How-To: Export your RADIUS Logs to Azure Log Analytics and Azure Sentinel
This guide applies to both Azure Log Analytics and Azure Sentinel since Sentinel is built on top of Log Analytics. Azure Sentinel is not required if you only want to collect and analyze logs, but it provides additional security features if you choose to use it.
Prerequisites
- The Keytos and EZRADIUS Entra ID applications are registered in your tenant
- You have an active EZRADIUS plan
How to Grant Log Contributor Permissions to the EZRADIUS Application in Azure
To allow EZRADIUS to send logs to your Log Analytics and Azure Sentinel workspace, you need to grant the EZRADIUS application the following roles on the Resource Group containing your Log Analytics workspace:
This can be done manually in the Azure Portal or using the Azure CLI.
How to Grant Permissions using the Azure Portal
It’s easy to enable the required permissions using the Azure Portal:
-
Navigate to the Azure Portal.
-
Open the Log Analytics Workspace you want to connect to EZRADIUS. If you are using Azure Sentinel, open the Log Analytics workspace connected to your Sentinel instance.
-
Click on Resource group to open the Resource Group containing your Log Analytics workspace.
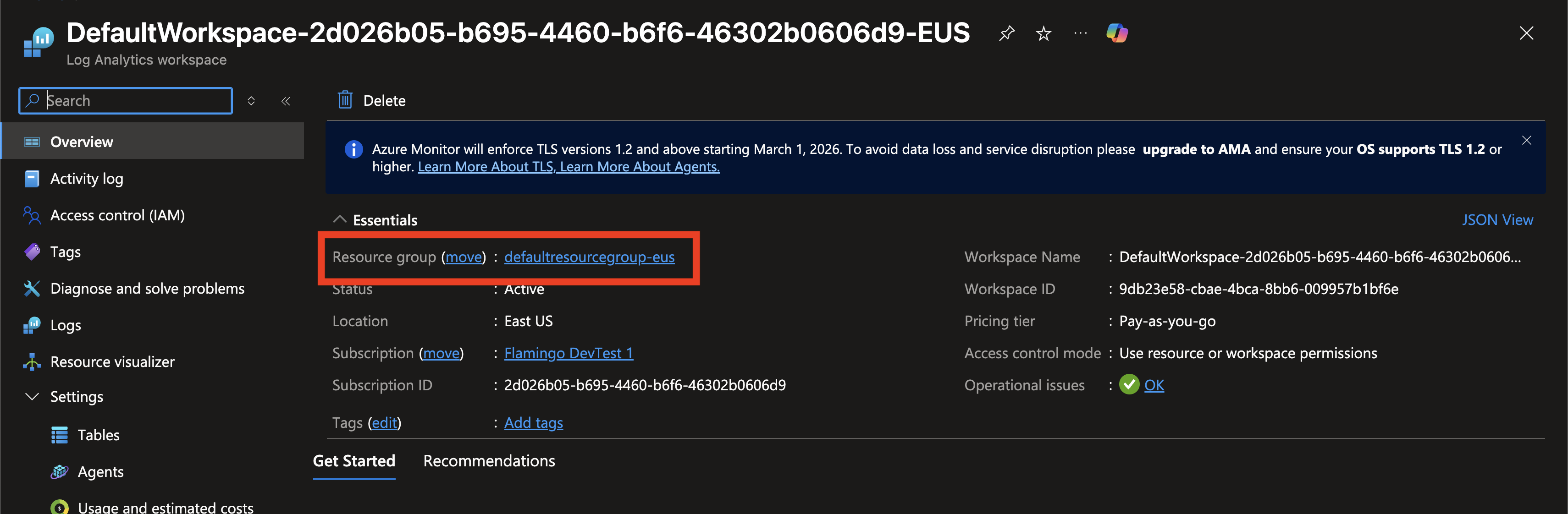
-
Click Access control (IAM) in the left menu.
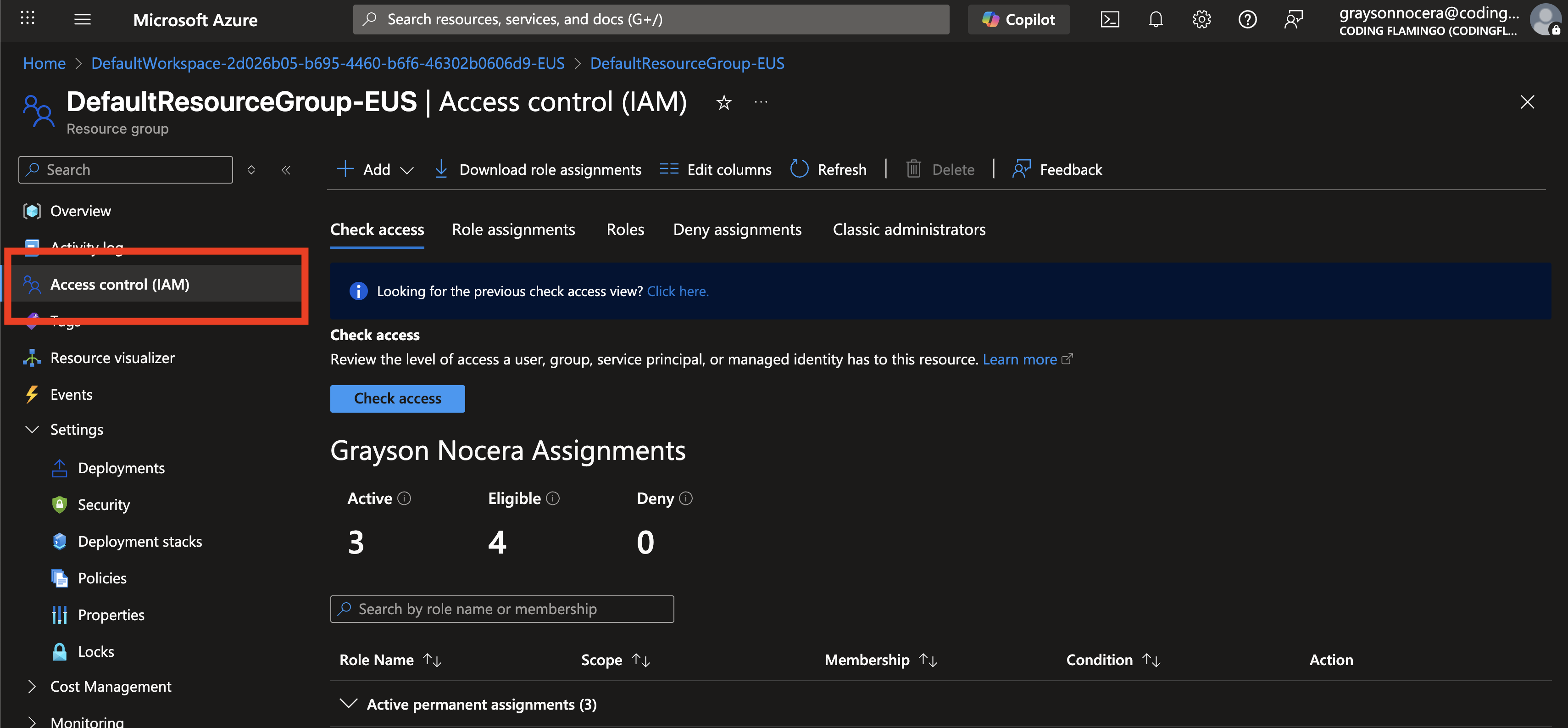
-
Click + Add and Add role assignment.
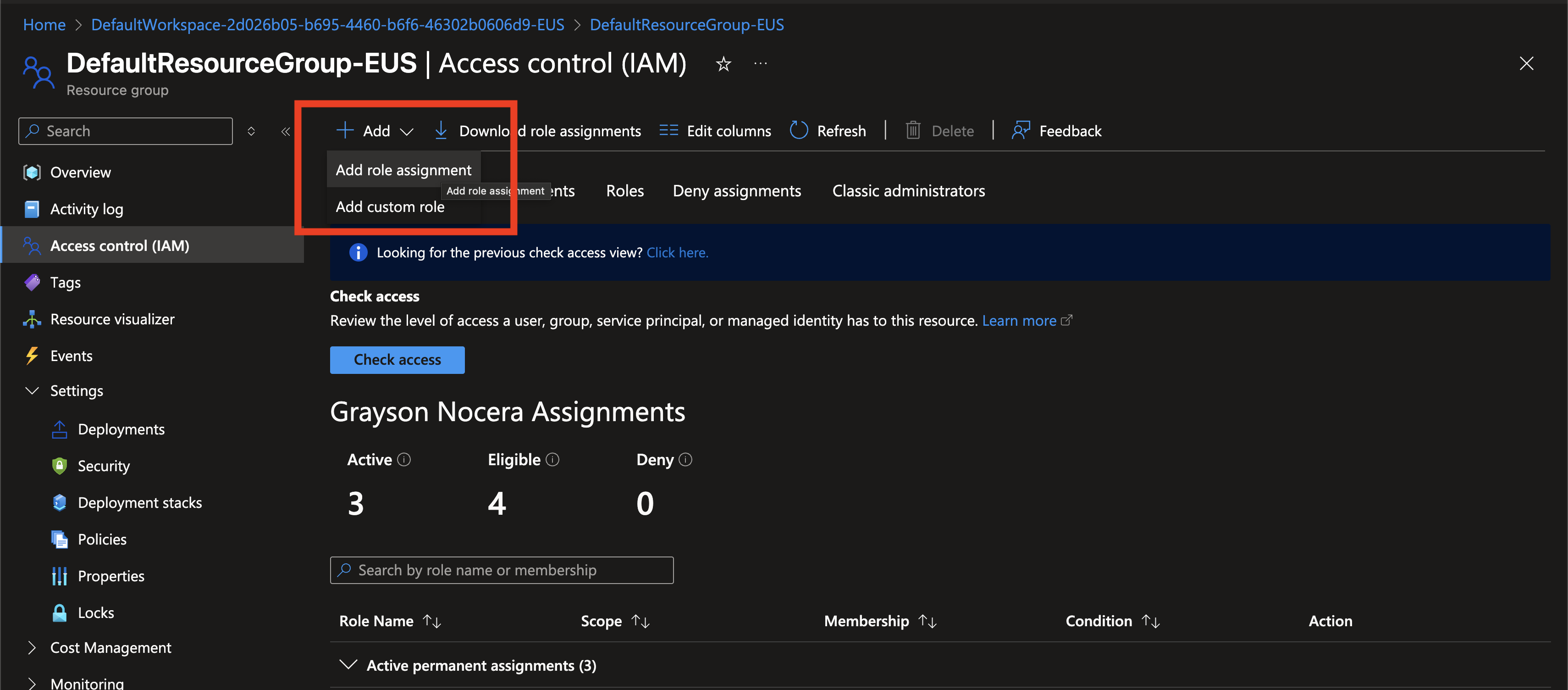
-
Search for Monitoring Contributor in the list of Azure roles. Select the role and click Next.
