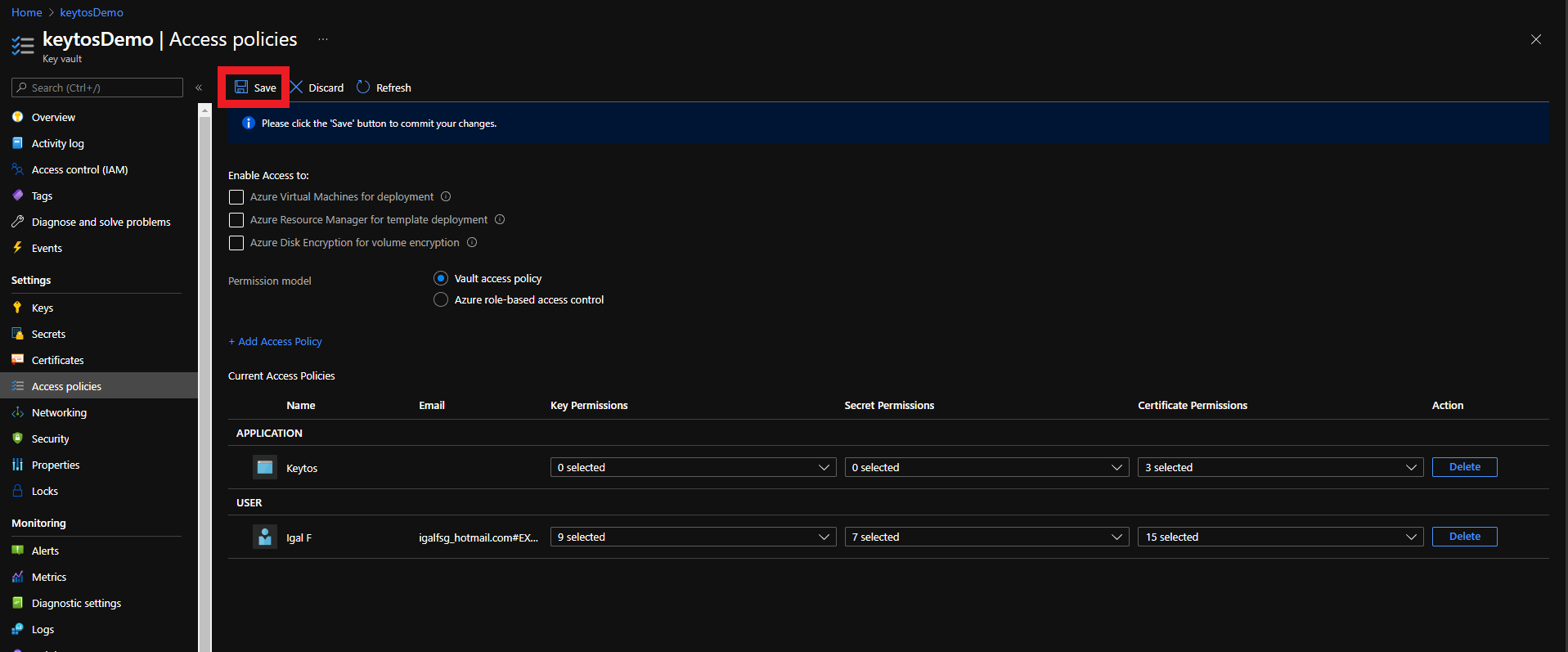
- Your Azure Key Vault is ready to be managed by EZCA!
Adding Access Policy for RBAC Enabled Azure Key Vaults for Automatic Certificate Rotation
If your Key Vault has RBAC enabled, you will need to add the “Key Vault Certificates Officer” Key Vault RBAC permission to allow EZCA to manage the certificates in the Key Vault.
- Login to https://portal.azure.com
- Navigate to the Key Vault you want EZCA to manage.
