How-To: Export your RADIUS Logs to CrowdStrike Falcon
EZRADIUS enables your security team to monitor critical user actions by pushing the information to your SIEM. In this page we will show you how to connect your RADIUS logs to CrowdStrike Falcon.
Prerequisites
How To Connect Your RADIUS Service To CrowdStrike Falcon LogScale
- Go to your EZRADIUS portal.
- Click on Settings.
- Scroll to the bottom and enable the “Send Audit Logs” to SIEM option.
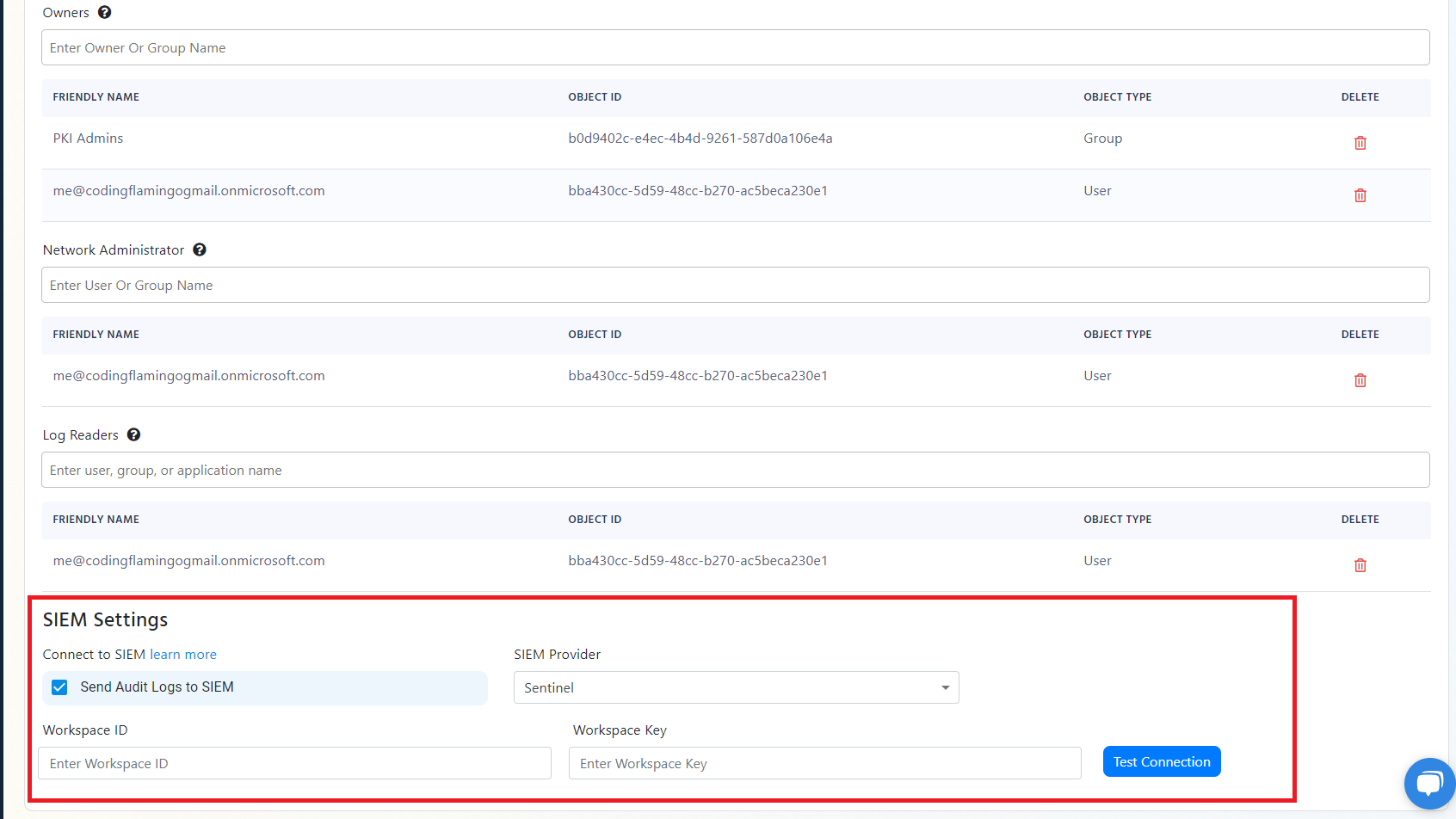
- Select CrowdStrike Falcon LogScale as the SIEM Provider.