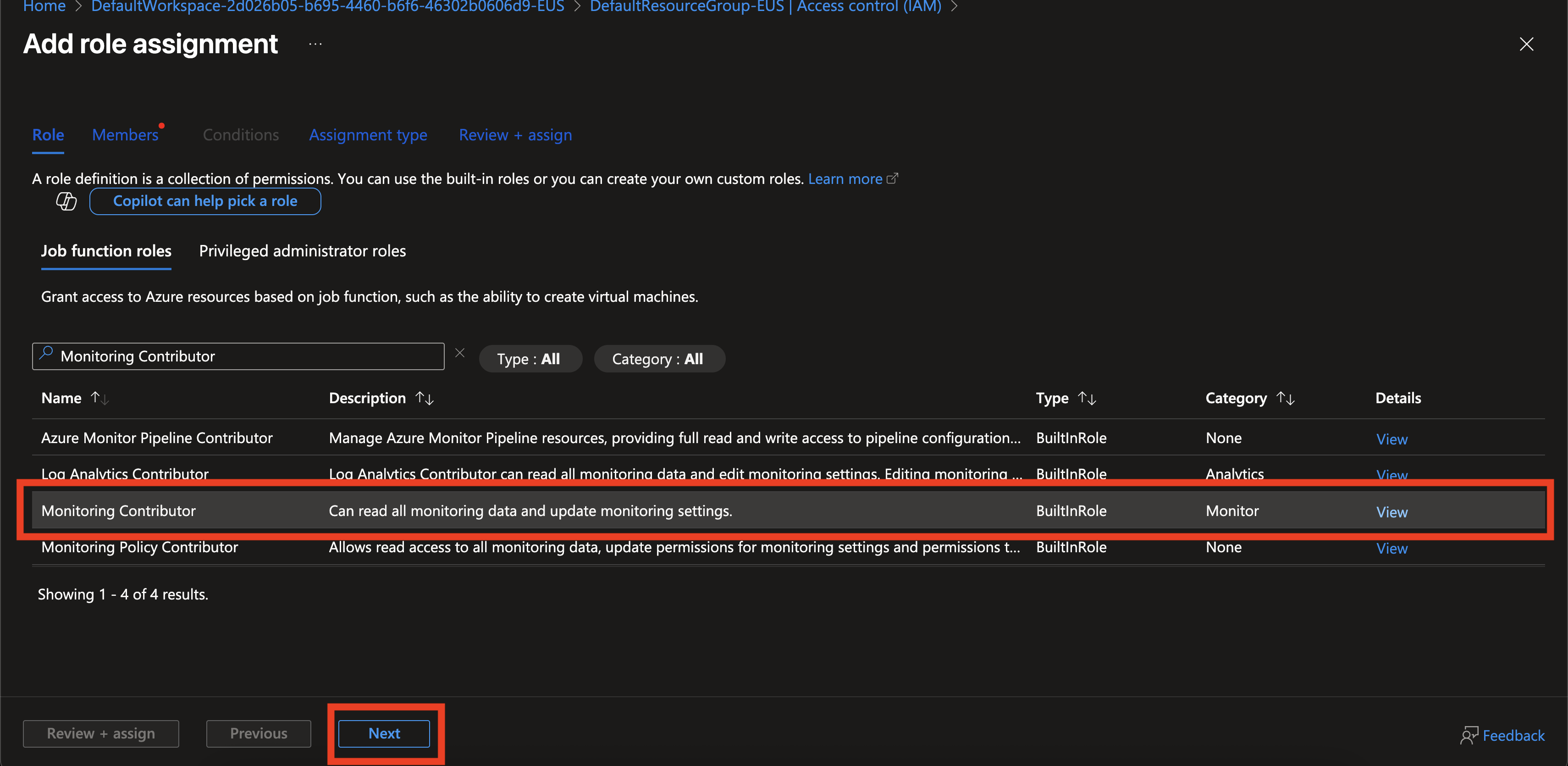
-
Click + Select members and search for EZRADIUS. Select the EZRADIUS application.
