How To Troubleshoot Cloud RADIUS
How To Troubleshoot RADIUS Configuration in EZRADIUS
If you have setup your Cloud RADIUS instance and are having trouble authenticating users, this guide will help you troubleshoot your Cloud RADIUS configuration for EAP-TLS or Entra ID Wifi Authentication in EZRADIUS.
- The first step to troubleshoot your RADIUS connection is to go to your EZRADIUS portal and click on Audit Logs. This will have most of the information you need to troubleshoot your RADIUS connection.
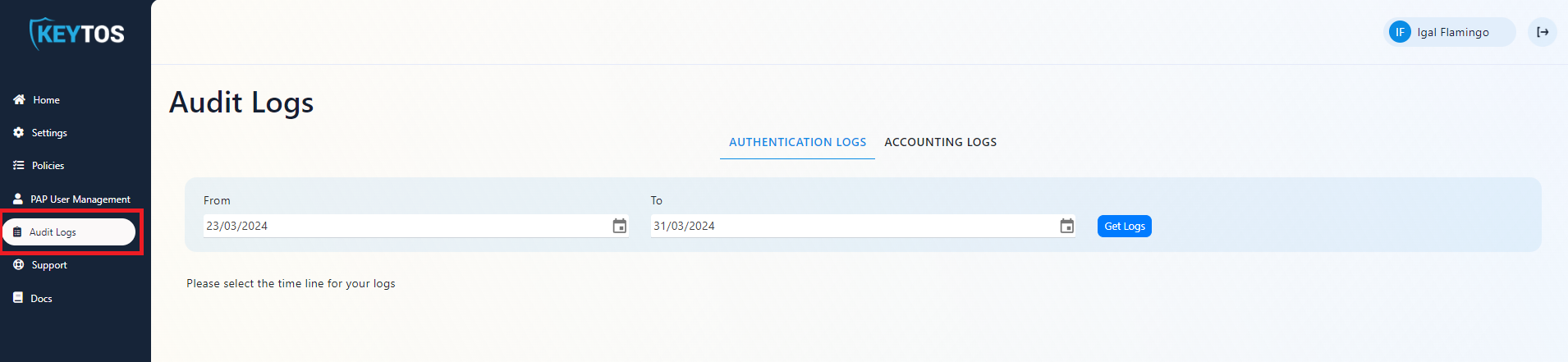
- In the top tab selector select “Authentication Logs” to view the logs of users authenticating to your Cloud RADIUS instance.
- In the next sections we will go through some common issues and how to troubleshoot them.
How to Troubleshoot No Logs in Authentication Logs
- In here we should see some connection attempts from your access points. If you don’t see any logs, it means your access points are not sending the RADIUS requests to your Cloud RADIUS instance. or that the wrong IP address is configured in your access points.
- Check your IP address in Nord VPN page and ensure that that is the IP address you have configured in your RADIUS policy:
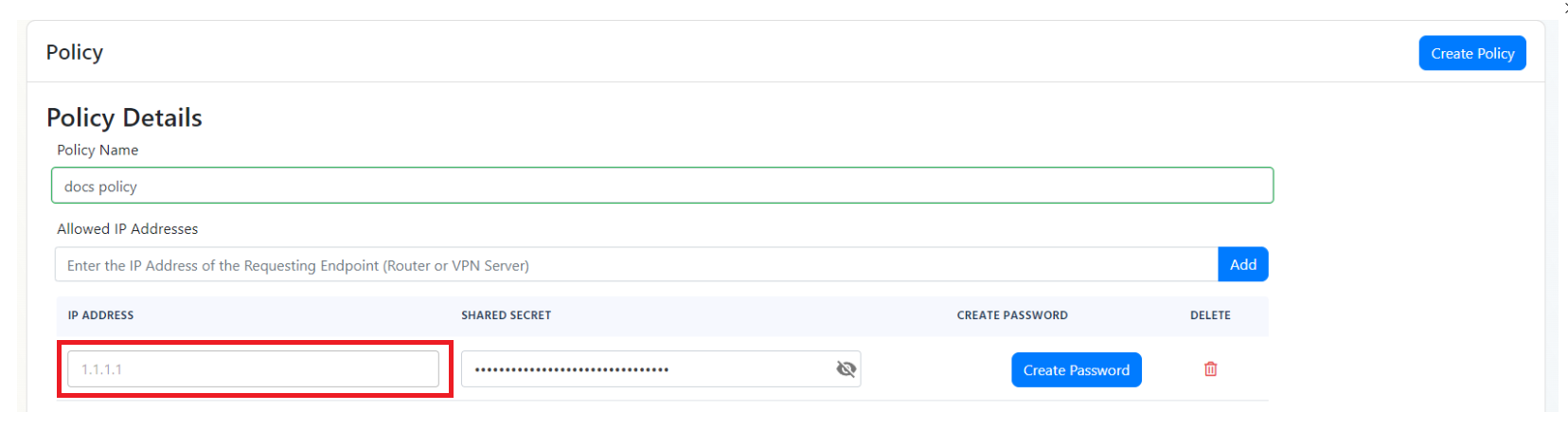
- If the IP address is correct, check your access point configuration and ensure that the RADIUS server is configured correctly.
