How-To: Troubleshoot Azure Key Vault Certificate Issues
Learn how to troubleshoot common problems when issuing and managing certificates in Azure Key Vault, such as pending CSRs or merging certificates.
EZCA can automate the process of rotating certificates stored in Azure Key Vault. This ensures that your applications always have access to valid certificates without manual intervention. In order to enable this feature, you need to grant EZCA access to your Azure Key Vault(s) via Azure RBAC and/or Key Vault Access Policies.
Azure Key Vault automatic certificate rotation requires EZCA to have access to your Key Vaults via two sets of permissions:
Reader role to verify the user requesting the certificate has access to the Key Vault.Get, Update, and Create, or an RBAC Key Vault Certificates Officer role to manage the certificates in the Key Vault.This guide will walk you through the steps required to give EZCA access to your Azure Key Vaults to enable automated certificate rotation.
The first step is to give EZCA the Reader role on the Key Vault. This will allow EZCA to read the list of authorized users for the Key Vault to verify that the user requesting the certificate has access to the Key Vault.
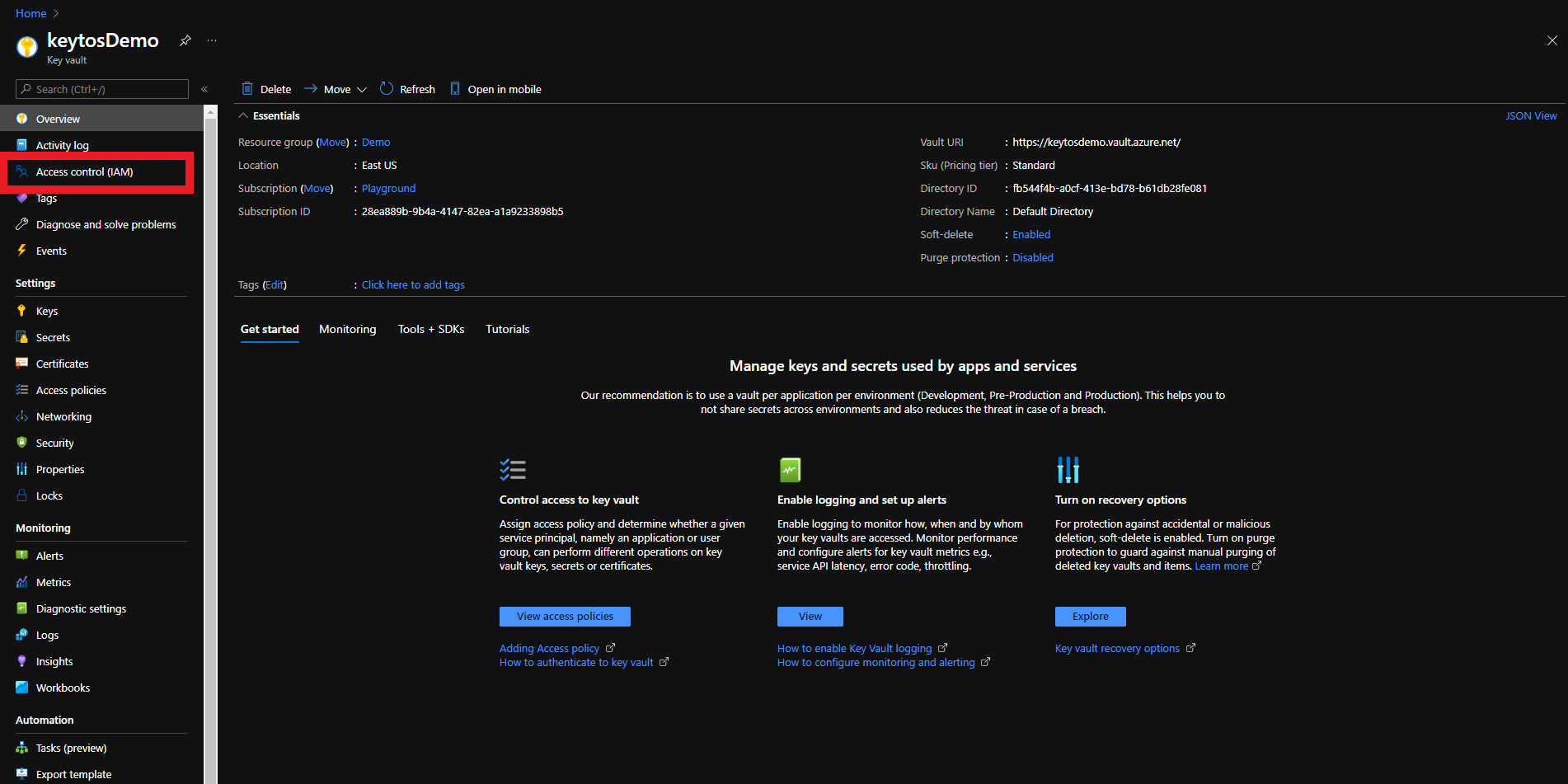
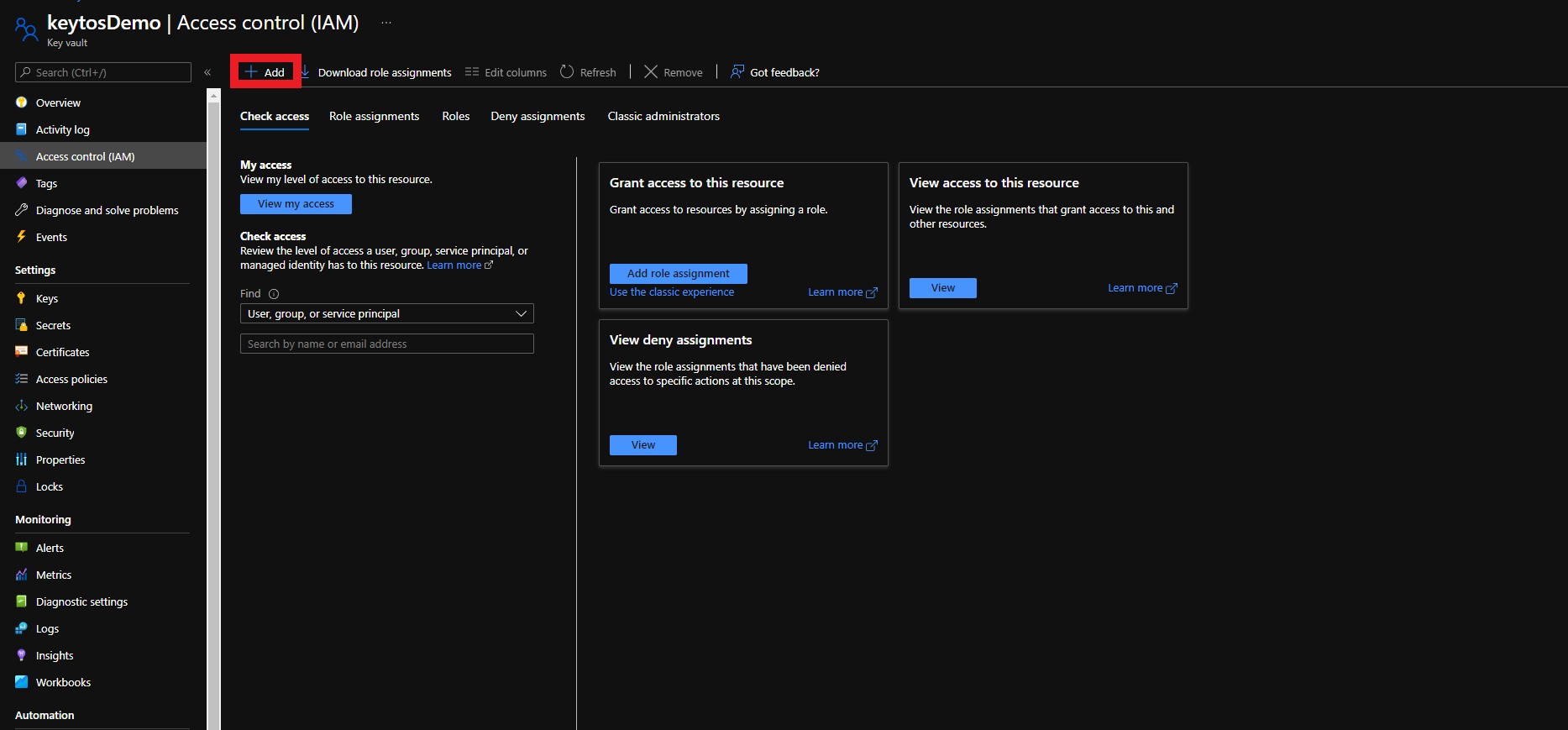
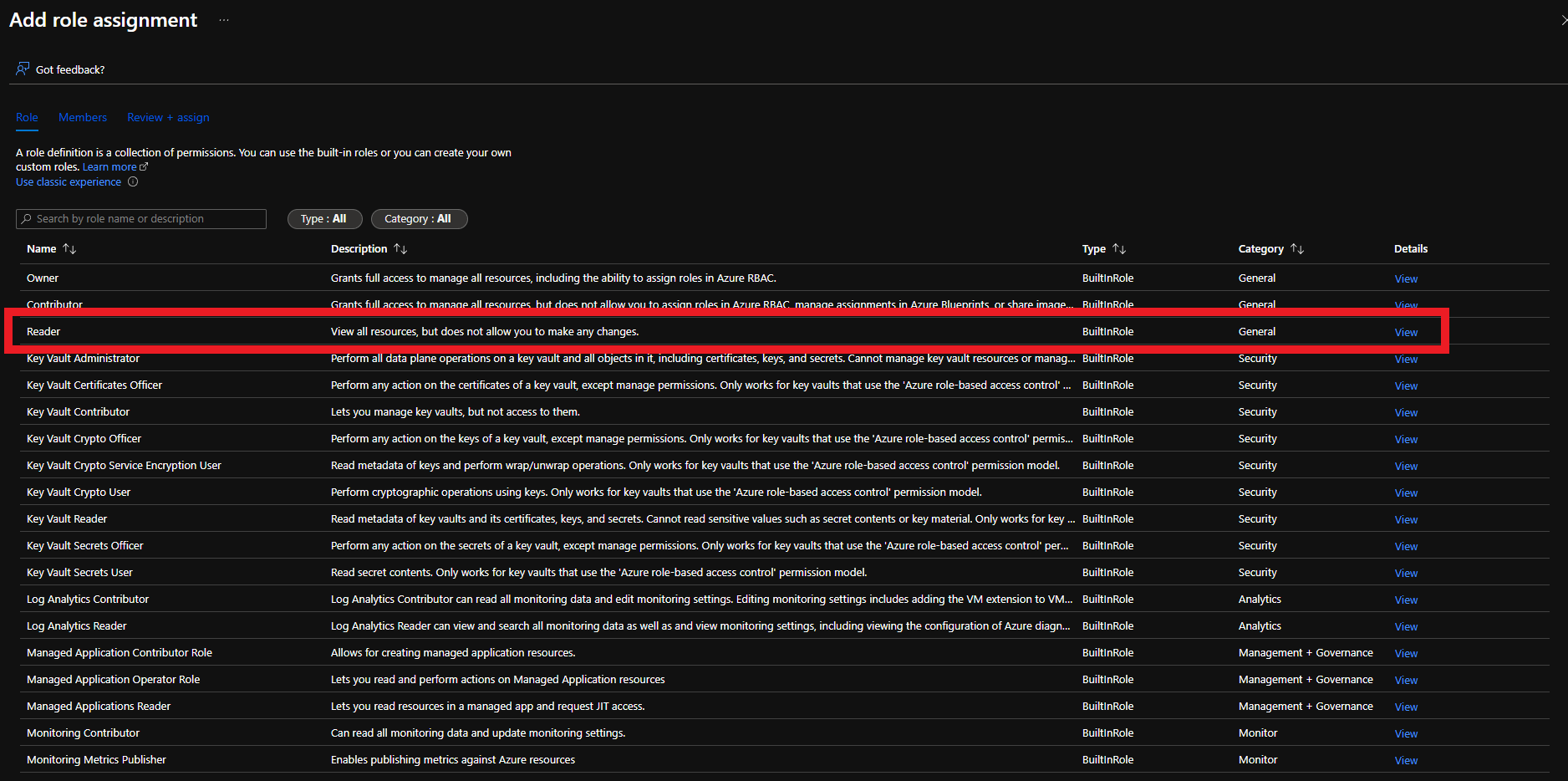
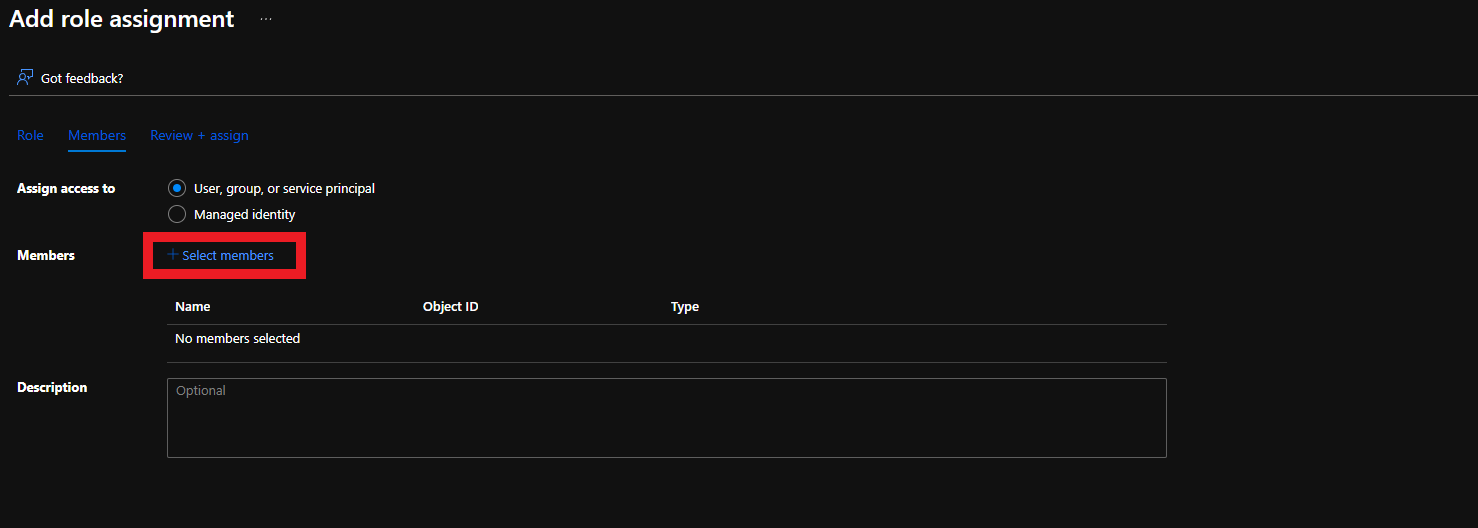
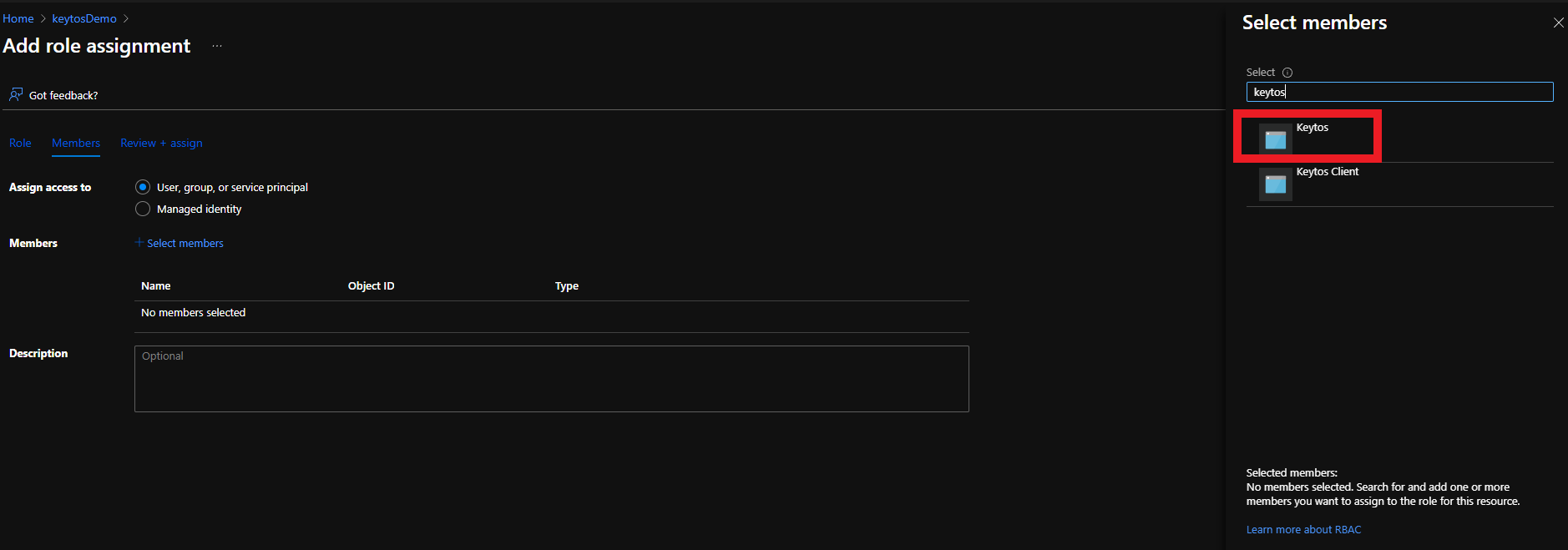
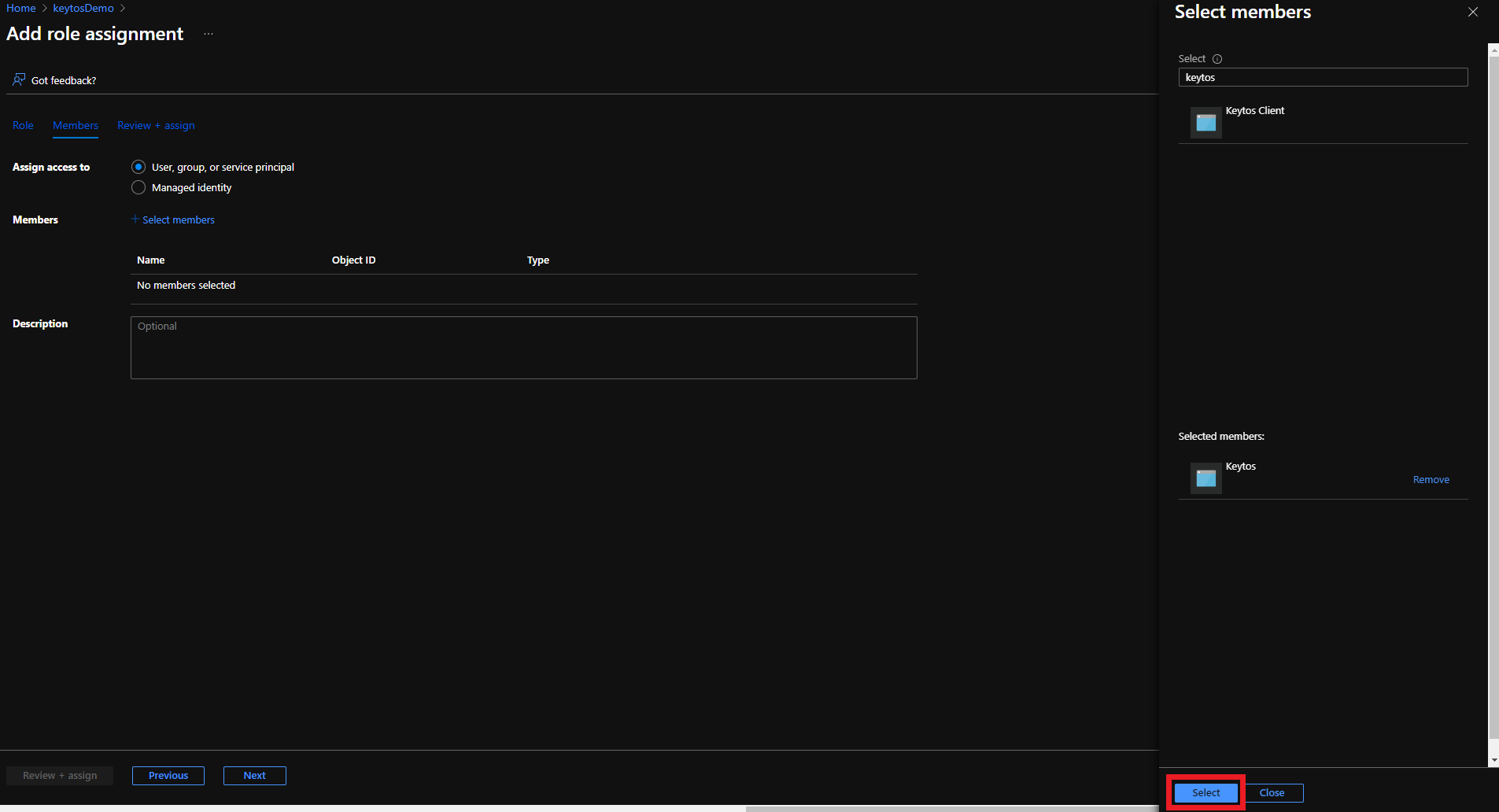
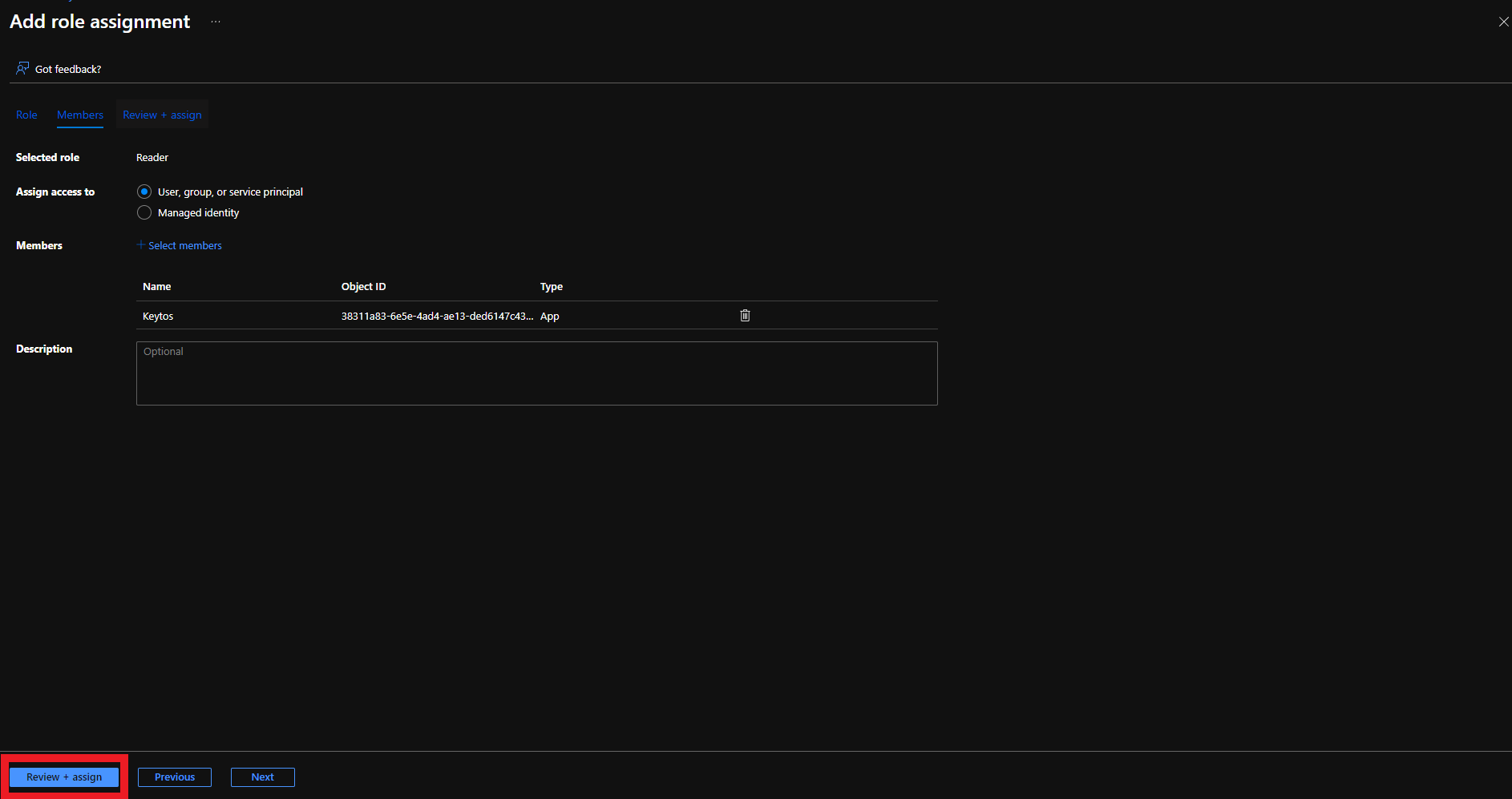
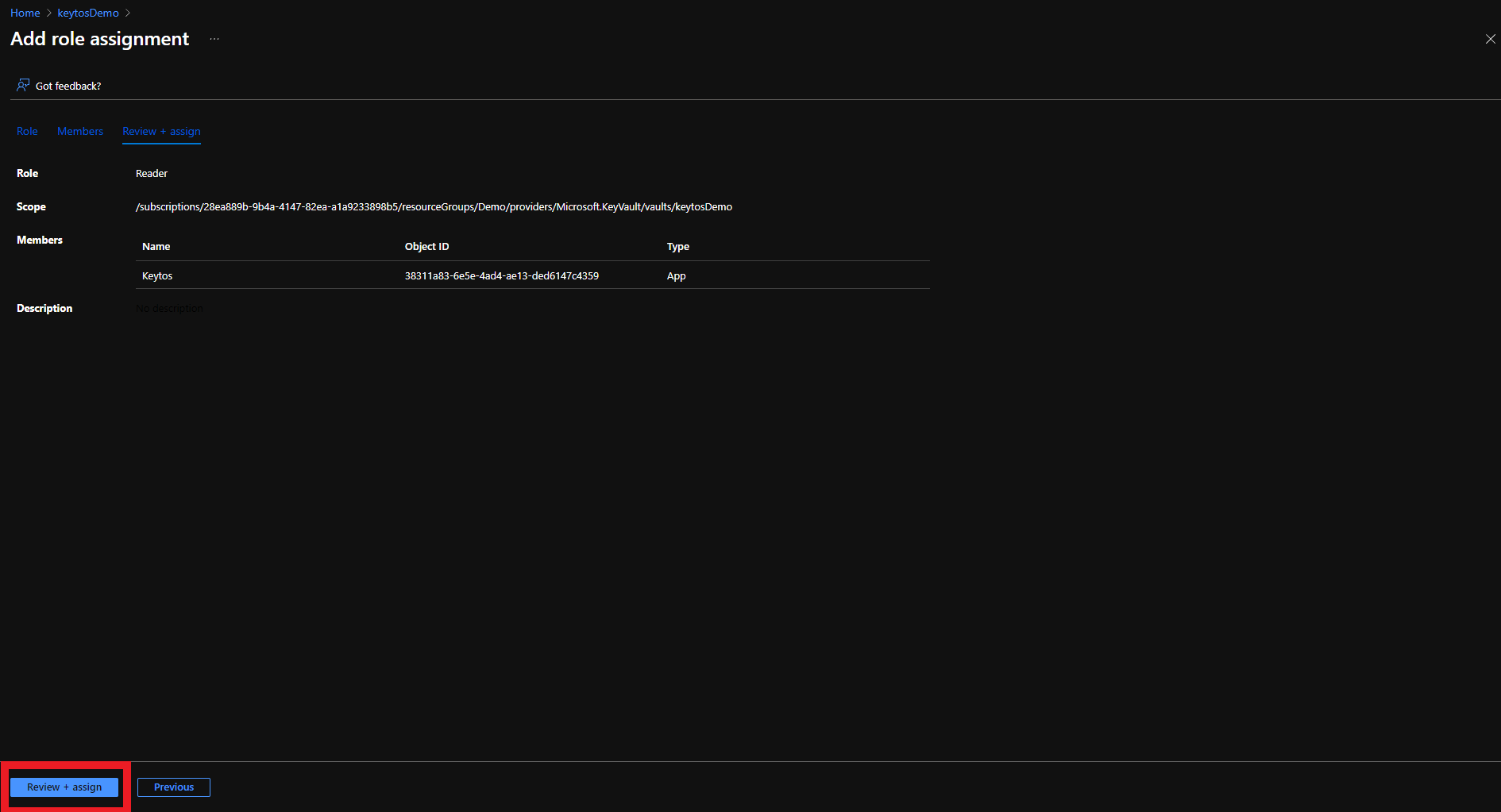
There are two ways to give EZCA access to manage certificates in your Key Vault. You can either use Key Vault Access Policies or Azure RBAC, depending on your Key