- In another tab, go to your CrowdStrike Falcon LogScale instance.
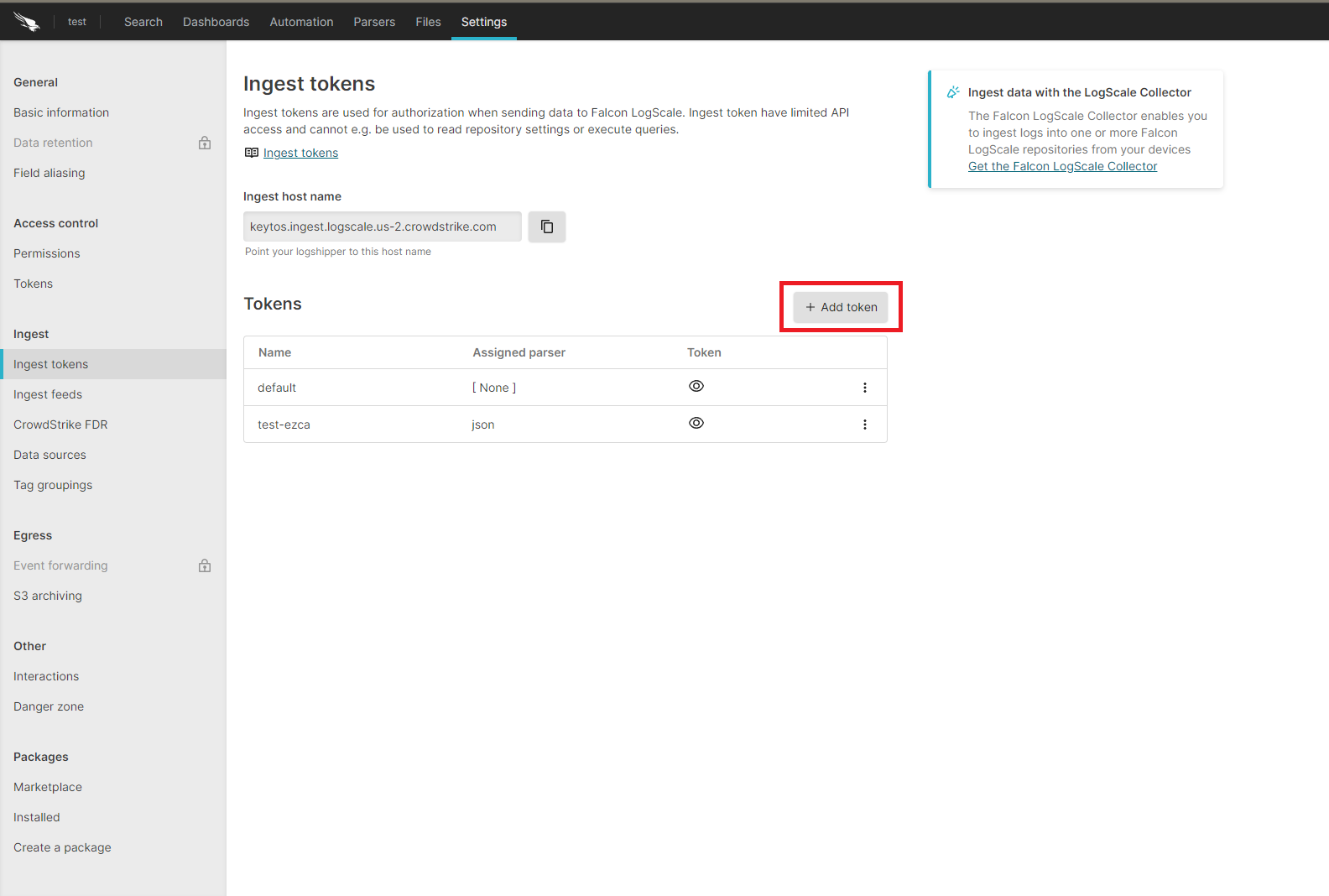
- Click on the Settings tab.
