How-To: Enable WiFi Certificate Authentication For Linux in Intune
While Intune does not have a specific profile for Linux devices, we have created some custom profiles that will allow you to issue certificates to Linux devices and enable WiFi Certificate Authentication.
Prerequisites
- Registering the application in your tenant
- Creating Cloud Radius Instance
- Being a Subscription Owner or Network Administrator
- Being an MDM Administrator.
- Have a certificate in the Device, if you do not have one, follow the guide on how to create Intune SCEP profiles for Linux.
How to Linux Enable WiFi Certificate Authentication in Intune
- Go to your Intune portal: https://aka.ms/Intune
- Select: Devices -> Linux -> Scripts.
- Click the “Add” button.
- Enter a name for the profile and click “Next”.
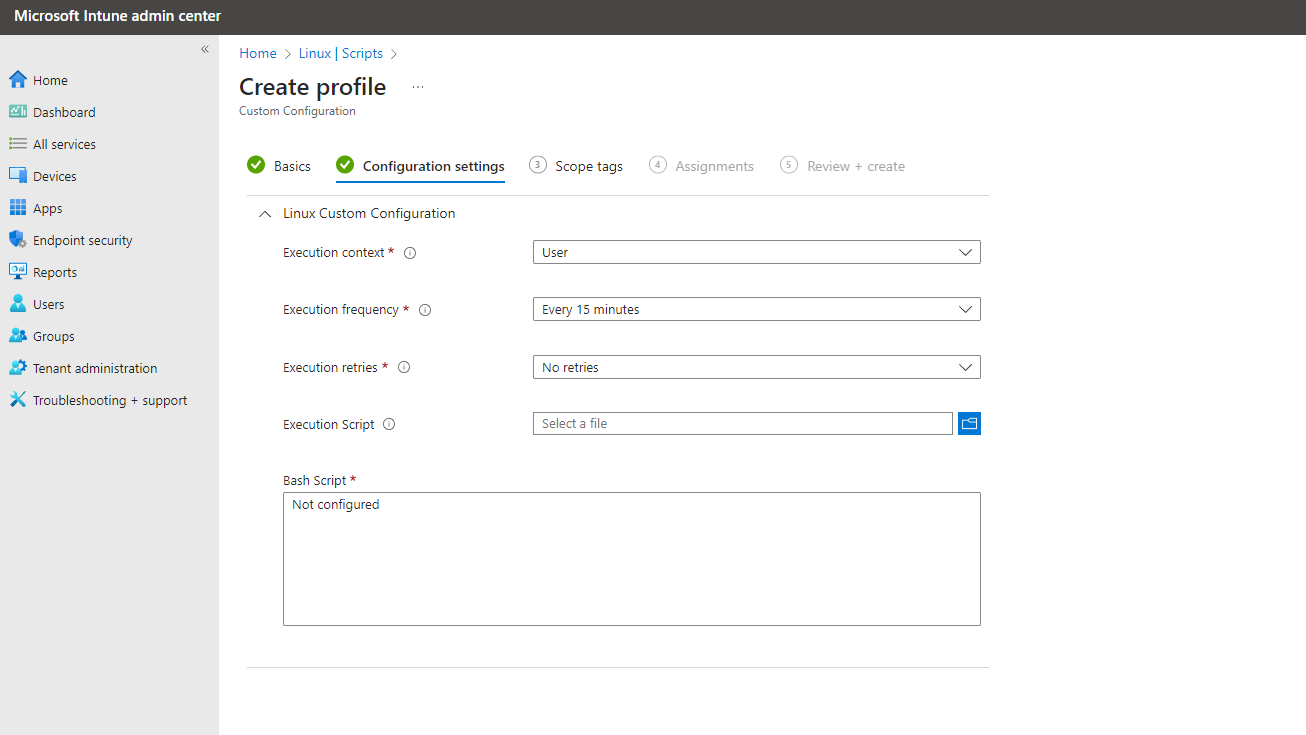
- Set your execution values.