Vault configuration. If you have previously disabled Access Policies on your Key Vault, you must use Azure RBAC to grant access.
Make sure to only use the option below which matches your existing Key Vault configuration. If you’re unsure, refer to the Access configuration section in your Azure Key Vault:
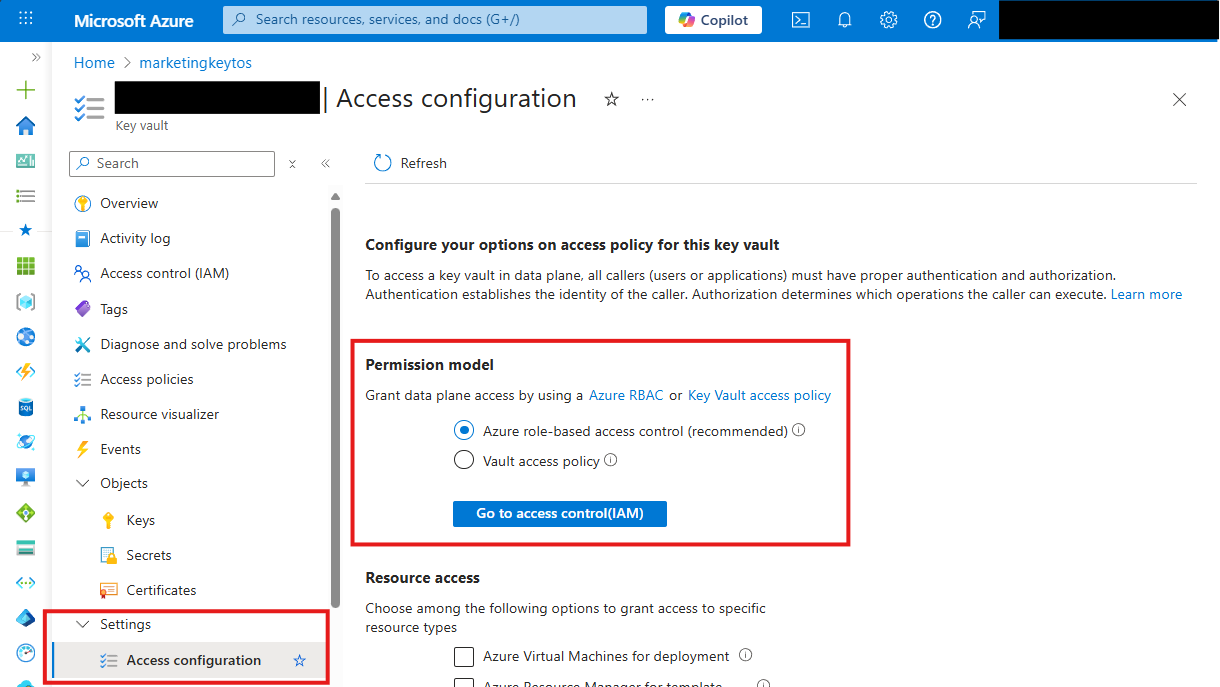
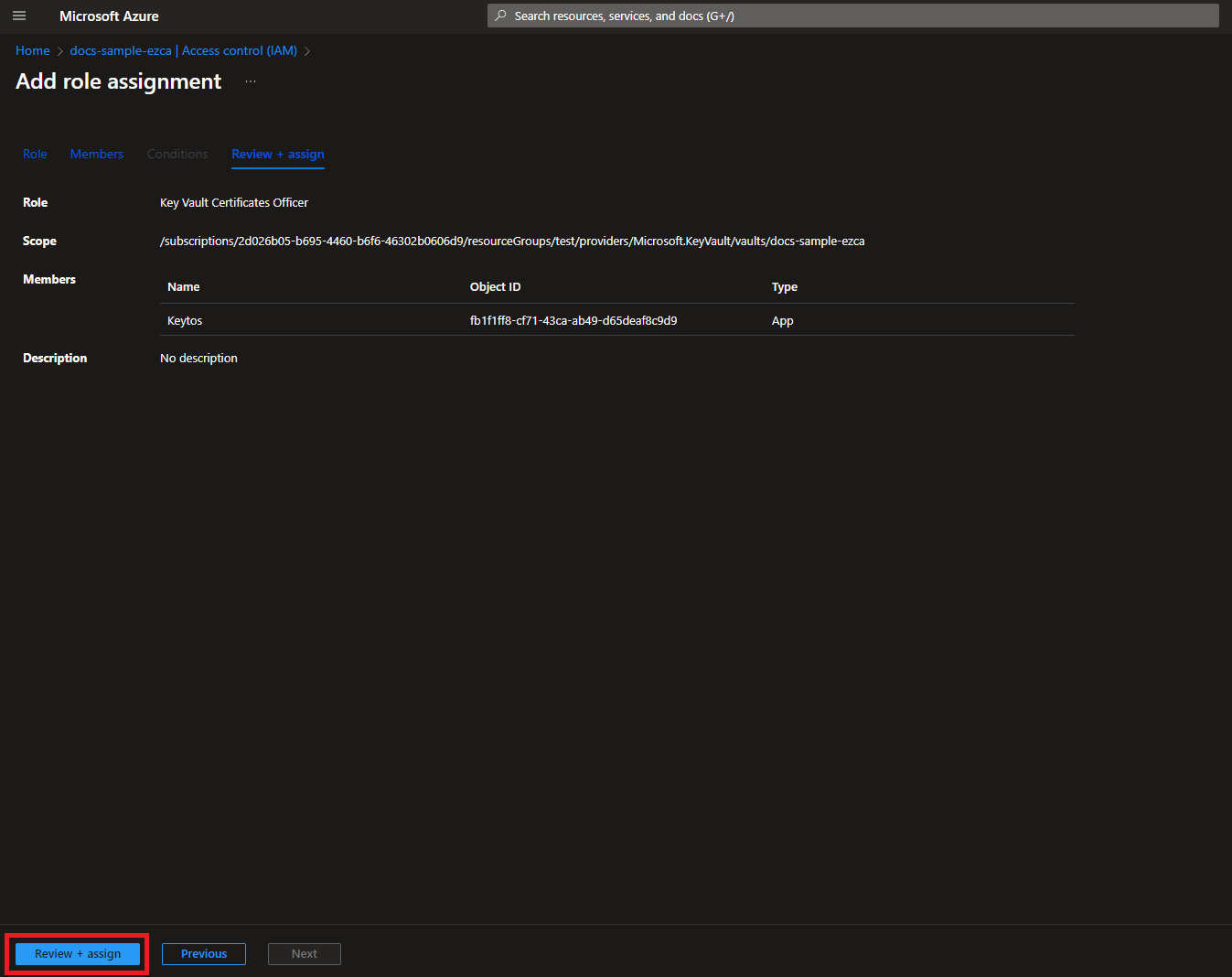
If your Key Vault has RBAC enabled, you will need to add the “Key Vault Certificates Officer” Key Vault RBAC permission to allow EZCA to manage the certificates in the Key Vault.