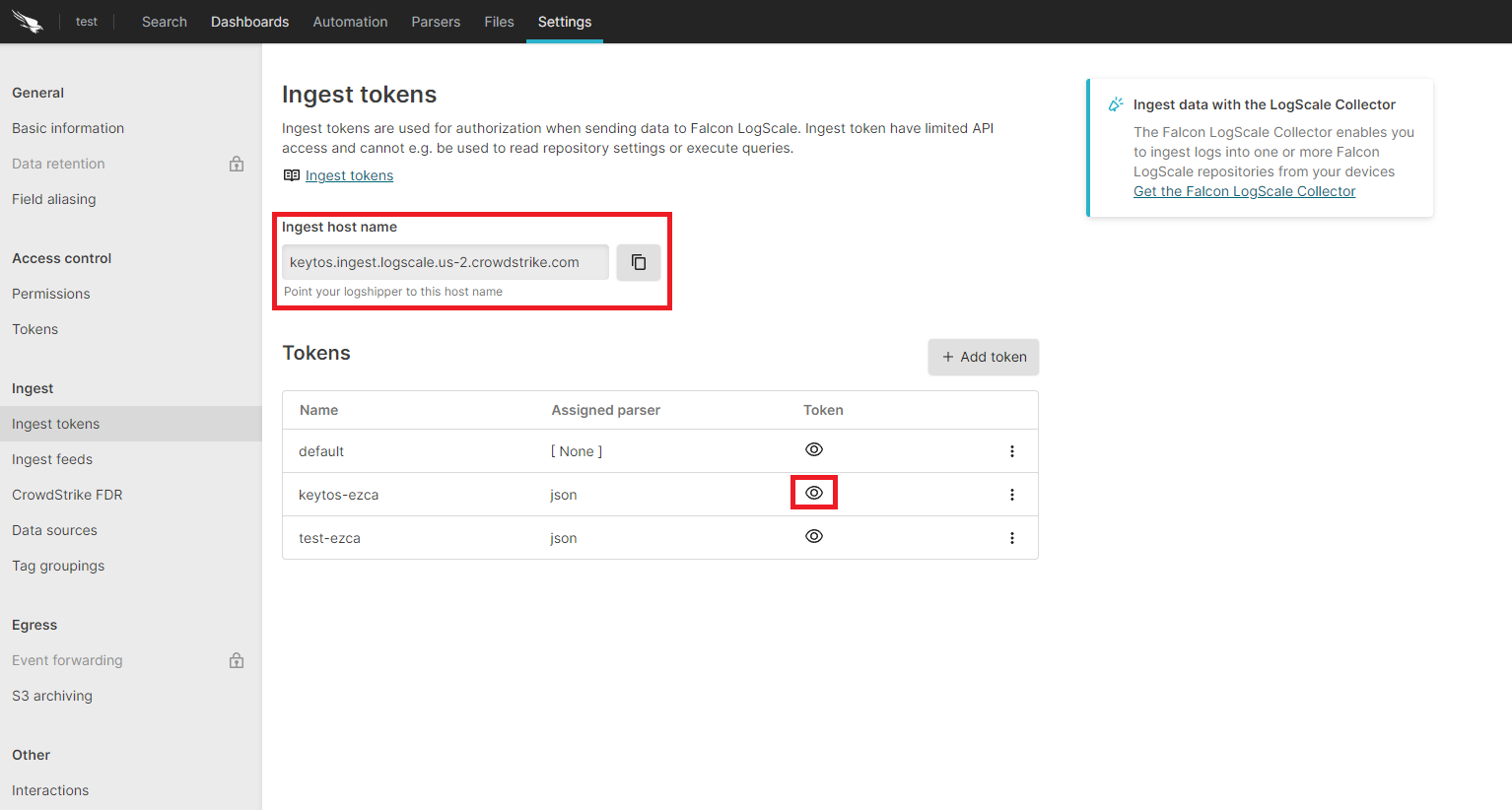
- Select the “Ingest Tokens” menu.
- Click on the “Add Token” button.
