Adding EZSSH Access to Endpoints With Bash Script
Prerequisites
Overview
EZSSH uses SSH Certificates to authenticate to endpoints. Since this is a OpenSSH supported protocol, no custom code has to run on your endpoints for authentication to work. By adding your EZSSH Certificate to your TrustedUserCAKeys your endpoint will start working with EZSSH.
In this page we will go through how to do this with running a bash script on an existing endpoint. You might also be interested in:
Getting the Script
- go to https://portal.ezssh.io/
- Select the policy type you want to access (Azure Policy or Hybrid Policy)
- Once you are in the policy type page, expand the policy you want to set up. In this example we will expand “AWS EastUS Policy”
- Click the “Get Script” button at the top of the policy.
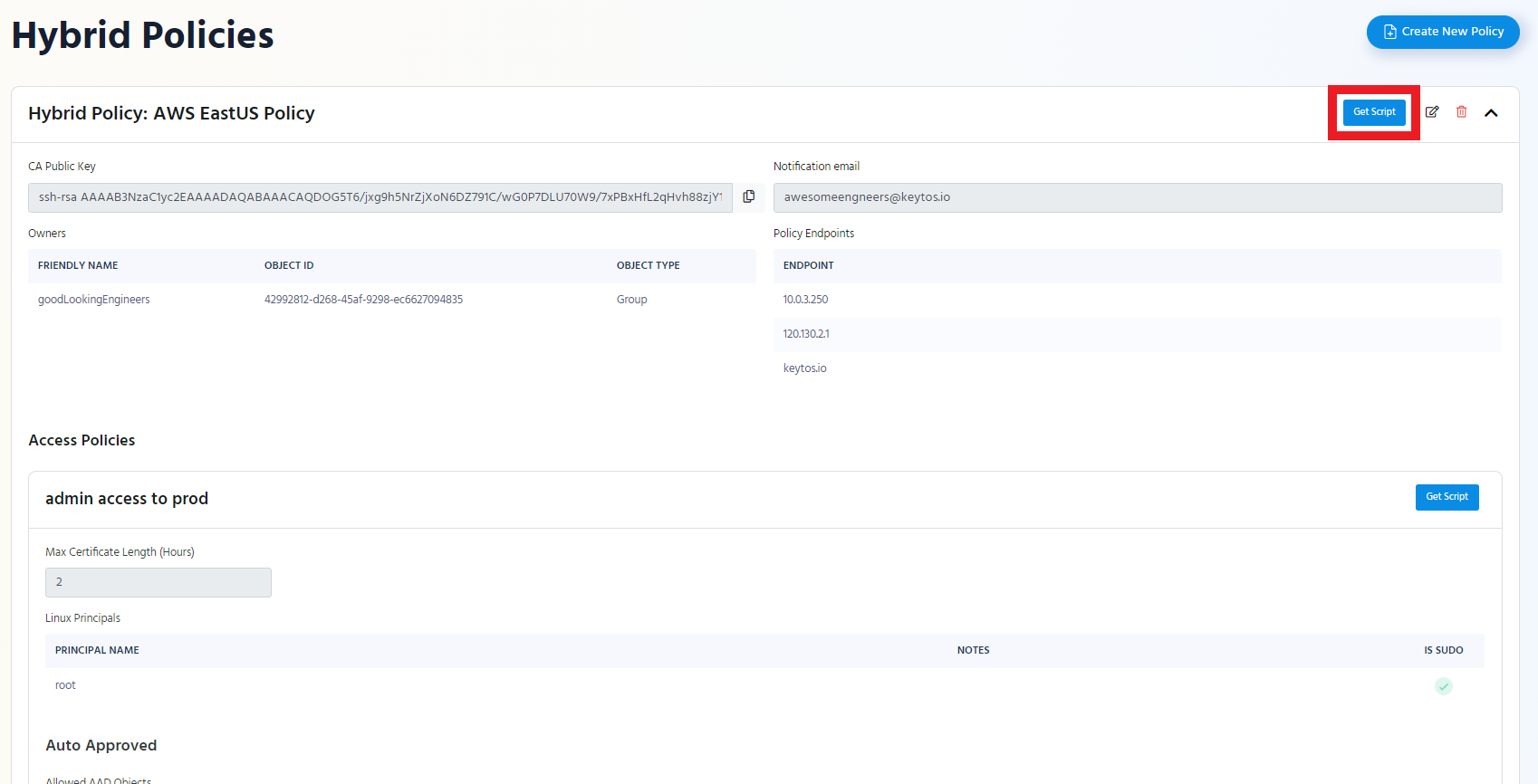
If you want to only set up the Linux principals of an access policy click the “Get Script” button of that access policy.