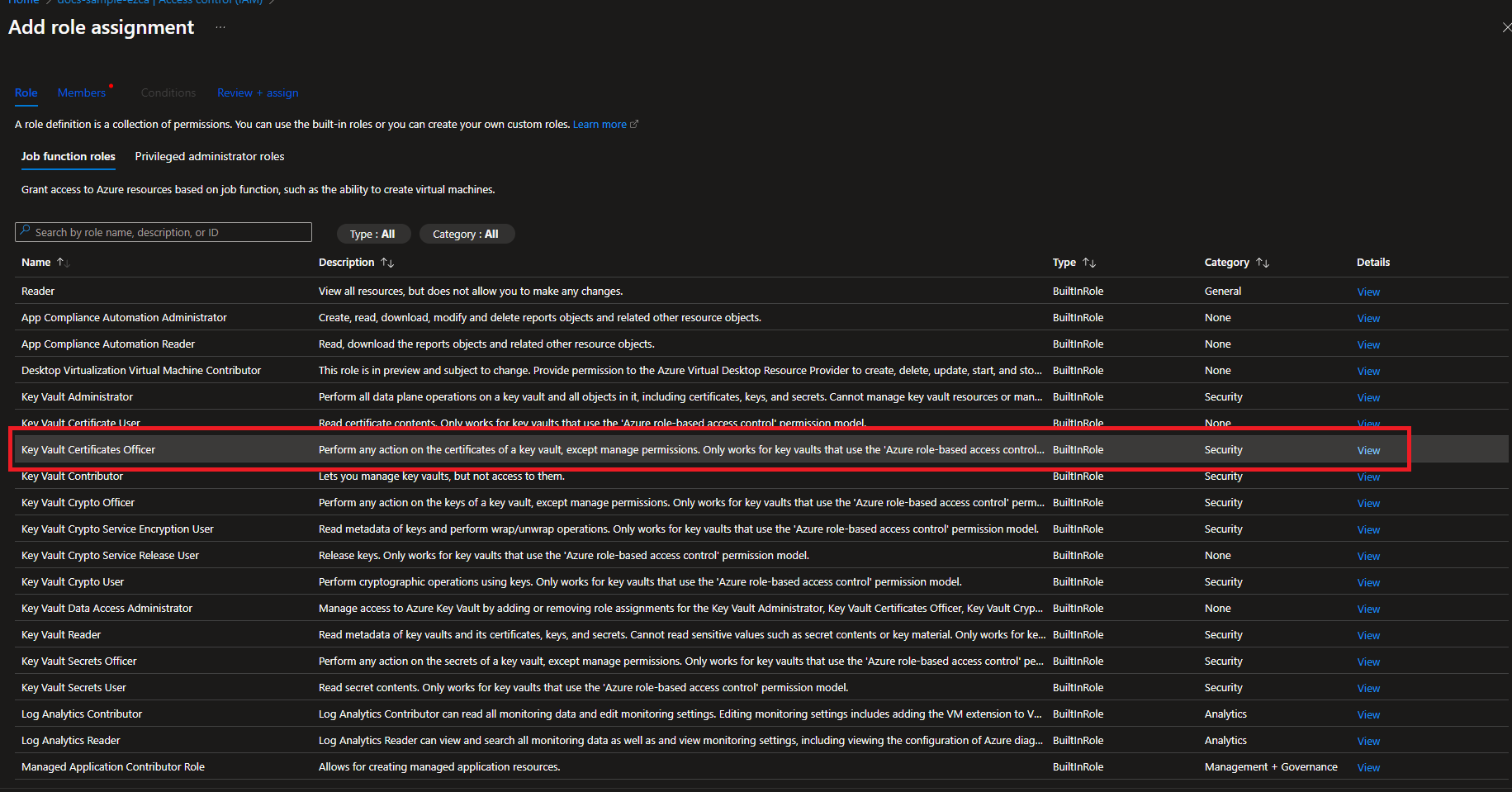




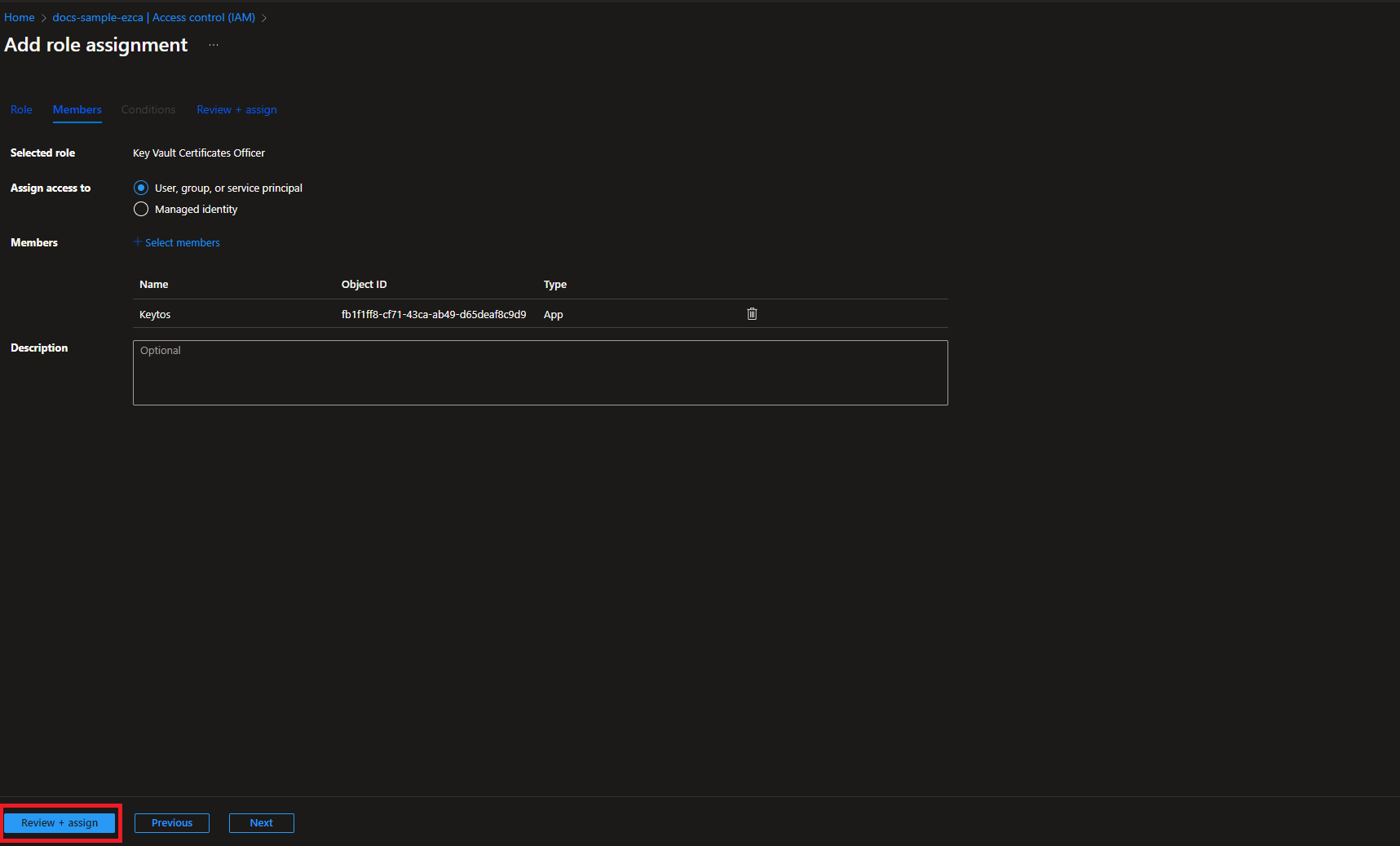
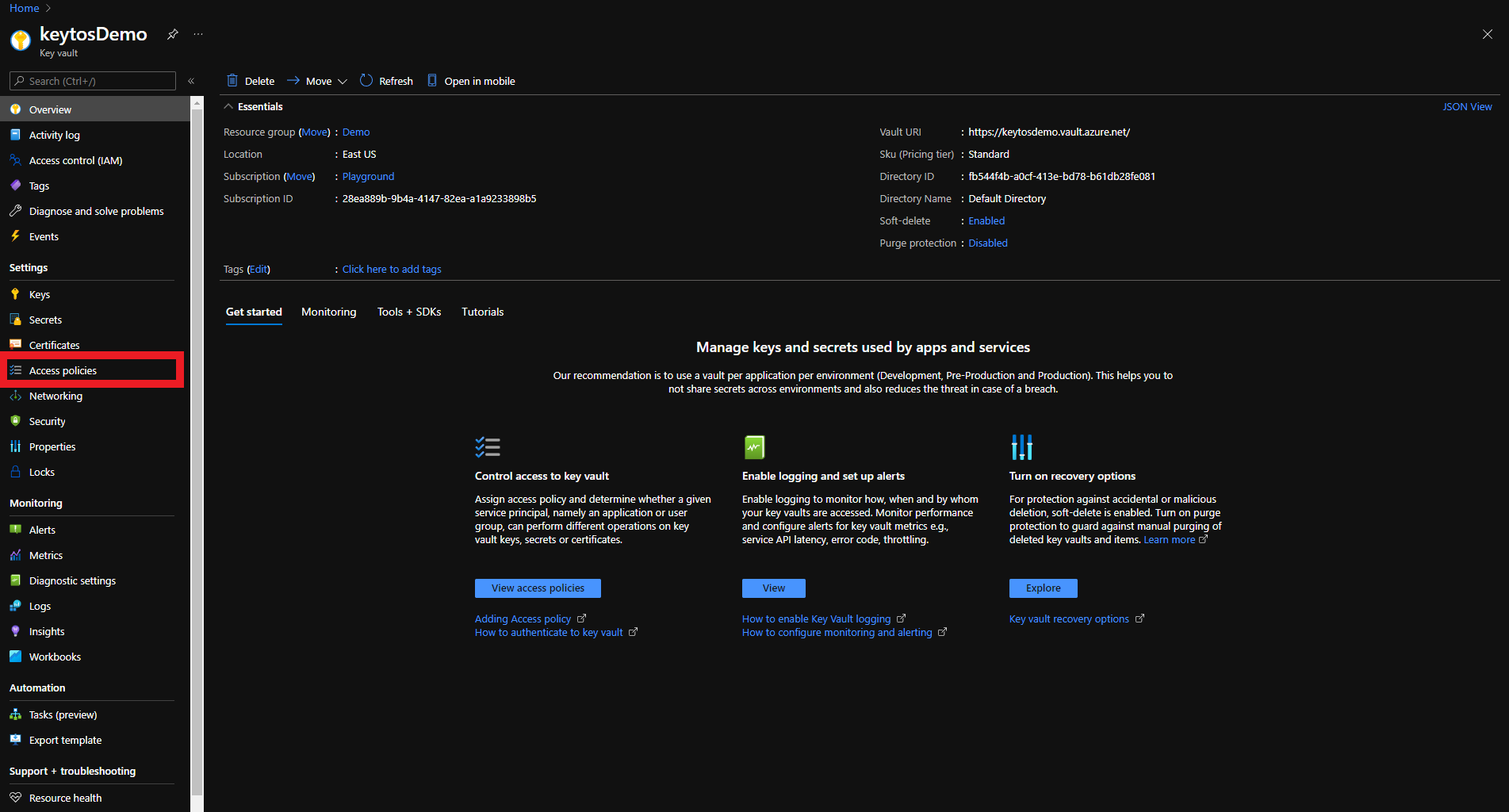
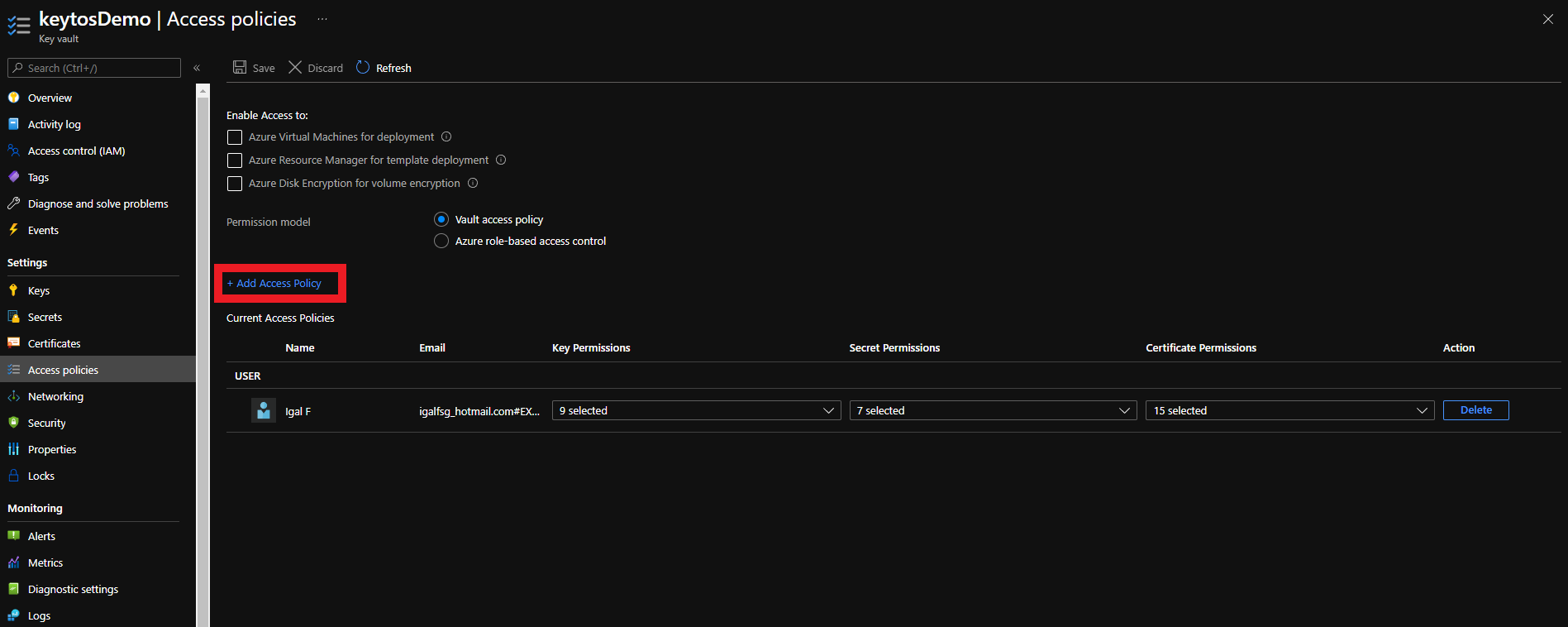
