Scan Private Networks
Prerequisites
Introduction
While many certificates are publicly trusted and added to certificate transparency logs, many large organizations also manage an internal PKI that issues certificates for critical internal resources. EZMonitor enterprise plans include scanning of private networks to also monitor private certificates. In this page we will go over how to set up our scanning tool to scan your network and report the finding to your EZMonitor account.
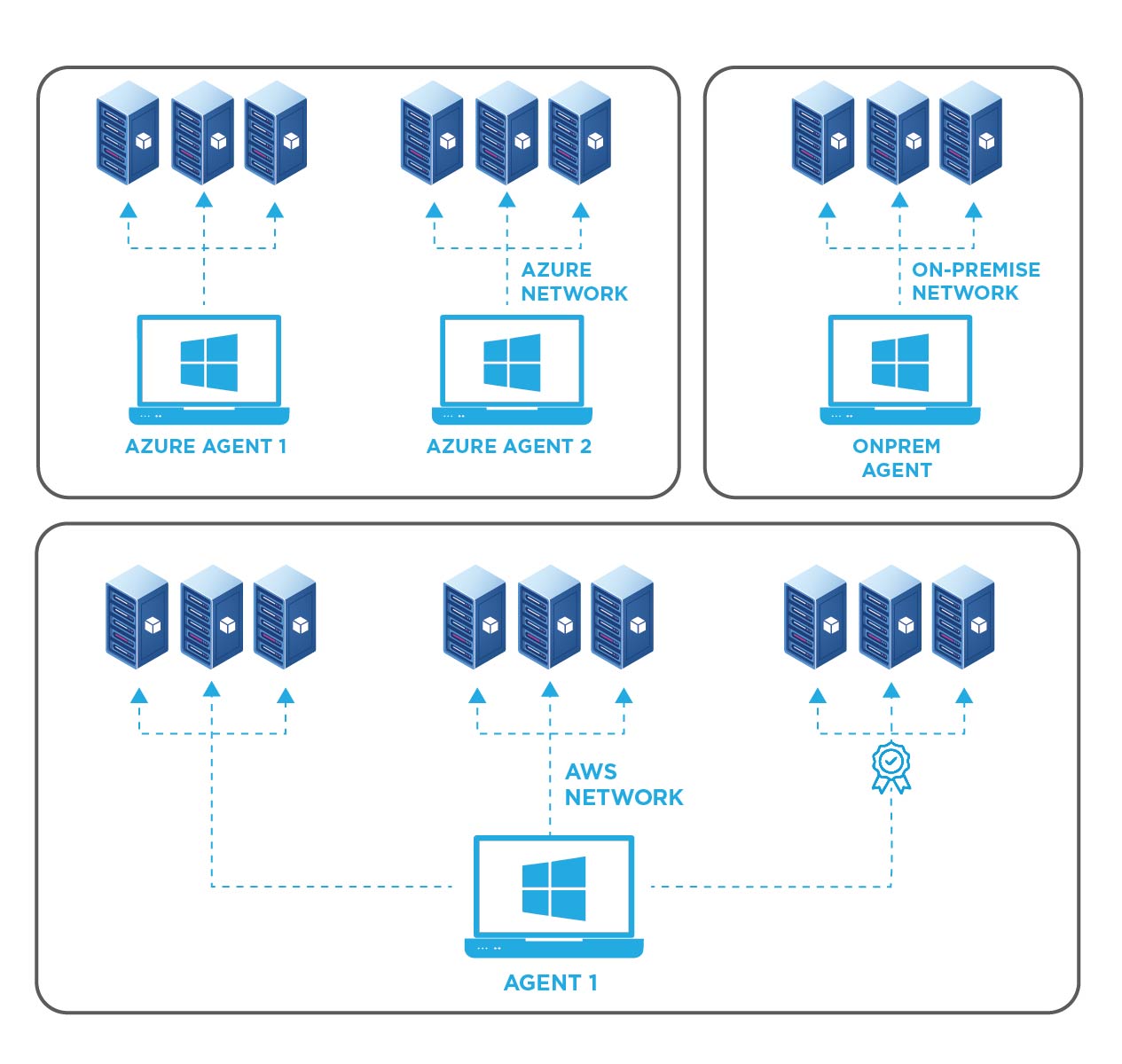
How To Monitor Internal SSL Certificates
EZMonitor allows you to monitor all your SSL certificates across all your networks. To give you an organized view, we break it down per network, then each network has one or more agents and those agents have a list or range of endpoints assigned. First we must start by creating a private network.