- Switch to the “Bash Script” Tab
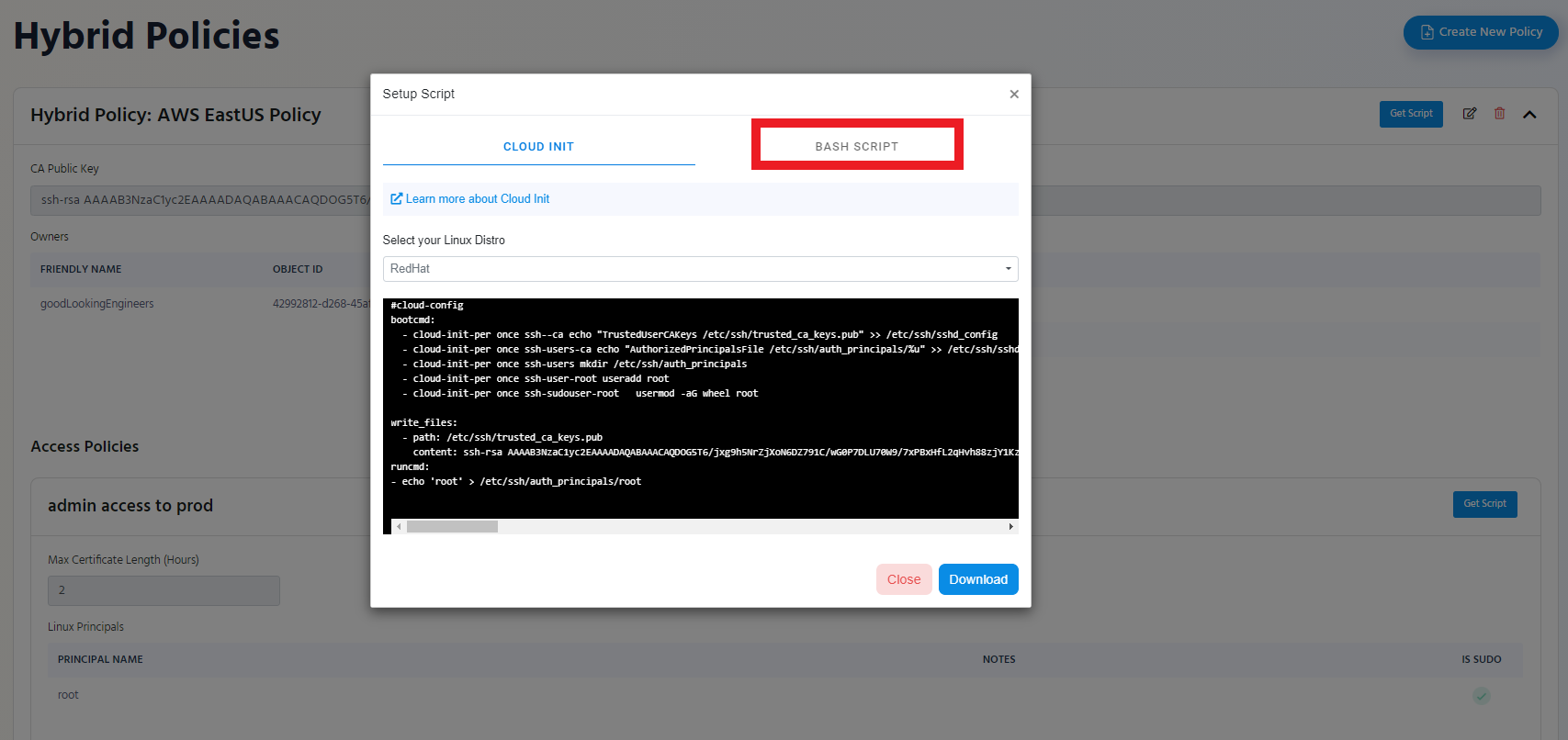
- Click the “Download” Button