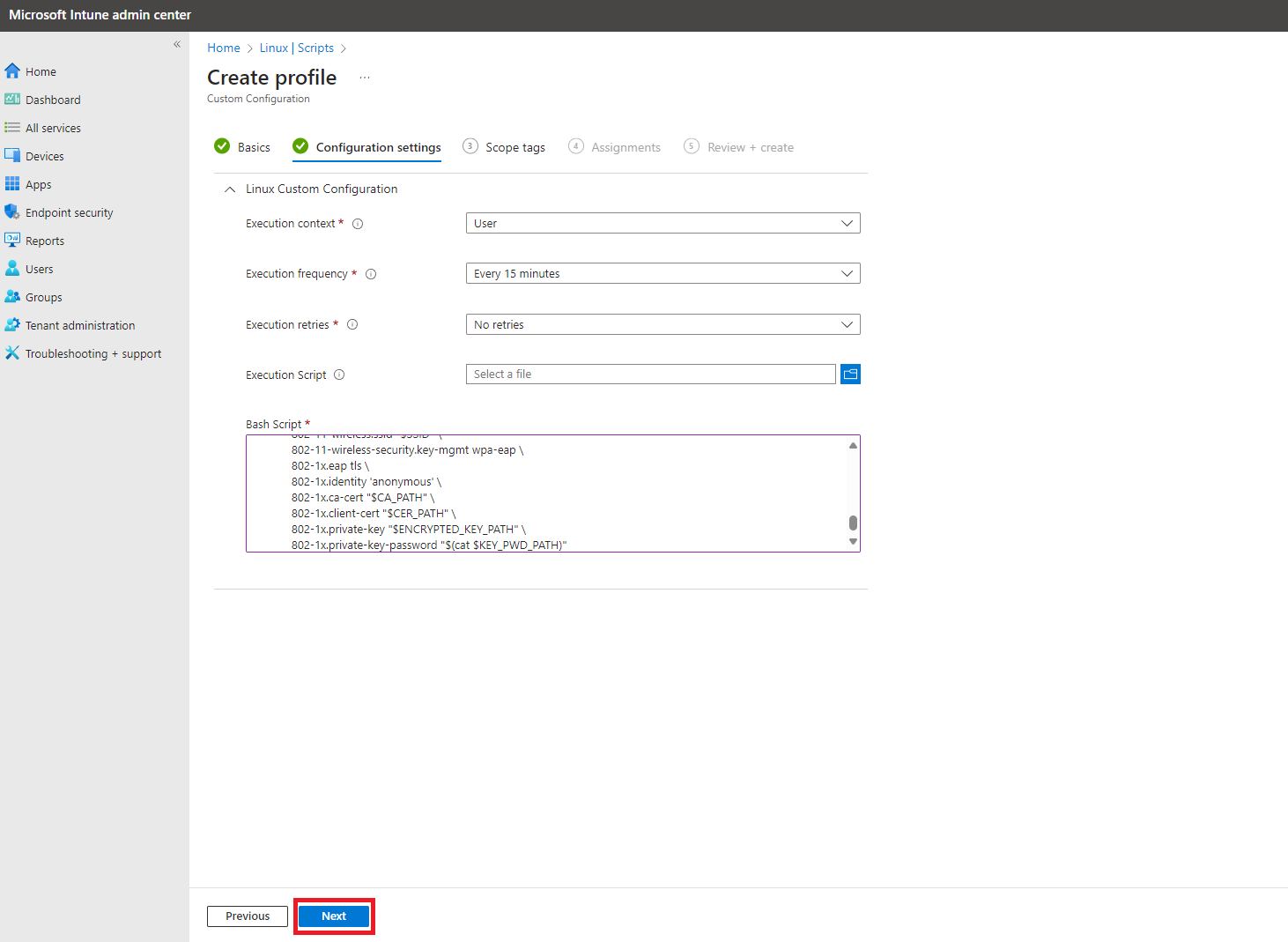
- Copy the following Script (Modifying the values for your CA and SSID):
# User-set values # CA_PATH= # Set to the absolute path of the server certificate CA EZCA_SERVER_CA_STATIC_SCEP_URL= # Set to the static scep URL of the server certificate CA SSID=test-wifi # Set to the SSID of the network # NOTE: if the server certificate is set to be auto-generated, leave the CA_PATH empty and # the script will install the autogenerated CA. If you are using a server certificate # generated from EZCA, the script will also install it automatically if you put down your # EZCA server certificate CA static scep URL ## ---------- ## ---------- ## ---------- ## ---------- ## ---------- ## # Check all required executables exist req_execs=("base64" "cat" "curl" "cut" "grep" "head" "mkdir" "nmcli" "sed") for exe in "${req_execs[@]}"; do if [ ! $(command -v "$exe") ]; then echo "Required executable $exe not found" exit 1 fi done SSID=${SSID:-'DEFAULT_SSID'} CONNECTION_NAME=${CONNECTION_NAME:-'keytos-ezradius-eap-tls'} SCEP_CER_DIR=${SCEP_CER_DIR:-"$HOME/.local/share/keytos/scep_certs"} KEY_PWD_PATH=$SCEP_CER_DIR/key.pwd ENCRYPTED_KEY_PATH=$SCEP_CER_DIR/key.encrypted.pem CER_PATH=$SCEP_CER_DIR/certificate.pem WIFI_NIC=$(nmcli -t -f DEVICE,TYPE device | grep wifi$ | head -n 1 | cut -d: -f1) if [ -z "$WIFI_NIC" ]; then