Registering a Private Network for SSL Monitoring
- Fist, go to the EZMonitor Portal.
- Login.
- In the menu, select “Private Endpoints”.
- Click The register network button.
- Enter the name of the network you want to monitor.
- Click the register network button.
- Once your network is created, click the “View Agents” button.
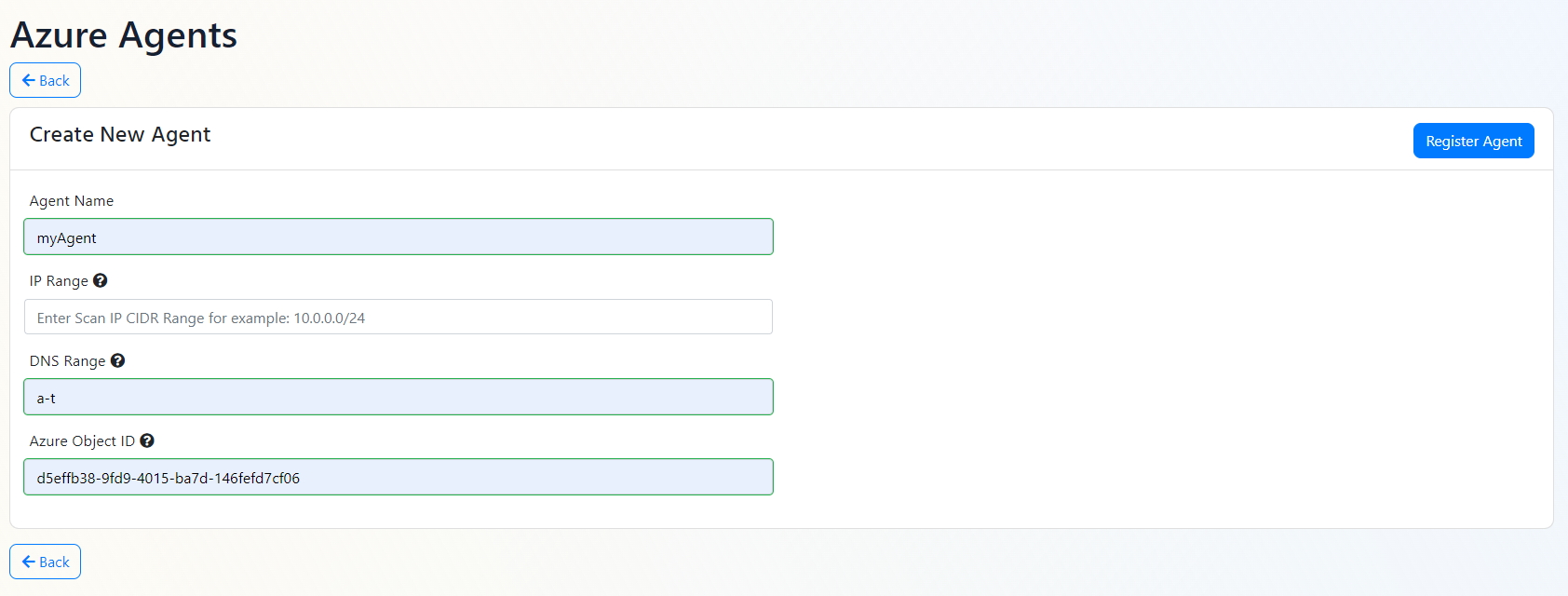
- Click the “Register New Agent” button.
- Enter the name of the agent.
- As previously mentioned, in addition to assigned endpoints, EZMonitor allows you to assign either IP rages or alphabetical DNS rages to your agent. If you are assigning a range of IP addresses, enter the IP range in CIDR format.
- If you are assigning a range of DNS names, enter the alphabetic range in the following format: a-z. in this case, EZMonitor will scan all the DNS names in the range a-z.
- For the agent to authenticate with EZMonitor, it must have an Azure identity enter the object ID of the identity you want to use.
- Click the “Register Agent” button.
- Once the agent is registered, you will see it in the list of agents. If you would like to add a list of endpoints for this agent to scan, navigate down to the agent you just created, and either enter the domains one by one or upload a txt file with the list of domains (one per line).