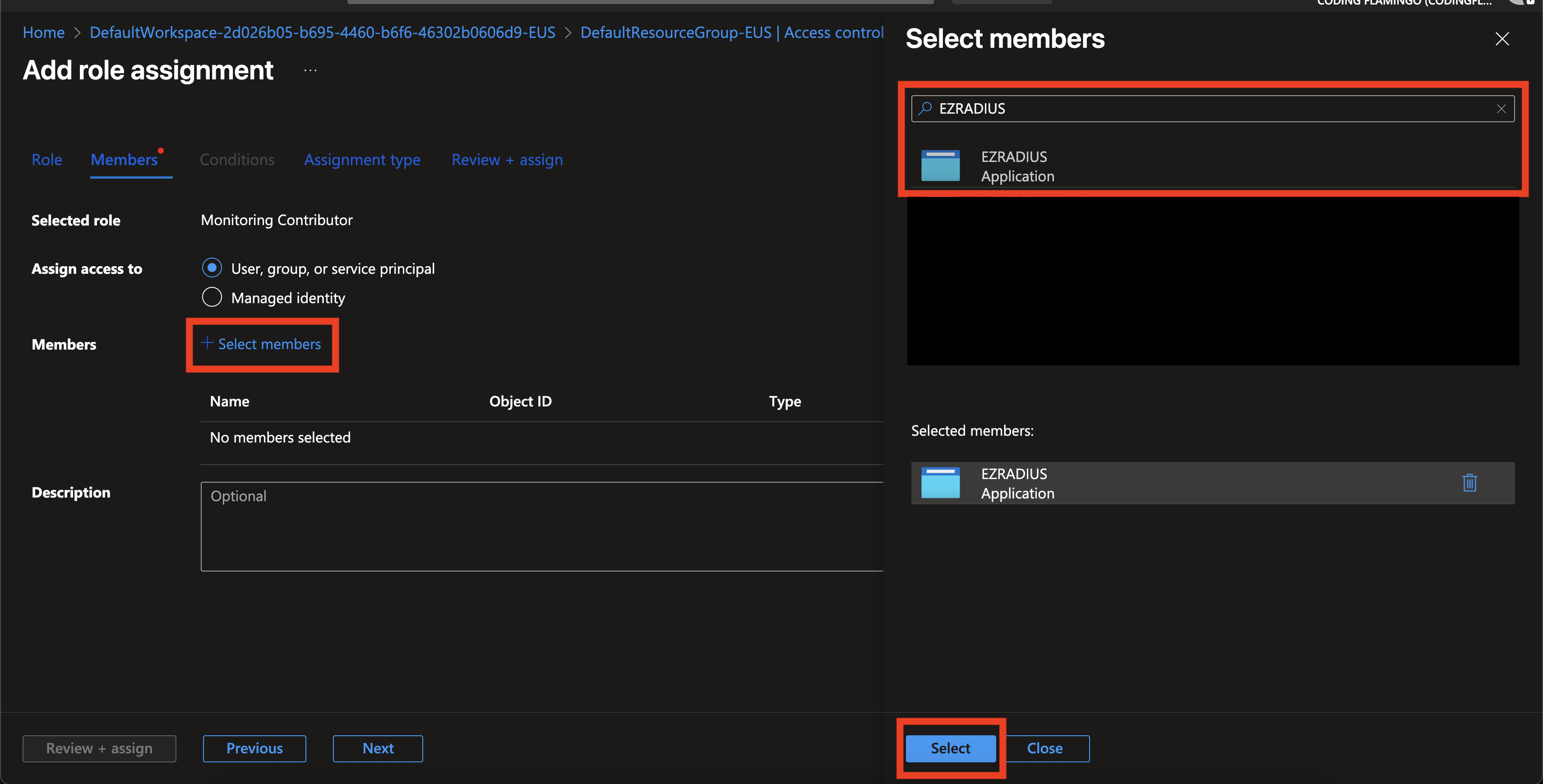
-
Click Review + assign twice to grant the role to the EZRADIUS application.
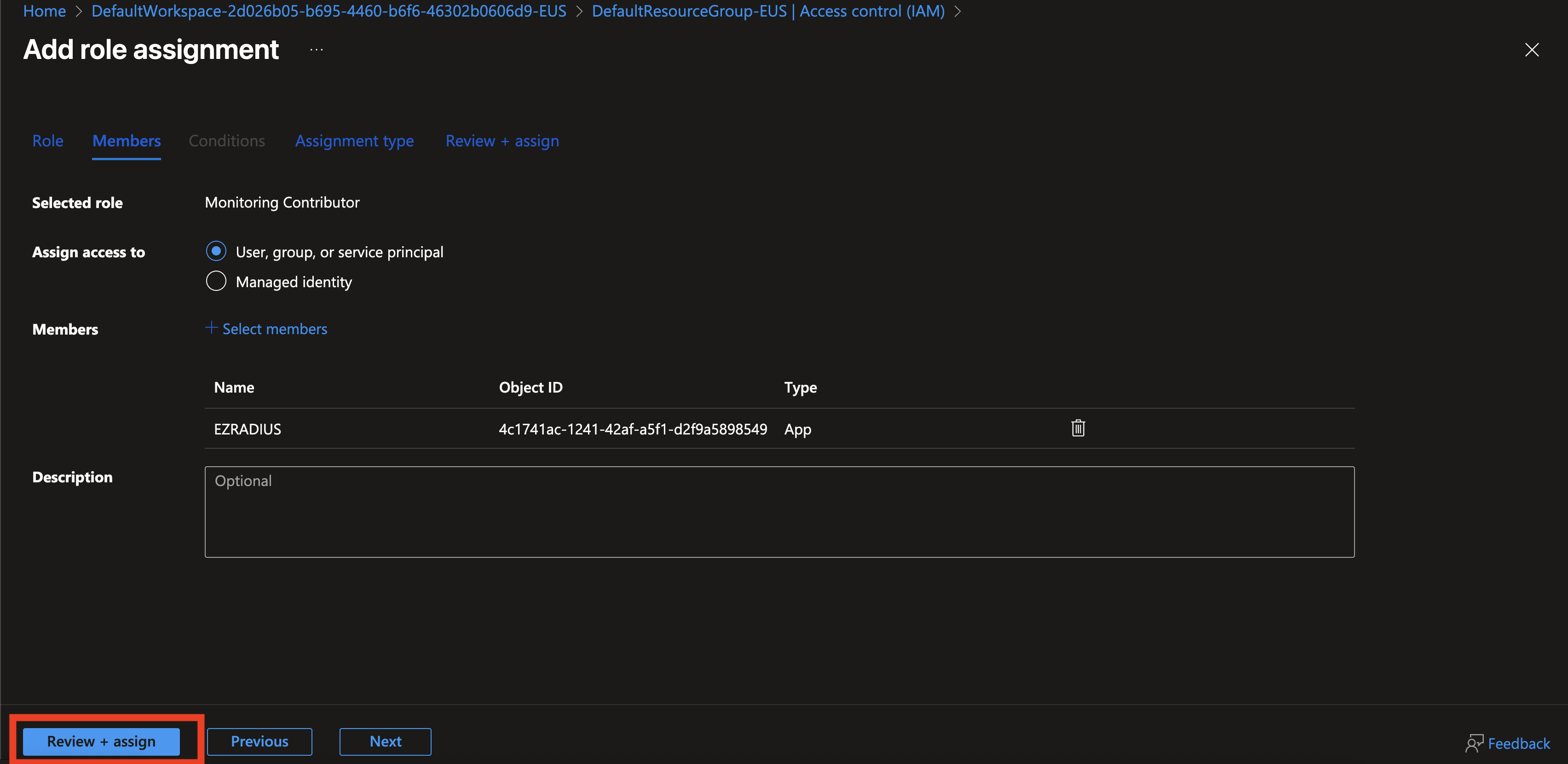
-
Repeat steps 1-8 for the Monitoring Metrics Publisher and Log Analytics Contributor roles.