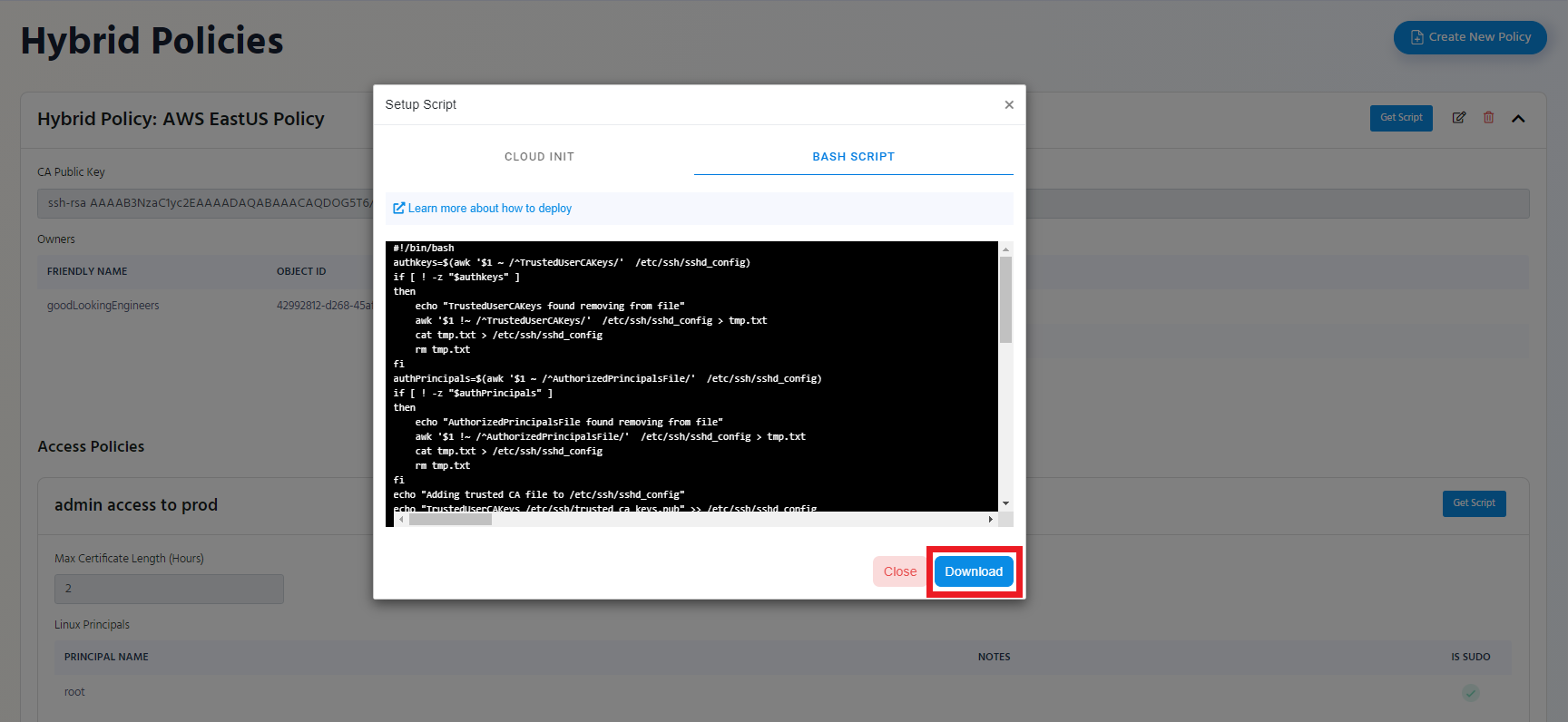
- The Script will be downloaded to your Downloads Folder.