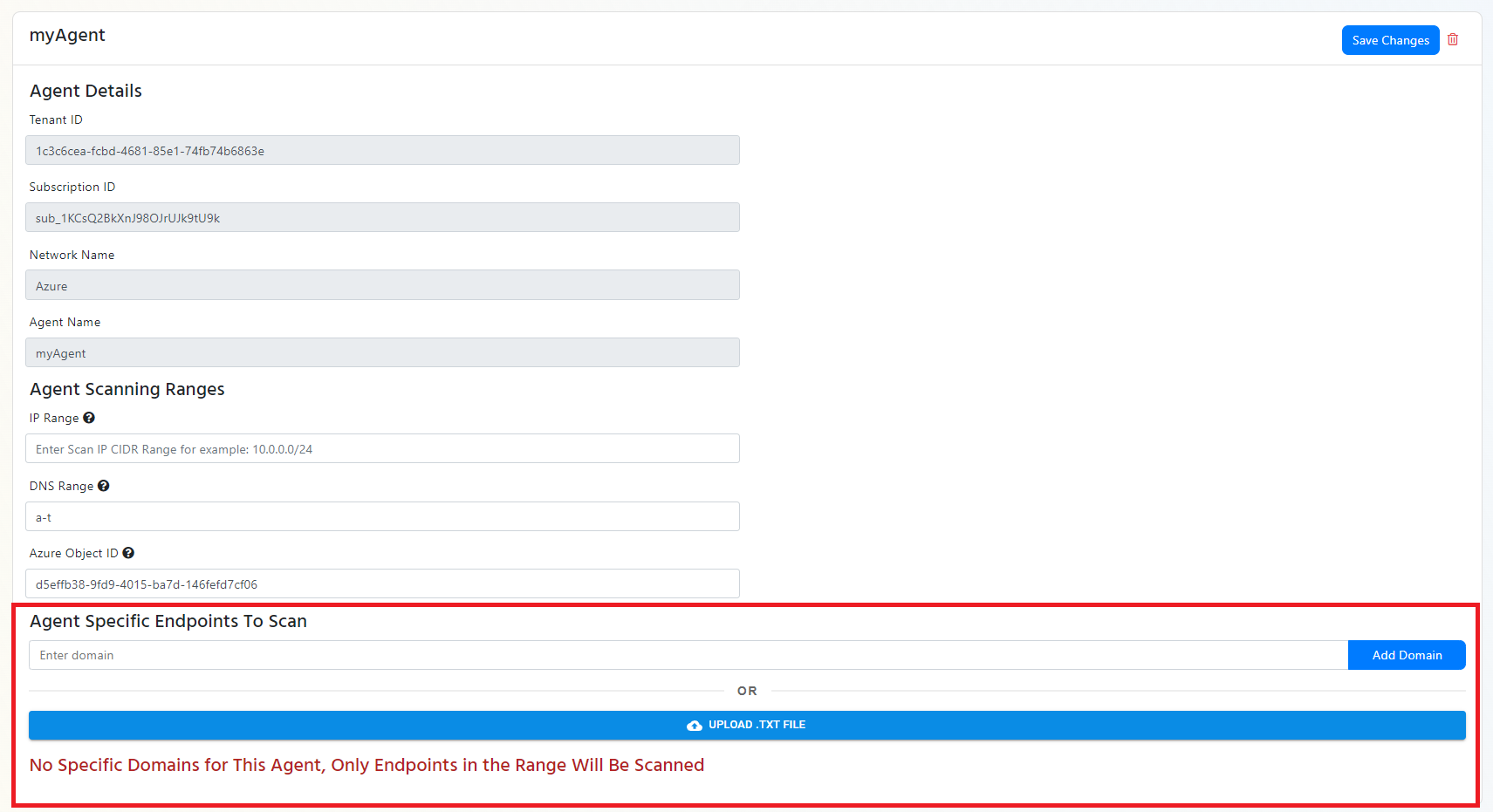
- repeat the process for all the agents and networks you want to create.
Using EZScan
EZScan (download) is the tool that helps EZMonitor gain visibility into your private network. This tool must run on a Windows computer in your network and have 443 out to EZMonitor.
Active Directory Certificate Services (ADCS) Certificate Download
If you would like EZMonitor to connect to your ADCS certificate authority to inventory the certificates issued by your CA follow the steps below to gather the inventory, while this is a great way to get started with certificate discovery, it is not required.
- Download the EZScan tool to a domain joined machine.
- Run EZScan from an account (we recommend using a gMSA) that has read access to the CA’s database. With the following parameters:
- -a the name of the agent you are running.
- -n the name of the network you are scanning.
- -ca and the CA name in the format: CA.HOSTNAME.DOMAIN\CA NAME
- (Optional) -t and the comma separated list of templates you want EZScan to get. If this option is not passed, all certificates will be downloaded.