- You can also Run Wireshark on your test machine with the filter ‘udp port 1812’ to see if the RADIUS requests are reaching your Cloud RADIUS instance. This is how a successful RADIUS request looks like:
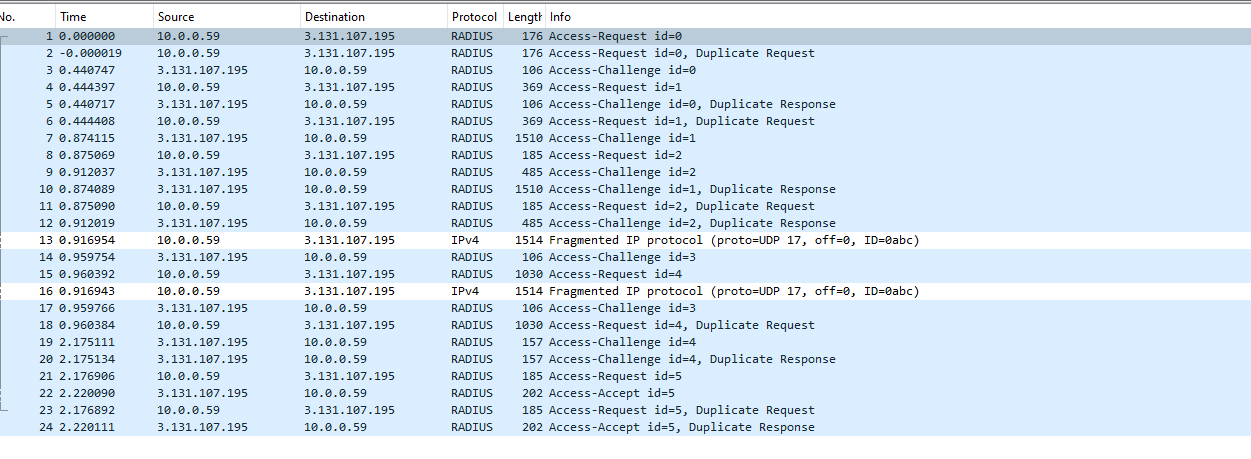
- If you only see one way ensure that your firewall is not blocking the RADIUS requests.
How to Troubleshoot RADIUS Authentication Failure
- If you see an error “The wrong shared secret was used to connect your network to EZRADIUS please check your configuration” or “Incorrect Shared Secret” it means that the shared secret configured in your access point is incorrect.