- Click on the Access control (IAM) menu option

- Click on Add

- Select the “Key Vault Certificates Officer” Role
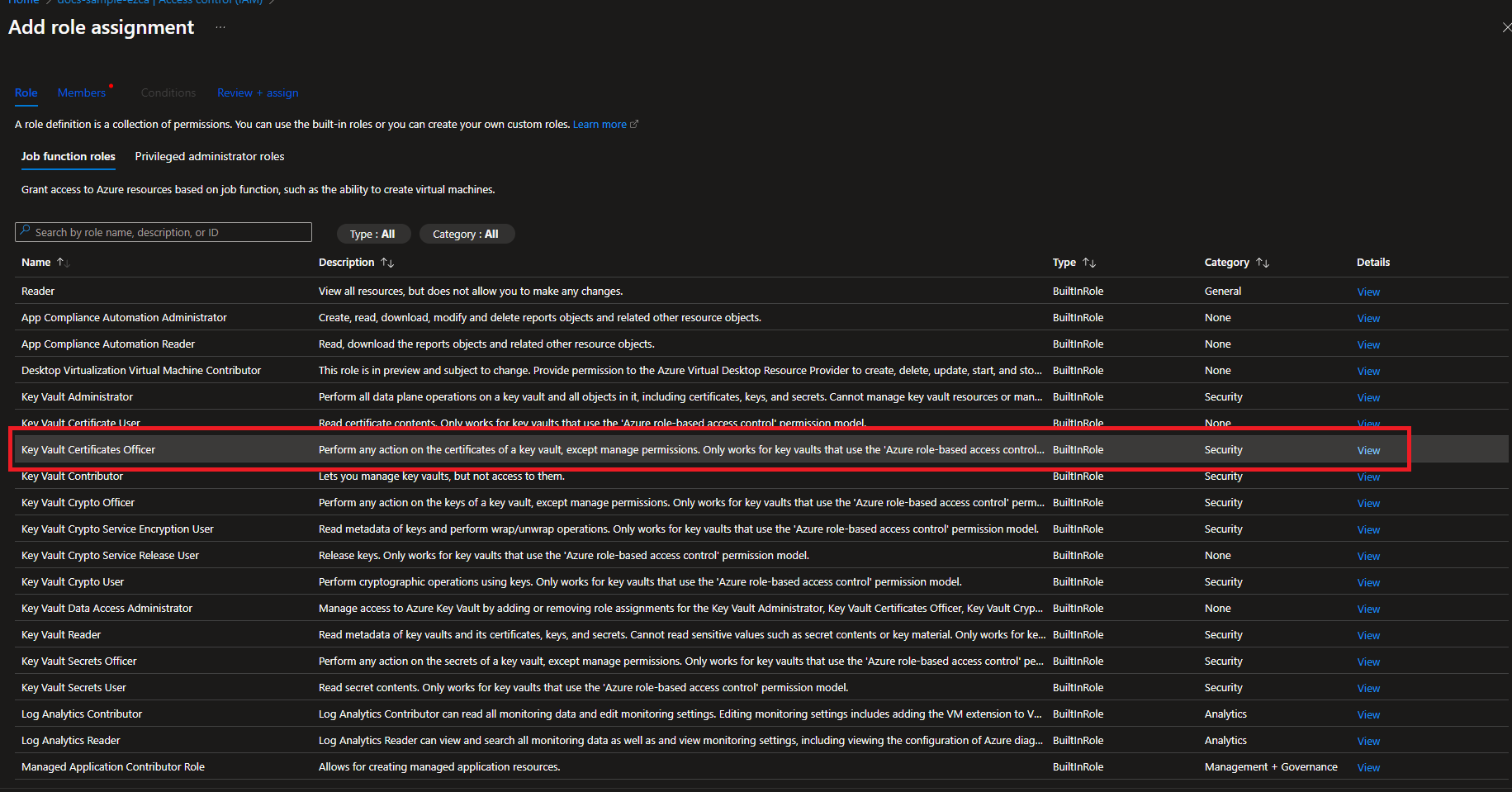
- Click on Members

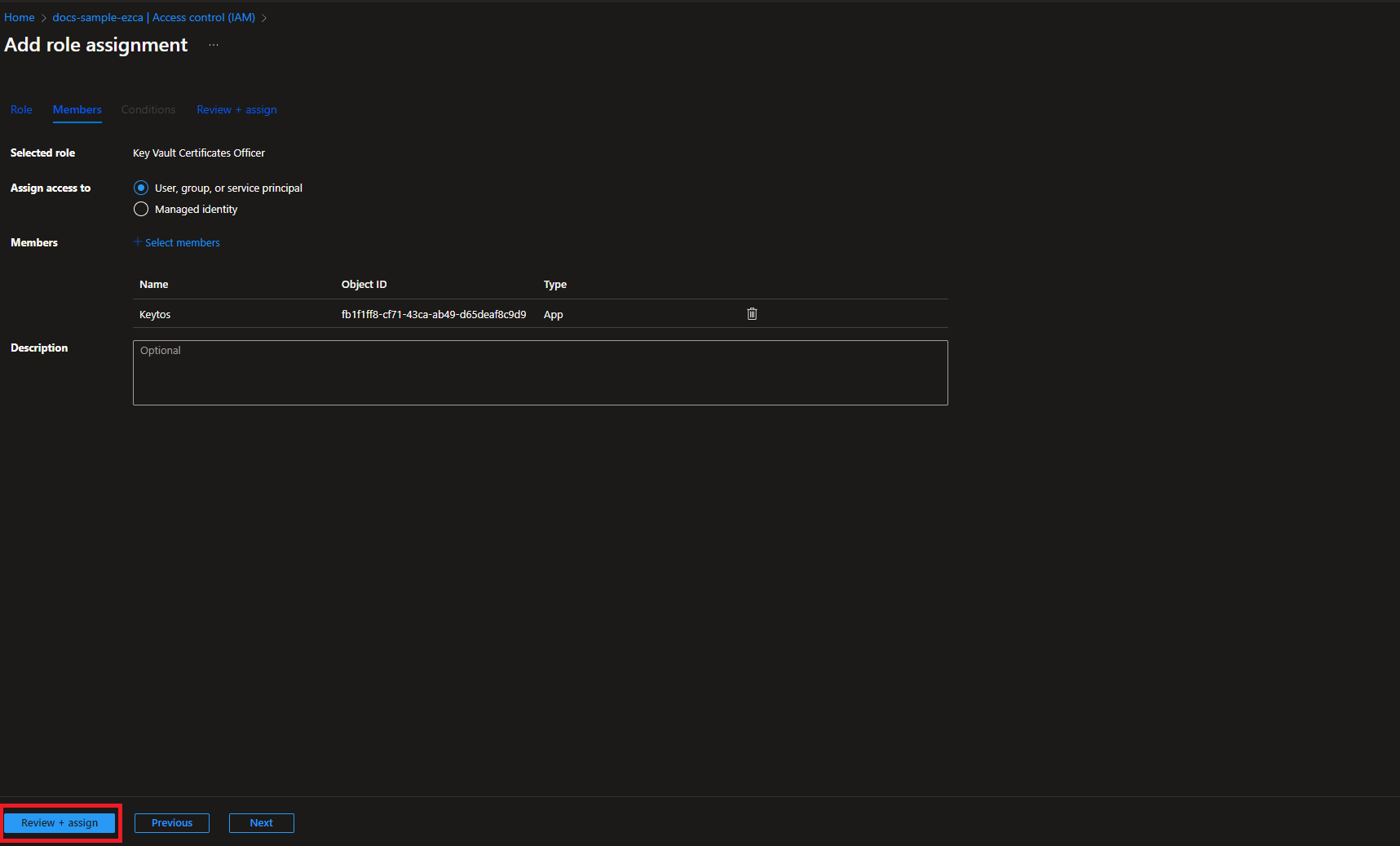
- Click on “Select Members”

- Select the Keytos Application