How to Grant Permissions using the Azure CLI
The Azure CLI can also be used to enable the required permissions. Follow these steps:
-
Open a terminal window on your device or navigate to the Azure Portal and open Azure Cloud Shell.
-
Begin by getting the object ID of the service principal for the EZRADIUS application in your tenant:
$objectId = az ad sp list --filter "appId eq '5c0e7b30-d0aa-456a-befb-df8c75e8467b'" --query "[].{id:id}" --output tsv -
Copy the Resource ID of the Resource Group containing your Log Analytics workspace. This can be found by going to the Resource Group in Azure, selecting Properties, and copying the Resource ID.
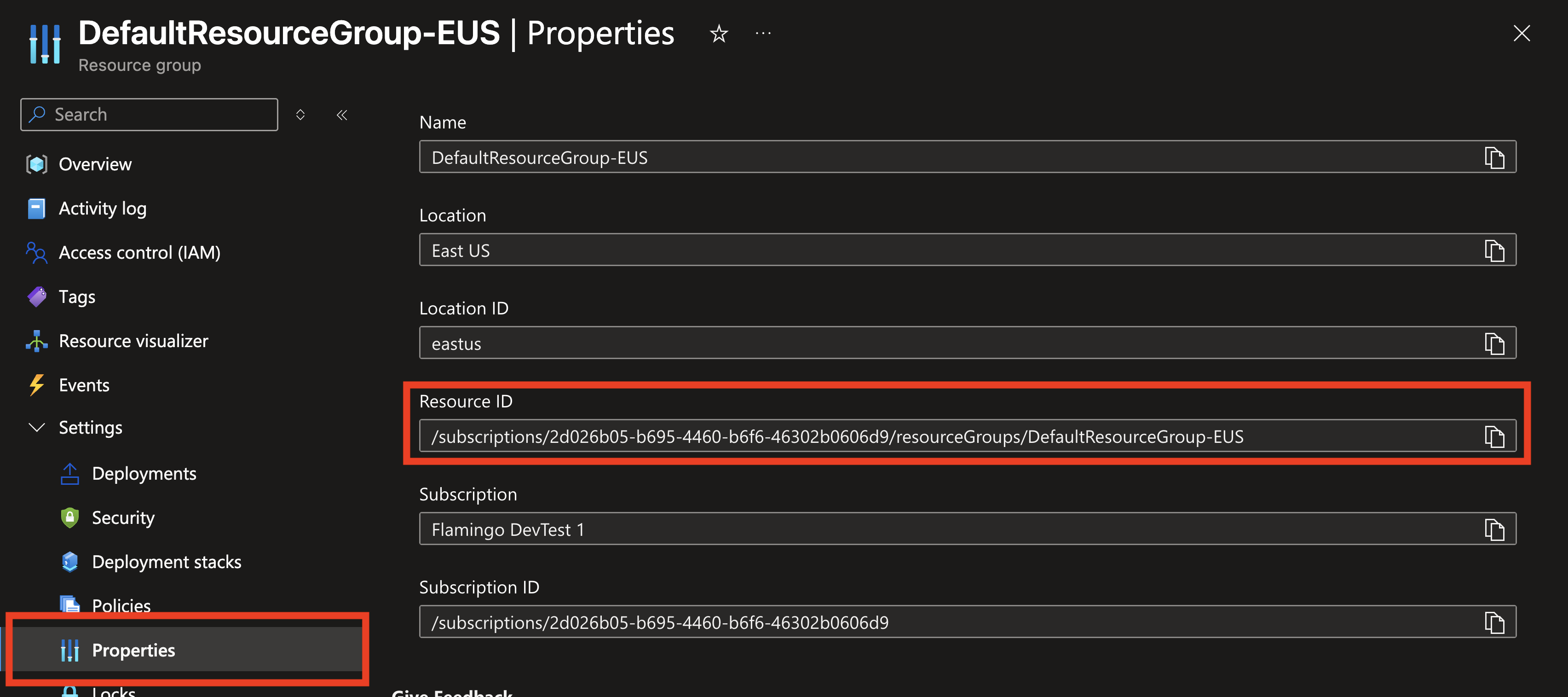
-
Save the Resource ID as a variable for easier use:
$resourceGroupId = "/subscriptions/<YOUR-SUBSCRIPTION-ID>/resourceGroups/<YOUR-RESOURCE-GROUP-NAME>" -
Grant the Monitoring Contributor role to the EZRADIUS application:
az role assignment create --scope "$resourceGroupId" --role "Monitoring Contributor" --assignee $objectId -
Grant the Monitoring Metrics Publisher role to the EZRADIUS application:
az role assignment create --scope "$resourceGroupId" --role "Monitoring Metrics Publisher" --assignee $objectId -
Grant the Log Analytics Contributor role to the EZRADIUS application:
az role assignment create --scope "$resourceGroupId" --role "Log Analytics Contributor" --assignee $objectId
How to Export your RADIUS Logs to Log Analytics and Azure Sentinel
Now that you have granted the necessary permissions to the EZRADIUS application, you can configure EZRADIUS to send your RADIUS logs to your Log Analytics and Azure Sentinel workspace:
How To Enable Log Export in EZRADIUS
-
Navigate to your EZRADIUS portal.