exit 1 fi nmcli -f GENERAL.STATE con show "$CONNECTION_NAME" > /dev/null if [ $? -eq 0 ]; then exit 0 fi # Get CA for the auto-generated certificate, if server certificate is custom it must # be manually installed and passed above if [ ! -f $CA_PATH ]; then INSTALL_DIR=${INSTALL_DIR:-"$HOME/.local/share/keytos/ezradius"} mkdir -p $INSTALL_DIR CA_PATH=$INSTALL_DIR/server_ca_certificate.pem EZCA_SERVER_CA_STATIC_SCEP_URL=${EZCA_SERVER_CA_STATIC_SCEP_URL:-'https://portal.ezca.io/api/SCEP/Static/d47b647b-ed31-46ef-829c-57e53b4b7cdd/6003b3dd-47e4-4111-b6f6-188dfb5ec4af/eastus?operation=GetCACert'} curl ${EZCA_SERVER_CA_STATIC_SCEP_URL}?operation=GetCACert \ | base64 \ | sed '1i -----BEGIN CERTIFICATE-----' \ | sed '$a -----END CERTIFICATE-----' \ > $CA_PATH fi # Check files exist if [ ! -f $CA_PATH ] || [ ! -f $CER_PATH ] || [ ! -f $ENCRYPTED_KEY_PATH ] || [ ! -f $KEY_PWD_PATH ]; then exit 1 fi nmcli c add type wifi ifname "$WIFI_NIC" con-name "$CONNECTION_NAME" \ 802-11-wireless.ssid "$SSID" \ 802-11-wireless-security.key-mgmt wpa-eap \ 802-1x.eap tls \ 802-1x.identity 'anonymous' \ 802-1x.ca-cert "$CA_PATH" \ 802-1x.client-cert "$CER_PATH" \ 802-1x.private-key "$ENCRYPTED_KEY_PATH" \ 802-1x.private-key-password "$(cat $KEY_PWD_PATH)" - Click “Next”.
- Select your Scope, and click “Next”.
- Select your Assignments, and click “Next”.