- Click the Select button

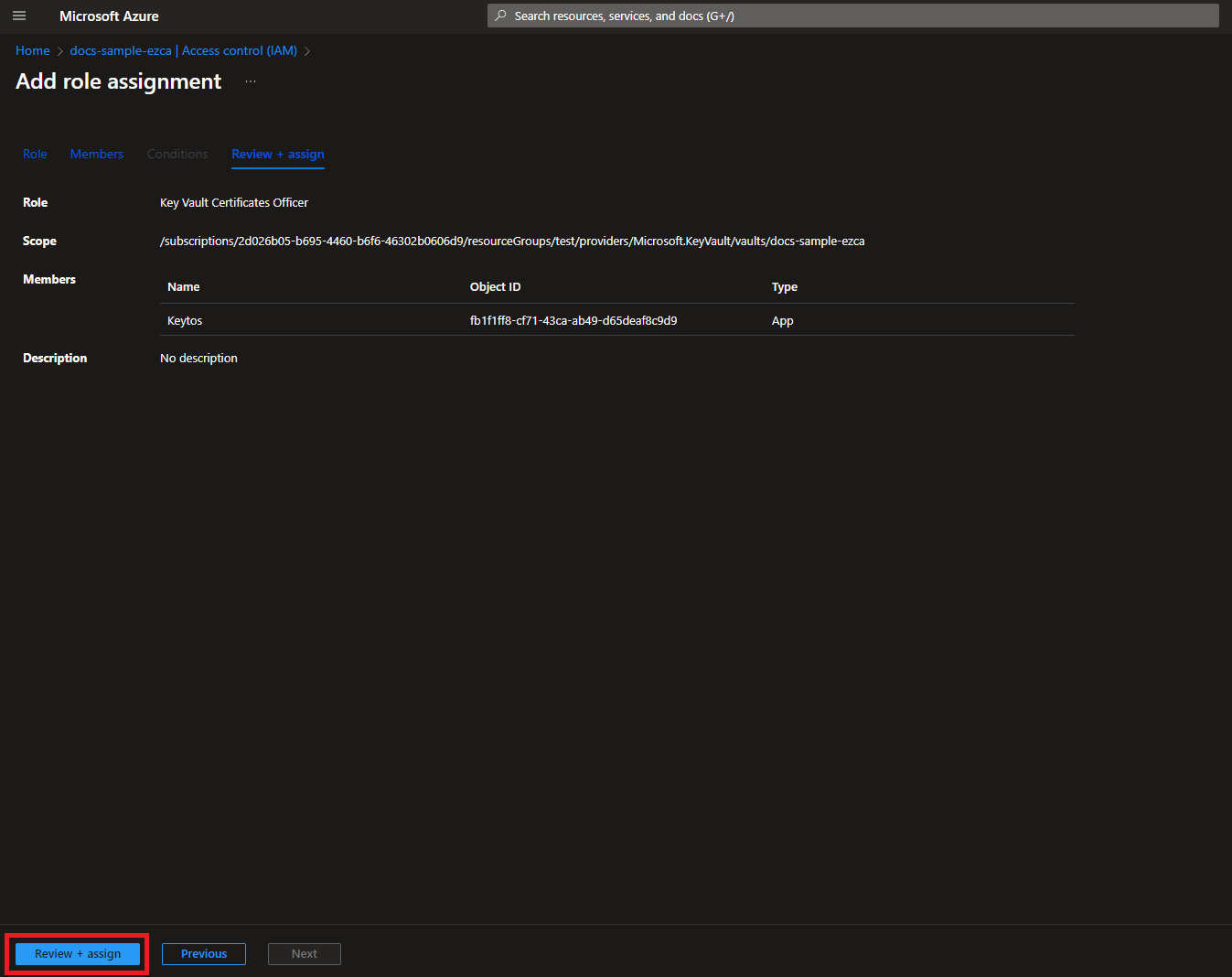
- Click the Review + assign button
- Click the Review + assign button
Adding EZCA IP Address to Azure Key Vault Firewall
If your Key Vault has a firewall enabled, you will need to add the EZCA IP address to the Key Vault firewall to allow EZCA to manage the certificates in the Key Vault. To find the EZCA IP addresses, please go to the EZCA portal status of your instance for example: https://portal.ezca.io/status and copy the IP addresses from the “Outbound IP Addresses” section.