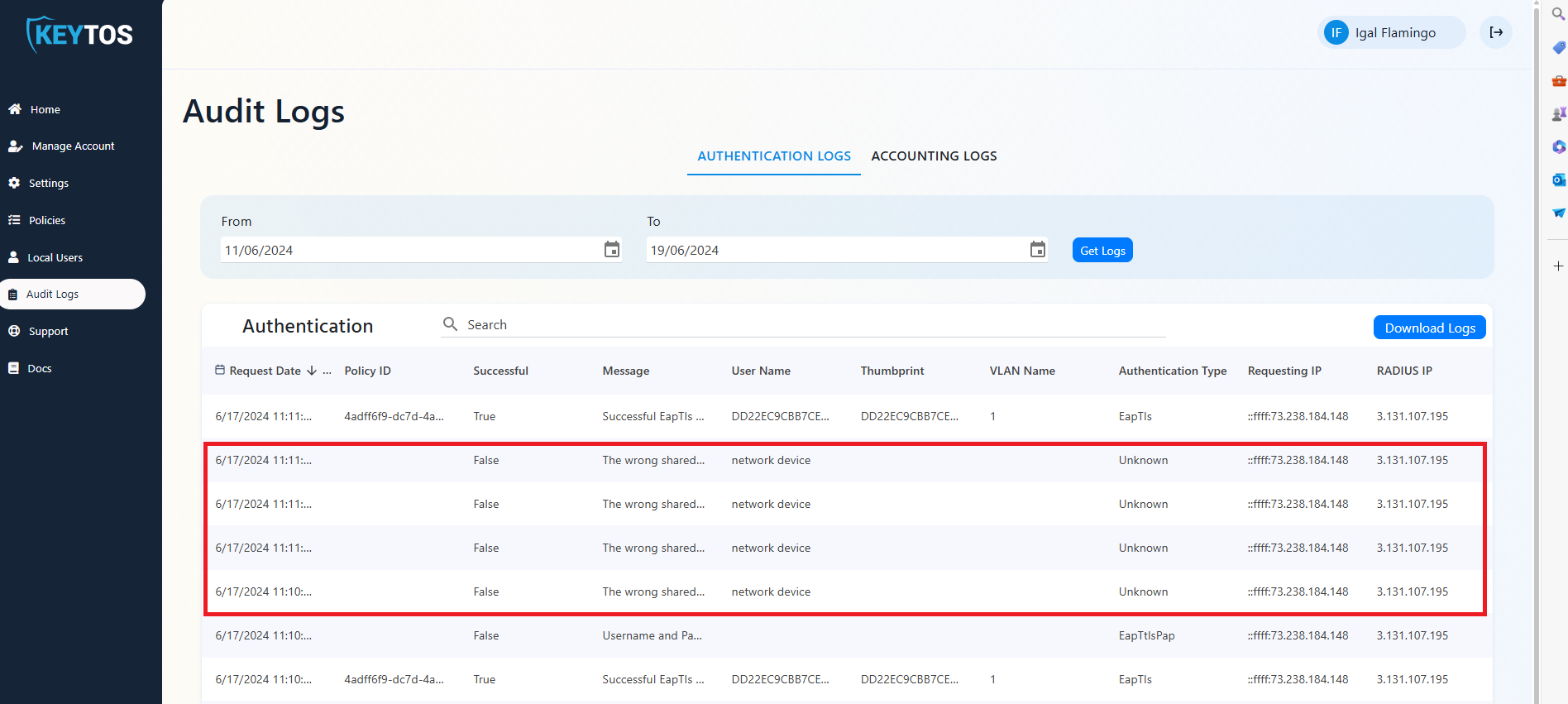
- This means that your access point is sending the RADIUS request with the wrong shared secret. This can be caused due to 3 reasons:
- the wrong secret was sent by the networking device. Ensure that the shared secret in your access point matches the shared secret in your RADIUS policy.
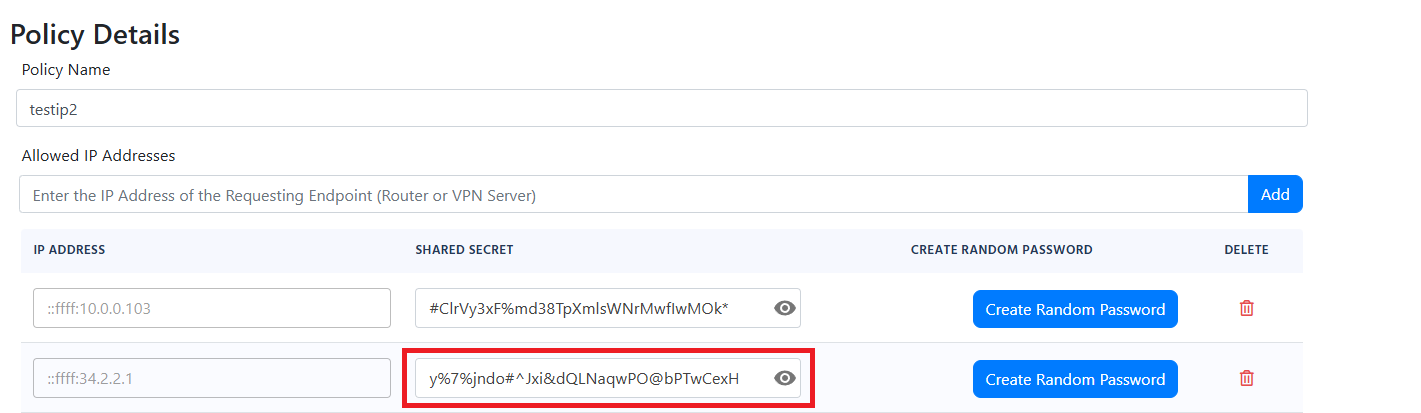
- The shared secret was recently changed in your RADIUS policy, both networking devices and EZRADIUS have caching mechanisms that might take a few minutes to update.
