How To Automatically Renew an X509 Certificate
Why I Should Automatically Renew Certificates
By Design certificates have an expiration date, when a certificate is approaching its expiration date, it is necessary to renew it to not lose access to the resources the certificate was used to authenticate to. Over 80% of organizations have reported a certificate related outage in the past two year. As the number of certificates an organization has increases, the risk of an outage increases exponentially. To avoid this, it is necessary to have an automatic certificate renewal process in place. While many protocols such as ACME and SCEP Take care of automatically rotating certificates, EZCA has other tools that can help you automate the certificate lifecycle for certificates that are not issued through these standards.
How To Auto Renewed Certificates
If a certificate is created in one of the locations that EZCA supports auto rotation, the certificate can be set to be auto renewed automatically by EZCA. If the certificate is set for auto renewal, EZCA will take care of the renewal automatically and will email the domain owners when the certificate is renewed.
Renewal in EZCA Supported Key Management Systems
If the certificate is created and maintained in a Key Management System that EZCA supports auto rotation of certificates but it is not set for auto renewal, an approved requester of the domains contained in that certificate will have to do the following steps:
- Navigate to https://portal.ezca.io/
- Navigate to Certificates.
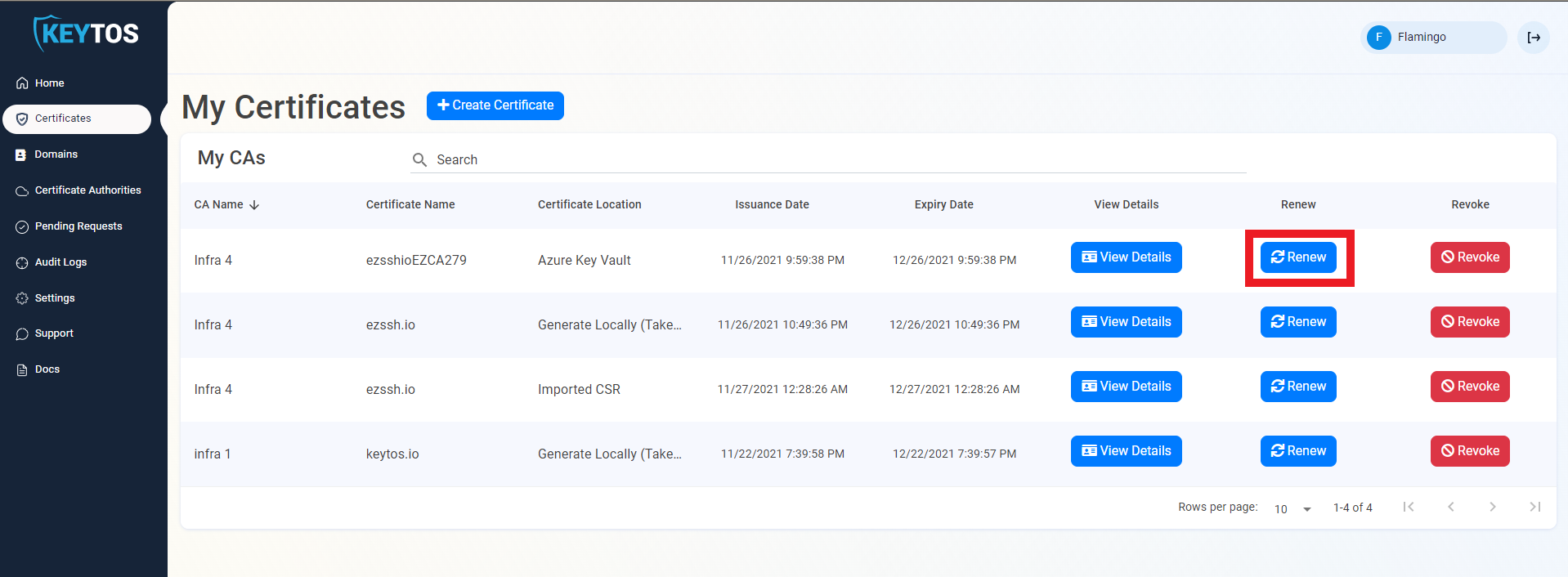
- Click the renew button for the certificate the user wants to renew.
- EZCA will renew the certificate and add it to the corresponding key management system as a new version of the certificate.
Renewal For Certificates Not Managed by EZCA
If a certificate was created and stored in a location that is not managed by EZCA (For Example: a CSR was imported or a Certificate was created on the browser) an approved requester of the domains contained in that certificate will have to do the following steps:
- Navigate to https://portal.ezca.io/
- Navigate to Certificates.

- Click the renew button for the certificate the user wants to renew.

- The User will be presented with the create certificate screen.
- The user can pick their preferred method to create a certificate.
- Once the certificate is created, the user will install the certificate in all the locations where the previous certificate was being used.
How To Renew an SSL Certificates in C#
In Keytos our goal is to make PKI services as easy to use for every person in the world. One way to make this a reality is by removing humans as much as possible from the equation. To help companies achieve this goal, we have created a sample C# console application that uses a certificate from the local certificate store in windows to authenticate with EZCA and requests a new certificate. See Sample Code