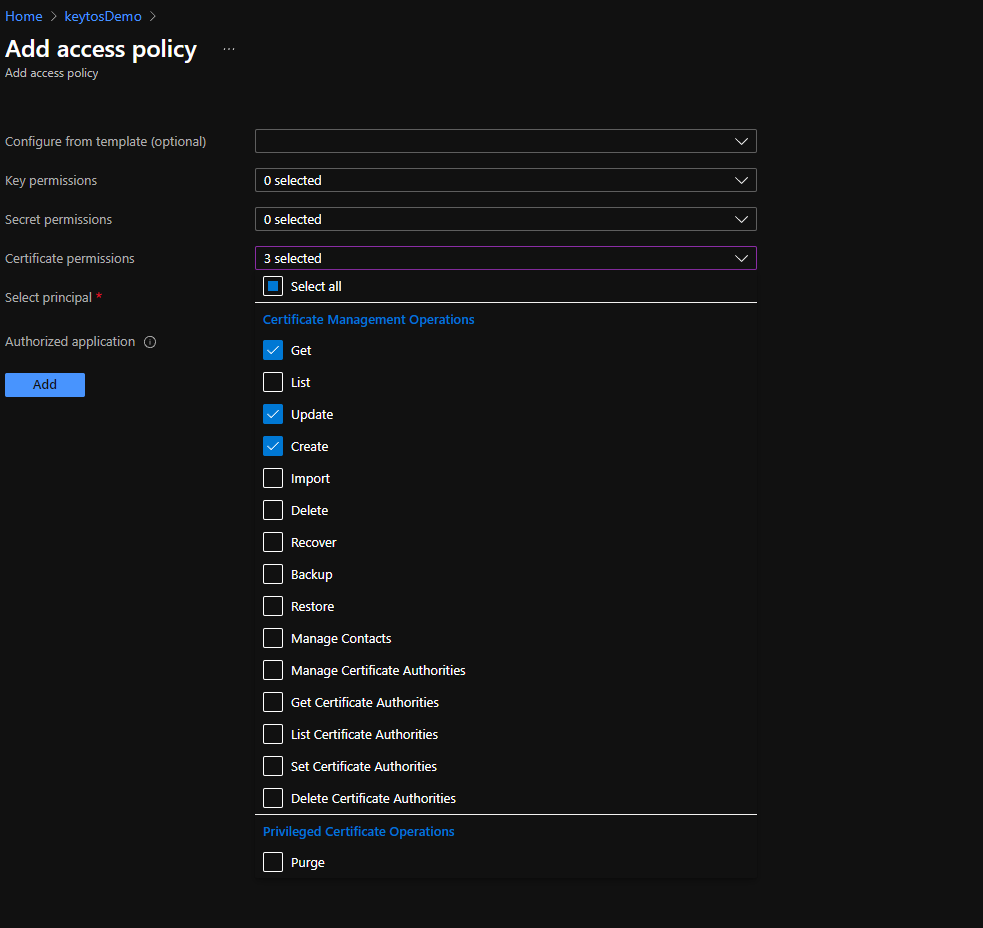
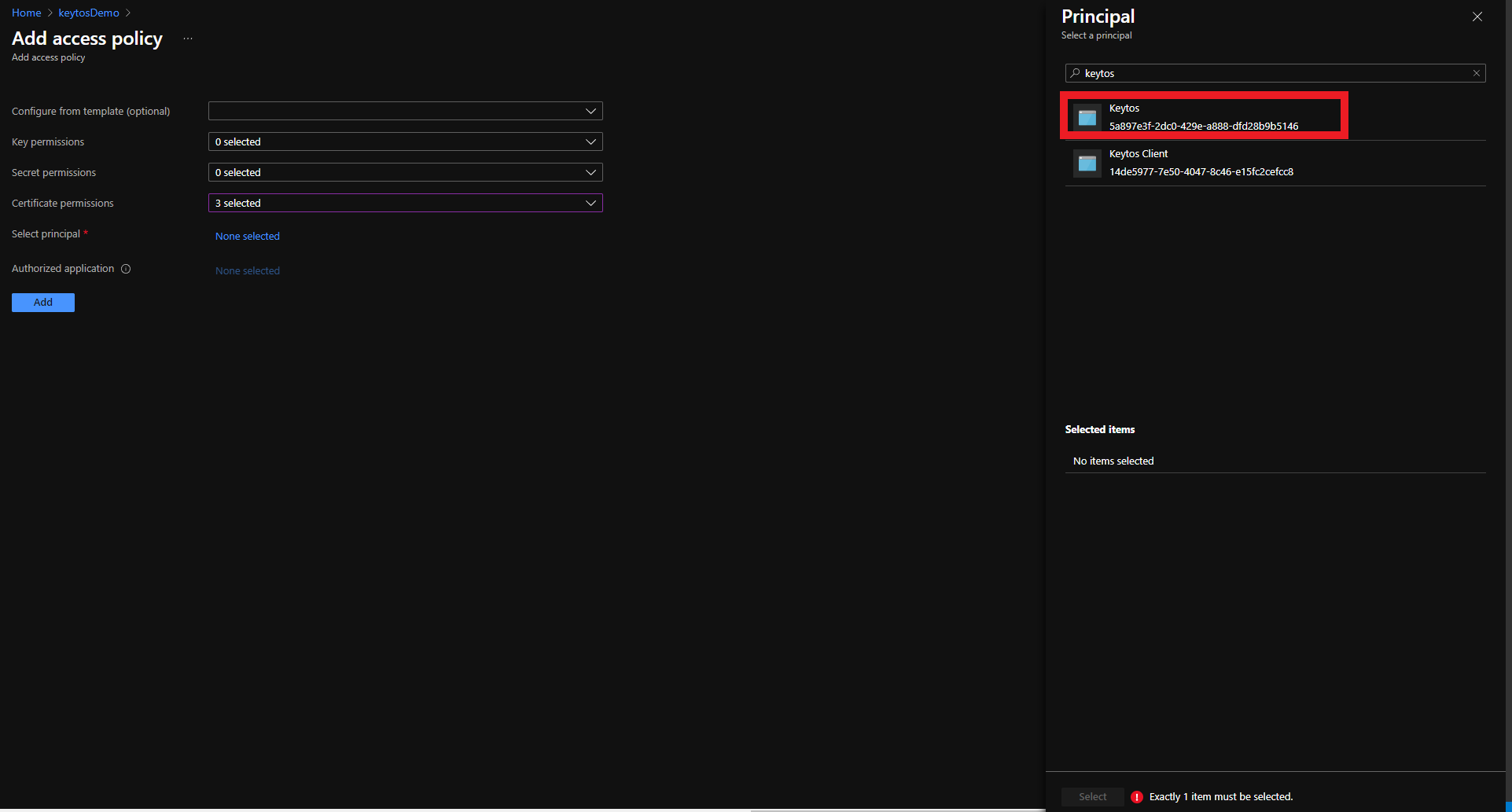
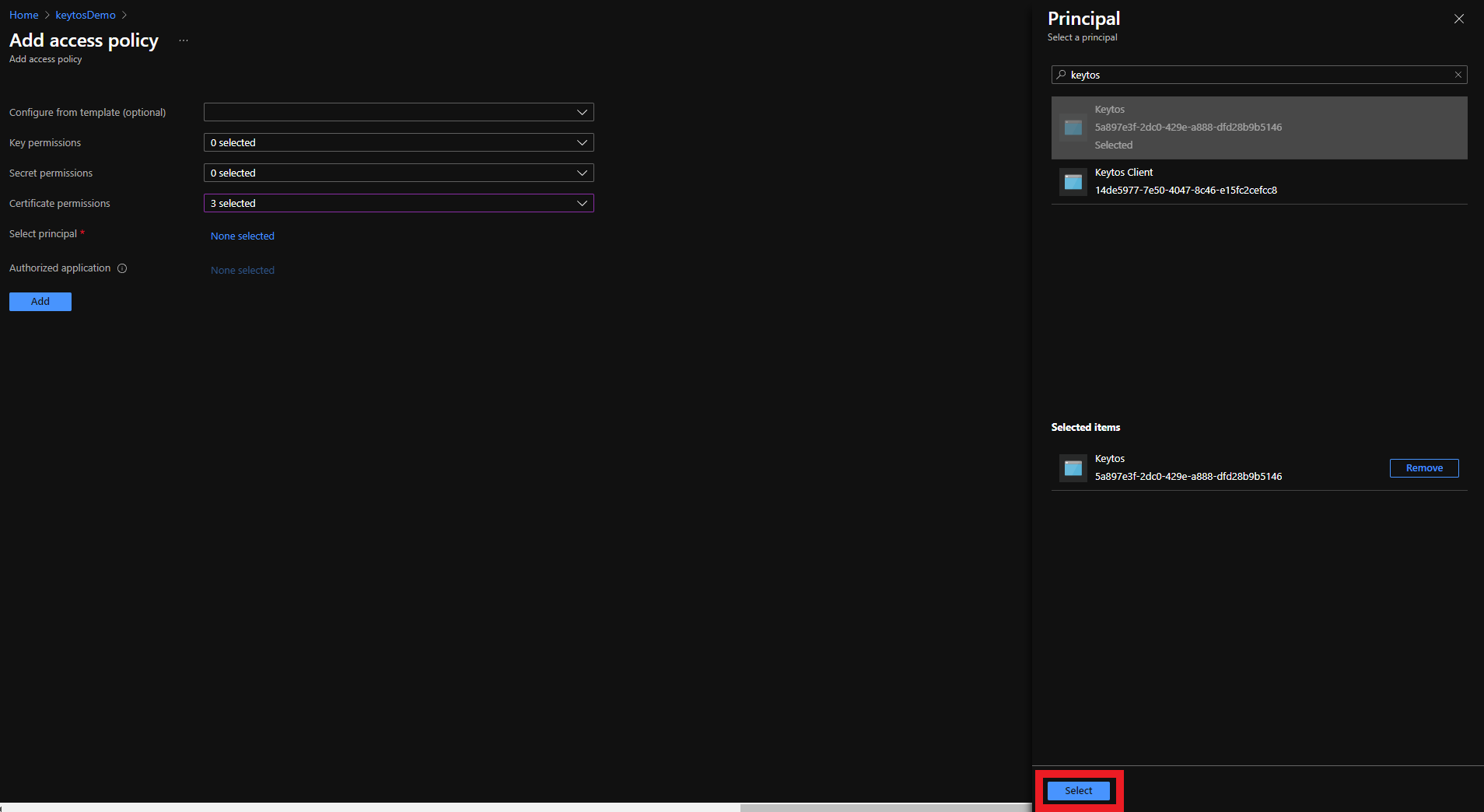
To get the most granular control over the permissions that EZCA has to your Key Vault, you can add an access policy to the Key Vault. This will allow you to specify the exact permissions that EZCA has to the Key Vault.