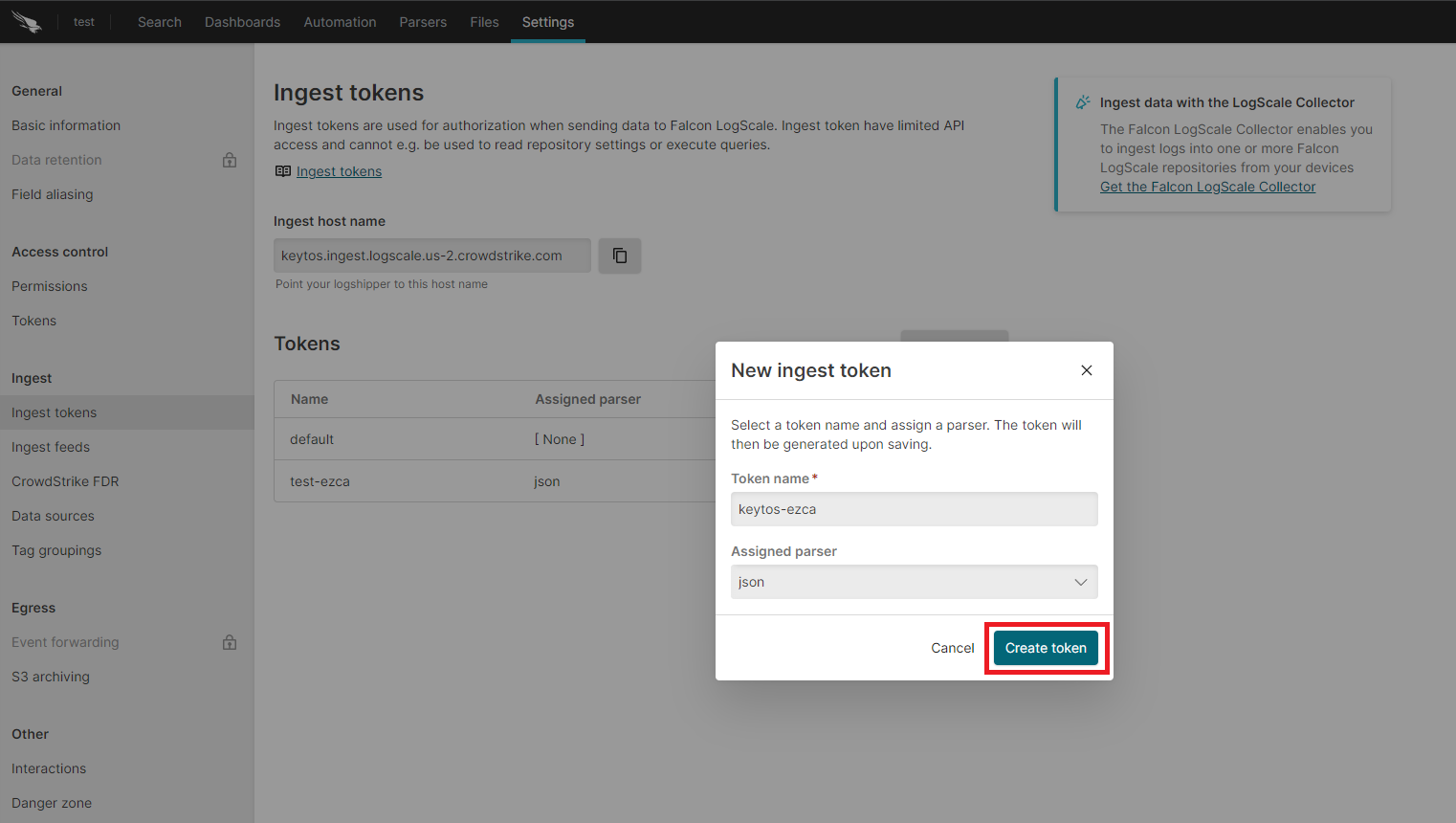
- Enter the token name
- Assign the json parser and click “Create”.
- Copy the token and the ingest host name.
- Go back to the EZRADIUS tab.
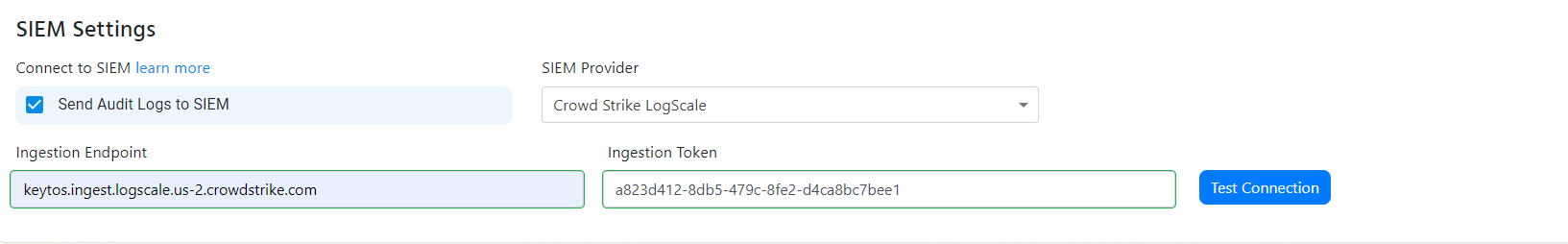
- Paste the ingest host name in the “Ingestion Endpoint” field.