- The shared secret is too long for your networking device. Some networking devices have a limit on the length of the shared secret. To troubleshoot this ensure that the shared secret is less than 16 characters.
- the wrong secret was sent by the networking device. Ensure that the shared secret in your access point matches the shared secret in your RADIUS policy.
How to Troubleshoot RADIUS Authentication EAP-TLS Failure
In EAP-TLS authentication, the client sends a certificate to the RADIUS server. The RADIUS server validates the certificate and if it is valid, it sends an Access-Accept message to the client. If the certificate is invalid, the RADIUS server sends an Access-Reject message to the client. There are many issues that might be causing the EAP-TLS authentication to fail. Here are some common issues and how to troubleshoot them:
Most of them start with the same error message so it is important to read the error message carefully to understand the root cause of the issue.
How To Troubleshoot EAP-TLS Authentication Failure Invalid Certificate
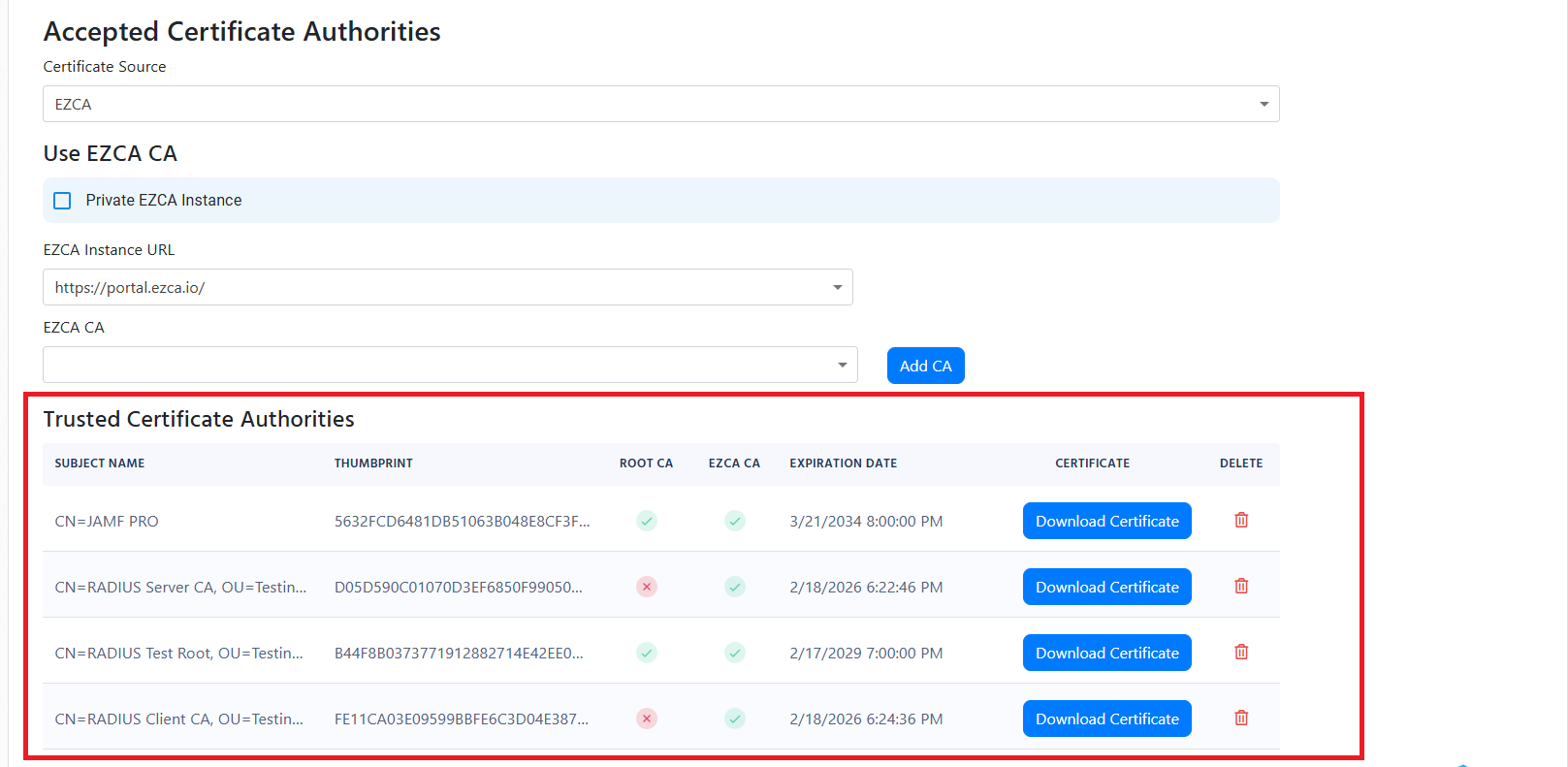