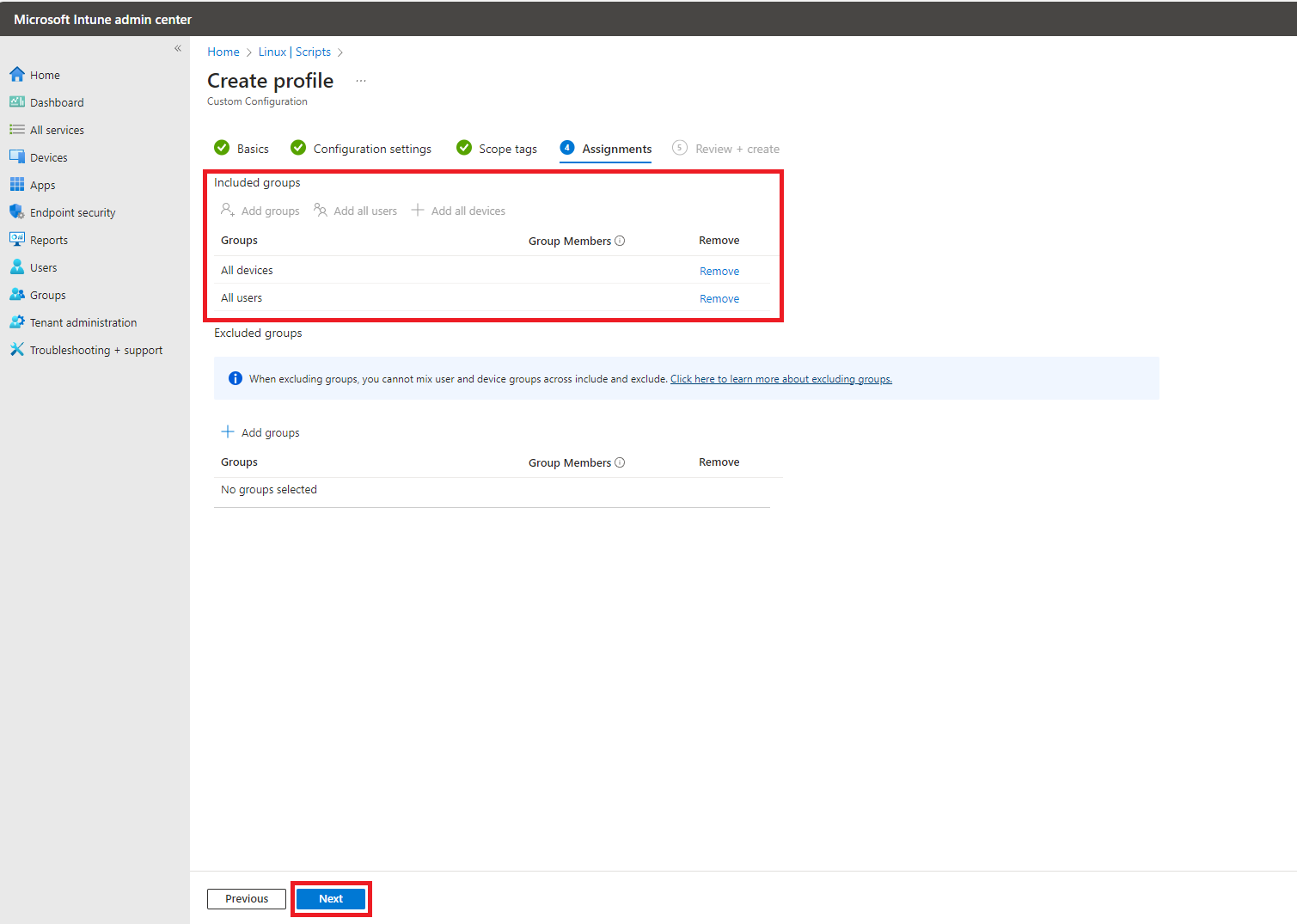
- Review your settings and click “Create”.