-
Click on Settings.
-
Scroll to the bottom and enable the “Send Audit Logs to SIEM” option.

How to Configure the Azure Sentinel Exporter in EZRADIUS
-
Under SIEM Provider, select Sentinel.
-
In another tab, navigate to the Azure Portal.
-
Select the Log Analytics workspace connected to your Sentinel instance (or any Log Analytics workspace you want to use if you are not using Sentinel).
-
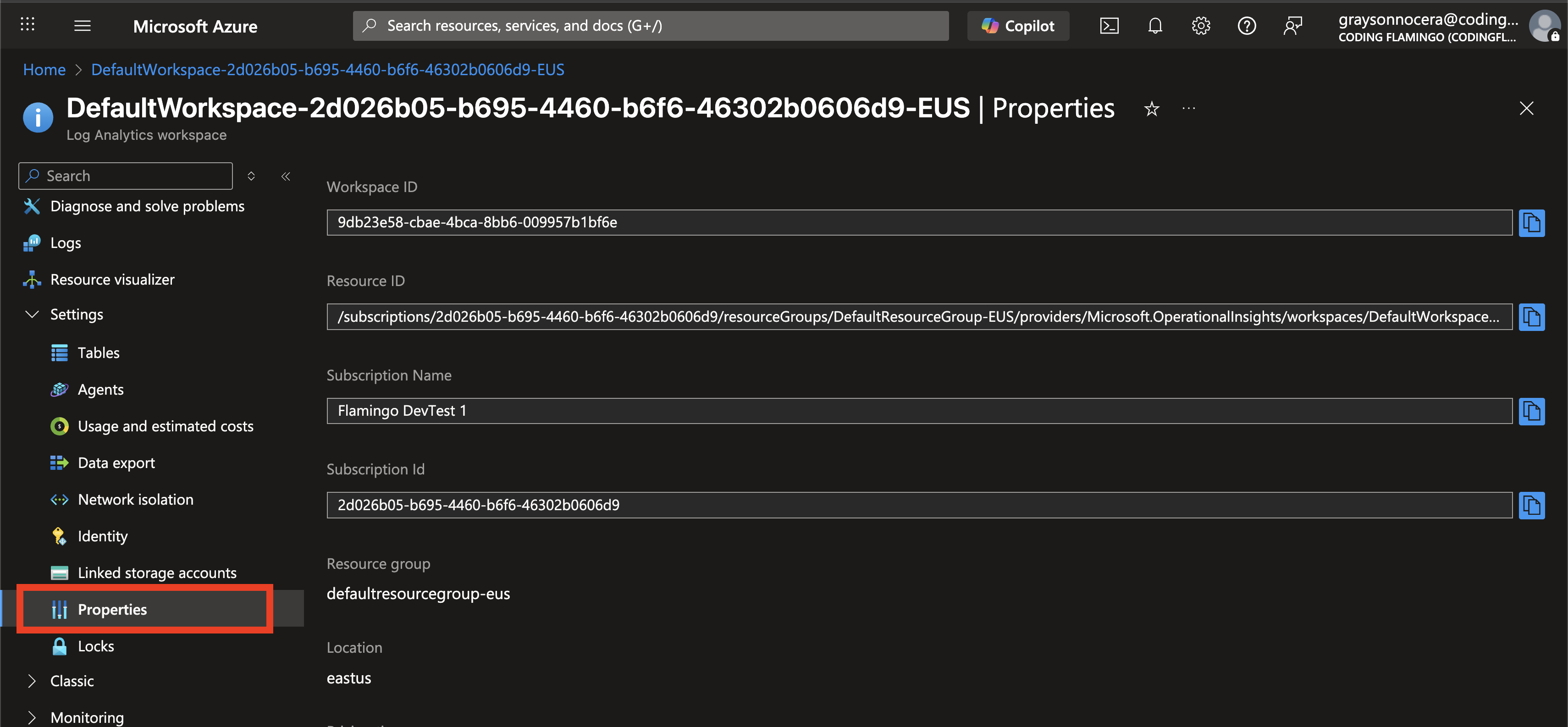
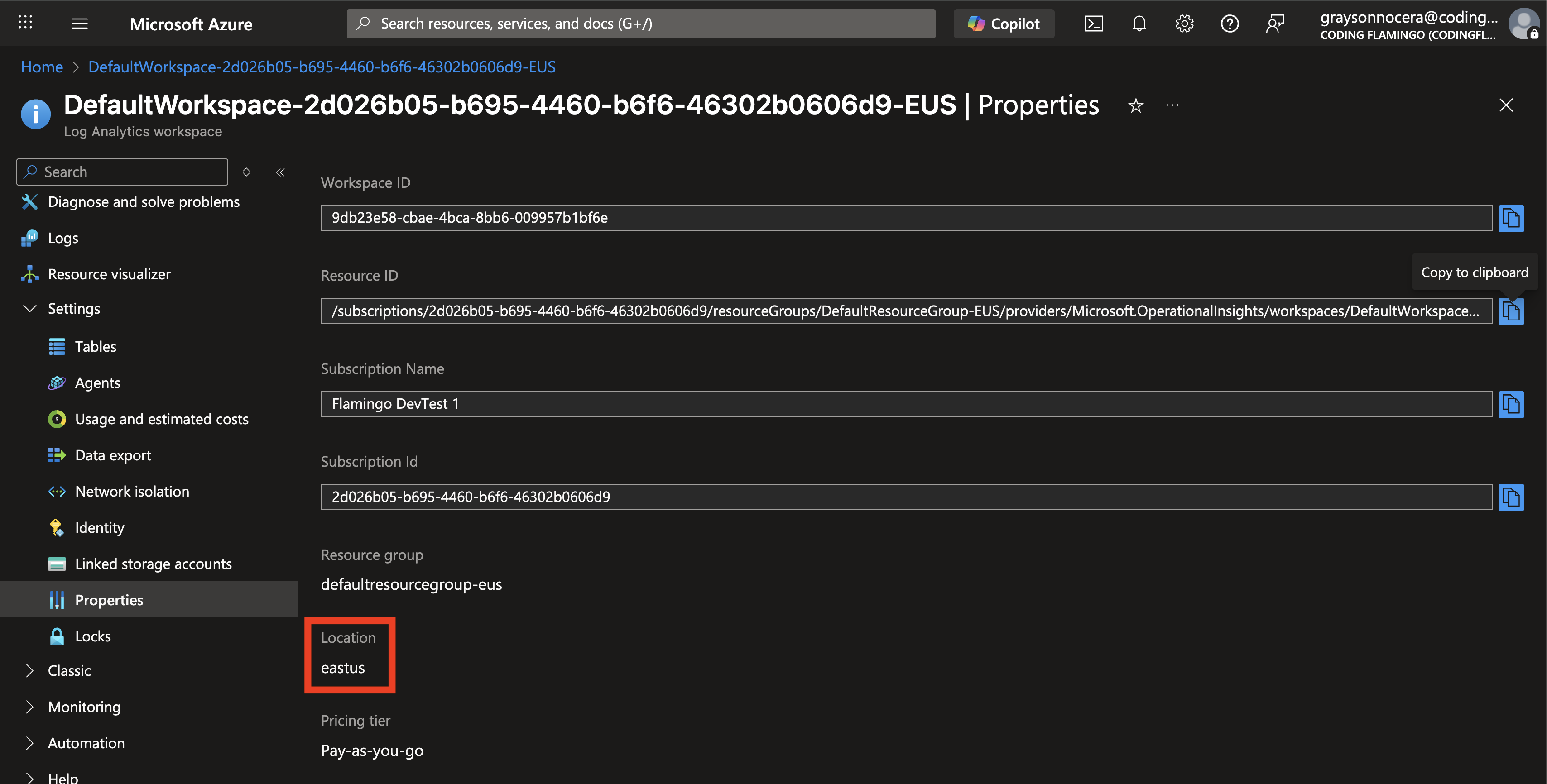
Click on Properties.
-
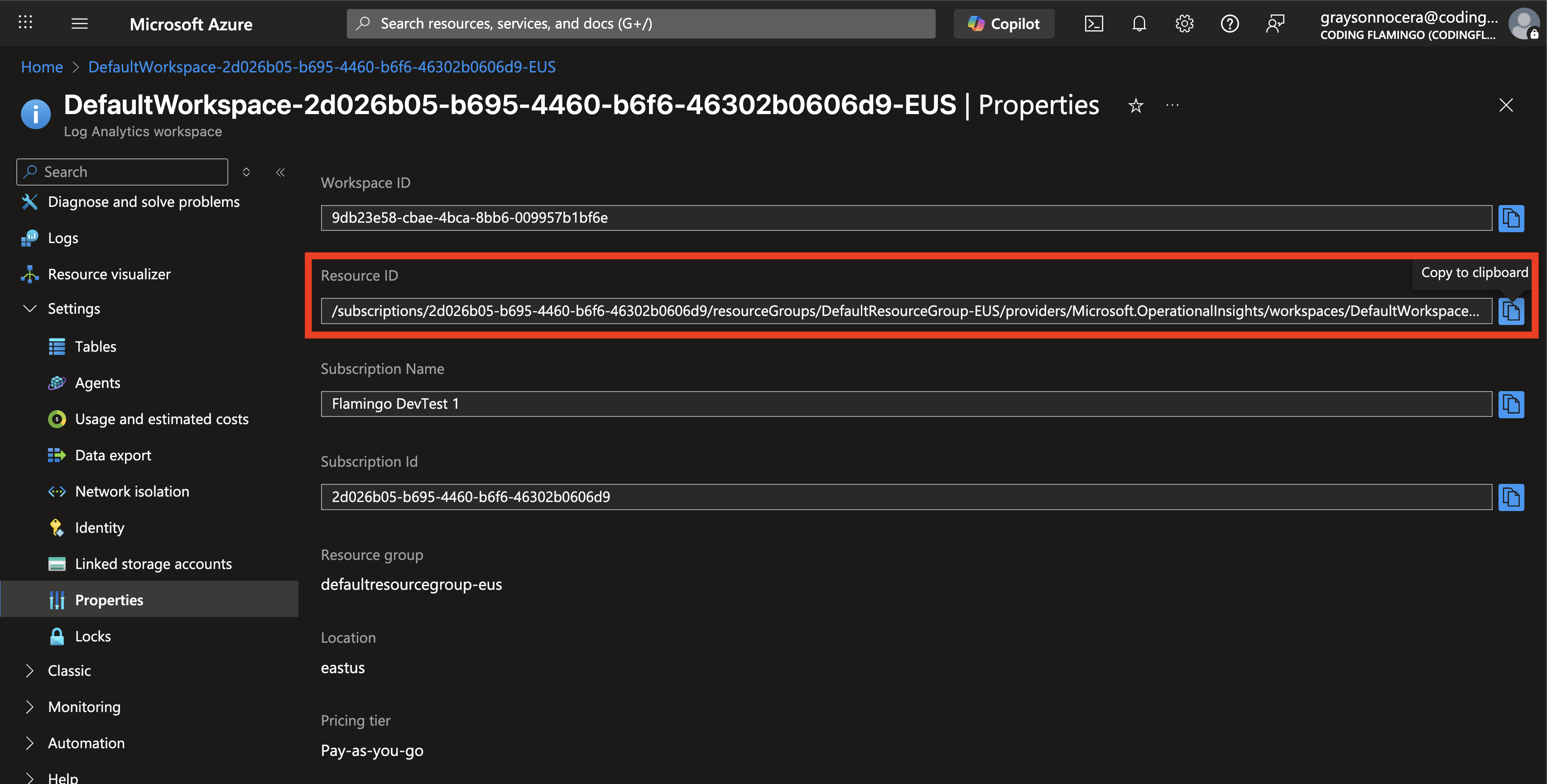
Copy the Resource ID.