- If you see an error “Failed to build and validate certificate (XXXX): RevocationStatusUnknown: unable to get certificate CRL OfflineRevocation: unable to get certificate CRL UntrustedRoot: self-signed certificate in certificate chain” it means that one of the certificates in the certificate chain is invalid. Please ensure that all the certificates in the certificate chain are part of your Policy Trusted Certificate Authorities.
How To Troubleshoot EAP-TLS Authentication Failure Certificate Expired
- If you see an error “Failed to build and validate certificate (XXX): NotTimeValid: certificate has expired” it means that the certificate has expired. Please ensure that the certificate is not expired.
How To Troubleshoot EAP-TLS Authentication Failure Failed to build certificate chain to a valid CA
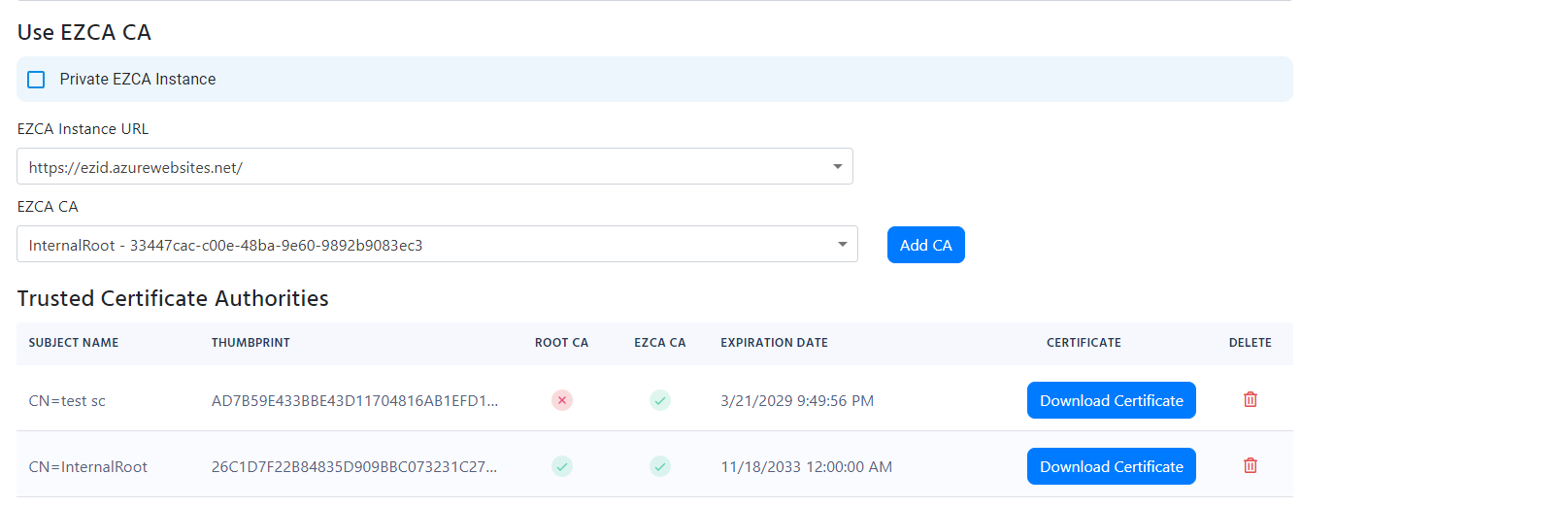
If you see an error “Failed to build and validate certificate (XXX): UntrustedRoot: self-signed certificate in certificate chain” or “Invalid certificate: Failed to build certificate chain to a valid CA” it means that the certificate is not trusted. Please ensure that the certificate is part of your Policy Trusted Certificate Authorities.