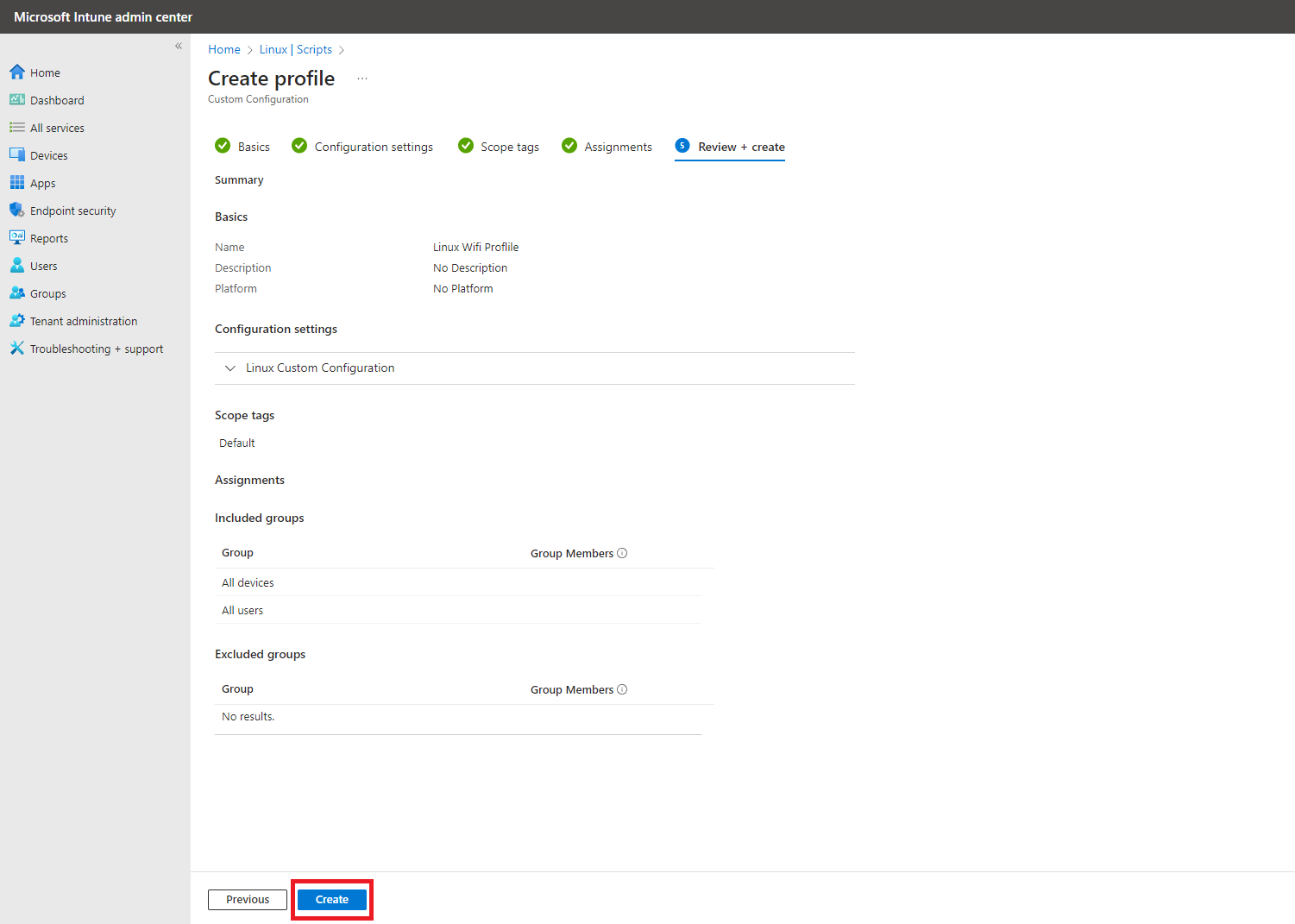
- Your Linux device will now be able to connect to the WiFi network using the certificate you provided.