Understanding the Script
This Script should get you started with accessing your endpoints using EZSSH. However, it is important to understand what it does, since you might want to modify it to fit your deployment. In this Section we will go through a sample script line by line.
First we check if there has been a CA file added to the sshd_config, if we find one we remove it.
#!/bin/bash
authkeys=$(awk '$1 ~ /^TrustedUserCAKeys/' /etc/ssh/sshd_config)
if [ ! -z "$authkeys" ]
then
echo "TrustedUserCAKeys found removing from file"
awk '$1 !~ /^TrustedUserCAKeys/' /etc/ssh/sshd_config > tmp.txt
cat tmp.txt > /etc/ssh/sshd_config
rm tmp.txt
fi
Then we check if an AuthorizedPrincipalsFile was set in the sshd_config, if we find one we remove it.
authPrincipals=$(awk '$1 ~ /^AuthorizedPrincipalsFile/' /etc/ssh/sshd_config)
if [ ! -z "$authPrincipals" ]
then
echo "AuthorizedPrincipalsFile found removing from file"
awk '$1 !~ /^AuthorizedPrincipalsFile/' /etc/ssh/sshd_config > tmp.txt
cat tmp.txt > /etc/ssh/sshd_config
rm tmp.txt
fi
Then we specify our own TrustedUserCAKeys file location in sshd_config
echo "Adding trusted CA file to /etc/ssh/sshd_config"
echo "TrustedUserCAKeys /etc/ssh/trusted_ca_keys.pub" >> /etc/ssh/sshd_config
Then we specify the location of our Authorized principals
echo "Adding Authorized Principals file to /etc/ssh/sshd_config"
echo "AuthorizedPrincipalsFile /etc/ssh/auth_principals/%u" >> /etc/ssh/sshd_config
Then we add the EZSSH Policy CA Public key to /etc/ssh/trusted_ca_keys.pub
echo "Adding CA Public Key"
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAACAQDOG5T6/jxg9h5NrZjXoN6DZ791C/wG0P7DLU70W9/7xPBxHfL2qHvh88zjY1KzH/wEYYuDpanuo7n5SrEDNaJTnHnBVDC/g6JQXQ1vXbyiggzW4G4Uw2eau5LQYNG8K9U5kamu9+a8g4sIHpE0G6N+tQiKWR1Yby3VMgZYZKlR55SIXjMVOpCwKcoiMcxwqsWmGnFoTgnXPc4uLVpOVvFNOkSYbA7bguTXQfPqFsZzaKAgl6TsguIg+XfiAtMsUb7NQip9VW75Gb6IacsJUeeh9xxaYo1URNupIyh7oLWU0p0UUoPa4yMroslZ/Qa0lfd/oQU5tRVCzmmKd1r3pUGFzJfFRymjm3p94EjCYikXfWaAM7HWvlOKBr9C2t7Zin2YWdb4RDijD3qGjRimc+9obImeY8Lh0ebdkfa87WnYCF6rNjxCNMTNFCinaUL9I7P3Gn7+tH0aqHAV8vYM944Poa96wkj3kVsLZlPUTHzSdb2hGEJhbR11O2etYUJkFjQRf1p8ShKPQ/lUV7FXj8EiJj2Ku9lDJ8JZ2/RGYWic9dn/qFYub7tOWVyUZ5oIMe2q7M3aJo/VDGQyQXu7ChAzZ3GNCT6A1Ux7SlGUYqHTUifNlb66hI8r1YQdneUu9SIeGrjxK247sgjYQ5vyzVk44QfE9szL+1pYgWo3QynyxQ==" > /etc/ssh/trusted_ca_keys.pub
Then we check if the directory we specified for auth principals exists, if not we create it.
if [ ! -d "/etc/ssh/auth_principals" ]; then
mkdir /etc/ssh/auth_principals
fi
Later we set a bool to see which type of sudo does your distro use:
sudogroup=$(awk '$1 ~ /^sudo/' /etc/group)
Then for each user on the policy we will try to create it and if it was marked as sudo we will try to add it to the sudo group.