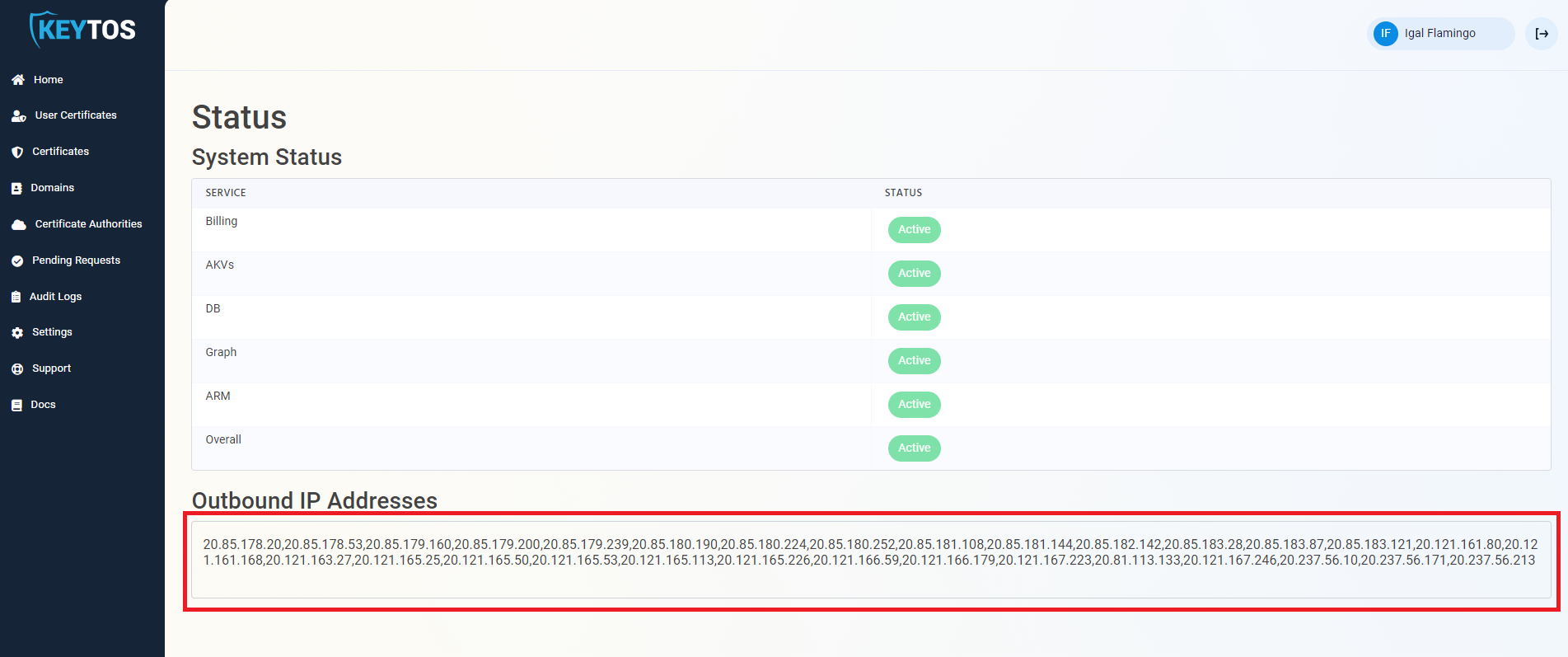 you can now add the IP addresses to the Key Vault firewall. Since the EZCA IP addresses are subject to change, we recommend adding the entire IP range to the Key Vault firewall. To do this, you can use the following PowerShell script to add the IP range to the Key Vault firewall. Replace the
you can now add the IP addresses to the Key Vault firewall. Since the EZCA IP addresses are subject to change, we recommend adding the entire IP range to the Key Vault firewall. To do this, you can use the following PowerShell script to add the IP range to the Key Vault firewall. Replace the $ipRange variable with the IP range from the EZCA portal status page:
Connect-AzAccount
$ipRange = ""
$resourceGroupName = "" # Replace with your resource group name
$keyVaultName = "" # Replace with your Key Vault name
$ipArr = $ipRange.Split(",")
Add-AzKeyVaultNetworkRule -VaultName $keyVaultName -ResourceGroupName $resourceGroupName -IpAddressRange $ipArr