- Paste the token in the “Ingestion Token” field.
- Click the “Test Connection” button, this will create a test log in your SIEM to make sure EZRADIUS can write to the SIEM.
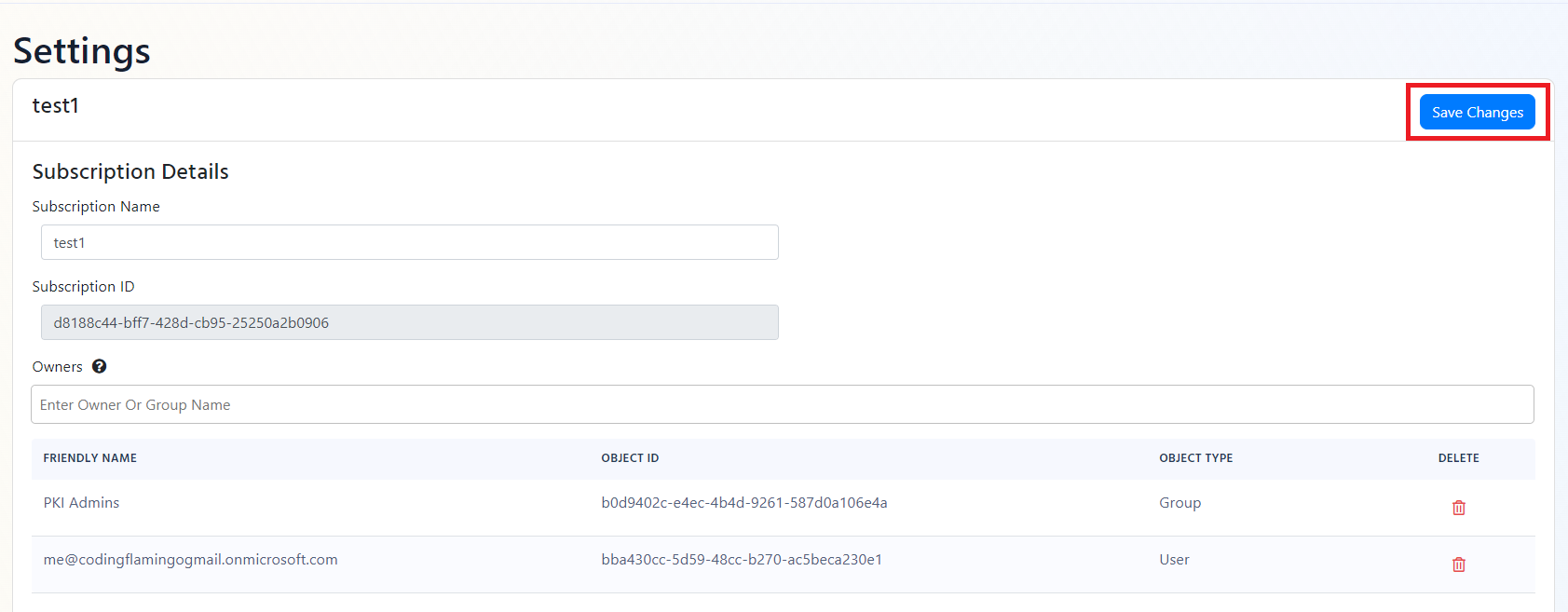
- If the connection test is successful, click “Save changes” at the top of the subscription.
How To Create Alerts in CrowdStrike Falcon LogScale to Monitor Your Cloud RADIUS Activity
Using a SIEM enables you to create alerts for critical operations or abnormal behavior. We recommend setting up alerts for any high criticality event, and closely monitor medium and low events. Below are sample queries for the Administrator events.
LogType = "EZRadiusAdministrator" and Action = "NotAuthorized"