How To Troubleshoot EAP-TLS Authentication Error Validating CRL
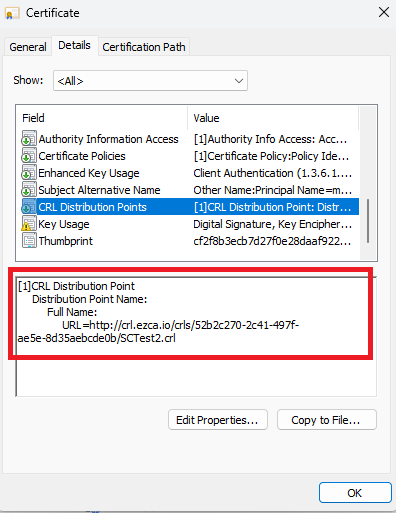
If you see an error “Exception occurred when validating the CRL” it means that the Certificate Revocation List (CRL) was not accessible by EZRADIUS. Please ensure that the certificates you are using have a valid CRL accessible through http (this is for the full chain, so it might also be the Root CA CRL).
How To Troubleshoot TLS Handshake Failure
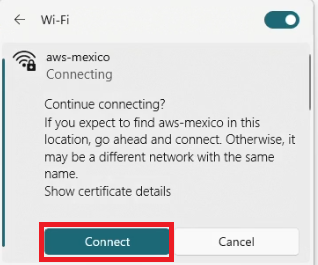
This error usually occurs when the client and the server cannot agree on the cryptographic tunnel to start the authentication. The most common issue with this is the client not trusting the server certificate. For this you must ensure that the server certificate is trusted by the client (if testing manually just accept when it as).
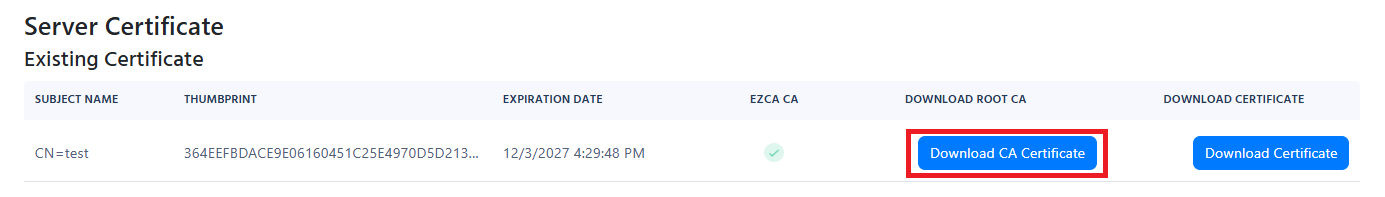
 When using an MDM you must distribute the Root Certificate Authority, (found under “Server Certificate in your RADIUS Policy) to your devices. and Add the subject name and IP address of the RADIUS server to the wifi profile.
When using an MDM you must distribute the Root Certificate Authority, (found under “Server Certificate in your RADIUS Policy) to your devices. and Add the subject name and IP address of the RADIUS server to the wifi profile.
 The other issue is if the client does not support the cryptographic tunnel that the server is trying to use. In this case, we recommend looking at the device logs to see what is the issue.
The other issue is if the client does not support the cryptographic tunnel that the server is trying to use. In this case, we recommend looking at the device logs to see what is the issue.
How To Troubleshoot Client Rejected RADIUS Server Certificate
For this you must ensure that the server certificate is trusted by the client (if testing manually just accept when it as).
 When using an MDM you must distribute the Root Certificate Authority, (found under “Server Certificate in your RADIUS Policy) to your devices. and Add the subject name and IP address of the RADIUS server to the wifi profile.
When using an MDM you must distribute the Root Certificate Authority, (found under “Server Certificate in your RADIUS Policy) to your devices. and Add the subject name and IP address of the RADIUS server to the wifi profile.

How to Troubleshoot RADIUS Password Authentication
- If you see the error “Username and Password authentication failed. Error password expired” it means that the password has expired. Please reset the password in the EZRADIUS portal.