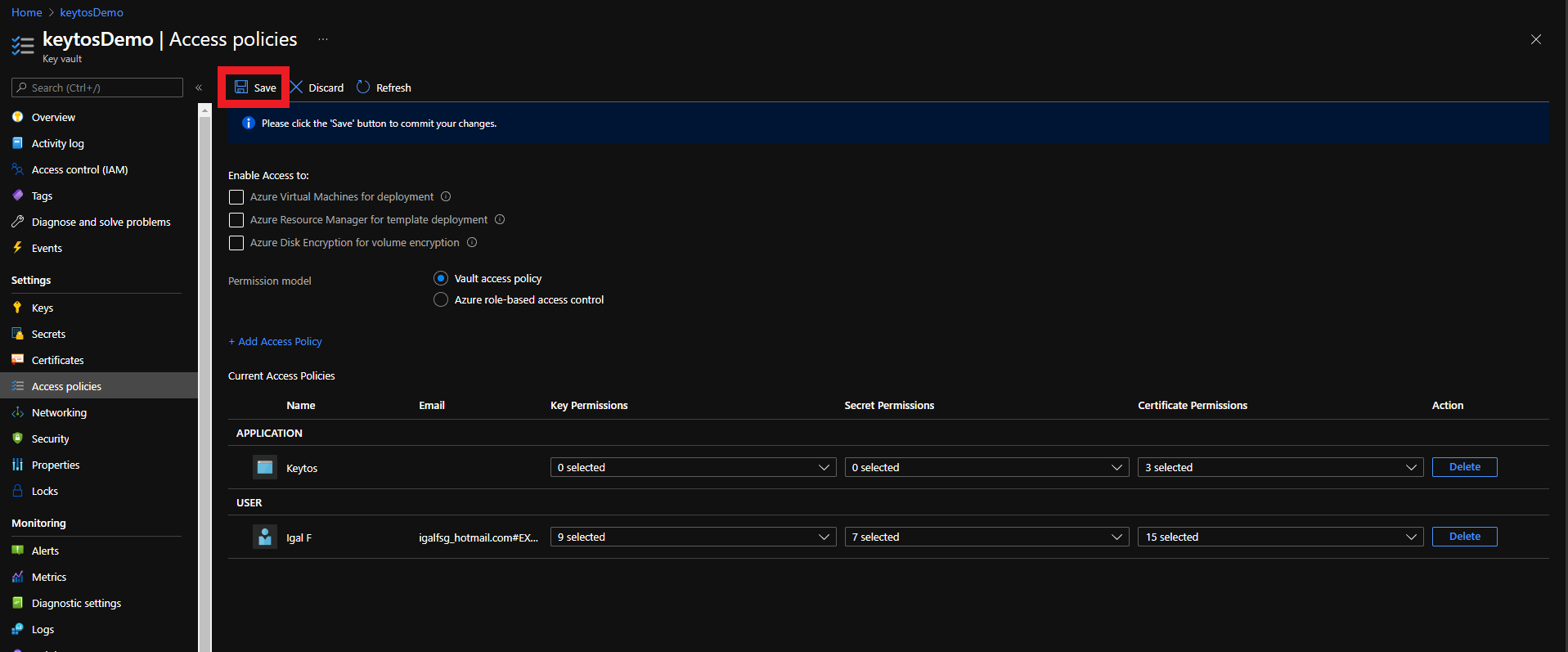
If your Key Vault has a firewall enabled, you will need to add the EZCA IP address to the Key Vault firewall to allow EZCA to manage the certificates in the Key Vault.
To find the EZCA IP addresses, please go to the EZCA portal status of your instance for example: https://portal.ezca.io/status and copy the IP addresses from the Outbound IP Addresses section.
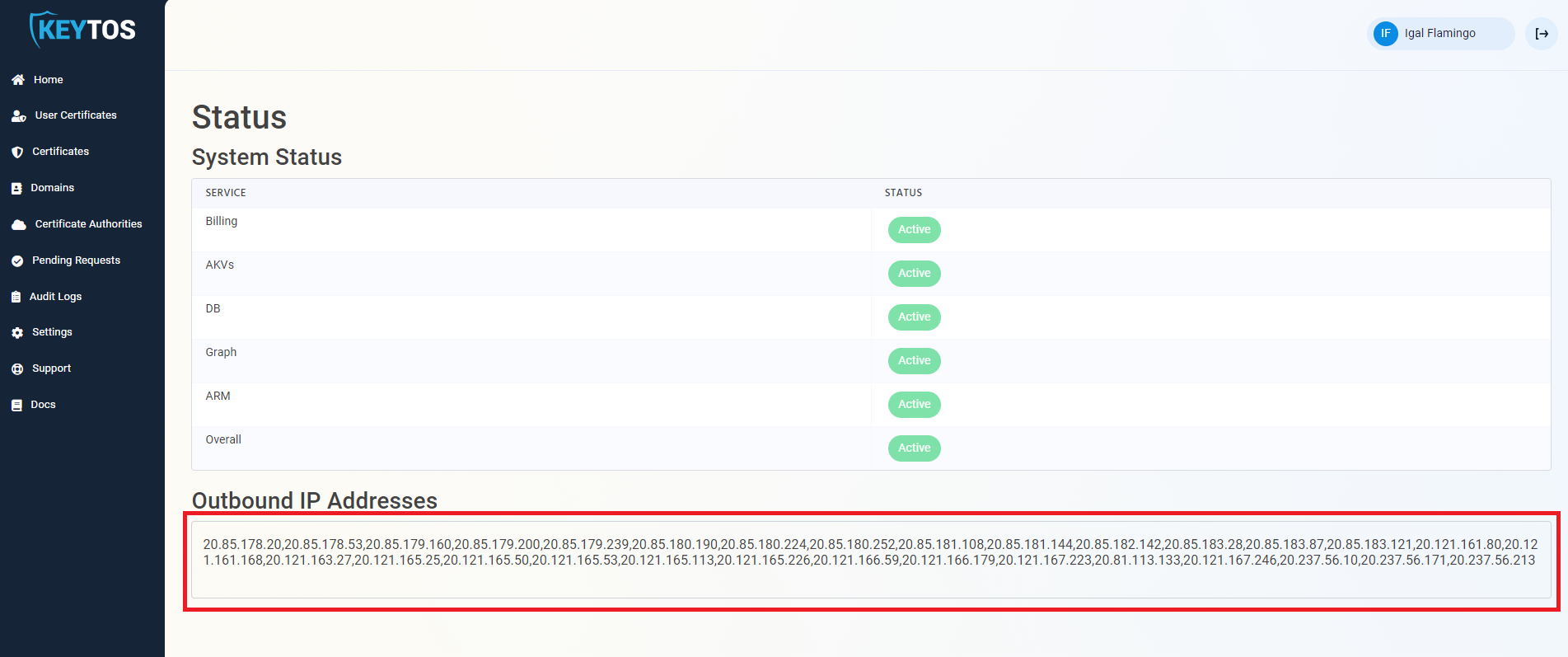
You can now add the IP addresses to the Key Vault firewall. Since the EZCA IP addresses are subject to change, we recommend adding the entire IP range to the Key Vault firewall. To do this, you can use the following PowerShell script to add the IP range to the Key Vault firewall. Replace the $ipRange variable with the IP range from the EZCA portal status page:
Connect-AzAccount
$ipRange = ""
$resourceGroupName = "" # Replace with your resource group name
$keyVaultName = "" # Replace with your Key Vault name
$ipArr = $ipRange.Split(",")
Add-AzKeyVaultNetworkRule -VaultName $keyVaultName -ResourceGroupName $resourceGroupName -IpAddressRange $ipArr
Learn how to troubleshoot common problems when issuing and managing certificates in Azure Key Vault, such as pending CSRs or merging certificates.