-
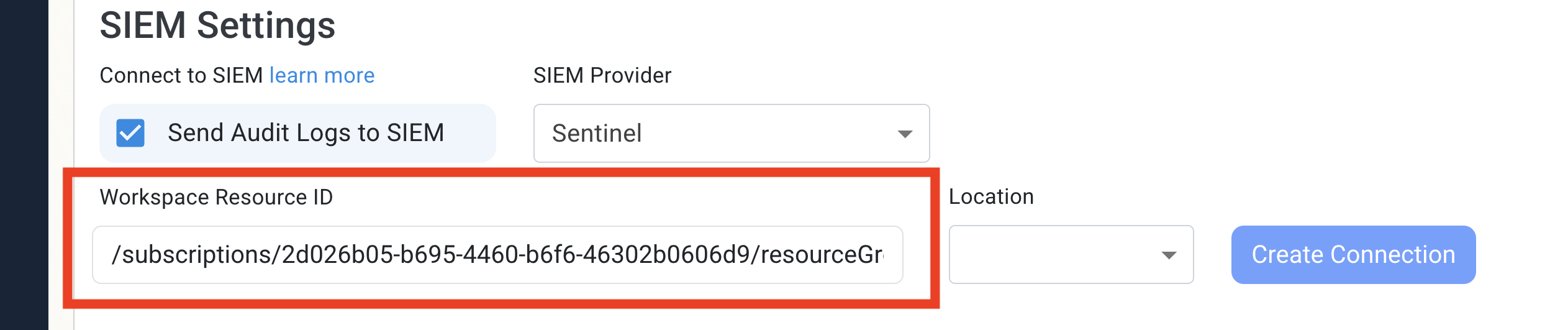
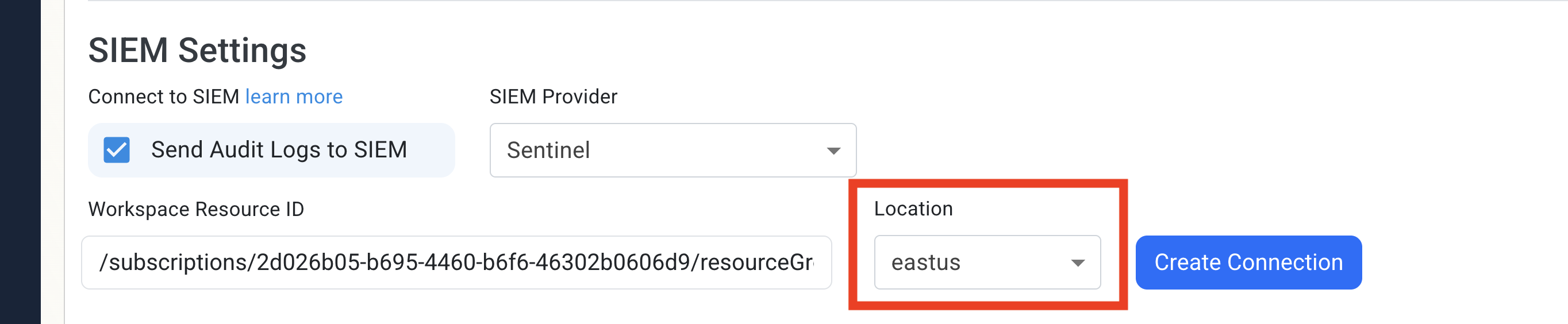
Go back to the EZRADIUS tab and paste the Resource ID into the Workspace Resource ID field.
-
Back in the Azure tab note the Location of the Log Analytics workspace.
-
In EZRADIUS select the same location in the Location dropdown.
-
Click the Create Connection button. This will create the necessary connection in your Resource Group to communicate with Log Analytics, and send a test message to ensure proper connection.
-
Once the test succeeds, make sure to click Save changes to save your SIEM settings.
-
Done! EZRADIUS will now send your security logs to your SIEM.
How to Create Dashboards Using your Cloud RADIUS Logs
Now that your EZRADIUS logs are flowing into EZRADIUS, check out how to create a dashboard for your RADIUS service.
Create RADIUS DashboardsHow To Create Alerts in Azure Sentinel to Monitor Your Cloud RADIUS Activity
We recommend setting up alerts for any high criticality event, and closely monitor medium and low events. Here is an example query to find all “NotAuthorized” actions in your EZRADIUS logs:
KeytosEZRadiusAdministrator_CL
| where Action == "NotAuthorized"