- -azt your Azure tenant ID
- -sub your EZMonitor subscription ID
- EZMonitor can use your MSI or Azure CLI token to authenticate EZMonitor. However, if you prefer using an Azure Service principal, you must pass the following parameters:
- -app the application ID of the service principal being used.
- -cert the certificate subject name used for authentication (EZScan will look in the user certificate store and get the latest certificate matching that subject name).
- (Optional) -ai an application insights connection string where EZScan can send run telemetry, this enables you to create alerts and detect issues with EZScan.
.\EZScan.exe -a AGENTNAME -n NETWORKNAME -ca "CA.HOSTNAME.DOMAIN\CA NAME" -t 1.3.6.1.4.1.311.21.8.60601.4814192.14238359.2561337.13409557.15.15002822.720910 -azt YOURAZURETENANTID -sub YOUREZMONITORSUBSCRIPTIONID
Active Directory DNS Lookup
If you assigned your agents a range of DNS names, EZScan can query your Active Directory DNS server and get all the DNS entries in the range and add them to EZMonitor.
- Download the EZScan tool to a domain joined machine.
- Run EZScan from an account (we recommend using a gMSA) that has read access to the to the DNS entries. With the following parameters:
- -a the name of the agent you are running.
- -n the name of the network you are scanning.
- -dns this is the hostname of your DNS Server: HOSTNAME
- -domain the domain (DNS Zone) you want EZScan to scan.
- -azt your Azure tenant ID
- -sub your EZMonitor subscription ID
- EZMonitor can use your MSI or Azure CLI token to authenticate EZMonitor. However, if you prefer using an Azure Service principal, you must pass the following parameters:
- -app the application ID of the service principal being used.
- -cert the certificate subject name used for authentication (EZScan will look in the user certificate store and get the latest certificate matching that subject name).
- (Optional) -ai an application insights connection string were EZScan can send run telemetry, this enables you to create alerts and detect issues with EZScan.
.\EZScan.exe -a AGENTNAME -n NETWORKNAME -dns HOSTNAME -domain YOURDOMAIN -azt YOURAZURETENANTID -sub YOUREZMONITORSUBSCRIPTIONID
Scanning The Network
To scan the network to detect detect SSL certificates, EZScan will download the list of domains and IP addresses gathered in the previous steps and will scan each one of them and will record the SSL status of the endpoint. To start the scan, run EZScan with the following parameters:
-
-a the name of the agent you are running.
-
-n the name of the network you are scanning.
-
-azt your Azure tenant ID
-
-sub your EZMonitor subscription ID
-
(Optional) -p Ports to scan, by default EZscan will scan port the ports in the table below, if you want to scan a custom port range, enter the port numbers in a comma separated list.
Port Protocol Usage 25 SMTP Email relay 80 HTTP Web browsing 110 POP3 Retrieving email from a mail server to an email client 443 HTTPS Secure web browsing 465 SMTPS Email submission from an email client to an email server 563 NNTPS Secure news server access 587 SMTP Email submission from an email client to an email server 636 LDAPS Secure access to LDAP directories 990, 989 FTPS Secure file transfers 992 Telnet over SSL/TLS Secure terminal access 993 IMAPS Secure mail retrieval 995 POP3 over SSL/TLS Secure mail retrieval 1433 Microsoft SQL Server Secure database connections 2484 Oracle DB Secure database connections 27017 MongoDB Secure database connections 3306 MySQL Secure database connections 3389 RDP over SSL/TLS Secure remote desktop access 5432 PostgreSQL Secure database connections 6514 Secure Syslog Secure system logging 6697 IRC over SSL/TLS Secure Internet Relay Chat connections 8080 HTTP Web browsing (often over SSL/TLS) 8443 HTTPS Secure web browsing (alternate port) 8883 MQTT over SSL/TLS Secure IoT messaging 9200 Elasticsearch Secure connections to Elasticsearch clusters 9999 IRC over SSL/TLS Secure Internet Relay Chat connections (alternate port) -
EZMonitor can use your MSI or Azure CLI token to authenticate EZMonitor. However, if you prefer using an Azure Service principal, you must pass the following parameters:
- -app the application ID of the service principal being used.
- -cert the certificate subject name used for authentication (EZScan will look in the user certificate store and get the latest certificate matching that subject name).
-
(Optional) -ai an application insights connection string were EZScan can send run telemetry, this enables you to create alerts and detect issues with EZScan.
.\EZScan.exe -a AGENTNAME -n NETWORKNAME -azt YOURAZURETENANTID -sub YOUREZMONITORSUBSCRIPTIONID