This script will create the user and add them to the sudo group if appropriate, but will not create a home directory for each user.
Check if the user exists (in this example the user is called “root”), if it doesn’t exist, create the user.
if id root &>/dev/null;
then
echo 'Skipping user root since it already exists';
else
echo 'Adding user root';
useradd root
fi
Then if the user is set as sudo in EZSSH the script will contain the following if statement to add it to the sudo group.
if [ ! -z "$sudogroup" ]
then
usermod -aG sudo root
else
usermod -aG wheel root
fi
Then we add the user as an authorize principal for authentication.
#Adding principal for authentication
echo 'root' > /etc/ssh/auth_principals/root
Once we have added all the users, we restart the ssh service for it to take the changes we made.
service ssh restart
Running the Script
- SSH into the endpoint where you want to enable the policy.
- Run the Script as sudo
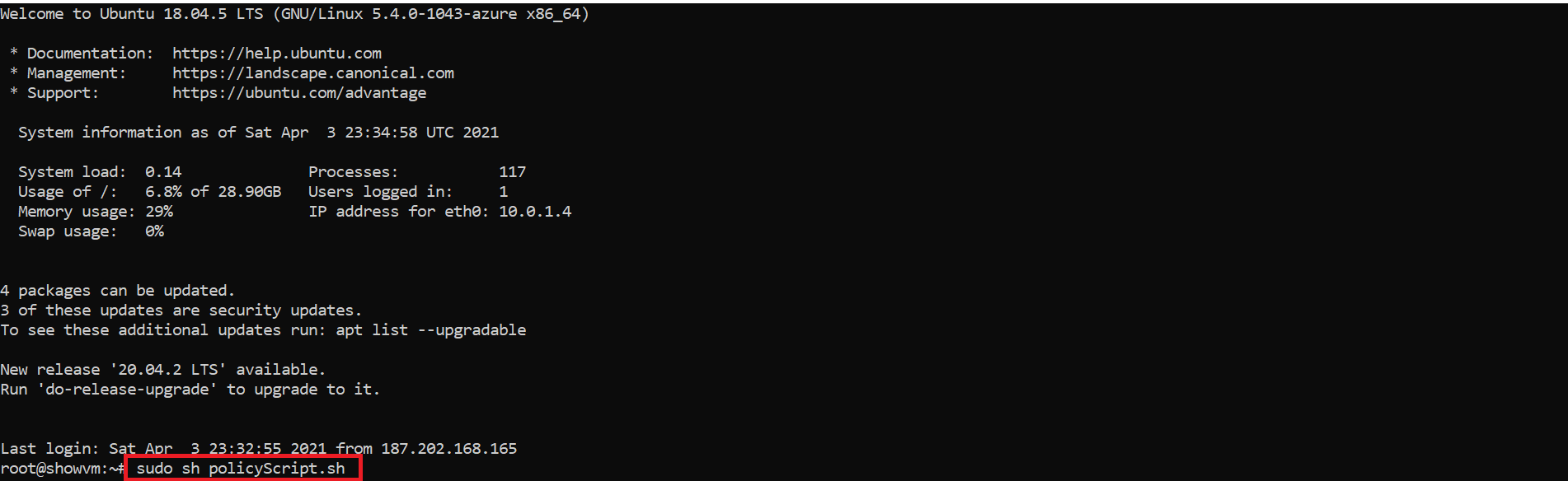
- You are ready to start using your EZSSH policy in this endpoint.